Multiple reports show that people don’t take the necessity to pick secure passwords for their login credentials and personal devices seriously enough. According to Verizon’s 2022 Data Breach Investigations Report, 80% of incidents resulting from hacking attacks involved weak and compromised passwords.
These findings make us wonder whether confirming a user’s identity just once at login is enough. Should this be a repeated procedure? And if so, how can we turn one-time authentication into a continuous process that ensures both strong data protection and an uninterrupted workflow? In this article, we review continuous authentication as a reliable method to securely authenticate users.
What is continuous authentication and what threats does it help to mitigate?
To develop a better understanding of what continuous authentication is, let’s review the main characteristics of secure authentication. There are three of them:
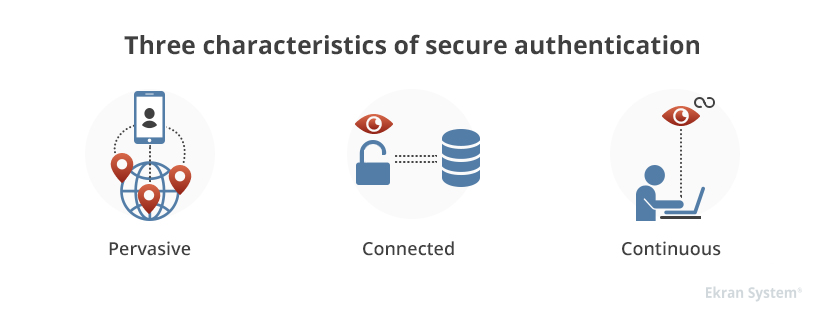

- Pervasive – access is secure across the network for all users, applications, and devices (both personal and corporate)
- Connected – information needed for protecting critical assets can be shared across the security ecosystem
- Continuous – authentication data is collected, analyzed, and acted upon continuously, not just from time to time
Continuous account authentication, or continuous risk-based authentication, is a verification method aimed at authenticating the user not just once but continuously throughout the whole user session. The main idea of continuous risk-based authentication is to deliver smart and secure identity verification without interrupting the workflow.
This method should be able to register unusual shifts in a user’s behavior and re-verify the user’s identity if needed. To do so, an identity and access management (IAM) solution with continuous authentication functionality should be able to:
- constantly collect information about a user’s actions and establish patterns of regular behavior
- learn to distinguish between normal and abnormal behavior of a particular user based on collected data
- grant access to the system or request additional user identity verification based on analysis of user behavior
At the same time, additional verification should only occur when there’s a real risk indicator so that users don’t waste their time repeating authentication procedures when they aren’t needed.
Brute Force Attack Detection and Prevention
When to use continuous authentication?
Continuous risk-based authentication can help you protect your organization from malicious attacks aimed at your employees’ login credentials. Cyber attackers can use a whole variety of means to compromise an organization’s accounts and enter internal systems unnoticed. Some of those means are the following:


Phishing is a social engineering attack that usually involves sending messages or emails to legitimate users with the intent of luring them into disclosing login credentials.
A brute-force attack is a trial-and-error method if finding the right login and password combination to enter a specific system.
Session eavesdropping is a way to steal valid login credentials by intercepting an ongoing login session.
A keylogger attack consists of sending a Trojan program to a user’s machine and, with its help, recording what the user inputs through the keyboard.
By detecting suspicious behavior and reverifying users’ identities, continuous authentication can help you ensure that perpetrators won’t stay in your systems long enough to cause significant damage.
Now let’s take a closer look at how continuous risk-based authentication works and what factors play a central part in this process.
Amazon WorkSpaces Session Recording
How does continuous authentication work?
Usually, you can verify a user’s identity with the help of one factor (single-factor authentication) or several factors (multi-factor authentication).
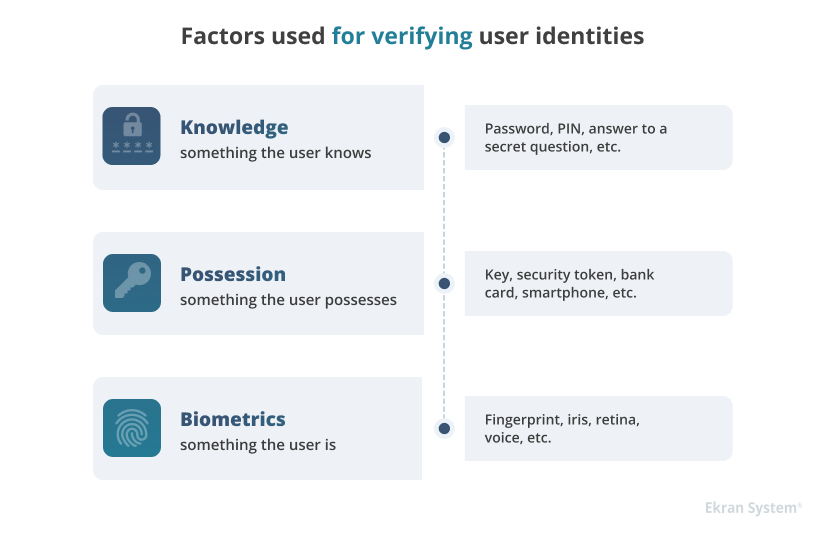

In contrast to these methods, continuous authentication also verifies a user by who they are. Instead of traditional biometrics such as retina and fingerprint scans, it uses so-called behavioral biometrics: patterns of user behavior that are unique for each person.
Here’s how continuous user authentication works in practice:
If you use the same device at the same location to log into the system, access the network at the same hours, and launch the same set of applications every day, the continuous authentication solution will recognize this pattern and allow you to access the system with a minimal number of verification procedures. But if you log in from a device that the IAM solution knows nothing about or try to access a critical application you’ve never used before, the system will re-confirm that you’re the person you claim to be.
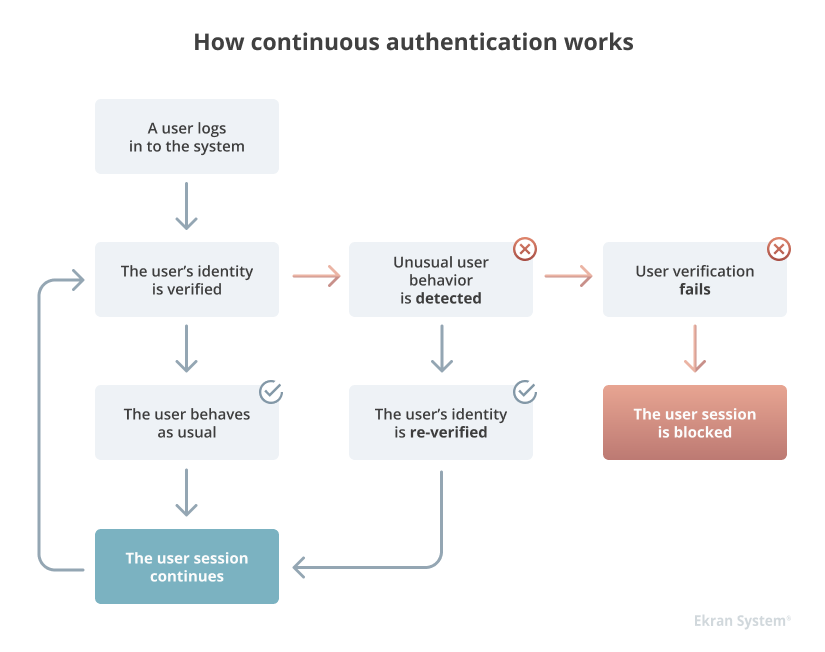

Behavioral biometrics uses machine learning technologies to continuously monitor a user’s behavior based on the user’s baseline behavior profile.
A baseline behavior profile is based on three categories of factors:
- Cognitive factors – eye-hand coordination, device interaction patterns, etc.
- Physiological factors – hand used (right or left), arm size, strength of key presses, etc.
- Contextual factors – location, time, device, etc.
In contrast to User and Entity Behavior Analytics (UEBA), continuous authentication using behavioral biometrics focuses not only on what a user normally does but on how they do it.
7 Cybersecurity Challenges to Solve with a UEBA Deployment
The most common example of behavioral biometrics is a keystroke pattern: Each person has their own speed and rhythm for typing on a keyboard, clicking a mouse, and tapping a smartphone.
Based on a user’s baseline behavior profile, the security solution can automatically and continuously check if there has been a switch of users for a particular device or web application. Such an approach allows for distinguishing actual users trying to access the system using someone else’s device or account from malware-like bots that use stolen credentials.
To deepen our understanding of continuous user authentication and its value for organizations, let’s compare it to another verification method – multi-factor authentication.
Continuous authentication vs MFA
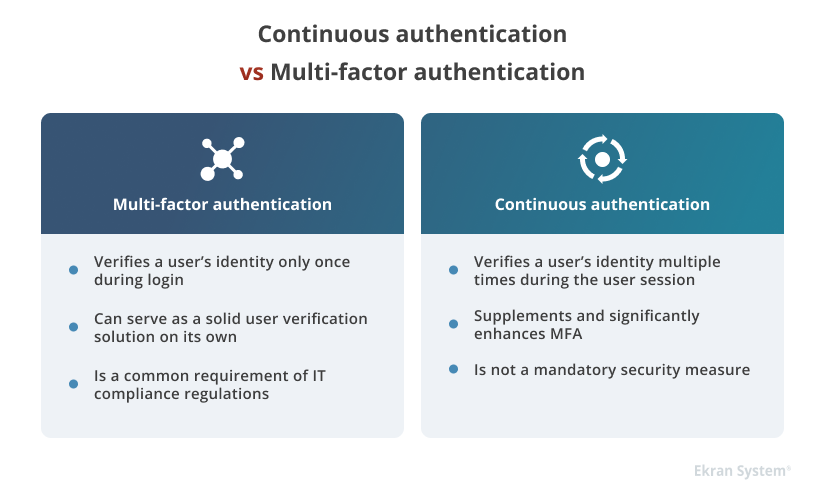
Continuous authentication should be viewed as a supplement to and not a substitute for multi-factor authentication (MFA). The main goal of any MFA solution is to confirm that the person trying to access the system is who they claim to be, thus adding an extra layer of security for protecting critical assets. However, a regular two-factor authentication solution won’t re-verify a user’s identity once the session is started.
Continuous user authentication is meant to fill this security gap and make user identity verification an ongoing process throughout the entire session. With the help of continuous authentication, you can mitigate the risk of someone getting hold of a specific device or application after a user’s identity has been confirmed and access granted.


Although continuous authentication often competes with MFA as an equal, it still can’t fully replace MFA as a security standard. It’s rather recommended to combine these two methods to enforce your organization’s cybersecurity.
Finally, from the perspective of compliance with standards, regulations, and laws such as PCI DSS, the GDPR, and HIPAA, multi-factor authentication is a must-have component for identity and access management. Adopting MFA is necessary for ensuring quality identity and access management and proper protection of your sensitive data.

Two-Factor Authentication (2FA): Definition, Methods, and Tasks
How Ekran System can help you ensure continuous user identity verification
Ekran System is an insider risk management platform with an extensive feature set for efficient identity and access management:
- Two-factor authentication (2FA) functionality allows you to verify user identities within your network by sending a unique one-time verification code to a user’s verified personal device.
- Secondary authentication can help you distinguish the actions of individual users working under shared accounts.
- An AI-based UEBA module [PDF] can help you detect signs of account compromise. Ekran System’s UEBA automatically compares each user’s actions with the user’s baseline behavior profile and notifies security officers about any suspicious deviations.
- Robust privileged access management capabilities enable you to granularly control access permissions for users and automate the management of secrets for passwordless authentication [PDF].
Additionally, with Ekran System, you can perform continuous user activity monitoring to keep a close watch on privileged and regular users’ actions. Ekran System enables you to configure a real-time incident response to efficiently detect and handle suspicious user actions and cybersecurity events. In addition, Ekran System’s extensive functionality significantly facilitates compliance with major IT security requirements.
5 Steps for Building an Agile Identity and Access Management Strategy
Conclusion
Continuous authentication is the method that has changed the way organizations authenticate users, turning it from a one-time procedure into an ongoing process. Adopting this method can significantly improve an organization’s security and reduce the risk of insider threats.
Machine learning and behavioral biometrics are the two main technologies that enable continuous user authentication.
While continuous authentication has become one of the best practices for IAM, this method should not be seen as a substitute for multi-factor and secondary authentication.
Our team constantly works on improving IAM services and other insider threat management capabilities of Ekran System to help you ensure a reliable level of cybersecurity in your organization.
Get a free 30-day trial of Ekran System and start your journey towards safer authentication today!





