Cybersecurity threats have been a headache for the hospitality industry for many years. When the COVID-19 pandemic turned this industry upside down, attempts to stay in business put many hotels in an even riskier position in terms of security. For instance, many organizations followed the example of hotels in Amsterdam that diversified their services and turned guest rooms into offices for remote employees. Such moves generated profit for the hotels but also created new vulnerabilities.
Changes in how hotels worked make their networks, internal infrastructure, and guest data more exposed to malicious activity. That’s why we decided to examine current cybersecurity challenges for hotels, explore insider threats examples, and offer eight practices to improve the security of your hospitality organization.
The pandemic created new cybersecurity threats for hotels
Hotels collect tons of sensitive information: financial records, credit card details, personally identifiable information (PII) of employees and guests. That’s why this industry has historically attracted hackers. After several massive and expensive data breaches affecting Marriott, Ritz, and Hyatt, hotels all over the world realized they must pay close attention to their cybersecurity.
The COVID-19 pandemic spurred a new spike of security attacks on hotels. Malicious actors tried to leverage the confusion in the industry and emerging security vulnerabilities to obtain more sensitive data. As hackers explore new ways to abuse hotel cybersecurity, you need to keep an eye on emerging risks and have a plan to mitigate their consequences.
Here are the key cybersecurity challenges hospitality organizations have been forced to deal with due to the pandemic:
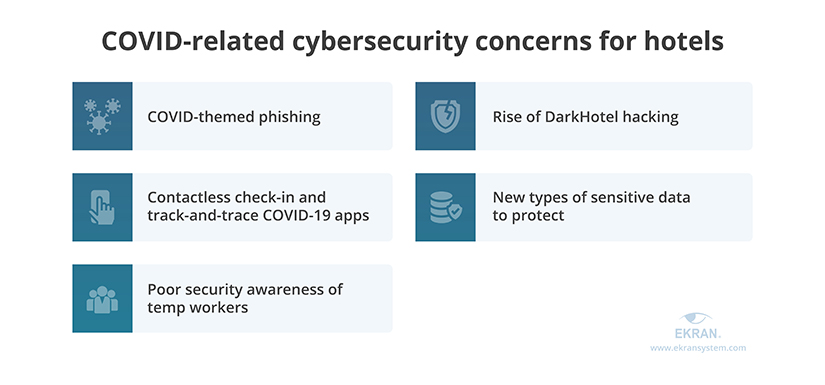

- COVID-themed phishing. Phishing attacks increased by 51% following the pandemic. Such attacks often lead to user account compromise and data leakage. For hotels, the risk of falling for a phishing attack has become much greater since hotels receive lots of COVID-related emails every week. It’s hard for hotel employees to stay focused and distinguish genuine emails from phishing emails.
- Rise of DarkHotel hacking. This type of hacking targets not hotels themselves but their top-ranking guests: C-level executives, business owners, government officials. Hackers obtain the travel itinerary of their target, hack into the hotel’s network, and deploy malicious code on the hotel’s server. When the guest connects to the unprotected hotel Wi-Fi, the hacker tries to steal sensitive information from their mobile devices.
- Contactless check-in and track-and-trace COVID-19 apps. To improve health protection, many hotels provide their guests with an option of contactless check-in using their phones. After checking in, guests may have to use some sort of track-and-trace mobile app to verify that they stayed in their rooms during quarantine. These activities expose hotels to the risk of identity fraud when a malicious actor impersonates a hotel guest. Also, connecting many mobile devices to the hotel network may expose it to malware attacks.
- New types of sensitive data to protect. Because of the pandemic, hotels have to protect new types of sensitive data. They need to store COVID-19-related medical records of their guests. Also, if a hotel provides additional services like offices for remote employees, they might need to take extra measures to strengthen data protection. Therefore, hotels must ensure the security of new types of data in accordance with HIPAA, GDPR, SWIFT CSP requirements, and other standards, laws, and regulations.
- Poor security awareness of temp workers. The issue of poor employee cybersecurity awareness became more pressing during the pandemic because many hotels had to part with their regular full-time employees and hire temps and part-timers instead. Providing new people with appropriate cybersecurity training is challenging for hospitality organizations, partially because these people often don’t stay long enough to learn new rules and security skills. Because of that, new employees are more susceptible to making errors and falling for user-oriented attacks like phishing and social engineering.
The combination of old and new cybersecurity threats makes the hotel industry extremely vulnerable to attacks from both outside and inside. Organizations that can’t adapt to the changes fast enough put their guests’ data at risk. Let’s take a look at several examples of hotel data breaches in 2021 and see what valuable insights they can give us.
5 Industries Most at Risk of Data Breaches
What can we learn from 2021 hotel data breaches?
There were many cybersecurity incidents in 2021. During the first nine months of 2021, US companies experienced more data breaches than during all of 2020. A lot of these breaches happened to hotels. Here are some of the most notable hotel security incidents and possible ways to prevent similar issues in your organization:
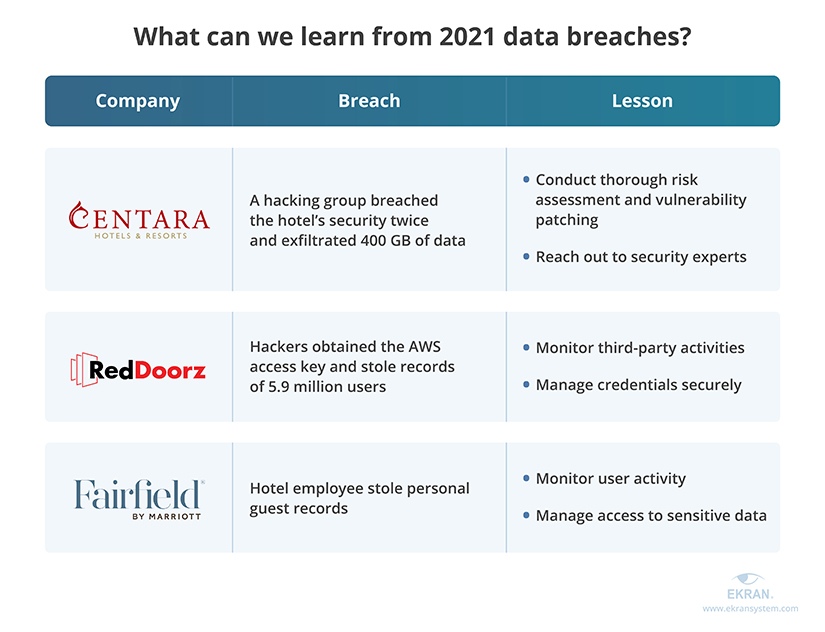

Centara Hotels & Resorts were hacked twice by the same group during October 2021. The Desorden hacking group gained access to the hotel’s sensitive data and demanded a $900,000 ransom. Centara Hotels & Resorts claimed they patched the vulnerability that allowed access and refused to pay. Within 10 minutes of this claim, hackers breached the hotel network again and exfiltrated 400 GB of personal guest records and the hotel’s corporate information.
Lesson learned: Rushing the risk assessment and vulnerability patching can lead to much more severe risks and losses than the security incident itself. Take time to make sure your organization has fully recovered from a data breach before making public statements about it. If you feel that your team lacks expertise, don’t hesitate to hire an outside consultant.
RedDoorz, a large booking service that works with hotels all over Asia, experienced a leak of 5.9 million records. Hackers discovered the AWS access key to the company’s database by digging through the RedDoorz application for Android, which was developed by a third party. Stolen records include users’ personal data like email, birth date, contact formation, and booking details.
Lesson learned: Review the activities of your contractors and make sure that they follow cybersecurity best practices. Also, make sure that credentials for your internal services and infrastructure are stored securely and can’t be accessed by an unauthorized user.
7 Third-Party Security Risk Management Best Practices
Fairfield Inn, a franchise owned by Marriott International, suffered an insider attack on its Shawnee hotel. In December 2021, the Fairfield Inn manager discovered that a hotel employee had stolen logs of guests’ personal information. During a police investigation, officers discovered that Lindsay Haley stole sensitive documentation from five different businesses and intended to sell it.
Lesson learned: While most of your employees deserve to be trusted, you have to keep your guard up in case some of them decide to go rogue. Make sure that you monitor employee activity and access to sensitive data and critical systems in order to quickly detect and stop a malicious actor.
Insider Data Theft: Definition, Common Scenarios, and Prevention Tips
How to secure your hotel’s data?
To withstand new security threats and challenges, you need to make sure that your organization’s cybersecurity system can deter, detect, and disrupt the risks and threats we discussed above. Your organization probably already has a lot of security controls. Reviewing your security system will help you analyze your strengths and weaknesses and get ideas on security improvements.
Let’s take a look at eight possible improvements and see which of them you can implement with Ekran System:


1. Assess new security threats and risks
Conducting a cybersecurity risk assessment is the first step towards building a solid data protection system. The assessment helps you discover new threat sources and events, security vulnerabilities, and their impact on your organization.
When searching for potential vulnerabilities and risks, take into account not only the history of security incidents in your organization but also:
- Incidents that have happened in other hotels
- Data breaches and security incidents of your contractors that have access to your data and systems
- Security controls described in NIST SP 1800-27 Securing Property Management Systems
- PCI DSS guidelines for protecting POS terminals and electronic payments
- Updated requirements of ISO 22483:2020
To speed up your risk assessment, you can analyze Ekran System logs and reports on past security incidents. They can help you define which risks are most common and dangerous.
2. Conduct security awareness training for all employees
Careless mistakes and a negligent attitude towards security rules can turn your employees from a valuable asset into a security vulnerability. Even without malicious intent, employees can hurt your organization by accidentally leaking their credentials, clicking on a phishing link, or uploading sensitive data to an unprotected cloud or USB device.
That’s why you need to develop a short, efficient, and comprehensive program of security awareness training. Having such a program in place helps you teach employees to:
- Securely work with your property management system (PMS) and guest data
- Recognize new types of phishing attempts
- Stop sharing access to the hotel’s resources if it can be avoided
- Keep an eye on suspicious activity of other employees and hotel contractors
Increased employee turnover makes the issue of poor security awareness even more pressing for hotels. To help your new employees and temps get up to speed, you can create handy materials and reminders on cybersecurity rules.
Ekran System provides you with records of past security incidents that you can use to educate your employees. Also, you can configure warning messages that will be shown each time a user violates your security rules. These messages will remind employees about the rules and explain their mistakes.
3. Establish employee activity monitoring
Monitoring the activity of your employees and contractors helps to improve your hotel’s cybersecurity in several ways:
- Detect security violations in real time
- Establish the context and intent behind malicious employee activity
- Use session records as evidence of security violations or an audit trail during forensic investigations
Ekran System provides you with a rich user activity monitoring (UAM) feature set that will keep you informed of any action on your protected endpoints. Ekran System captures the user’s screen coupled with multiple types of metadata from keystrokes to connected USB devices.
You can watch user sessions in real time or search for a particular event by any metadata record. This way, you’ll be able to review, analyze, and collect data on any event in your network.
4. Gain control over third-party activities
Hotels prefer to outsource non-core activities like the development of booking websites, PMS maintenance, and accounting. As an alternative to outsourcing, some hotels deploy ready third-party solutions like cloud services. Both options create lots of potential entry points inside the organization’s network. If left unprotected, these entry points can be abused by hackers or malicious contractors.
That’s why you need to secure and monitor the activity of third parties. With Ekran System, you can:
- Monitor how contractors interact with your data and systems
- Configure their access rights
- Verify the identities of third-party users
- Analyze third-party activity and detect security violations
5. Speed up security threat response
Detecting security violations by manually reviewing user activity is impossible for almost any hotel, where employees often work in shifts day and night. To keep threat detection and response swift, you can configure real-time alerts about suspicious user activity or deploy software that empowers you to respond to threats automatically.
For example, when Ekran System detects prohibited user activity, it sends an email with the link to the user session and a description of the event to the responsible personnel. Using it, a security officer can assess and stop the threat in real time. Then, the officer can either kill the process that breaks the security rule or block the user.
To protect your data from the most impactful risks, you can configure automated responses to particular user actions. In this case, Ekran System will kill the process or block the user the second it detects a violation.
Real-Time User Activity Alerts and Incident Response
6. Minimize and manage user access
Hotel employees often need access to several sensitive systems to do their jobs. For example, the receptionist has to be able to check bookings and payments, create and edit records about guests, and contact and coordinate hotel contractors. Some IT security managers simply assign such employees unlimited privileged access to hotel systems. It makes life easier both for hackers and malicious insiders, however, since they can access all your sensitive data without triggering the security system.
You can avoid this threat by configuring and managing access rights for all your users: employees, partners, contractors, etc. Allowing each user or user group to interact only with the resources they need greatly reduces security risks.
With Ekran System, configuring access rights is quick and simple. Our platform relies on a role-based access control method, so you can create groups for users with similar responsibilities and define which resources they can use. Changing group configurations or customizing them for a particular user takes only several minutes. Also, you can enable time-based access to your resources to prevent employees from connecting to your network outside working hours or approve access requests manually.
Lightweight Privileged Access Management
7. Automate user credential management
Obtaining legitimate user credentials allows malicious actors to bypass an organization’s cybersecurity system. And the combination of poor security awareness, high employee turnover, and susceptibility to phishing attacks make obtaining credentials of a hotel employee an easy job.
To prevent such incidents, you can deploy credential management software that will take care of user credentials for your employees and contractors. For example, Ekran System can automatically create, rotate, store, and dispose of complex user credentials. Our software also encrypts all credentials, so malicious actors won’t be able to obtain or guess your employees’ logins and passwords.
8. Protect shared and privileged accounts
Creating many shared and privileged accounts is considered a bad cybersecurity practice, but it’s nearly unavoidable for hospitality organizations. Hotels employ too many shift workers with shared accounts for their positions and contractors with elevated access rights.
Such accounts can pose a significant security threat if compromised by a malicious actor, but you can protect them with several mechanisms. For shared accounts, you can enforce secondary authentication with Ekran System. It makes an employee provide the password for a shared account and then provide personal credentials to confirm their identity. This measure makes hacking a shared account a lot harder even if the hacker knows the account password. You can also distinguish the activity of a specific user logged in under a shared account.
To protect privileged accounts, use Ekran System’s two-factor authentication. It helps you identify the person logging in to a privileged account by checking their credentials and sending an additional verification code to their previously verified phone number.
Conclusion
Hotels have always had to respond to cybersecurity challenges and events as fast as possible, which is a challenging task as it is. The pandemic has made it even tougher by creating new cyber risks and threats. As a result, hotels all around the world have to significantly change their cybersecurity posture in order to guarantee guest data protection.
You can protect your organization from new cybersecurity threats by re-evaluating your security risks and capabilities, detecting weak spots, and implementing needed improvements. To do it quickly and conveniently, it’s best to use software that provides you with all the necessary security controls in one place.
Ekran System is a full-cycle security risk management platform. You can use it to deter, detect, and disrupt security risks while saving time for configuring and integrating numerous tools. Try our demo or a 30-day trial to see how Ekran System will fit into your security infrastructure!





