Traditional identity and access management (IAM) implementation methods can’t provide enough flexibility, responsiveness, and efficiency. Indeed, many organizations struggle with developing a mature IAM program according to the State of Enterprise Identity report by the Ponemon Institute. Among the key reasons for this challenge cited by respondents in the report are a lack of employee awareness, an insufficient budget, and ineffective planning. At the same time, the cybersecurity environment is actively changing due to factors such as the COVID-19 pandemic, geopolitical disturbances, and increased teleworking, which is also changing the requirements for efficient IAM.
To keep pace with the constantly changing cybersecurity landscape, consider increasing the agility of your cybersecurity efforts, starting with your organization’s identity and access management strategy. In this article, we explain the advantages of an Agile approach to cybersecurity and offer five practical steps for bringing agility to your IAM strategy.
Understanding the need for Agile cybersecurity
Originally, Agile was a project management methodology described in the Agile Manifesto. This approach was meant to enable software developers to:
- Quickly adapt to change
- Better see opportunities
- Gain process transparency
- Detect blocks on the way to efficiency
Although widely used in software development, the Agile methodology can be applied to nearly any process that can be planned and managed. Cybersecurity is not an exception, as it requires flexibility and regular enhancements in order to provide the necessary level of efficiency and protection.
No matter the process you apply it to, the core pillars of the Agile approach are the same. Let’s see how those pillars work in cybersecurity:
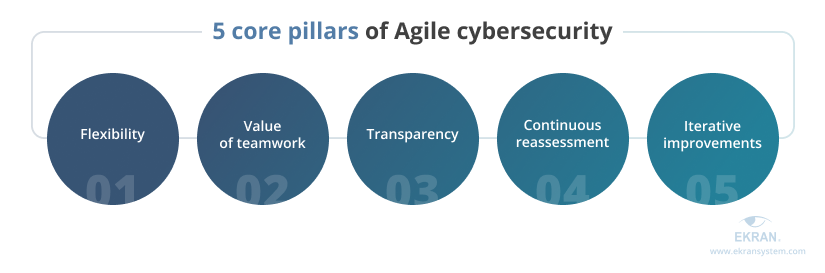

Flexibility. According to the Agile Manifesto, responding to change in Agile is valued more than following a plan. Balancing the time, scope, and budget for implementing and managing your cybersecurity strategy can help you quickly adapt to changing needs and cybersecurity requirements without losing velocity.
Value of teamwork. Cybersecurity team members that follow Agile principles work collaboratively, trust each other, and clearly understand their roles and responsibilities. People rely on each other rather than processes and tools, ensuring flexibility and efficiency. Communication between team members happens as needed.
Transparency. The Agile approach implies that all people involved in managing and implementing the cybersecurity strategy are on the same page. All team members share a common understanding of the organization’s cybersecurity plans, processes, and goals, use standard terminology, and know the project’s progress. Important changes are justified and promoted to motivate employees.
Continuous reassessment. Periodic reassessment is needed to identify an organization’s cybersecurity flaws and potential issues in a timely manner. Reviews of teamwork also help to detect inefficient processes and adjust them as soon as possible, resulting in higher-quality work and achievement of planned cybersecurity objectives.
Iterative improvements. Changes to an organization’s cybersecurity system are implemented in short cycles, called sprints. Short sprints help you quickly implement and test new cybersecurity controls and processes on the go. Based on the results of the previous sprints, your cybersecurity team can plan improvements for the following iterations, without waiting months until the entire cybersecurity system is developed.
Moving Beyond Fear, Uncertainty, and Doubt (FUD): 3 Ways to Strengthen Your Cybersecurity Today
To better see why the Agile approach to cybersecurity is better than a non-Agile approach, let’s compare them.
Comparison of Agile vs non-Agile approaches to cybersecurity


- Increased flexibility — A flexible cybersecurity strategy can help an organization be resilient and meet constantly changing cybersecurity regulations.
- Better responsiveness — An Agile approach enables you to manage changing priorities and react to new cybersecurity challenges and business needs.
- Improved visibility — A prioritized roadmap, timeline, and budget help keep cybersecurity activities visible and on track.
- Increased operational efficiency — Better team productivity, faster cybersecurity strategy execution, and more efficient processes help reduce cybersecurity risks.
- Reduced costs — The choice of efficient solutions and processes can make an organization’s cybersecurity more cost-efficient.


- Inability to change — Rigid cybersecurity strategies and solutions are incapable of fast and efficient change. New solutions are often inefficiently implemented on top of existing outdated ones.
- Weak cyberthreat resilience — A poor understanding of current and emerging cybersecurity challenges increases the possibility of cyber incidents.
- Lack of proper planning — Deadlines are frequently missed because of unclear timeframes and slow, difficult-to-trace processes.
- Demotivated cybersecurity team — Inefficient cybersecurity team cooperation and unclear responsibilities create confusion and tension between team members.
- Budget overruns — Because of decreased efficiency and low flexibility, the cybersecurity budget is often exceeded.
Read on to discover our five helpful steps for bringing agility to your organization’s IAM.
How to make your IAM strategy more Agile
Being the core of an organization’s cybersecurity, IAM also needs an efficient, rapid, and flexible delivery method. One way to establish such a delivery method is by approaching the IAM strategy from an Agility perspective.


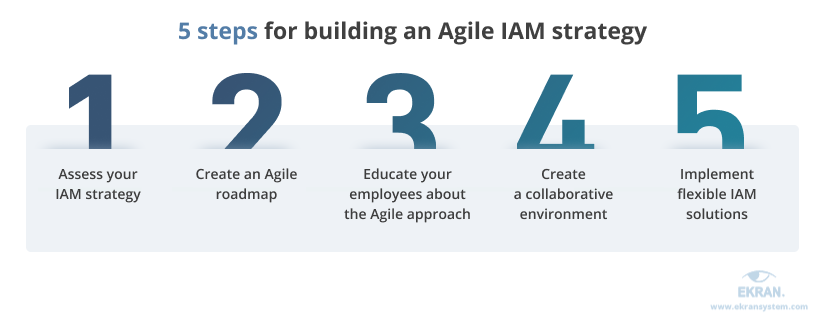
We have outlined five steps for bringing agility to your organization’s access and identity management strategy:

The tips we offer here are applicable both for IAM strategy development from scratch as well as for making your existing IAM strategy more Agile.
1. Assess your IAM strategy
Assess what you already have.
To understand the current state of affairs, you need to review processes, policies, and the overall IAM strategy your organization has at the moment. Analyze user lifecycle processes, HR systems, active directory environments, etc. Once you do this, you’ll know the strong and weak sides of your IAM strategy and what to do next.
After the initial assessment, perform a gap analysis for easier Agile methodology adoption. Check your IAM assessment results for compliance with the desired Agile principles and values. This will help you outline how the current corporate culture, identity and access management practices, the user access review process, Active Directory audits, and other key procedures need to be changed and reorganized. Define and describe the necessary changes as the “future state” – a target condition of IAM that your company wants to achieve.
The initial assessment is not the final one, though. Consider reviewing and improving your organization’s IAM strategy on a regular basis in order to maintain a high level of flexibility and keep up with emerging cybersecurity threats. A key part of the assessment is not only reviewing processes and systems but also contemplating the trends and new opportunities that can transform your IAM routines for the better.
7 Best Practices to Conduct a User Access Review
2. Create an Agile roadmap
Plan your IAM flexibly.
Efficient use of your IAM strategy assessment results would be transforming them into an action plan. It will help you measure progress, define clear deadlines, and outline specific steps to be made towards the desired IAM strategy goals. A roadmap will serve as a defined guideline and keep your IAM improvement progress on track.
At the same time, in order for an IAM strategy to be responsive, a roadmap must be capable of change. Compared to a traditional roadmap, an Agile roadmap is much more flexible, allowing for rapid adjustments when needed. How to build an Agile IAM roadmap? By keeping your IAM planning horizon a few months ahead rather than an entire year ahead. As new cybersecurity threats, trends, and employee feedback emerge, your identity and access management implementation plans may change.
Agile IAM roadmapping also suggests using an iterative model, which implies implementing IAM capabilities and processes incrementally during set periods of time called sprints (usually from two weeks to one month). Defining specific use cases can help you narrow the focus and decide what IAM capabilities and processes to put in each sprint backlog — a list of tasks to be completed during one sprint. Multiple tasks can be done simultaneously during a sprint, with no need to wait until a particular task is performed.
Privileged Access Management: Essential and Advanced Practices
3. Educate your employees about the Agile approach
Spread Agile knowledge across the staff.
Agile is about people. To make it work, educate your cybersecurity team and others responsible for IAM implementation in your organization on the core Agile principles. You need to explain what Agile is, how it works, and, most importantly, why your organization needs it. People need to understand the motivation behind any change; otherwise, they may sabotage it.
Consider designating an employee who will be responsible for promoting and implementing Agile principles across your company or specifically in your cybersecurity department. You might also seek help from an Agile consultant to organize educational lectures or hire a full-time Agile specialist or even an entire Agile team that will ensure the Agile methodology is understood and used correctly and efficiently in relation to your IAM strategy.
Why Do You Need a Just-in-Time PAM Approach?
4. Create a collaborative environment
Achieving results is a shared responsibility.
A collaborative environment can make it easier to assess your organization’s IAM strategy and efficiently change it. Leveraging the spirit of teamwork can help to ensure that every person involved in IAM is open to communication and able to share knowledge during the entire Agile adoption period.
Key stakeholders and IAM decision-makers deserve special attention, as they frequently limit the potential of the Agile approach by not supporting it. To shift the management’s perception, the need for collaboration must be clearly communicated. Achieving the goals of your IAM strategy is only possible through joint efforts.
One way to leverage collaboration is by facilitating Agile meetings. While traditional meetings may contain a lengthy agenda with multiple objectives and are often off-topic, an Agile meeting should be strongly focused around a specific topic or purpose. Such an approach guarantees the meeting doesn’t wander off and achieves its goals in time.
5. Implement flexible IAM solutions
Think holistically.
Your IAM infrastructure must have a wide range of capabilities to be efficient in the long run. Plan for your IAM to cover all possible access levels, identity types, and functionality your organization needs. Also, considering that IAM requirements will evolve over time, flexible solutions are the best choice. So when planning your actions, consider the possible IAM requirement changes in the future.
To implement an identity and access management strategy cost-efficiently and to avoid future integration and management issues, it’s crucial to align your IAM goals with a holistic cybersecurity strategy. Think about the integration potential of the implemented IAM solutions in advance. Depending on the needs and future goals of our business, you may give preference to solutions supporting not only on-premises but also cloud and hybrid environments to increase the agility of your IAM processes.
When looking for a suitable identity management system, take into account its agility along with other criteria. Different IAM capabilities and any related functionality should be considered depending on your business and cybersecurity demands.
Let’s see what Ekran System can offer you in this regard.
15 Cybersecurity Best Practices to Prevent Cyber Attacks in 2022
How Ekran System can help bring agility to your IAM
Ekran System is an insider risk management platform that can enhance your IAM with flexibility, integration, and customization capabilities, empowering you to take a holistic approach to your organization’s cybersecurity.
Ekran System’s extensive IAM capabilities allow you to:
- Verify user identities using two-factor authentication (2FA)
- Granularly control access rights of regular and privileged users
- Approve user access manually or automatically
- Grant temporary access to critical endpoints
- Personalize user sessions within shared accounts
- And more
Two-Factor Authentication (2FA): Definition, Methods, and Tasks
On top of robust IAM features, there are a number of ways Ekran System can improve the overall agility of your cybersecurity:
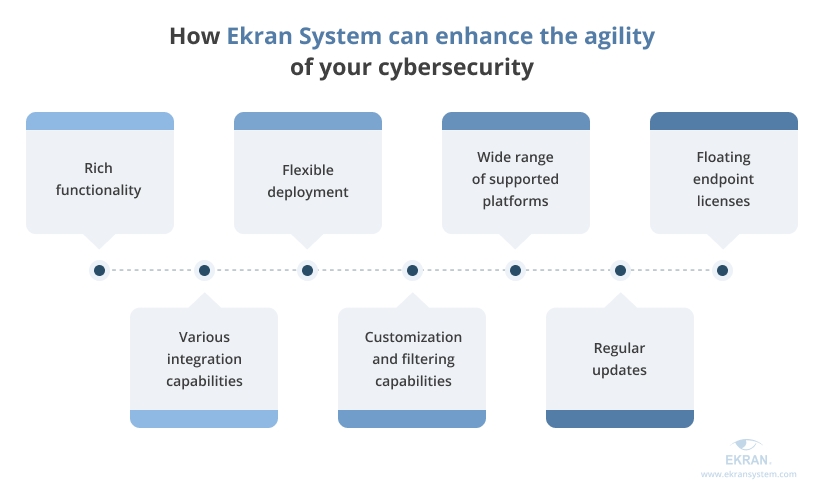

1. Rich functionality. Ekran System may become a holistic solution to many of your organization’s cybersecurity needs. Being an all-in-one insider risk management platform, it can enhance your cybersecurity with privileged access management (PAM), user activity monitoring (UAM), incident response, and auditing and reporting functionality, help you meet IT compliance requirements, and more.
2. Flexible deployment. Deploying Ekran System for performing IAM processes in the cloud, on-premises, or in hybrid environments will allow you to be more responsive and easily adapt to infrastructure changes. In addition, Ekran’s multi-tenant mode allows you to set up and separately control multiple systems in a single Ekran System environment.
3. Wide range of supported platforms. You can install Ekran System on different types of endpoints: infrastructure servers, terminal servers, jump servers, and physical and virtual desktops. Supported platforms include Windows, Linux, macOS, UNIX, X Window System, Citrix, and VMware.
Privileged Account and Session Management: How To Deploy It
4. Floating endpoint licenses. Other platforms demand permanently tying licenses to specific endpoints, while Ekran System provides the ability to reassign a license between endpoints.
This eliminates the need to buy additional licenses, as you can effectively use fewer licenses to protect your entire infrastructure. Plus, the reassignment process is fast and easy, taking only a couple of clicks.
5. Various integration capabilities. Ekran System supports integration with any general-purpose SIEM system, helping you detect more cybersecurity breaches. You can also integrate Ekran System with some ticketing systems, such as SysAid and ServiceNow, and connect to Active Directory and other services.
Secure Active Directory with Privileged Access Management and Regular Audits
6. Customization and filtering capabilities. In addition to default templates and settings, Ekran System allows you to be more flexible by customizing reports and alert rules as well as changing system settings. Extensive filtering capabilities in monitoring recordings and reports help you concentrate on the factors that matter most at the moment.
7. Regular updates. Ekran System is constantly being improved to bring new capabilities and help you be more responsive to current cybersecurity challenges. We’re always open to your feedback and have a 24/7 technical support team ready to help you get the most out of deploying Ekran System.
Conclusion
Conventional IAM implementation methods are often rigid and ineffective. Layering new solutions on top of outdated IAM infrastructure is not the best way to secure your IT environment. An Agile methodology can help your IAM strategy advance by bringing in the necessary flexibility, efficiency, and responsiveness against the rapidly changing cyber threat landscape.
To build an identity and access management strategy that is Agile and dynamic, your organization needs a mindset shift towards a collaborative environment where everyone involved in IAM is willing to adopt a new methodology. The Agile approach requires iterative cybersecurity improvements, flexible planning, and a willingness to rapidly adapt and change. The transition requires time and commitment while promoting agility across your cybersecurity team and constantly reassessing the efficiency of your IAM strategy.
If you’re looking for a holistic solution to your cybersecurity needs, consider Ekran System. Our platform can make your organization’s IAM strategy more flexible and efficient while providing all the necessary IAM capabilities.
Download a FREE 30-day trial of Ekran System to see how your organization’s cybersecurity can become more Agile now!





