Intellectual property (IP) is crucial for manufacturing organizations to compete in the market. At the same time, IP may be a target for dishonest competitors, former employees, and cybercriminals. That’s why it’s vital to take all possible measures to protect the security of intellectual property in the manufacturing sector.
In this article, we dive deep into the topic of protecting intellectual property in manufacturing and provide you with nine time-proven practices to improve cybersecurity for manufacturing companies.
Manufacturing industry and information security
The manufacturing industry leverages raw materials, labor, machinery, tools, and biological or chemical processing for the production of goods or their components.
Manufacturing organizations are traditionally divided into two groups depending on who they produce goods for.

- Contract manufacturers are organizations that sign agreements with other organizations to produce parts, components, or whole products for brands.
- Brand product companies handle everything from product manufacturing to marketing and product distribution under the brand name, by themselves or with the help of contract manufacturers.
Organizations operating in the manufacturing sector deal with lots of sensitive data – both their own and their business partners’.
Why data protection is a must for manufacturing organizations
The COVID-19 pandemic was a tipping point for manufacturers. The manufacturing industry wasn’t prepared for a massive switch to remote work and faced a 300% increase in cybersecurity attacks in 2020. Additionally, the manufacturing industry became the top target of cyber attackers in 2021 according to IBM’s 2022 Threat Intelligence Index.
The reason why the manufacturing industry is so attractive to cybercriminals is that manufacturing organizations often store and process the personal and financial data of their employees and clients. But even more importantly, these companies store confidential information about technologies they use during manufacturing, product designs and formulas, and other unique know-how.
The loss of employees’ or customers’ personal data and financial information, or organization’s intellectual property assets can lead to significant reputational and financial losses.
10 Data Security Best Practices: Simple Steps to Protect Your Data
Intellectual property in the manufacturing industry
According to Gartner, intellectual property includes assets that pertain to original and novel creations of the human intellect, such as patents, copyrights, and regulatory licenses. Intellectual property is protected by law to prevent others from using your creations and inventions without your permission.
Types of intellectual property in manufacturing
There are four common types of intellectual property in the manufacturing sector:


- Patents – A patent confers the legal right to own a specific invention and fully manage who can use, produce, or sell the invention, as well as how they can do so. In exchange for disclosing your invention to the world, you get up to 20 years of patent protection and the ability to license the use of your invention by others.
- Trademarks – A trademark is any recognizable phrase, symbol, or design that denotes and differentiates your product from others. Registering a trademark can prevent others from using your recognizable insignia, disguising themselves as your organization, and misusing your reputation.
- Copyrights – A creator’s right to original work that allow those with the creator’s authorization to reproduce, distribute, and display the work. Although a copyright is usually applied automatically, it’s recommended to register for a copyright to have an advantage in court in case someone unlawfully uses your creation.
- Trade secrets – These are any practices, processes, patterns, or information you apply within your organization that are unknown outside the company. These assets are commercially valuable and give you a competitive advantage.
While patents, trademarks, and copyrights are publically available to people outside organizations, trade secrets are confidential and are the most vulnerable. Since trade secrets carry critical economic value, consider appropriately protecting intellectual property in manufacturing from both internal and external malicious actors.
Who should you protect your intellectual property from?
Knowing the threat source is the first step to securing manufacturing intellectual property. Manufacturing organizations need to be aware of these three groups:

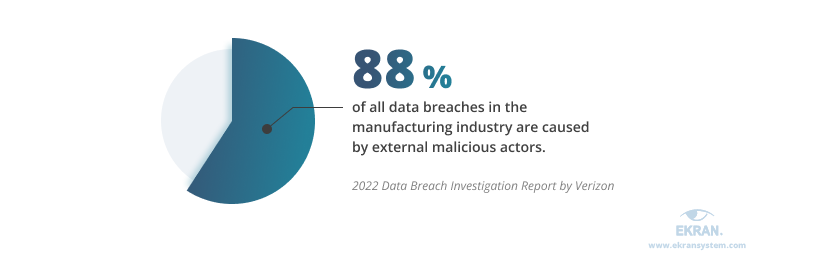
Outside attackers are external malicious actors trying to access your organization’s valuable data. Most often, such actors aim to receive financial gain by getting a ransom from the victim or selling information to a third party.
Outside attackers cause the majority of data breaches in the manufacturing industry according to data from Verizon.

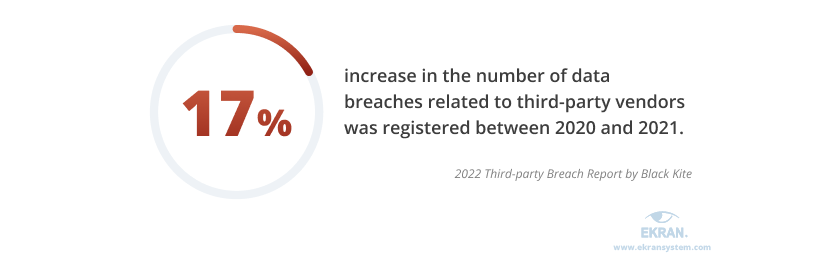
Business partners are vendors, suppliers, and other third parties that you cooperate and share intellectual property with. Malicious actors can leverage gaps in your partners’ cybersecurity to get access to your intellectual property. Besides, third parties you work with might also want to obtain your sensitive data and technology secrets.
Although third-party security incidents are not as common as malicious attacks from the outside, the number of third-party threats has grown in recent years.

Employees can be in-house or remote. Malicious or disgruntled employees may want to appropriate your intellectual property to get revenge or to gain an advantage in the hiring process at one of your competitors. However, insiders can put your intellectual property at risk even without realizing it. Carelessness, a lack of cybersecurity awareness, and reluctance to follow security rules can cause critical data loss or compromise.
The Ponemon Institute’s findings show that employee negligence causes far more security incidents than malicious insiders.
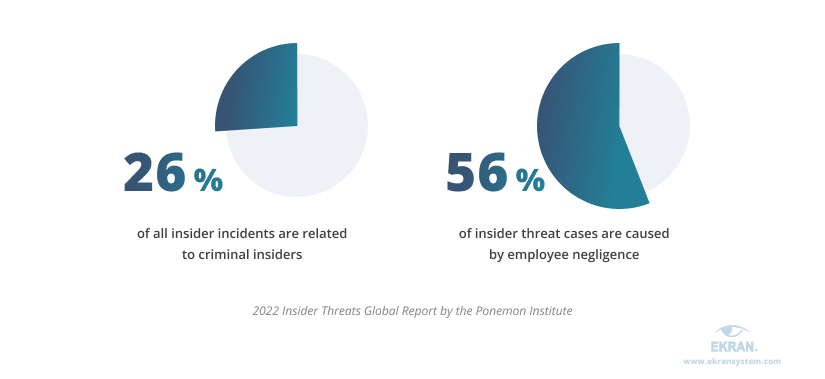

Now that we know about the most common threat actors that can endanger intellectual property in manufacturing, let’s see what means they often use to carry out their malicious activity.
Mitigating Insider Threats: Plan Your Actions in Advance
Common cyber threats to intellectual property
To minimize the risks of intellectual property theft and compromise, you need to know about the means malicious actors use to obtain your organization’s critical assets. When you know what to be aware of, you have a higher chance of identifying and mitigating a particular threat in time.
There are several types of cybersecurity threats to intellectual property in manufacturing:
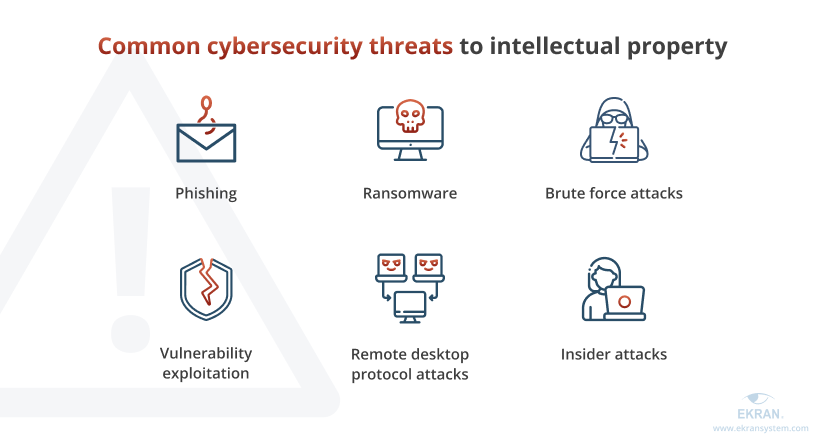

Phishing is a social engineering attack performed through email or another communication channel that lures an organization’s employees to provide sensitive data, such as access credentials. Phishing messages are usually in the guise of emails sent from legitimate users, colleagues, or even C-suite members.
7 Best Practices to Prevent Intellectual Property Theft
Ransomware is a type of malware that encrypts a computer’s files and demands a ransom for the decryption key. Malicious actors using ransomware can also steal data and threaten to disclose it or sell it to a third party.
Ransomware attacks account for 23% of all attacks on the manufacturing sector according to IBM’s 2022 Threat Intelligence Index. Ransomware attacks are only possible when computers within your organization’s network are infected. Most commonly, attackers send phishing emails with malicious links or attachments or use employees’ stolen credentials to infect your network.
Brute force attacks utilize a trial and error method to crack login credentials or decryption keys and eventually get access to an organization’s systems and networks.
During a brute force attack, hackers try numerous usernames and passwords until they successfully log in to your internal systems under a legitimate account. The worst-case scenario is when a malicious actor gets access to an account with privileged access permissions, as it will enable them to easily compromise your most valuable assets.
Protect User Credentials and Manage Access Rights to Prevent Brute Force Attacks
A vulnerability exploitation is an attack where cybercriminals take advantage of software or network vulnerabilities or security flaws to get access to your data. After a successful attack, cybercriminals can run malicious code in your network and steal your critical data.
Cybercriminals are always searching for security gaps and flaws and ways to exploit them. Eventually, vulnerabilities in your organization’s network, software applications used by employees, and even devices within your office can lead to data leaks and intellectual property compromise.
Remote desktop protocol (RDP) attacks are cybersecurity attacks executed through RDP connections, aimed at remotely taking full control over a compromised computer or network.
It may be hard to identify RDP attacks in the system because they’re difficult to distinguish from the actions of legitimate users. Due to that, malicious users may remain unnoticed for a long time, giving them more opportunities to get hold of your organization’s sensitive data.
Insider attacks are a type of threat that can come from any user inside your network. Insiders can be malicious or negligent, compromising your critical data intentionally or by mistake.
Insider threats are more dangerous than external threats since insiders often hold legitimate access to your sensitive data and know your cybersecurity measures well, making it easier for them to bypass those measures and steal or damage your data.
7 Best Practices to Prevent Data Theft by Departing Employees
The list of possible cyber attacks that pose a significant risk to your intellectual property is not limited to those mentioned above, so it’s critical to keep an eye out for suspicious activity.
In the next section, we dive deeper into how to prevent intellectual property theft in a manufacturing firm.
9 Best practices for protecting intellectual property in the manufacturing industry
Reliable protection of intellectual property requires a well-thought-out holistic approach. Ekran System is a full-cycle insider risk management platform that can help you implement such an approach in a manufacturing organization.
Ekran System can help you safeguard your organization’s intellectual property in combination with the following nine best practices:
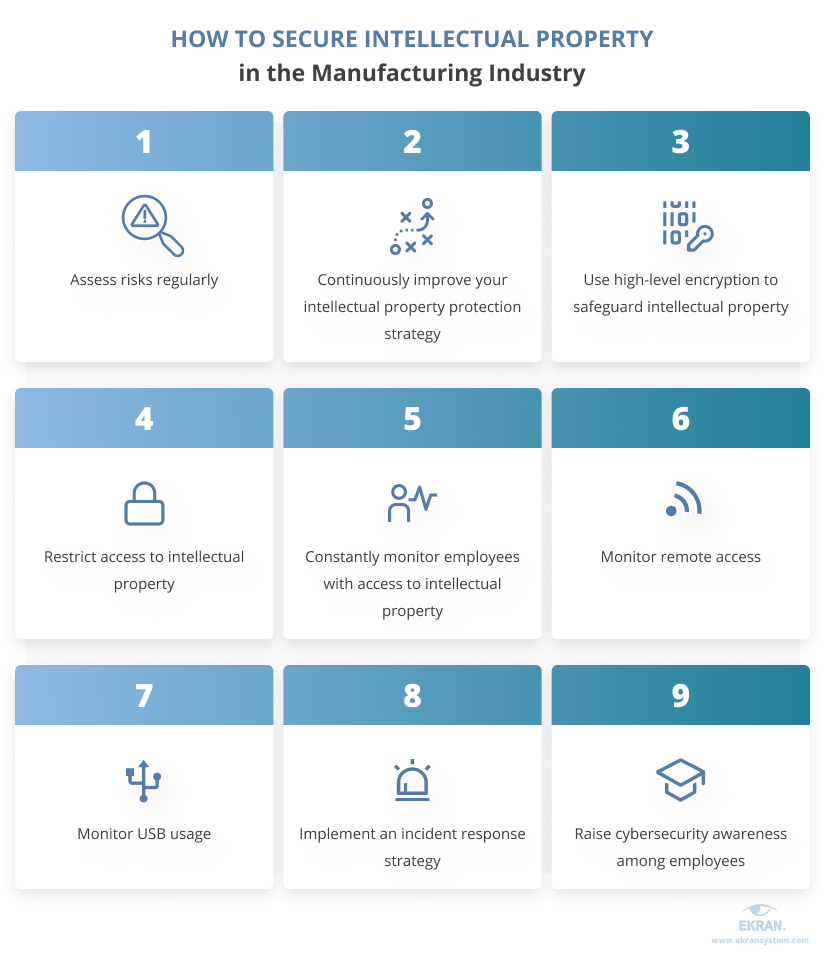

1. Assess risks regularly
Consider performing a thorough risk assessment to identify and prioritize possible risks to your intellectual property. A detailed risk assessment can help you make informed decisions on protecting intellectual property and preventing the loss of critical data.
When performing a risk evaluation and assessment, you may rely on recognized risk assessment guidelines, such as the NIST Cybersecurity Framework.
A crucial point to remember is that you must regularly conduct cybersecurity risk assessments to yield results. Consider implementing a periodic risk assessment review in your organization to keep pace with ever-evolving cybersecurity threats.
Ekran System’s advanced reporting and auditing functionality can help you keep abreast of potential risks. You can enhance your auditing process with a set of customizable reports to get meaningful insights into how your employees and third-party vendors work with your organization’s intellectual property.
2. Continuously improve your intellectual property protection strategy
Once risks have been identified and prioritized, you can develop a solid plan to effectively address and minimize them.
Your intellectual property protection strategy will require regular updates. As new risks to your intellectual property arise and you reassess risk priorities, you will need to adapt your cybersecurity strategy to reflect those changes.
Refining your intellectual property protection strategy after each risk assessment session is a good rule of thumb.
3. Use high-level encryption to safeguard intellectual property
Data encryption can help protect intellectual property in manufacturing. When encrypted, your sensitive files are only accessible to those individuals holding the decryption key.
Consider using high-level encryption that meets the Advanced Encryption Standard (AES) specification established by NIST to ensure the security of your intellectual property.
4. Restrict access to intellectual property
When access to intellectual property isn’t limited across your manufacturing organization, safeguarding such assets is hardly possible. Provide access to your intellectual property only to a limited group of employees and business partners.
Ekran System’s Privileged Access Management (PAM) capabilities can enable you to grant access to intellectual property to specific users, roles, and groups of users. You can provide individuals with temporary access credentials, specify the expiry date for particular permissions, and much more.
5. Constantly monitor employees with access to intellectual property
Consider implementing privileged user monitoring procedures to closely watch how your employees and subcontractors handle your intellectual property. You can also benefit from user and entity behavior analytics (UEBA) tools to get notified about employees’ abnormal activity.
In addition to UEBA functionality, Ekran System provides an extensive set of robust features for user activity monitoring (UAM) and privileged user monitoring (PUM) to ensure a high level of control over all users across your network. Ekran System offers lightweight user session video recording, keylogging, and more.
7 Cybersecurity Challenges to Solve with a UEBA Deployment
6. Monitor remote access
The activity of third-party vendors and remote employees should also be closely monitored. Consider deploying software that will allow you to monitor and log SSH and RDP sessions in your organization’s network.
Ekran System provides you with remote employee and third-party vendor monitoring tools and allows you to closely watch all live and recorded remote sessions to secure your valuable digital assets. Ekran System also enables you to receive real-time notifications and generate informative reports on remote user activity.
7. Monitor USB usage
Controlling and monitoring USB devices can significantly lower the chances of intellectual property theft and compromise.
Make sure you can block and whitelist specific USB devices. Consider implementing procedures for requesting access in cases when an employee tries to plug in a suspicious USB device.
Ekran System lets you granularly monitor ongoing USB connections and manually block or allow new connections. With Ekran System’s USB monitoring functionality, you can also create rules to automatically monitor, permit, or prohibit the use of particular USB devices.
How Can Ekran System Protect You against Infected USB Devices?
8. Implement an incident response strategy
Despite all your effort, you can hardly prevent each and every security incident in your organization. That’s why it’s critical to maintain a reliable incident response procedure. The procedure should define people assigned to respond to a detected incident and list actions they need to perform.
Ekran System’s real-time user activity alerts allow you to automate incident response in your organization. You can take advantage of an extensive library of default alerts and notifications or create custom ones. The AI-powered UEBA module in Ekran System can also automatically detect and quickly respond to suspicious user activity that doesn’t correlate to baseline user behavior.
Additionally, Ekran System allows you to export recorded user sessions in a protected standalone format for forensic investigation.
Incident Response Planning Guidelines
9. Raise cybersecurity awareness among employees
Lack of knowledge among employees about cybersecurity and the need to keep critical data (particularly intellectual property) safe can add to the risk of data compromise.
Regularly conduct training for employees to educate them about the most common cybersecurity threats and ways to detect and prevent them.
With the help of Ekran System, you can make your awareness training more tangible and effective. Session recording functionality enables you to gather real-life examples of malpractice and threat prevention cases for demonstration. In addition, you can configure custom warning messages in case of rule violations, allowing your employees to learn from their mistakes as they work.
Insider Threat Awareness: What Is It, Why Does It Matter, and How Can You Improve It?
Conclusion
Intellectual property is what gives your manufacturing organization a competitive advantage and differentiates it from others.
Developing and accumulating intellectual property assets may require months or even years of hard work. It may take significantly less time for malicious actors to steal or compromise your intellectual property if your protection mechanisms are not reliable enough.
With Ekran System, you can successfully implement the aforementioned best practices to secure your intellectual property.
Request a 30-day free trial to see how Ekran System can help you enhance the protection of your manufacturing organization’s valuable data.





