Rights and powers mean access to data. And sometimes, when an employee feels a lack of control, they can use the data they’ve been given access to for their own benefit. This misuse can threaten an organization’s data security or even lead to a data breach. Data misuse was in the top seven categories of threat actions in 2020 according to the Verizon 2021 Data Breach Investigations Report (DBIR). For organizations, data misuse may lead to costly lawsuits and loss of reputation.
In this article, we show real-life situations where data misuse led to significant consequences for organizations, cover four effective methods to avoid such misuse of information in your company, and suggest our solution for building effective protection against data mishandling.
What is data misuse and what are the reasons behind it?
The definition of data misuse is pretty simple: using any information in a way it’s not supposed to be used. Terms of proper data use are usually spelled out in laws, industry standards, corporate policies, and user agreements.
Data misuse is often associated with data theft. Unlike data theft, however, in the case of data misuse, information isn’t always passed to third parties.
In some cases, data misuse can lead to a data breach. For example, an employee can copy data to a flash drive for personal use but lose it, resulting in a data leak. Or, in order to work from home, an employee can send data to their personal laptop, which can be hacked.
The most common reasons for data misuse are:
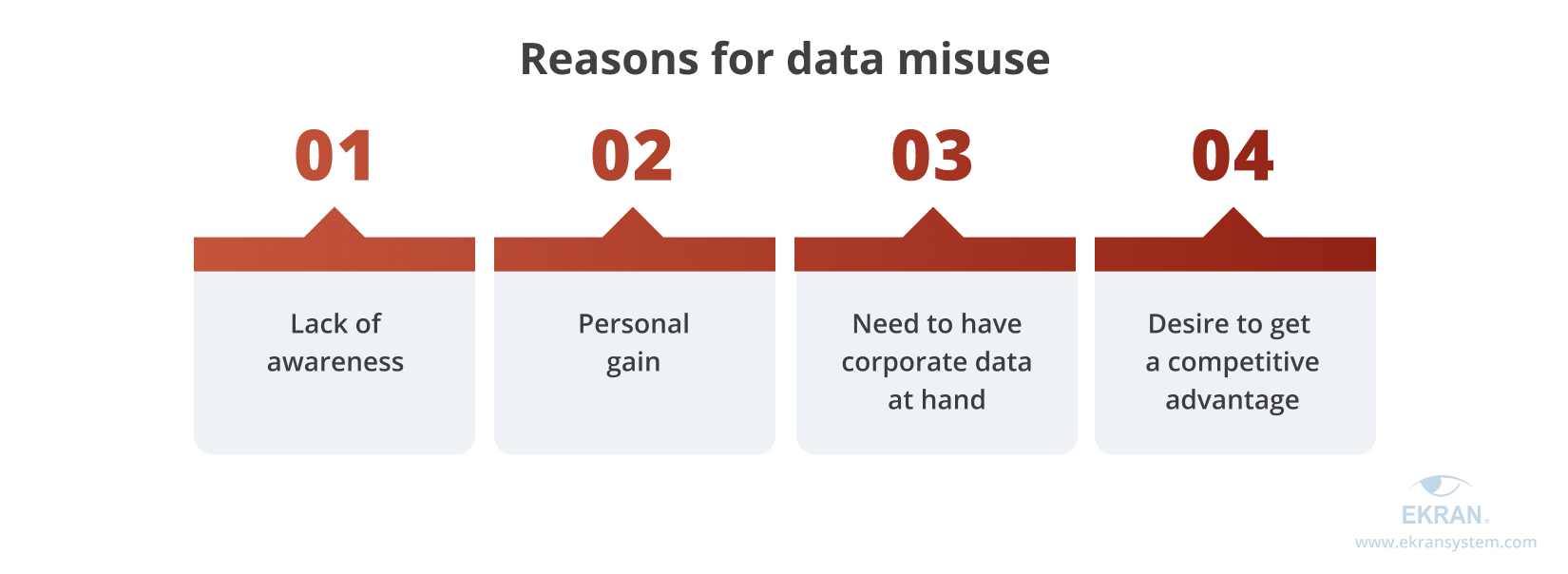

Now, let’s see examples of how secret data has been misused and how real people have been affected.
Insider Threat Techniques and Methods to Detect Them
4 major real-life cases of data misuse
How can data be misused?
While data misuse can remain unnoticeable for a long time, its consequences can bring lots of harm to an organization.


Nationwide Children’s Hospital data leak
The Research Institute of the Nationwide Children’s Hospital in Columbus, Ohio, experienced a trade secrets leak that came to light in spring 2021. A researcher at the institute, together with his wife, sold the hospital’s trade secrets to China. During ten years of research, the pair collected data in separate laboratories and then illegally handed it to competitors. The secret data, related to exosomes, is important for research, as well as for identifying and treating various diseases.
For conspiring and selling trade secrets, Yu Zhou, the researcher, was sentenced to 33 months in prison along with confiscation of assets and a $2.6 million fine.
Stop Data Leaks: Active DLP Systems vs. Passive Monitoring Solutions
Fifth Third Bank data abuse
Fifth Third Bank in Cincinnati experienced an abuse of data in February 2020, when sensitive information was misused by a group of employees. They leaked social security and account numbers, driver’s licenses, address information, and even customers’ mothers’ maiden names.
As part of a fraud ring, the employees presumably wanted to set up credit accounts outside of Cincinnati, where fraudulent charges would be difficult to catch until reported to credit reporting agencies.
After the incident, employees that abused their access to the bank’s assets were put under criminal investigation. In turn, the bank took steps to strengthen the security of customers’ accounts.
How to Protect an Enterprise Database from Privilege Abuse
Credit Suisse insider attack
In February 2022, Credit Suisse suffered an insider attack carried out by an employee whistleblower. The employee leaked data to which he had access to a German newspaper.
As a result, information on more than 18,000 accounts (which contained more than $100 billion) was revealed to the Süddeutsche Zeitung newspaper, and afterwards to a wide number of other global media and organizations. Journalists quickly spread the information, as it contained data on “dirty billings” belonging to some people under sanctions. Shares of Credit Suisse lost around 3% after the incident.
5 Real-Life Data Breaches Caused by Insider Threats
Avago and Skyworks trade secrets theft
On June 26, 2020, a U.S. District Court found Chinese citizen Hao Zhang guilty of trade secrets theft and economic espionage against both Avago and Skyworks. According to the court, Hao collected materials for five years with the aim of helping the Chinese government and opening his own business.
Hao and his accomplices obtained information regarding the manufacturing and performance of wireless devices. The conspirators then opened their own company and tried to compete with the firms from which they stole data. Employees of the Chinese Tianjin University also took part in the scheme.
10 Data Security Best Practices: Simple Steps to Protect Your Data
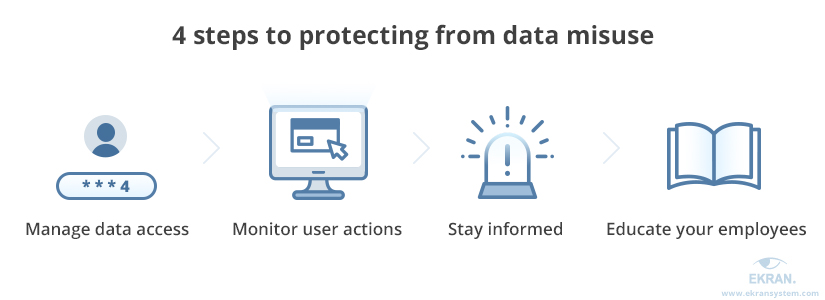
4 steps to protecting your company from data misuse
To breathe easy, you should not only secure all your data at rest and in transit but also wisely configure notifications and provide courses to support your staff members. Let’s observe four core ways to detect and prevent data misuse.
How can you avoid data misuse?

Manage data access
Data access is the entry point for potential misuse. Employees and subcontractors may get access to confidential or sensitive data they aren’t supposed to have access to in various ways:
- An admin may accidentally provide access
- An employee can use their legal access
- A malicious insider can use a shared account or a coworker’s password
Data can be misused when proper access management is not in place. This happened to Fifth Third Bank, as you saw in the data misuse examples above. Those who misuse data are concentrated on data exfiltration according to the Verizon 2021 DBIR.
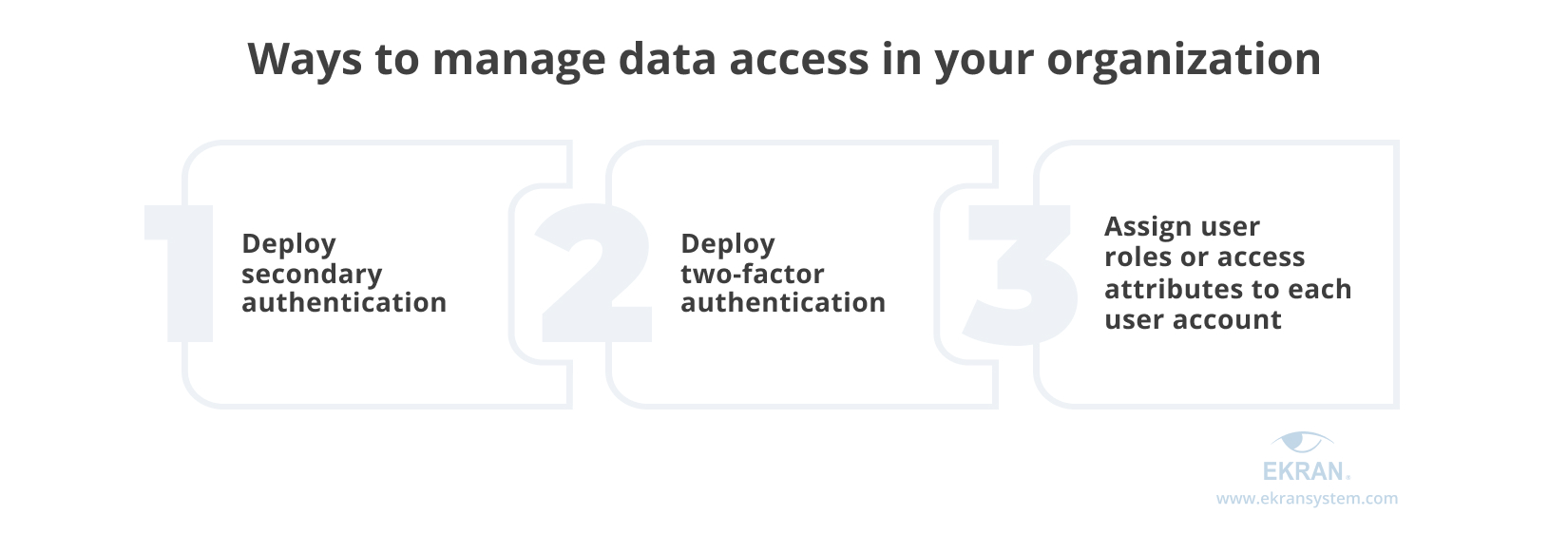

- Deploy secondary authentication
It’s important to verify an individual user’s identity in order to know who exactly is trying to log in to the system. This becomes more complicated when employees use shared accounts, such as admin and root. It’s also important to use additional authentication if you use shared accounts.
- Deploy two-factor authentication
Credential theft remains one of the most popular ways of causing a security breach. Multi-factor authentication allows you to positively identify a user, as it requires not only what a user knows (credentials) but something the user owns (such as a smartphone) or something a user is (such as biometric data).
- Assign user roles or access attributes to each user account
Once a user’s identity is verified, you should be able to granularly manage access. To do that, you can assign user roles or access attributes to each user account.
The Verizon 2021 DBIR shows the tendency of data misuse, which requires legitimate access to assets. Access management is especially important for privileged users.
With Ekran System’s capabilities, you can manage data access easily and effectively:
- To reliably identify remote or on-premises users of your organization, use our two-factor authentication functionality.
- To identify users of built-in or shared accounts, use secondary authentication capabilities.
- To mitigate the risks of privilege misuse, use our privileged access management (PAM) solution.
Monitor user actions
One of the best ways to detect and prevent data misuse is to see exactly what happens after data is accessed. A dedicated user monitoring solution allows you to easily see what has happened with data – when it was used, how, and by whom.
This method of insider threat mitigation includes:
- Сollecting user activity logs. This is the most basic way to monitor user actions. Logging every user action taken in your network provides you with context for actions. But if your company employs hundreds of workers, it’s almost impossible to detect data misuse in time only with activity logs.
- Continuous user monitoring. This can help you catch a malicious insider in the act. It might have helped to prevent data misuse at the global investment firm Fifth Third Bank in Switzerland, as we saw in the case above.
- Video recordings. Modern user activity monitoring solutions combine continuous observation with searchable video recordings of each session. This way you can find records of a suspicious event within seconds, figure out the context, and determine whether the action had malicious intent.
As the Verizon 2021 DBIR claims, the two biggest misuse actions that led to data breaches in 2020 were privilege abuse and data mishandling. That underlines the importance of paying special attention to privileged users’ actions as well as educating staff on proper handling of sensitive data.
You can use these methods of enhanced user monitoring in your organization with Ekran System monitoring, session recording, and logging functionality for:
- Employees — Monitor computer activity of employees who have limited or constant access to critical information.
- Privileged users — Monitor the activity of your high-level workers and administrators who regularly have or gain extended access permissions.
- Third-party vendors — Closely watch your partners, vendors, or providers that access the organization’s sensitive data.
What Is Privileged Session Management and How Can It Help Secure Your Sensitive Data?
Stay informed
Managing user access and monitoring user activity provides you with lots of activity records and logs that are useful for investigating data misuse and its consequences. But that’s not enough for preventing misuse in real time.
The amount of time it takes you to detect and stop data misuse is one of the main factors in the cost of a data breach. The Ponemon Institute points out in their 2021 Cost of a Data Breach Study [PDF] that organizations who were able to identify and contain a data breach in less than 200 days saved $1.26 million compared to those who needed more than 200 days.
Also, privilege misuse appears to be one of the two causes of a data breach that take the longest to discover according to the Verizon 2021 DBIR. Timely prevention of a breach resulting from data misuse saves a lot of potential time and resources. Several tools can help you do it.
- Employing dozens (if not hundreds or thousands) of workers makes their continuous monitoring difficult. That’s why customizable automated alert and notification functionality is a must for modern user monitoring software.
- The efficiency of rules-based alerting functionality largely depends on how well thought out the set of rules is. When configured correctly, rules spare a security officer from a ton of false positives. Too few alerts are also a warning sign, as it might indicate that your rules don’t cover all suspicious actions.
- To protect your organization from suspicious actions going unnoticed, you need to be informed of any actions that aren’t ordinary for a specific user. This can be done with the help of a user and entity behavior analytics module (UEBA).
You can customize Ekran System’s functionality for your organization’s current needs and for specific actions you want to be notified about:
- Automated alert and notification capability can notify security personnel of a security event: logging into a server, leapfrog logins, running a certain application, connecting a new USB device, etc.
- A highly customizable rules-based alerting system is a more traditional approach. You can use a collection of default alerts based on the most common suspicious events. For specific cases, you’re free to create new rules.
- AI-powered UEBA functionality analyzes user behavior during day-to-day activities and figures out baseline activity for each employee. If a worker behaves suspiciously (for example, tries to access data or a server they’ve never used before), the software alerts a security officer.


Educate your employees
When talking about how to prevent data misuse, don’t underestimate the power of employee education.
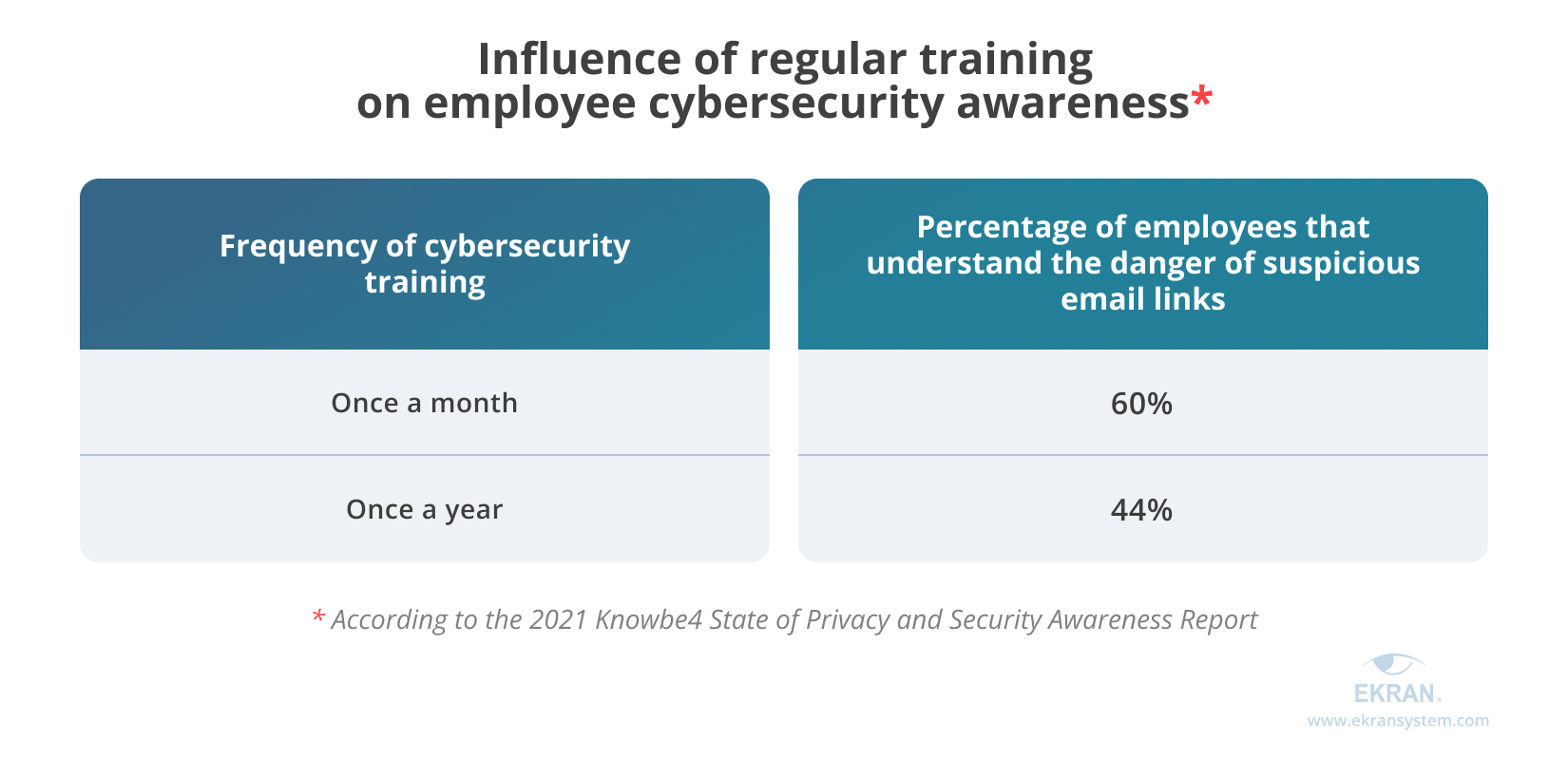
A 2021 State of Privacy and Security Awareness Report by Knowbe4 [PDF] shows that infrequently performed staff training increases employee cybersecurity negligence. Only 42% of US-based employees understand the dangers of repeated or weak passwords, and only 37% understand the importance of locking their computer while leaving.
Also, compare these figures for 2020–2021, which show how the increasing frequency of training improves employees’ awareness of suspicious email links:

There are two steps to educate your employees:

- 1. Include information on data security in a general corporate policy. A well-thought-out policy is a reliable source of information about in-house procedures and standards, including cybersecurity. It’s the best way to let newcomers know what they can and can’t do with corporate data.
- 2. Set up educational courses on data security. You can ask security officers to share their experience. A generic course on cybersecurity is always useful to remind employees not to share their credentials, inform them about new phishing methods, etc. Make sure to remind employees why it’s important to take care of sensitive data and what consequences data misuse will have not only for the company but also for its employees.
To strengthen data security, consider creating a dedicated insider threat policy. It can help you prevent your employees from misusing data. The 2021 Insider Threat Report by Cybersecurity Insiders states that 81% of organizations in the world already have or are currently building an insider threat program.
It’s noteworthy that an insider threat and risk management policy is required by NIST SP 800-53, HIPAA, GDPR, and other cybersecurity requirements. You can implement such policies on your own or as part of a wider cybersecurity policy.
To learn more about this vital element for preventing data misuse, check out our 12-step guide to building the perfect insider threat program.
Linux User Activity Monitoring
Conclusion
Deploying a specialized insider risk management platform like Ekran System can help you detect data misuse using various capabilities:
- Identity and access management will prevent your employees from abusing access to sensitive data.
- Continuous activity monitoring will provide you with online surveillance and records of all user actions.
- Incident response functionality will make it possible to block forbidden user actions or warn users about actions they’re trying to commit that constitute data misuse in the form of real-time alerts and notifications.
- Session recording and activity logs will help you in training your employees using your own examples, cases, and threat landscape.
With Ekran System, you only need to take care of educating your employees about data misuse by providing detailed instructions on data use in your corporate policy and setting up employee cybersecurity training. Ekran System will take care of everything else.






