Your organization most likely has privileged users — employees, subcontractors, and even customers who are authorized to access critical applications and sensitive data. But those elevated access rights make an organization vulnerable. If a privileged user makes a mistake or an attacker gets access to a privileged account, your most valuable data is at risk. According to the 2021 IBM Security X-Force Insider Threat Report [PDF], privileged accounts were related to at least 80% of insider-caused security incidents that X-Force responded to between 2018 and 2020.
In this article, we go over the five most common human errors in cybersecurity made by privileged users. We also explore the reasons why people tend to make these mistakes and offer advice on how to prevent privileged users from making mistakes that cause inadvertent insider threats.
The danger of privileged users’ mistakes
People make mistakes. The problem is that even unintentional actions can cause serious damage to your organization. For instance, if one of your employees inadvertently causes a data breach, your company might lose not only sensitive data but also money and reputation.
Insiders who inadvertently harm their organization are responsible for 56% of all insider threat cases according to the 2022 Cost of Insider Threats Global Report [PDF] by the Ponemon Institute.


Privileged users are either humans or system-related identities: applications, programs, or processes. But while machines and applications do what they’re programmed to, people don’t always play by the rules.
Privileged users’ ignorant and negligent behavior when accessing your organization’s critical resources can lead to negative consequences:
- Loss or leaks of sensitive data
- Сrashes of critical processes
- Operational disruptions
You should be aware of the most common mistakes made by privileged users to avoid such negative consequences. With this knowledge, it will be easier for you to establish efficient privileged user management, which is required by HIPAA, NIST 800-63 password guidelines, and other cybersecurity standards, laws, and regulations.
8 Poor Privileged Account Management Practices and How to Improve Them
5 unintentional mistakes of privileged users
Some privileged users don’t know or don’t understand the true importance of following cybersecurity policies. Others break the rules to simplify or speed up routine processes without thinking about the consequences.
Let’s take a look at five common mistakes of privileged users.
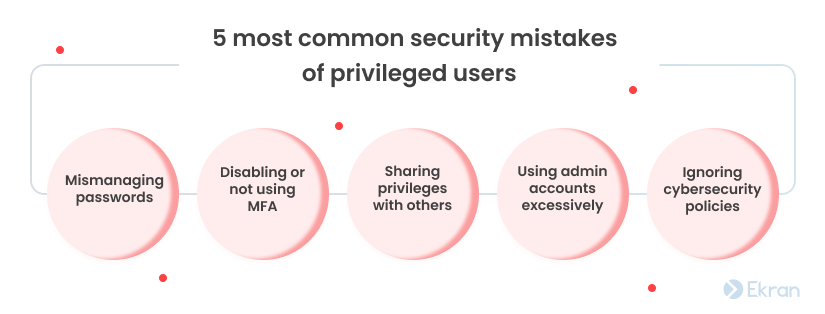

1. Mismanaging passwords
Passwords are the keys that protect your sensitive data, systems, and applications from intruders. There are many recommendations for securely managing passwords, such as using complex passwords and regularly updating them. But while many people know about these recommendations, few bother to follow them.
Here are the five most common password management mistakes to watch for in your privileged users’ daily routines:
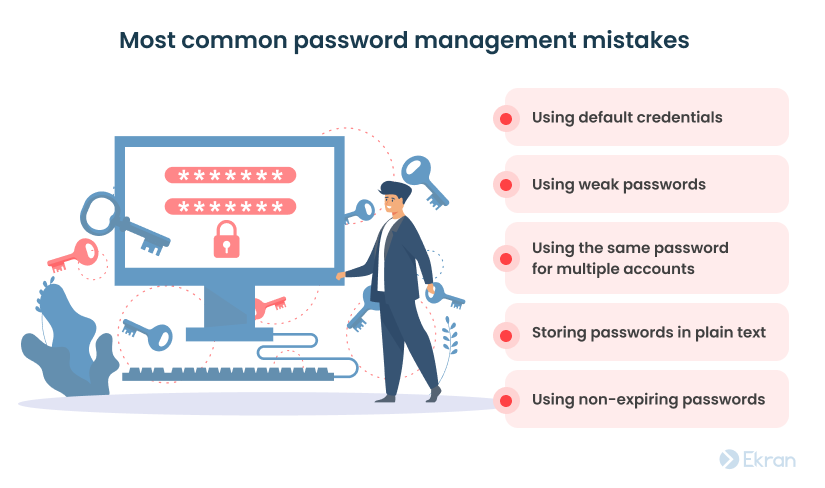

- Using default credentials. Some organizations may still use the word “admin” as both the login and password to the sysadmin account. Default credentials make your privileged accounts vulnerable to brute-force attacks.
- Using weak passwords. Weak passwords are usually short (six symbols or fewer) and easy to guess (names, birthdates, phone numbers, and so on).
- Using the same password for multiple accounts. If a reused password gets compromised, attackers will get access to all accounts it was used for.
- Storing passwords in plain text. Storing passwords in unencrypted text files is never acceptable. The moment someone gets access to that file is often the beginning of a large data breach.
- Using non-expiring passwords. Using the same password for a long time increases the risk of privileged account compromise. Password management best practices recommend rotating passwords every three to six months.
A robust password policy combined with regular employee training on password security can help your organization minimize the number of mistakes.
How to Identify and Prevent a Brute Force Attack
2. Disabling or not using MFA
Multi-factor authentication (MFA) is the cybersecurity gold standard of our times. This technology protects your sensitive data from unauthorized access much better than a password alone by adding more verification layers to the authentication process.
Cybercriminals can steal or guess a password, but they can’t trick an MFA mechanism that easily.
The problem is that sometimes privileged users can disable additional authentication measures. They might not want to use MFA because they don’t understand its true importance or feel like waiting for a verification passcode is a waste of time.
Without MFA, your sensitive data loses a crucial layer of protection. Consider enforcing additional authentication measures for all users and make sure to explain their value.
Two-Factor Authentication (2FA): Definition, Methods, and Tasks
3. Sharing privileges with others
Ideally, privileges should be granted only to those who need them, when they need them, and only after the approval of your cybersecurity officer. But in real life, colleagues often share privileged account credentials without a second thought.
Another common scenario is when a team shares one admin account to manage an application, website, or cloud storage service because creating an extra account would cost additional money.
When it comes to privileged user activity, visibility is essential. If you have two or more people using the same account, you can’t actually tell who did what. So if data is compromised or something stops functioning the way it should, you won’t be able to tell who is responsible.
A solution to this issue is to create personal privileged accounts wherever possible. If you can’t provide each privileged user with their own account, try to add more visibility to actions performed under a shared account. Secondary authentication can help with this.
Top 10 Mistakes of Security Officers in Protecting Remote Workplaces
4. Using admin accounts excessively
When people use privileged accounts more often than needed to do their job, it can increase your organization’s vulnerability. For example, an employee can stumble upon an email with malware attachments or a compromised website trying to launch a malicious script. If they do so while being logged in to an account with elevated access rights, the consequences can be severe.
It’s a common practice to distinguish privileged user accounts from regular accounts and never use privileged accounts to perform day-to-day tasks. That’s why employees in many companies have several accounts with different access permissions assigned to each.
Even if you make this practice a part of your security policy, there’s a chance that privileged users will ignore or sabotage it. In such cases, consider deploying a password management tool. Such tools allow you to limit the time for which privileged accounts can be accessed and forcibly log users out of accounts with elevated privileges.
7 Best Practices to Secure System Administrators’ Privileged Accounts
5. Ignoring cybersecurity policies
No matter what rules you specify in your organization’s cybersecurity policy, you’re likely to find someone who disobeys them. People don’t follow these rules for different reasons:
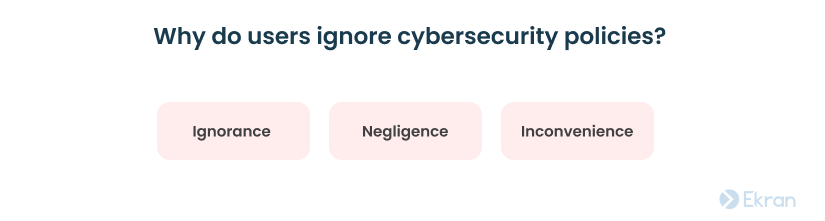

- Ignorance – Some of your employees or subcontractors may be unaware of specific rules and recommendations. Sometimes, people don’t even know there’s a cybersecurity policy they should follow.
- Negligence – People may know the rules but not understand why following them is important.
- Inconvenience – Sometimes, people choose to ignore cybersecurity policies because following them slows down their work or complicates their daily tasks.
For instance, users may break rules by using solutions or devices that aren’t allowed by the organization’s IT department. These may be cloud services, file sharing applications, messengers, and devices that are outside of the organization’s ownership and control. Such solutions are called shadow IT.
Another way of breaking rules is using employees’ own devices for work. Many organizations implement a bring your own device (BYOD) policy, allowing employees to use personal devices for their jobs. However, the key to benefiting from BYOD lies in close cooperation with the organization’s IT department. If your company’s IT department isn’t aware of devices used by employees with access privileges, there’s no way they can manage and secure them.
Consider conducting regular cybersecurity awareness training to communicate the importance of cybersecurity measures and make your privileged users more willing to follow your organization’s security policy.
10 Must-Have Information Security Policies for Every Organization
How can you prevent mistakes of privileged users?
Minimizing the risk of negligence on the part of privileged users and preventing your regular employees from turning into inadvertent insider threats is essential for your cybersecurity. Let’s explore a few best practices for securing system administrators’ accounts that will help you achieve that goal:
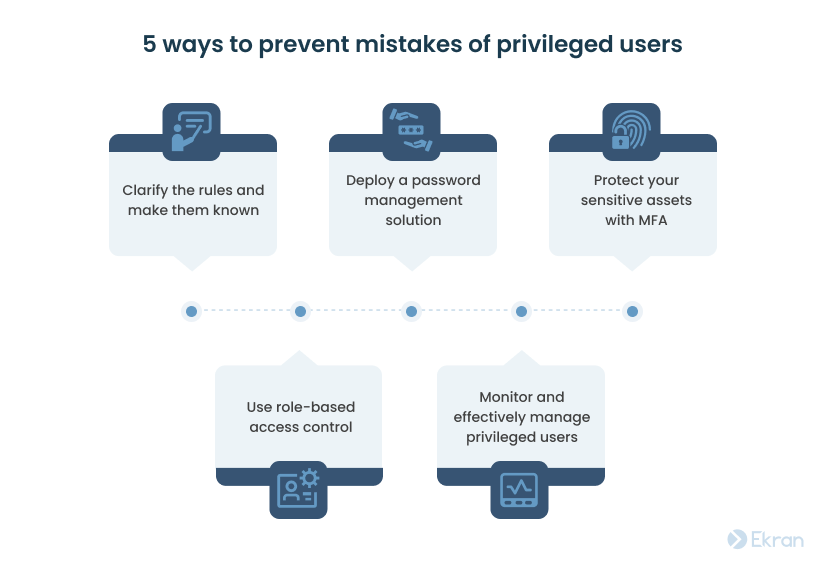

1. Clarify the rules and make them known. Start with specifying the rules for every process your privileged users are involved in. Then educate your employees and subcontractors on these rules. Make sure people know the rules and understand why it’s important to follow them. Educate both regular and privileged users to improve your company’s overall cybersecurity.
2. Deploy a password management solution [PDF]. Consider using a dedicated password management tool or service alongside specifying rules for password use in your cybersecurity policy. Look for a solution that allows for securely storing, managing, rotating, and revoking passwords.
3. Protect your sensitive assets with MFA. Make MFA mandatory for the most important and valuable resources in your company. But don’t overdo it, as increasing the number of required identity verifications can frustrate and inconvenience your employees.
4. Use role-based access control (RBAC). Define specific roles within your company and assign granular access rights to each. In this way, you can effectively implement the principle of least privilege and make sure that people in your company have just the right privileges to do their jobs.
To discover more about this access control model, you can read our detailed article on what is RBAC and ABAC.
5. Monitor and effectively manage privileged users. Watch your privileged users closely so you can see who did what and quickly respond to possible incidents. Look for privileged user activity monitoring or session recording software that allows for monitoring and logging of privileged user sessions. Being able to set custom alerts and automatically terminate suspicious processes and accounts would also be useful. Further, consider implementing a privileged access management (PAM) solution to granularly control access of privileged users.
Privileged Access Management vs Privileged User Management: What’s the Difference?
Ekran System is the ultimate insider risk management platform that provides your organization with all it needs to:
- Add granularity to privileged access management
- Increase the protection of privileged accounts
- Add visibility to actions taken by privileged users
- And do much more
Conclusion
Privileged users have access to the most valuable data and services, making them a key target for cybercriminals. Besides that, like all human beings, they are prone to making mistakes.
To prevent privileged users from making the mistakes we have described in this post, you may want to first create a comprehensive cybersecurity policy and educate your employees and subcontractors on it.
To secure your organization, you may also consider deploying a dedicated solution like Ekran System that has multi-factor authentication, privileged access management, privileged user monitoring, user activity monitoring, password management [PDF], and other insider risk management functionality. This will help you quickly detect potential threats and mitigate them before they cause harm.
Request a free trial of Ekran System today and prevent privileged users’ mistakes from escalating into real threats to your organization’s security.





