Fear, uncertainty, and doubt (FUD) is no longer just another fancy blockchain-related term used to influence the public’s and investors’ opinions. This concept thrives in many fields, turning our attention to the problems of data, system, and operational security.
In this article, we discuss the FUD meaning in cybersecurity and how this concept works. We also overview ways you can use cybersecurity FUD to gain valuable insights for protecting your organization against today’s cyber threats.
Changing the perspective on FUD conversations
Fear, uncertainty, and doubt is a known manipulation technique that some businesses turn to in an attempt to control both prices and public opinions. This technique usually involves negative news, encouraging strong emotional — and thus less objective — reactions from the audience.
But what does FUD mean in cybersecurity?
It’s true that in the cybersecurity field, it’s easy to be influenced by FUD news. If we look at the latest cybersecurity reports, we’ll see that both the number and the cost of cybersecurity incidents are increasing. If we analyze some of the most recent incidents, we’ll discover that even large corporations with robust cybersecurity teams and extensive cybersecurity budgets often are unable to quickly react to changes. And seeing all this, we might find ourselves wondering whether there even can be such a thing as a flexible, bulletproof cybersecurity program for our organization.
So how to avoid FUD in cybersecurity?
We can take a look at the same concept from a little bit different perspective, turning these fear-mongering ideas into actionable questions:
- Fear — What can we learn from reports on recent cybersecurity incidents?
- Uncertainty — How can we adjust our cybersecurity measures to continuous changes?
- Doubt — How can we make our employees a cybersecurity strength and not a threat?


Let’s discuss in detail each of these questions.
Cyber Security in Hotel Industry: Pandemic Lessons and 8 Best Practices to Improve Data Protection
1. How can you use information about the latest cybersecurity incidents?
Knowledge becomes power, if you know how to use it.
Organizations fear the rising threat of cybersecurity incidents. The Ponemon Institute, IBM, Verizon, and others report the rising threat of leaks, breaches, and theft of sensitive data by different actors.
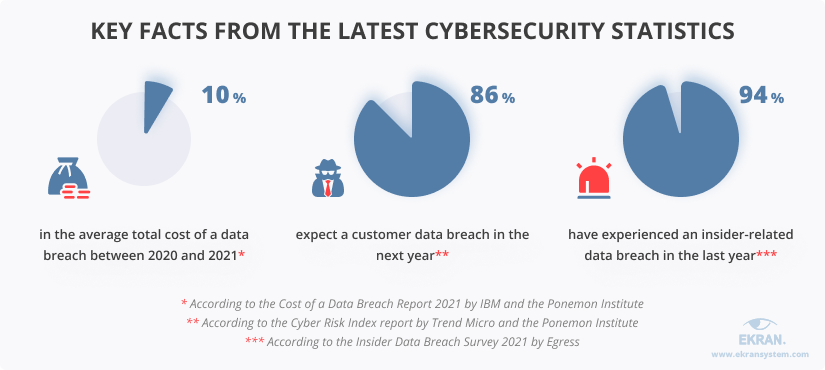
The Cost of a Data Breach Report 2021 by IBM and the Ponemon Institute shows that in just a year, the average total cost of a data breach increased by nearly 10%, from $3.86 million in 2020 to $4.24 million in 2021. Let’s take a look at some more interesting facts in the graphics below:


Do these disturbing statistics mean that we have to succumb to our fears? Of course not.
These reports can turn out to be really helpful and serve as insights for building your action plan. All you need to do is switch your focus from the events to the reasons behind them.
For instance, the Cost of a Data Breach Report 2021 names several common reasons for a data breach, among which are credential compromise, malicious insiders, and phishing attacks.
Same threat sources are mentioned in the Cyber Risk Index report, accompanied by threats like ransomware and negligent insiders. Finally, if we look beyond the numbers in the Insider Data Breach Survey 2021, once again, we’ll see that businesses are worried about phishing attacks and employee negligence. In addition, researchers outline the risk of data exfiltration as one of the biggest threats feared by businesses.
What can you do?
Knowledge is key. But knowing what your most critical servers, databases, services, and applications are is not enough to keep cybersecurity threats at bay. You also need to see who does what with your critical assets. Only then will you be able to both determine the true reasons behind a particular incident and respond to emerging threats in a time-efficient manner.
To do so, it’s best to implement a robust user activity monitoring solution that allows you to observe, record, and review all user actions on protected computers and servers.
With Ekran System being a full-cycle insider risk management platform, you get the power of real-time user activity monitoring and review. User sessions recorded by Ekran software are indexed with context-rich metadata that you can use for in-session search and filtering.
Another factor to pay special attention to is your knowledge of key cybersecurity risks related to your valuable assets. Conducting regular audits and risk assessments can help you determine which assets to secure first and from what risks and threats.
Insider Threat Risk Assessment: Definition, Benefits, and Best Practices
With Ekran System’s advanced reporting capabilities, you can generate custom reports both manually and upon schedule as well as export them in a tamper-proof format if needed.
Also, consider limiting access to your critical data and systems to only a small circle of people. This is where practices like the principle of least privilege, one-time passwords, and multi-factor authentication (MFA) can help you prevent malicious actors from getting a hold of your valuable data records and trade secrets.
Ekran System provides you with an advanced two-factor authentication feature leveraging true MFA principles.
Two-Factor Authentication (2FA): Definition, Methods, and Tasks
2. How can you adjust your cybersecurity measures to continuous changes?
Stay flexible to stay well protected.
Any organization can face situations like mergers and acquisitions, the emergence of new customer demands, changes in regulatory requirements, or a pandemic. Some are predictable, while others take place faster than we can react to them.
Particularly, the COVID-19 pandemic has brought a lot of changes to the way businesses operate. As a matter of fact, a study by Ladders predicts that by the end of 2022, the percentage of highly paid jobs that are remote will reach as high as 25% in North America alone. For comparison, before the pandemic, it barely reached 4%.
The key lesson we can learn from this is that changes are inevitable. And while office workers continue turning into teleworkers, business executives and security officers are left uncertain about what to protect, from whom, and exactly how.
The shift to remote work due to COVID-19 alone has brought a lot of cybersecurity challenges:
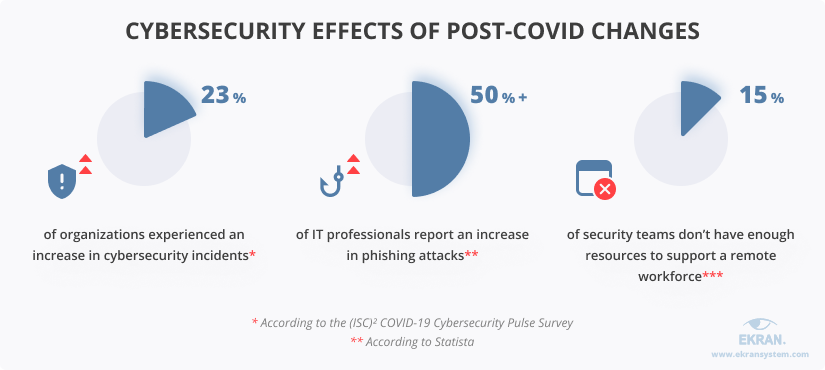


In order to maintain a high level of data and operational security, you need to stay flexible and learn how to adjust on the go.
Remote Employees: How to Manage Insider Risks
How can you make your security more flexible?
Many organizations are already moving from having a single tightly secured cybersecurity perimeter to targeted protection of the most critical assets, implementing approaches like zero trust and just-in-time privileged access management. As stated in the Cost of a Data Breach 2021 report, data breaches cost $1.76 million less for organizations with a mature zero trust architecture compared to those who haven’t deployed any zero trust measures.
Why Do You Need a Just-in-Time PAM Approach?
You may also join the zero trust movement and use Ekran System to set granular access permissions, limiting access to a particular asset to a specific role, a group of users, or even a single user. For even stronger protection of critical resources, the Ekran System platform provides you with robust manual access approval capabilities.
Along with taking appropriate proactive measures, consider improving the ways your organization responds to cybersecurity incidents. Once you perform the thorough cybersecurity audit and risk assessment we talked about in the previous section, you’ll have enough insights to prepare an incident response strategy for relevant types of incidents and educate your people on it.
Incident Response Planning Guidelines for 2022
Ekran System allows you to set custom alerts and notifications to notify your security professionals about a potential threat in real time. You can also configure the platform to block a suspicious user, process, or application to automatically disrupt a potential attack at an early stage.
Last but not least, dedicate some of your time to monitoring industry news and the most recent reports from industry leaders like the Ponemon Institute, Forrester, and Garter. In this way, you’ll be able to keep up with both the latest cybersecurity trends and the newest cybersecurity threats to protect against.
Real-time user activity alerts and incident response
3. How can you make your employees a cybersecurity strength and not a threat?
Join forces with your people.
Malicious insiders aside, we can outline two key insider-related risk factors for organizations working in post-pandemic times:
- Lack of cybersecurity awareness
- Insider negligence
Many cyberattacks are based on the victim’s unawareness of the risks and threats that may come from a single email, website link, or colleague’s request. For example, 73% of organizations had experienced a phishing attack in the year prior to the Insider Data Breach Survey 2021. A recent research [PDF] has outlined eleven factors that influence a person’s decision to reply to an email. We’ll focus on the four most common and dangerous ones:



All respondents who participated in the above mentioned research believed that if an email comes from someone they know, has all the expected logos, a usual title and body, and no links inside, then the chances are high that the email is safe. The reality, however, shows that none of these factors guarantee the safety of an email, and your employees must know that by heart.
Another common threat comes from ransomware, where a single mouse click may lead to losses ranging from $70 to $1.2 million. In 2020 alone, ransomware was involved in 10% of all data breaches according to the 2021 Data Breach Investigations Report by Verizon.
Take a people-centric approach to cybersecurity.
Deploying powerful and flexible cybersecurity tools is important. But to build a future-proof cybersecurity system, you’ll also need to join forces with your employees in this cybersecurity battle against fear, uncertainty, and doubt.
It’s important that your employees and subcontractors know what cybersecurity risks are relevant for your organization. But it’s even more important that they understand how their actions might lead to these risks and what they can do to avoid letting theoretical threats turn into real-life disasters.
People-centric Security for Remote Workers
You need to dedicate enough time and resources to raising cybersecurity awareness among your employees and conducting comprehensive cybersecurity training on a regular basis. This is especially important when the COVID-19 pandemic has forced many organizations to completely rebuild their operational routines and make a drastic shift to remote work.
You can also collaborate with your employees in securing your most valuable assets and establishing new, safe workflows.
As example material during training, you can use Ekran System’s monitoring records. Also, the Ekran platform allows for customizing user notification messages so you can not only prevent your employees from violating your cybersecurity rules but also educate them on those rules.
Insider Threat Awareness: What Is It, Why Does It Matter, and How Can You Improve It?
Conclusion
In times when we are challenged with a continuously changing threat landscape and the need to adjust to hybrid work environments, it’s crucial to not let fear, uncertainty, and doubt cloud your mind.
Use information about FUD in cybersecurity to enhance your cybersecurity routines. Focus on the practices most relevant to your industry and business. Put effort into building strong collaboration with your employees to efficiently mitigate risks related to both employee negligence and insider threats. As an insider risk management platform and a privileged access management system, Ekran System will help you take care of the technical side of the process.
Leverage Ekran System’s rich user activity monitoring, access management, and incident response processes to keep your cybersecurity system flexible and efficient.





