The COVID-19 pandemic has forced organizations to temporarily transition to remote work environments. Two years have passed, but the remote work trend is still with us, with over 75% of people worldwide working remotely at least once a week.
As telecommuting concerns more cybersecurity experts around the world, some security officers still make drastic mistakes in configuring and managing remote environments. Read our blog post to learn the top ten security mistakes organizations make with regards to remote work. Discover what you can do to avoid these mistakes and enhance your cybersecurity.
Why is telecommuting a point of cybersecurity focus?
How can remote employees endanger your organization?
In an article on seven top trends in cybersecurity for 2022, experts from Gartner express their concern about the expansion of the attack surface that came with remote work and the increasing use of public clouds, supply chains, and cyber-physical systems.


Gartner, “Seven top trends in cybersecurity for 2022,”
Susan Moore, 13 April 2022 (subscription required)
Remote work raises cybersecurity risks, as it not only expands the potential attack surface but also moves it outside conventional perimeter defenses such as firewalls. Environments and devices that telecommuters work from are frequently unprotected.
Even today, when many employees combine working from the office with telecommuting, the situation is not improving. Hybrid work environments lead to cybersecurity mistakes among your remote workforce and, eventually, to cybersecurity breaches.
Employees’ remote work mistakes that put organizations at risk include installing insecure and outdated software, mismanaging sensitive data, and relying on weak passwords. Telecommuters are more susceptible to social engineering attacks or may act as malicious insiders.
All of the above opens up your organization to an abundance of cybersecurity threats. Phishing and brute-force attacks, malicious software installations, data theft, and even sabotage are on this list.
Effective Ways to Detect and Prevent Brute Force Attacks
Where is the proof?
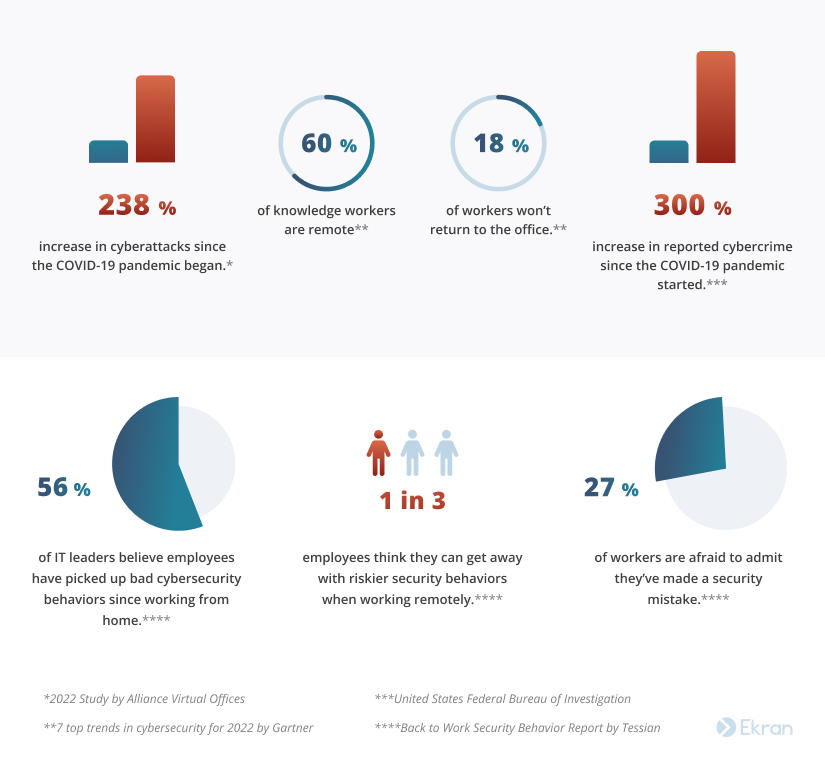
Gartner has recently reported that 60% of knowledge workers are remote and at least 18% won’t return to the office. Working from home has increased the frequency of cyberattacks by 238% since the start of the COVID-19 pandemic according to a 2022 Study by Alliance Virtual Offices, while the FBI has claimed a 300% increase in reported cybercrime since the pandemic began.

What’s at stake?
Organizations may experience the following risks as a result of poorly secured remote work:
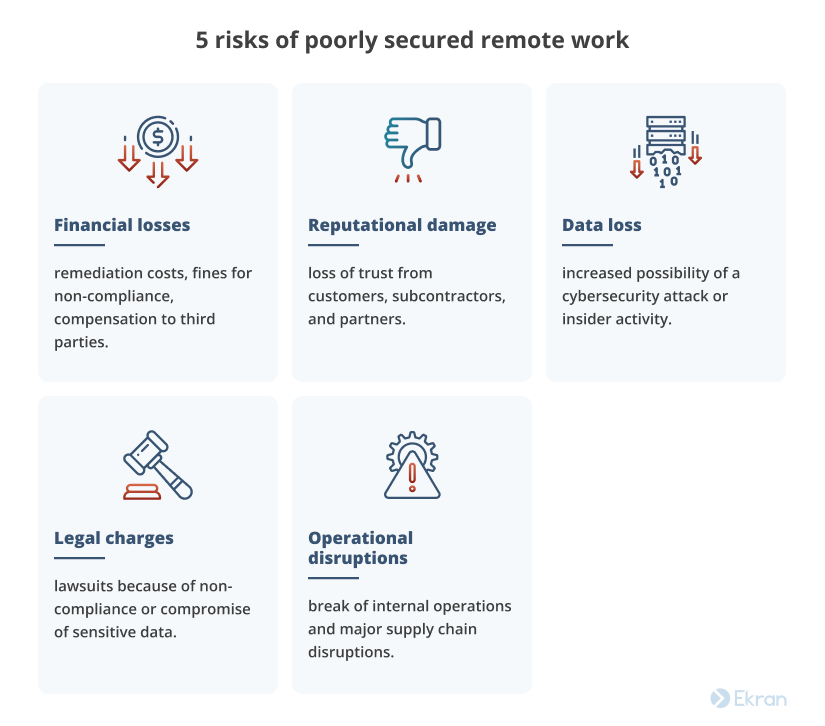

Read on to find out what your organization should and shouldn’t do to reduce cybersecurity risks related to remote work.
Remote Employees: How to Manage Insider Risks
10 common mistakes in securing remote work and how to avoid them
We have compiled a list of the ten most common mistakes your security officers might make in regard to your organization’s remote work environment.


1. Lack of visibility over remote activity with corporate resources
Insufficient visibility into what remote employees do in your organization’s IT environment undermines your ability to detect and disrupt security incidents.
While working in a less secure setting, telecommuters have the same level of access to sensitive information as their office-based colleagues. Given that about 43% of remote employees make mistakes that have cybersecurity consequences, your organization must take steps to minimize these repercussions.
Additionally, if a remote worker becomes a malicious insider, they’ll find it easier to steal or corrupt sensitive data, perform industrial espionage, or commit fraud without ever getting noticed.
To be able to detect and prevent such threats, security officers must be able to fully monitor remote desktop activity. Consider deploying dedicated insider threat management software like Ekran System — a universal insider risk management platform that can help your security officers prevent malicious insider attacks and other cybersecurity threats caused by remote work activities.
How can Ekran System help?
Ekran System’s user activity monitoring (UAM) capabilities allow you to:
- Monitor all activity of your remote employees and record it in a video format accompanied by useful metadata
- View recorded user sessions or live user activity in an intuitive YouTube-like player
- Search user sessions by multiple parameters, including launched applications, visited URLs, and executed commands
2. Providing remote employees with uncontrolled access
Remote employees and third parties with too many access rights may be a source of privilege abuse, data breaches related to account compromise, and other cyber attacks.
The solution is for your security officers to prohibit access unless needed. This is called the principle of least privilege, and it means granting access scarcely, giving your employees only necessary access rights to perform their direct job responsibilities. Cutting the number of remote employees with unnecessary access to critical information can help you prevent potential data breaches.
To enhance access limitations on a need-to-know basis, consider implementing a more comprehensive just-in-time approach to access management.
Remote privileged users and third parties require even more attention than office employees, as their privileges to access your organization’s infrastructure may be elevated. Lack of control over your partners, subcontractors, and other privileged remote users heightens the cybersecurity risks they pose for your company. Make third-party risk management an essential part of your cybersecurity program, and consider managing your supply chain risks.
How can Ekran System help?
Ekran System’s privileged access management (PAM) functionality can help you secure, optimize, and automate access management processes for telecommuters, remote privileged users, third parties, and other users in your organization. Ekran System’s PAM functionality allows you to:
- Granularly manage access rights of all users in your organization
- Set up a manual access request and approval workflow
- Limit the time for which access is granted
3. Absence of a remote access policy
Not having security policies in your organization may result in poor articulation and synchronization of your security goals.
A remote access policy (RAP) guides your organization’s efforts to ensure proper cybersecurity of remote work. Such a policy outlines the processes your security officers and telecommuters should rely on to minimize remote work-related cybersecurity risks.
An RAP may be part of a larger information security policy (ISP) containing other aspects of your organization’s security. An RAP should also contain a list of cybersecurity solutions and tools for managing your organization’s remote work risks.
How can Ekran System help?
Ekran System can help you ensure that a remote access policy is correctly implemented in your organization by allowing you to:
- Monitor the activity of users connecting remotely to corporate networks
- Control remote access to your organization’s systems and data
- Verify identities of remote users connecting to your organization
5 Steps for Building an Agile Identity and Access Management Strategy
4. Allowing users to set their own passwords
A poorly secured work environment combined with weak password habits of remote employees increases the risk of account compromise as a result of brute force attacks, password spraying, and other cyberattacks.
Up to 35% of remote employees reuse their passwords for business applications and accounts, according to a Work From Home Study by IBM Security and Morning Consult.
Poor password management habits of telecommuters force organizations to manage user credentials themselves using specialized software.
How can Ekran System help?
Ekran System’s password management [PDF] capabilities provide your security officers with full control over remote employees’ credentials to your organization’s accounts. Ekran System enables you to:
- Generate account credentials for remote workers in your infrastructure
- Grant secrets for passwordless authentication of remote users
- Provide remote users with one-time passwords
- Rotate user passwords automatically or ad hoc
All passwords and secrets are stored in Ekran System’s secure vault, encrypted with the military-grade AES 256-bit standard.
5. Failing to check remote users’ identities
The inability to check who’s using an account can result in unauthorized access to your organization’s critical assets.
If a telecommuter’s account credentials are compromised, there must be a way for security officers to prevent cybercriminals from accessing your organization’s assets. Multi-factor authentication (MFA) is a time-proven method and a requirement of many IT security standards and regulations for verifying user identities and preventing unauthorized access.
MFA ensures that there are more factors for authenticating a user that tries to access your network than just a password. The most common scenario is for a user to receive a one-time SMS password sent to their phone. With MFA enabled, a cybercriminal can make no use of stolen credentials.
If you want to make the most of MFA, make sure to research the topic of zero trust and consider implementing a zero trust architecture in your organization.
How can Ekran System help?
Being part of Ekran System’s identity management capabilities, MFA can provide your organization with an efficient way to verify identities of remote users connecting to your IT systems.
Additionally, the secondary authentication feature in Ekran System can help you identify users of shared accounts by requiring an additional authentication step.
Rethinking IAM: Continuous Authentication as a New Security Standard
6. Unsecured and misconfigured network
Failing to secure and properly configure your organization’s network is where many security vulnerabilities of remote work routines are born.
Paula Januszkiewicz, a cybersecurity expert at the RSA Conference, listed misconfigured network communication services as the number one reason remote work causes cybersecurity incidents. Network misconfigurations cost organizations 9% of annual revenue according to a report by Titania.
To ensure your cybersecurity system is configured as it should be, think about ways you can audit and control your admins’ actions, such as by installing user activity monitoring solutions.
How can Ekran System help?
Ekran System’s privileged user management capabilities provide your organization with visibility and control over the activity of system administrators. You can:
- See how sysadmins configure the system by monitoring their actions
- Record sysadmins’ monitored user sessions to increase accountability
- Manage sysadmins’ access privileges and secrets, including SSH keys
How to Secure System Administrators’ Privileged Accounts: 7 Best Practices
7. Lack of network segmentation
If your organization’s network is monolithic, a cybercriminal has much more freedom and access opportunities than if the network is segmented.
Network segmentation limits your organization’s exposure to cybersecurity incidents and gives you more control over who has access to what. With the use of devices like bridges, switches, and routers, you can divide the network into several subnets, each of which will function as a separate small network.
By isolating systems and services from one another, security officers can prevent a minor breach from becoming a significant cybersecurity incident with severe consequences. The more closed doors a cybercriminal encounters, the greater the chance they’ll give up and look for easier targets elsewhere.
The network segmentation approach is necessitated by the heightened cybersecurity risks of remote work. Therefore, consider restricting communications between your organization’s networks. This will help you limit unauthorized access to sensitive systems and data. You can segment the network not only physically with the help of various devices but also logically using software.
How can Ekran System help?
Just as network segmentation can help you prevent unauthorized access by cutting off potential pathways for cyber criminals, Ekran System can also limit unlawful access at the level of authorization and authentication, enabling you to control user access and verify user identities.
Additionally, Ekran System is flexible and able to meet your organization’s network requirements by supporting a wide set of on-premises and virtual platforms.
8. Leaving employees’ home environments unsecured
Many cybersecurity incidents happen because remote employees don’t use the right tools and measures to secure their environments.
Once you have an RAP, make sure telecommuters follow it. Information security policies, including your remote access policy, are high-level documents that provide a general approach to an organization’s cybersecurity. However, your security officers may create low-level rules and guidelines for remote workers to follow when accessing your organization’s systems.
To ensure the environment your employees connect from is safe, provide them with a list of what they should do and what cybersecurity mistakes remote workers need to avoid. Make sure that this list covers the following essential matters:
| How to secure your remote employees’ home environment | |
| Use of applications | Provide your staff with a list of safe applications and tell them about the dangers of installing unauthorized software. Make sure your employees install necessary software and operating system updates. |
| Use of personal devices | Tell your employees to avoid using personal devices for remote work, if possible. Develop rules for using such devices: for example, employees must keep their work-related devices away from family members. |
| Password habits | Form secure password habits among your employees, such as regularly updating passwords, using unique passwords for different accounts, and ensuring proper password complexity. |
| Network security | Instruct your employees on how to use antivirus software, VPNs, and other security tools at home. It’s vital that your staff protects their home Wi-Fi and avoids using public networks for remote work. |
| Email security | Ensure that remote personnel use only corporate email for sending and storing sensitive data. Tell employees about social engineering and how not to become a victim. |
How can Ekran System help?
By deploying Ekran System in your organization, you can:
- Monitor user activity to see if remote users follow your security requirements
- Find out what applications remote employees use, what websites they visit, what keystrokes they type on your corporate endpoints, and more
- Receive real-time alerts on suspicious activity of remote employees in your infrastructure
Voyage Encore Travel Ensures Remote Employee Productivity and Data Security with Ekran System [PDF]
9. Failing to engage telecommuters in cyber awareness training
If telecommuters don’t consider cybersecurity important, they can forget, ignore, and even sabotage critical security processes for their own comfort.
42% of employees in the UK have not received cyber awareness training since shifting to remote work. Try not to become part of these statistics, as employees’ cybersecurity awareness is a cornerstone of any organization’s security.
Ensure that your security officers conduct regular security training to prepare your remote employees for the latest cyber threats. By focusing the training around personal experience rather than simply listing existing threats, there will be a better chance that remote employees will remember and use your security recommendations. Therefore, make sure there are enough examples of cybersecurity incidents, especially examples of phishing attacks and their consequences. If possible, showcase any security incidents that may have happened in your organization.
How can Ekran System help?
Ekran System can help you enhance your remote employees’ cyber awareness by allowing you to:
- Collect and demonstrate examples of cybersecurity incidents in the form of detailed video records
- Educate remote employees with warning messages if they perform forbidden actions
- Record the results of simulated cyberattacks and show employees their mistakes
10. Not having an incident response plan
Without a plan on how to respond to a cybersecurity incident, you’ll lose precious time, which frequently equals a loss of money and reputation.
The more time it takes your security officers to detect, stop, and remediate a cybersecurity incident, the more damage a cyber criminal can cause to your organization.
An incident response plan (IRP) serves as a cybersecurity lifeboat when things get critical and you need to act fast. An IRP outlines direct and concrete steps for your security officers to take if an incident is discovered. An efficient IRP contains:
- Indicators of cybersecurity incidents
- Descriptions of the most common security incidents and corresponding response scenarios
- A list of employees included in the incident response team and their responsibilities to act in response to an incident
- Recovery and incident investigation measures
- Contacts of people and regulatory authorities to notify about an incident
How can Ekran System help?
Ekran System’s alerting and incident response functionality allows you to spot early signs of cybersecurity incidents and respond to them promptly. Your incident response team will be able to:
- Set customizable alert rules according to your organization’s needs
- Get instant email notifications on suspicious activity of remote employees in your system
- Automatically or manually stop a suspicious user’s session, terminate the related application, or warn the user with a message based on the triggered alert
- Detect and respond to a user’s abnormal behavior patterns using Ekran System’s AI-based UEBA module
On top of that, Ekran System’s reporting and exporting capabilities can provide your organization with tools for internal audits and incident investigation procedures. You’ll have the ability to:
- Generate clear reports on the user activity of your remote employees
- Export user sessions in a standalone, immutable format for forensic investigators
Insider Threat Statistics for 2022: Facts and Figures
Conclusion
With the expansion of the attack surface caused by the rapid rise of remote work, organizations have to prepare themselves for new cybersecurity risks presented by telecommuting. Ensure that your security officers make use of our best practices on how to avoid remote work security mistakes described in this article.
First, make sure to properly configure your networks. To decrease the attack surface, practice network segmentation, find a way to limit your remote employees’ access, and check user identities. To improve visibility, monitor and log your telecommuters’ actions. Additionally, increase your employees’ cyber awareness, have a plan for security incidents, and don’t forget to document everything in your remote access policy.
As an all-in-one platform, Ekran System brings together robust user activity monitoring, privileged access management, and other functionalities to help your organization efficiently manage the cybersecurity risks associated with remote work.
See what Ekran System can do for your organization right now with a free one-month trial!





