A low level of insider threat awareness among employees can cause all sorts of cybersecurity issues: user negligence and risky behavior resulting in cybersecurity incidents, non-compliance with critical regulations and industry standards, etc. Installing insider threat detection software and establishing stricter rules can’t always protect an organization from these threats.
In this article, we discuss what insider threat awareness is, explain why it’s important to raise the level of awareness among your employees, and offer you six best practices to conduct efficient awareness training.
What is insider threat awareness?
Security officers go through lots of effort to secure sensitive data from insider threats and attacks, and then… life happens. Someone emails financial details to the wrong recipient or ignores a policy because it seems inconvenient to them. According to recent insider threat research, human error or negligence are the top reason of insider threat security incidents.
To avoid such incidents, you need to both fine-tune cybersecurity software and educate employees on the security risks of their actions.
Insider threat awareness refers to employees’ knowledge of insider-caused security risks and threats and employees’ alertness to these threats. It’s one of the pillars of the people-centric approach to cybersecurity. This approach promotes forming a cybersecurity culture in the organization and shifting the attention of security officers from machines and software to people.
But how can insider threat awareness prevent insider threats?


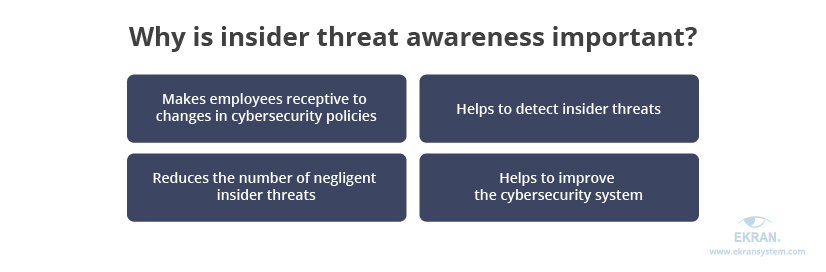
Why is it important to be aware of insider threats?
Employees with a high level of insider threat awareness enhance an organization’s cybersecurity because they:
- Support implemented security tools and procedures. User activity monitoring, access restrictions, and strict password management procedures can stress out employees if they don’t understand the reasons to implement these practices. Even more, they might think the employer doesn’t trust them and look for a way to trick the cybersecurity system. Employees that are aware of insider risks are more receptive to changes in security procedures and the implementation of new tools.
- Always follow cybersecurity rules. According to the 2020 Cost of Insider Threats Report [PDF] by the Ponemon Institute, 63% of insider threats are caused by employee or contractor negligence. Raising awareness using examples and by showing the possible consequences of negligent mistakes makes employees and contractors more careful and reduces the number of security incidents.
- Are wary of insider threats. When employees know specific indicators of insider threats, they’re more likely to notice them. Some alerts raised by employees will surely be false. On the other hand, employees can detect suspicious activity even before software does.
- Help to improve the cybersecurity system. Employees interact with an organization’s cybersecurity tools every day and undoubtedly know if there’s a way to trick them. If employees are aware of the possible consequences of exploiting such cybersecurity loopholes, they will provide security officers valuable insights on how to improve the current system.

How to raise the level of insider threat awareness?
The best way to improve employee awareness of insider threats is to conduct relevant training. For organizations compliant with HIPAA, NIST, SOC 2, and several other laws, regulations, and standards, conducting such training is obligatory.
Insider threat awareness training has several key goals:
- Improve employee awareness of insider threats, their main indicators, and possible consequences
- Teach employees how to respond to particular insider threats
- Change employee behavior towards cybersecurity
Such training can be arranged as part of an insider threat management program or as an independent educational program. Below, we share six best practices to prevent insider threats with insider threat awareness training.
Ekran System’s IT Compliance Capabilities
6 best practices for conducting efficient insider threat awareness training
Lots of organizations treat insider threat awareness training as a formal necessity to achieve compliance. This approach isn’t the most efficient if your goal is to truly enhance cybersecurity by educating your employees. Here are several best practices for insider threat awareness training:


1. Define the audience and scope of training
The first thing to do before starting a training course is to define who you need to educate. Different types of employees need different training: regular users need a general understanding of insider threats and risks, while system administrators and security officers require an in-depth course.
Also, define which types of security incidents are most common in your organization. You can also prepare different examples for each user group depending on the most common violations.
Then, focus the training on widespread user errors or security rule violations. Make sure employees not only learn the rules mechanically but understand why these rules are important and how violating them can harm the company’s cybersecurity.
2. Choose the type of training
There are three common ways to conduct insider threat awareness training. Each requires a different amount of resources and has a different aim. You can also combine these types of training to achieve the best possible result.


Training with an instructor is suitable for employees that don’t know much about insider threats. An instructor can adjust the training course to the audience, answer questions, and verify that the audience truly understands the importance of insider threat protection.
This type of training is the most time-consuming. You’ll need to prepare an instructor or hire one and schedule group meetings with employees that require training.
Training with software involves quizzes, tests, and attack simulations that help employees check their knowledge of insider threat protection. This type of training only fits employees who already have a general understanding of insider threats and need to verify and test their skills.
Software-based training requires fewer resources, as you can use not only paid software but also some free tools. Also, you don’t need to arrange group meetings, as each employee can pass the tests at their convenience.
Training with documentation is passive training based on the use of memos, instructions, mailouts, etc. It’s only efficient for employees that have deep knowledge of insider threat protection and only need to refresh it or learn about new types of threats.
The key difficulty here is that preparing documentation for such training requires lots of research and attention to details.
How to Build an Insider Threat Program [10-step Checklist]
3. Make the training course engaging and relevant
While the need for insider threat training is obvious to cybersecurity officers, for regular employees, it’s another activity that distracts them from their duties. If the training course is also boring or has nothing in common with their daily routines, employees will most likely learn nothing from it.
There are several ways to involve employees in the educational process:
- Avoid using generic insider threat awareness training materials
- Combine various types of content: lectures, articles, videos, quizzes, etc.
- Make the training about personal experience and clearly explain how insider threats and non-compliance with cybersecurity rules may affect trainees
- Prepare relevant examples of insider threats and their consequences
Analyzing examples of cybersecurity incidents that have happened in the organization is the best way to illustrate the importance of insider threat protection and teach employees basic dos and don’ts.
Ekran System’s User Activity Monitoring
4. Create an inviting atmosphere
Open insider threat discussions help with forming a culture of awareness in an organization. The ability to ask questions and make mistakes is an essential part of building such a culture and of any learning process. An open atmosphere helps employees engage in training and get the most out of it.
Make sure your employees are free to ask anything about insider threats during or after the training. Also, it’s a bad practice to punish employees for wrong answers or poor test results. Such punishments will only motivate your employees to learn correct answers mechanically and forget them after the training is finished.
When training is over, provide employees with contact information of a person they can reach out to if they have additional questions or spot something suspicious.
5. Simulate an insider attack
The final stage of any training is verifying that students actually gained knowledge and skills. Usually, training results are checked with tests or interviews, but it’s much more efficient to conduct an experiment and see how your employees will behave during a cybersecurity incident after receiving the training.
Partner with your IT department to perform one or several fake attacks: send out a phishing email, try to use social engineering to gain employee credentials, ask employees to share sensitive data, etc. Then collect the results and analyze the mistakes made by employees and the reasons behind those mistakes.
Keep in mind that it’s impossible to achieve perfect results. There will always be someone who accidentally opens a phishing letter or tries to visit a forbidden website. But the goal of insider threat awareness training is to bring the number of people who make such mistakes to a minimum.
Incident Response Planning Guideline for 2021
6. Get ready for the next training
A one-time training can’t provide you with a long-lasting effect: employees will forget what they learned, the company will hire new employees with little knowledge of insider threats, etc. To keep awareness at a high level, it’s best to make employee training a regular event. This helps employees be up to date with new security threats and keep an eye open for suspicious activity.
Here are several best practices to prepare for the next awareness training:
- Analyze the results of the previous training to find out which parts of the educational program need to be improved
- Add new insider threat indicators and patterns
- Update information on the state of insider threat prevention in your organization
- Prepare new ways to test the success of the training
Preparing insider threat awareness training with Ekran System
Insider risk management software such as Ekran System helps you not only to detect, deter, and respond to insider threats but also educate your employees. Here are several examples of how you can use Ekran System features to boost insider threat awareness training:
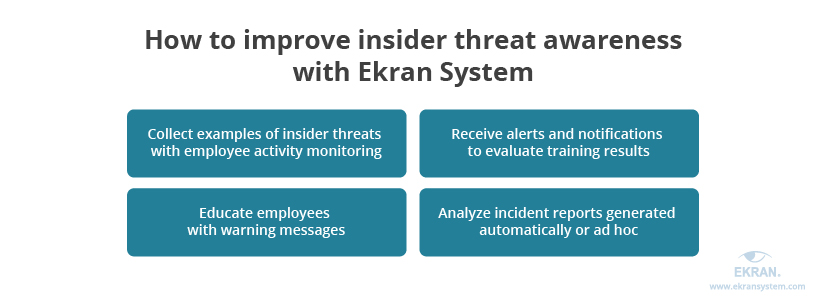

- Collect examples of insider threats with employee activity monitoring. This feature provides you with video and audio records of security incidents along with comprehensive metadata: keystrokes, executed commands, visited URLs, connected USB devices, etc. Using this data, you can model an incident, show your employees what went wrong, and offer advice on how to avoid similar incidents in the future.
- Receive alerts and notifications to evaluate training results. When conducting a fake insider attack, you need to see how employees respond to it. Ekran System sends security officers an alert for each security rule violation. This way, you’ll be able to see how your employees respond to a security incident in real time.
- Educate employees with warning messages. You can also configure Ekran System to show customized warning messages when an employee violates a security rule. This feature helps to prevent negligent insider threats and reminds employees of security rules.
- Analyze incident reports generated automatically or ad hoc. These reports can help you gain knowledge of the most common cybersecurity mistakes and violations made by different types of users in your organization. After the training, you can compare old and new reports to see the effect of the training.
Conclusion
In this article, we’ve explained why insider threat awareness is important for forming a cybersecurity culture in your organization. Understanding the nature and the consequences of insider threats helps employees make safer choices and reduces the number of cybersecurity mistakes they make.
Conducting insider threat awareness training is the best way to establish a strong cybersecurity culture in your organization. It helps you educate employees, explain to them the true importance of insider threat protection measures, and improve employee behavior. Security awareness training that educates employees on insider threats is also a requirement of many IT-related laws, regulations, and standards.
With Ekran System’s user activity monitoring and reporting functionalities, you can both protect your organization from insider threats and prepare an engaging and relevant training course for employees.






