Privileged access is granted to certain users so they can perform their work. Yet admin and service accounts often are the causes of cybersecurity incidents since they allow their owners to install and remove software, modify system configurations, and more. Even with privileged access management practices in place, malicious actors can continue to find new ways to compromise your sensitive data. However, a new just-in-time PAM approach promises to improve the situation.
In this article, we explain what just-in-time privileged access management is and how it helps businesses enhance their cybersecurity. This article will be helpful for security officers and anyone interested in efficient ways of managing privileged accounts.
What is the just-in-time approach to privileged access management?
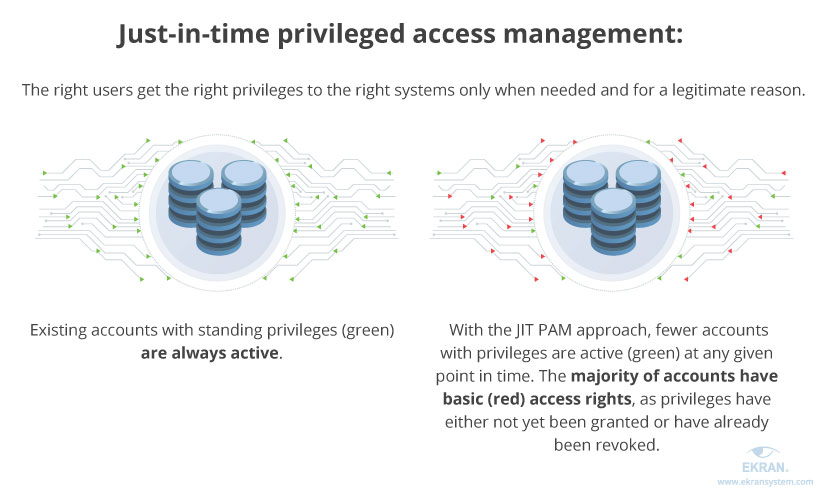
Just-in-time privileged access management (JIT PAM) ensures that only the right users are provided with privileged access to specific systems and resources, only for a valid reason, and only for the time required. The JIT PAM model helps organizations implement the cybersecurity principle of least privilege, with zero standing privileges as the goal.
The idea behind JIT PAM is to grant access permissions only when users need to perform a certain task and for no longer than the time required to fulfill that task. This minimizes the risk of privileged users taking advantage of sensitive data or privileged accounts being abused by attackers.

PAM practices are essential, as privileged accounts pose an inherent threat to a company’s critical assets.
Privileged accounts, or superuser accounts, are granted more privileges and permissions than accounts of standard users. Superuser accounts allow their owners to access an organization’s sensitive data, systems, and applications. Users can abuse these access rights to compromise corporate information, while cybercriminals can steal the credentials to privileged accounts to use those accounts for malicious purposes.
With the JIT PAM approach, you don’t have to create privileged accounts at all. Rather, you can provide privileges to users on demand for a valid reason and for a limited amount of time. By reducing the time for which users are granted extra access rights, you also reduce the risk of cybersecurity incidents.
Why choose JIT PAM over the basic PAM approach?
Organizations often choose basic or “business as usual” PAM practices that mostly focus on monitoring and controlling existing privileged accounts and managing privileged passwords.
The biggest mistakes companies make by implementing this approach are:
- Granting too many access rights to privileged users
- Providing users with standing privileges
- Granting unneeded privileges
- Creating personal privileged accounts for privileged users
While a basic PAM method helps businesses meet compliance requirements and make sure that employees and third parties use their privileges in an authorized manner, it’s not enough to completely implement the principle of least privilege.


Gartner, “Remove Standing Privileges Through a Just-in-Time PAM Approach”, Michael Kelley, Felix Gaehtgens, Abhyuday Data, 6 September 2019 (Gartner subscription required)
The cornerstone of the JIT PAM principle is to provide users only with the access they need for the time they need it and then to remove that access or privilege. On the contrary, most organizations tend to provide privileged users with access to sensitive information on a permanent basis.
According to Gartner, to implement the principle of least privilege to the fullest extent, businesses need to apply the zero standing privileges (ZSP) strategy through a JIT PAM model. A just-in-time model with zero standing privileges aims to eliminate standing or always-on privileges to reduce the attack surface of privileged accounts.


Gartner, “Remove Standing Privileges Through a Just-in-Time PAM Approach”, Michael Kelley, Felix Gaehtgens, Abhyuday Data, 6 September 2019 (Gartner subscription required)
The JIT PAM model ensures that privileged access rights are provided to the right users for the right resources only when needed and for a legitimate reason. Thus, it helps businesses minimize the risk of privilege abuse, critical data compromise, and stolen credentials.
Zero Trust Model: Can Trusting No One Be the Answer to Your Cybersecurity Problems?
Why do you need to implement JIT PAM?
Even when using PAM practices and monitoring tools, users with standing privileges can compromise your organization’s sensitive data.
Your critical assets can be compromised in multiple ways:
- An employee or a third party may misuse their privileges and provide sensitive data to your competitors.
- Users may break cybersecurity rules and make inadvertent mistakes that put your assets at risk.
- Malicious actors may steal credentials to your privileged accounts and gain access to your confidential information.
- Former employees or contractors might use their old accounts to take revenge.
- A privileged account that isn’t used for a long period of time (for instance, the account of an employee who left the company) is more likely to be hacked than is an active account.
Top 5 Inadvertent Mistakes of Privileged Users and How to Prevent Them
Let’s explore five major reasons to implement the just-in-time PAM approach and see which issues it can eliminate.


Truly implement the principle of least privilege
The principle of least privilege requires organizations to remove unnecessary standing privileges and provide only required privileges when absolutely essential for users. All privileges for all users should be limited to the bare minimum needed to perform their work.
Minimize risks of insider threat-related incidents
Privileged accounts often have broad access rights, similar to admin accounts. Some even grant access to multiple systems within an organization. This is why privileged accounts attract malicious insiders. When following JIT PAM practices, organizations reduce the attack surface and minimize the risk of data theft by insiders.
Simplify auditing and compliance activities
JIT PAM, as a mature form of traditional PAM practices, also helps companies apply best practices of PUM and user activity audit to meet various compliance requirements. The JIT PAM approach allows you to track who requested access to what information and when access permissions were removed.
Reduce the need to manage additional accounts
An advanced way of adopting the JIT PAM approach is to choose not to create privileged accounts at all. Instead, privileges can be requested for a certain amount of time for valid reasons. Access is granted only if a request meets the required parameters. In this way, you minimize the risks of account misuse, reduce the number of inadvertent mistakes of privileged users, and eliminate the need for managing privileged accounts altogether.
Help employees get required resources faster
Keep your workflow fast and avoid sacrificing security. When implementing the JIT approach to PAM practices, your employees can quickly gain access to organizational resources that are outside their routine work functions to perform tasks without the need to directly interact with credentials. Each time employees request access to resources, they get permissions on the fly via a system that provides or denies access automatically. Thus, you can eliminate the need for time-consuming processes of requesting access through emails and filling out various forms.
Now that we’ve explored the major advantages of the JIT PAM approach, let’s learn about the challenges of implementing it.
What to consider when adopting JIT PAM?
To protect your critical assets from malicious insiders, JIT PAM has to be implemented thoughtfully and efficiently.
Here are a few things to consider before adopting the JIT PAM approach:
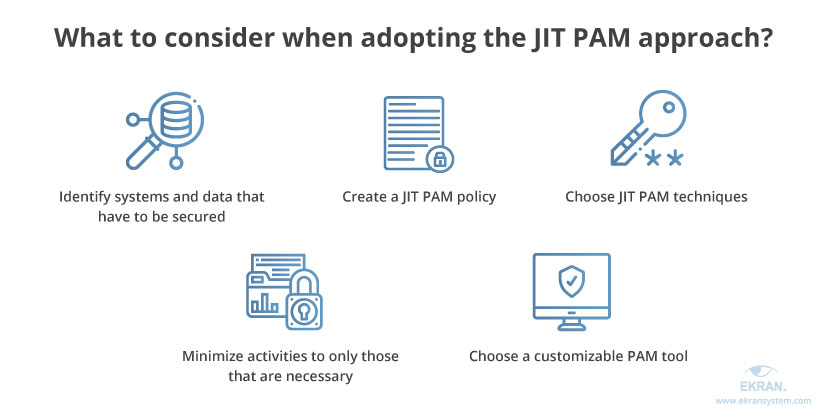

Identify systems and data that have to be secured in the first place and think of operational use cases. Also, you should define which users can request specific access rights for work purposes and which can perform all their tasks without requesting additional access.
Create a JIT PAM policy to govern a JIT account for proper privileged access. This policy should define variables that can trigger the cancellation of privileges. All privileged activities that fall outside the context of the policy should be automatically forbidden. Such a policy should define the time period for access, applications that may indicate account compromise, the time for session termination, inappropriate modification of resources, and the conditions for creating or deleting accounts, systems, data sets, etc.
Choose JIT PAM techniques to efficiently manage privileges. Define your strategy for creating and cancelling privileged accounts, granting account privileges, and disabling administrative accounts.
There’s always a risk of a hacker compromising accounts of privileged users and gaining access to critical assets. To prevent this, include multi-factor authentication in your PAM tools.
Even with time-limited access, a malicious insider or outsider can manage to compromise sensitive data. Consider restricting access to the minimum necessary, recording user activity, setting alarm notifications, and using user and entity behavior analytics to immediately spot abnormal activity.
An approach to PAM with just-in-time administration can be complex and costly to implement because you have to think of all possible scenarios: which users can request access to which systems for which reasons and for what amount of time. Search for the most convenient PAM tools that meet your needs and offer customizable options so you won’t pay for features you don’t use. In the long-term perspective, implementing JIT PAM will save you more money than it costs.
Adopting a JIT PAM approach requires sophisticated software with a number of helpful features to monitor and record privileged user activity, provide access to critical data after approval, detect abnormal activity, and immediately react to it.
Privileged Account and Session Management: What It Is and How To Deploy It
How can Ekran System help you implement a JIT PAM approach?
Ekran System offers a wide range of features to ensure quality privileged access management, user monitoring, and insider threat prevention. With a lightweight PAM solution from Ekran System, you can leverage basic functionality to implement a JIT PAM approach.
To employ the principle of least privilege and eliminate unnecessary credential management, use one-time passwords (OTP) and time-based user access restrictions. OTP functionality allows you to grant temporary access to critical endpoints after manual approval on a session-by-session basis. Time-based user access restrictions limit privileged access to critical assets and therefore minimize the chance of sensitive data being compromised.
With an access request feature, you don’t need to give users continuous access to privileges. Instead, you can grant them privileged access only after approval. Consider enhancing your PAM solution with require comment functionality so admins can prohibit users from accessing sensitive information without a legitimate reason.
Ekran’s workflow approval functionality also includes ticketing system integration as an additional layer of protection. With this feature, you can apply the purpose-based access principle to high-risk sessions initiated by your employees or contractors. After each session, a short report with a direct link to the session record will be attached to the corresponding ticket.
Thanks to Ekran System USB device management options, you can require users to request access to USB mass storage and mobile devices. Thus, you can secure USB devices by granting access based on necessity.
| Ekran System features to help you implement a JIT PAM approach | |
| One-time passwords (OTP) | Time-based user access restrictions |
| Request access | Require comment |
| Ticketing system integration | Request access to USB mass storage and mobile devices |
The JIT PAM approach offered by the Ekran System platform helps you deploy access control and identity management and prevent insider threat incidents.
Top 5 Poor Privileged Account Management Practices
Conclusion
Leveraging the just-in-time approach to privileged access management is a sure way to bring your cybersecurity to the next level. By providing privileged users with required access for only the time required to complete their tasks, you minimize the chances of data being stolen or compromised.
The crucial thing to remember is that zero standing privileges and just-in-time PAM approaches also require numerous activities like privileged user monitoring, session recording, and secure authentication. Ekran System offers an advanced solution for managing privileged access, including major features to implement the just-in-time PAM approach.





