When faced with a cybersecurity threat, few organizations know how to properly handle the incident and minimize its impact on the business. Having a well-designed incident response plan (IRP) in place can save your organization time and resources on incident remediation.
We can get you started with building an efficient IRP. Read this post and create an IRP that fits your organization’s needs using the best practices from the NIST incident response framework.
Incident response plan: what it is and why you need one
Most organizations are not prepared for incident response. Only 26% of organizations globally have a cybersecurity incident response plan that they consistently apply across the organization according to IBM’s Cyber Resilient Organization Study 2021. As for the types of attacks organizations are prepared for, the same study found the following:


What is an IRP?
An incident response plan (or program), or an IRP, is a set of written instructions enabling a timely response to data breaches, insider threats, and other cybersecurity incidents. An IRP elaborates measures to detect and identify an incident, respond to it, mitigate its consequences, and ensure it won’t reoccur.


Why is it important to have an incident response plan?
Any cybersecurity incident can take an unprepared organization by surprise, and recovering from such an incident can drain lots of time and resources. Conversely, the presence of response plans indicates a developed cybersecurity culture in an organization.
Having an IRP is highly recommended for businesses of all sizes.
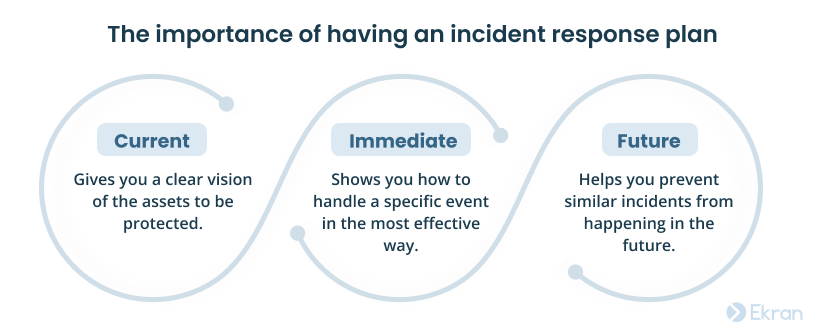

Here are seven reasons you should have an incident response plan:
1. Get ready for emergencies — It’s vital to have a thought-through incident response process ahead of time, as security incidents occur without notice.
2. Coordinate cybersecurity efforts — An IRP makes it possible to immediately determine who should do what during an incident.
3. Resolve incidents promptly — Written procedures can reduce the time it takes to fully remediate an incident.
4. Reduce the damage — Shorter response times limit the perpetrator’s ability to cause critical damage to your sensitive assets.
5. Cover security gaps — The process of developing an incident response plan helps to reveal flaws in your organization’s security measures and address them in advance.
6. Collect critical knowledge — An IRP helps your organization preserve knowledge and experience of dealing with an incident to prevent future occurrence.
7. Comply with cybersecurity requirements — Having incident response procedures is a requirement of many cybersecurity standards, laws, and regulations.
Alerting and Incident Response
Checklist to create an incident response plan
Consider the following ten recommendations to build or check your organization’s IRP:
| Recommendations for building an incident response plan |
| 1. Specify the main incident response requirements that you need to follow (NIST, HIPAA, PCI DSS, etc.) along with business-related requirements (response times, recovery strategies, etc.). |
| 2. Conduct a security audit to identify weaknesses in your company’s security posture that you can immediately address. |
| 3. Define what a security incident is. Your employees need to know what events are considered security incidents, how to define their severity, etc. |
| 4. Establish your incident response team and detail team members’ roles and responsibilities at all stages of incident response. |
| 5. Include a comprehensive communication plan. Your IRP must specify whom to call first in case of an incident, when to call them, and whom to contact if they’re unavailable. |
| 6. Plan procedures to address security incidents your organization is most likely to face or has faced in the past. Then expand the scope of covered security incidents little by little. |
| 7. Diversify your IRP by adding levels of possible data breaches, levels of incident severity, types of affected endpoints, etc. |
| 8. Plan recovery scenarios. Incorporate backup solutions and specify system and data recovery procedures to follow after a security incident. |
| 9. List authorities to whom you need to report incidents in your organization. For instance, the GDPR and California’s SB1386 require issuing a public notification in case of a data breach. |
| 10. Improve your IRP based on previous incidents. Once you’ve handled an incident, analyze it in depth to update your current IRP with more effective response strategies, procedures, and scenarios. |
Cybersecurity Incident Investigation
Some organizations use templates to make their own incident response plans. Below are a few ready-made templates and examples of other organization’s IRPs for reference:
It may be tempting to copy-paste another organization’s cyber incident response scheme and just change names. However, an IRP must take into account each organization’s unique goals and problems to be effective. Please use these templates and IRPs only as a point of reference and examples to learn from.
Now, let’s consider a popular incident response guideline to follow and see how to create an incident response plan for your organization.
Data Breach Response and Investigation: 8 Steps for Efficient Remediation
NIST guidelines for building an incident response program
The National Institute of Standards and Technology (NIST) provides a series of guides that your organization can use as a baseline for building your incident response program.
In particular, you can follow recommendations of the Computer Security Incident Handling Guide, 800-61 Revision 2, to effectively manage a potential cybersecurity incident.
According to NIST guidelines for incident management, an incident response plan should include the following phases:
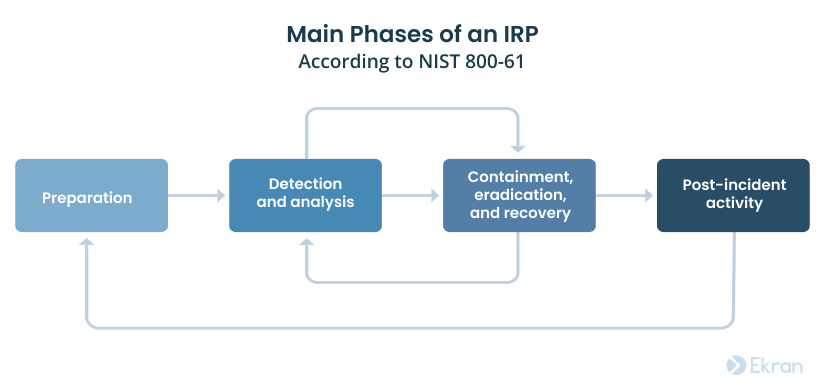

Preparation
An organization should be ready to deal with a cybersecurity incident before it happens and plan response procedures in advance. The preparation phase also includes planning what to do to prevent a data breach or attack from happening in the first place.
Detection and analysis
An organization must be able to detect cyber incidents and have tools and technologies in place to collect, document, and analyze data relevant to an incident. To make this task a bit easier, NIST specifies eight attack vectors and lists the most common signs of a cybersecurity incident. We’ll discuss them in detail in the next section.
Consider analyzing and prioritizing each incident according to the estimates of the incident’s business impact and the time it takes to recover.
Containment, eradication, and recovery
An organization must be able to effectively handle an attack, remove the threat, and start recovering affected systems and data.
At these phases, it’s also important to gather evidence about the incident to use later both for resolving the incident and in legal proceedings.
Post-incident activity
After successfully handling a security incident, an organization should use information learned from the incident to improve its current IRP.
The best thing about the NIST cybersecurity framework is that it’s both flexible and adaptive, so it can be efficiently implemented by large enterprises as well as small businesses.
Let’s see how to build your own NIST-compliant IRP.
Meeting NIST Compliance Requirements
Tips for implementing a NIST-compliant incident response plan
We have condensed pages of detailed NIST incident response guidelines into a compact checklist of five best practices:
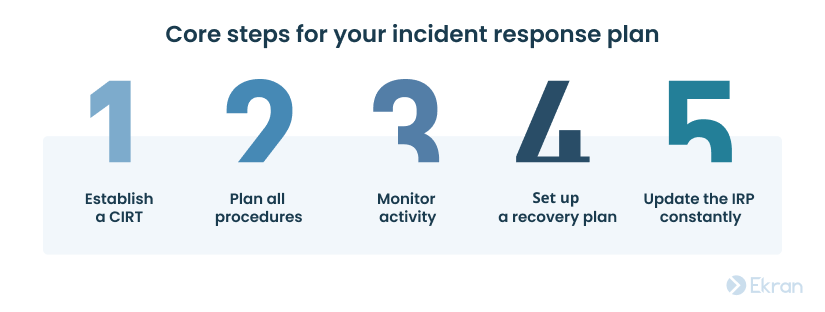

1) Establish a cybersecurity incident response team
Or at least choose responsible personnel.
No matter the size of your organization and the field you work in, the first thing to do when creating an incident response plan is to build a cybersecurity incident response team (CIRT).
A CIRT is responsible for coordinating key resources and team members during a security incident to minimize the impact of an incident and restore all operations as quickly as possible.
The main functions of the CIRT are to:
- Define incident response policies and procedures
- Handle cybersecurity incidents in a timely manner
- Investigate and analyze previous incidents
- Create incident reporting capability and establish necessary communications
- Train staff and raise awareness about cybersecurity threats and their mitigation
- Improve the current incident response program
As for members of the incident response team, consider the following:
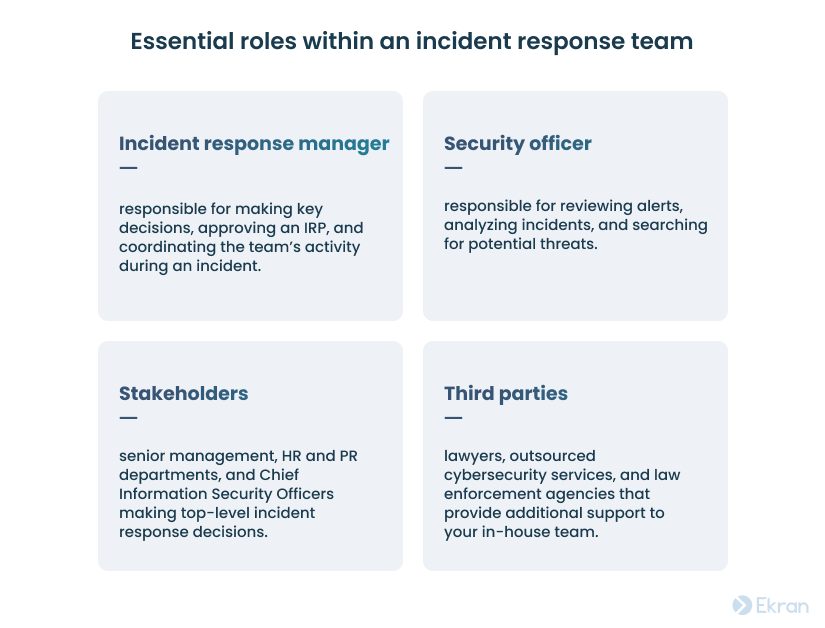

The number of CIRT members depends on the size of the company and the threats it may experience. No matter how large your CIRT is, make sure it’s trained and ready to act at all times.
2) Plan all procedures in advance
Planning is vital.
Should a cybersecurity incident take place, your CIRT needs to know exactly how to handle it with minimal losses. You need to compose and battle-test your security incident response plan before any real-life incident occurs.
Your incident response team needs to accomplish four main tasks at the planning stage:
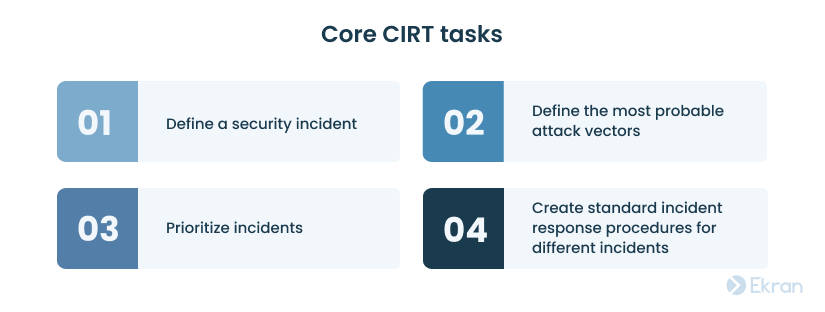

First, determine what events are considered cybersecurity incidents. Then, consider writing an incident response plan for each type of incident.
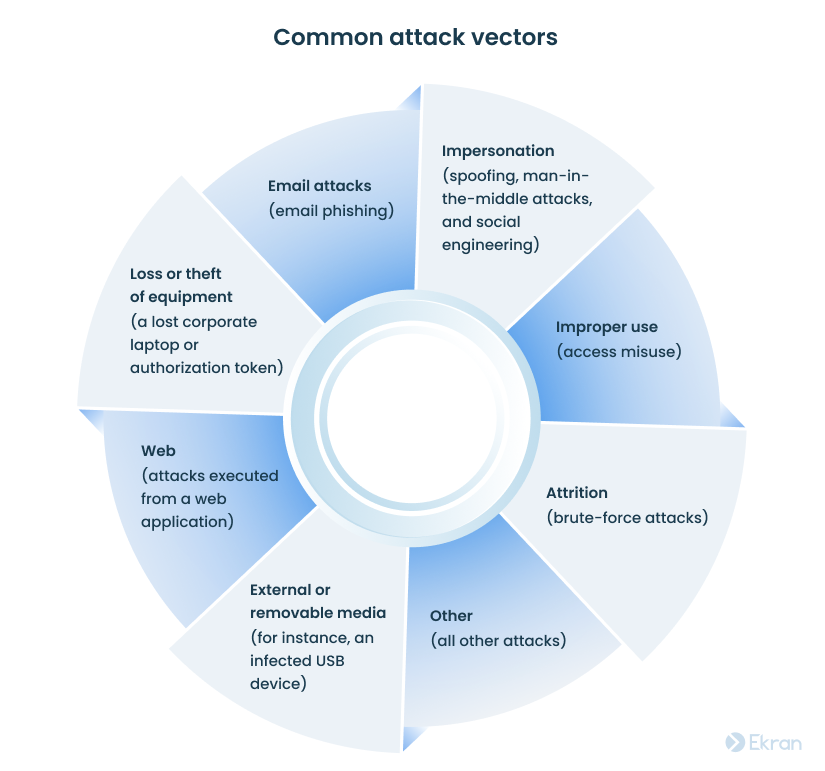
The Computer Security Incident Handling Guide by NIST specifies a list of attack vectors and suggests developing a common incident response scenario for incidents that use the same attack vector.
Among common attack vectors are:

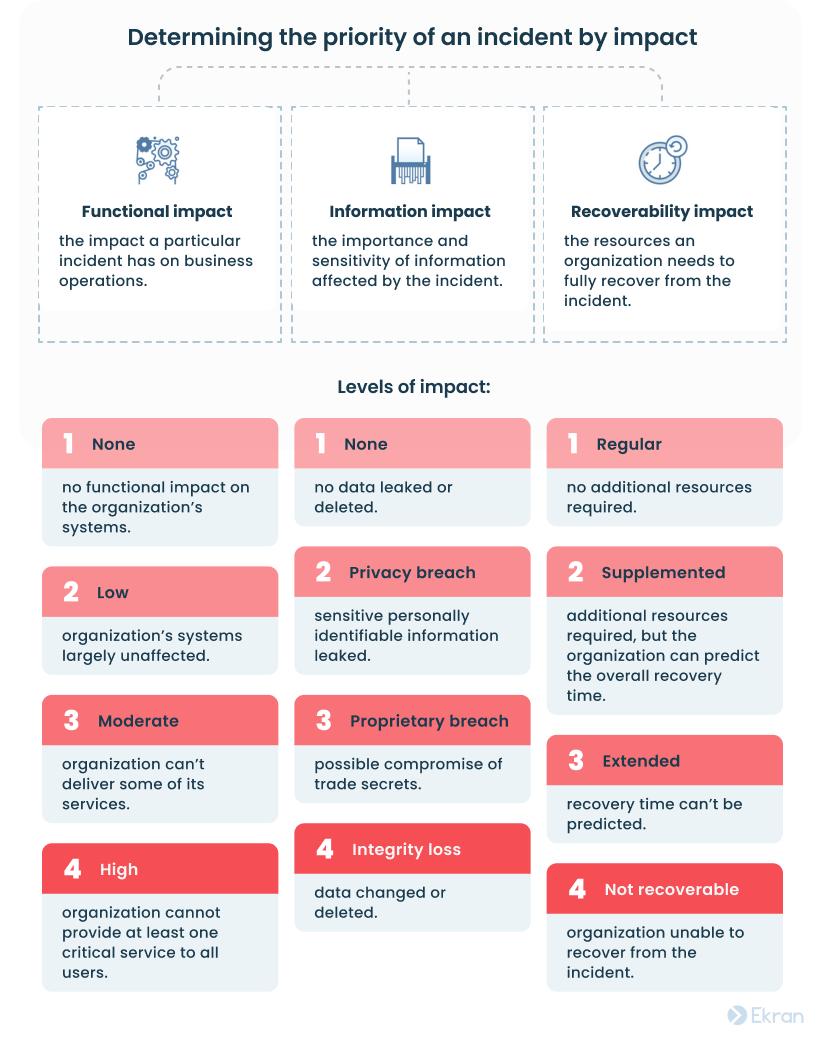
Next, prioritize possible threats and attacks based on their impact on your business. After all, there’s no sense wasting time on managing minor attacks when a critical breach remains unaddressed.
The NIST incident response framework offers three impact-based criteria for determining an incident’s priority:

Once you prioritize possible incidents, it’s time to start planning standard procedures for responding to them. Consider developing containment strategies and standard operating procedures (SOPs) for the most common events, such as system failures, denial of service, intrusion, and spyware infection.
In an SOP, specify the technical processes, techniques, checklists, and forms for the CIRT to use in the event of a particular incident.
You can refer to NIST Special Publication 800-86, Guide to Integrating Forensic Techniques into Incident Response, for further guidance on establishing proper response procedures.
3) Monitor user and network activity
If you can see it, you can manage it.
Monitor everything that happens in your network to prevent potential attacks. Consider deploying a user activity monitoring solution to address the problem of insider threats and subcontractor-related security risks.
By keeping an eye on the activity of individual users and entities in your network, you can:
- Detect and terminate an attack at an early stage
- Collect evidence and valuable data for further analysis
When choosing a user activity monitoring solution, look for one with a flexible incident response system. Being able to set custom alerts and automate at least some SOPs will help you ensure a timely response to cybersecurity incidents.
Consider implementing a solution with user and entity behavior analytics (UEBA) functionality. AI-powered technology can automatically detect deviations from baseline user behavior, indicating early signs of account compromise or insider activity.
Also, consider limiting access to sensitive data by deploying identity and access management solutions.
Major Supply Chain Cybersecurity Concerns and 7 Best Practices to Address Them
4) Take care of backups and recovery strategies
No one wants to lose valuable data.
A recovery strategy is a key part of any IT incident response plan.
As with handling an incident, it’s better to think about recovering from an incident before any breach happens and compose detailed data recovery procedures for different scenarios.
Start with determining what data is most valuable to your business and take additional care about its protection. This will let you know what to focus on during a real-life cybersecurity incident: what data you’ll need immediately and what assets can be restored later without causing damage to the business.
There are two major tasks for your CIRT to keep in mind regarding the organization’s recovery from a cybersecurity attack or data breach:
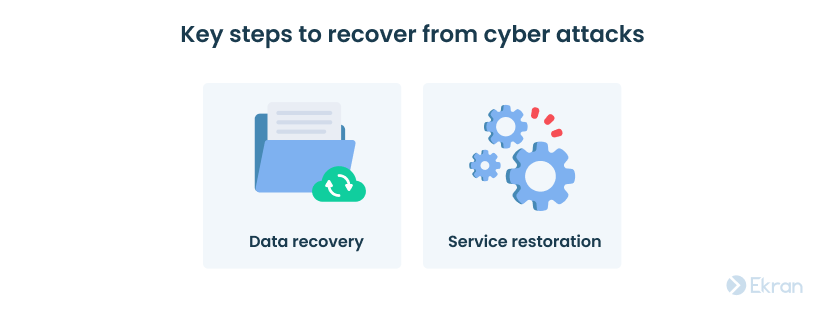

Data recovery. It will be difficult to quickly counter a cybersecurity incident without a backup system. Deploying a data loss prevention tool and regularly creating backups will help you safely restore all business-critical information.
For better protection of critical data, choose a hybrid backup solution combining on-premises and cloud-based services.
Service restoration. The following two steps are critical for restoring your organization’s systems to a normal state after an incident:
- Check your network to confirm that all systems are operational.
- Recertify as operational any systems or components that might have been affected during the incident.
Make sure to reset passwords for users of breached accounts and block accounts and backdoors that could have enabled the intrusion. For maximum protection, you should also follow other NIST password guidelines.
5) Update your incident response plan regularly
There’s always room for improvement.
NIST suggests reviewing an IRP at least once a year. However, new cybersecurity threats necessitate that organizations (especially large companies) check and update an IRP more frequently.
Consider mirroring any significant business changes in the IRP, be it entering a new sphere or changing your internal infrastructure.
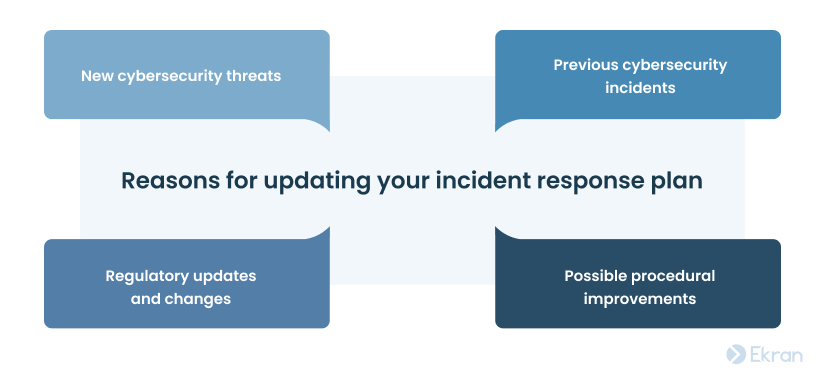

If your organization is a potential target for a new cybersecurity threat, it’s important to prepare an adequate incident response scenario for this type of attack. Plan, test, and document all procedures and recovery tools related to the new threat.
Examining how your organization and other companies handle real-life incidents is also essential. Such analysis can show you if your current strategy works well and what you can do to prevent such future incidents.
Handling incidents with Ekran System
Consider enhancing your IRP measures with dedicated incident response solutions.
Ekran System is a universal insider risk management platform that combines reactive and proactive approaches to handling user-related incidents.
| Ekran System’s proactive approach decreases the probability of incidents by allowing you to: | Ekran System’s reactive approach helps you detect and respond to incidents by enabling you to: |
| Manage access of privileged and regular users in your infrastructure | Receive alert notifications about users’ suspicious activity and view live user sessions |
| Monitor user activity of your employees and any remote users connecting to your system | Stop suspicious activity that triggered an alert by killing an application or blocking the user |
| Secure and manage passwords of all users in your organization | Leverage the AI-powered UEBA module to automatically detect and respond to abnormal user behavior |
This is just a selection of the features Ekran System has to offer. Among other things, you can use Ekran System as USB device management, user activity reporting, security incident investigation, and remote session recording software.
Ekran System helps you meet the most important IT compliance requirements, including those imposed by NIST, HIPAA, and PCI DSS.
Meeting IT Compliance Requirements
Conclusion
Incident response planning is an integral part of a successful cybersecurity strategy. Instead of using IRP templates, consider building a customized incident response plan that reflects your organization’s specific requirements. This way, you’ll be able to respond to any incident quickly and minimize possible damage.
Use our selection of tips and best practices inspired by NIST for your organization’s incident response. Build a cybersecurity incident response team, plan their actions in advance, monitor user activity, establish backup and recovery procedures, and don’t forget to update your IRP regularly.
Robust cybersecurity solutions like Ekran System help you boost and automate your incident response capabilities.
Start a free 30-day trial to test Ekran System’s incident response features in your organization now!





