Multi-factor authentication (MFA) is an essential part of today’s identity and access management best practices. It’s also one of the main compliance requirements for user identity verification. MFA allows you to add one more layer of protection to critical endpoints, data, and functionality. The main function of MFA is to make sure that the person or entity trying to access protected assets really is who they claim to be.
In this article, we explain what true multi-factor authentication is and take a look at the key two-factor authentication methods you can use to enhance your cybersecurity.
What is multi-factor and two-factor authentication?
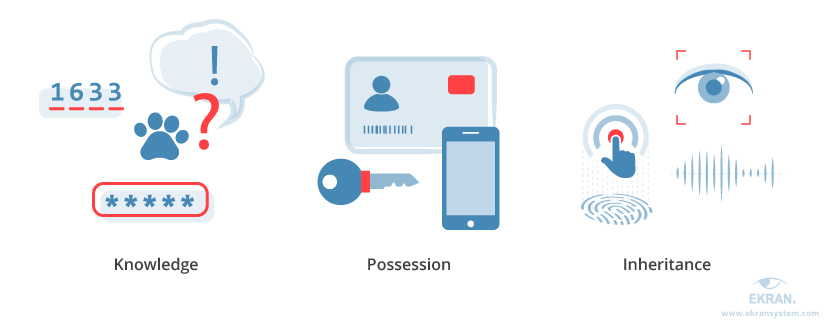
There are three categories of factors. You need to use at least two.
Classic authentication methods are usually one-factor: a password (if you know it, you’re authorized), a key (if you have it, you get access), and so on. Multi-factor authentication, otherwise known as two-factor authentication or simply 2FA, requires the authentication process to include verification of factors from at least two out of three categories:
- Something a user knows (password, PIN, answer to a secret question, etc.)
- Something a user possesses (key, security token, bank card, smartphone, etc.)
- Something a user is / biometrics (fingerprint, iris, voice, etc.)
Some vendors may add location and time verification to this definition.

What is NOT two-factor authentication?
The answer is crucial to the security of your data.
With the growing attention to security and authentication, many vendors put efforts into strengthening their authentication processes. But don’t be caught by the marketing wording; not all multi-step authentication approaches can be called true MFA.
For example, a set of secret questions or secret images following the credentials verification screen simply represents another knowledge component. It’s a multi-step but not a multi-factor authentication approach. Asking a question like What’s our boss’s nickname?probably won’t be a good enough second line of defense. At least, not from a colleague who likes to borrow passwords.
Another example of double knowledge-based authentication is the use of a password in conjunction with a verification code sent to the user’s email. In most cases, email can be accessed from any location using just another piece of knowledge – the email account password. And even though there are some email providers that support 2FA, not all of their users actually enable it. For instance, over 90% of Gmail users reportedly don’t use the free 2FA feature provided by Google.
An SMS verification code sent to the user’s verified smartphone represents a possession factor. Thus, it can form true two-factor authentication together with credential verification.
Scenarios described above are examples of so-called strong authentication.


But remember: while any multi-factor authentication is strong, not all strong authentication is multi-factor.
Methods for building a two-factor authentication system
Where should you start from?
As we mentioned, the inheritance factor, represented by biometrics, isn’t popular among computer system vendors. Biometric verification is mostly used in control systems serving restricted access locations, often in the form of biometric IDs. Social networks and mobile device providers also actively use biometrics as one of the identity verification factors.
А more generic approach that most computer system vendors rely on is based on the combination of knowledge and possession factors.
Knowledge is traditionally represented by credentials – a username and password. A whole bunch of underlying technologies serve to strengthen this factor of authentication: password vaults, password management systems, one-time passwords, and so on.
12 Best Cybersecurity Practices in 2019
There are a number of methods for implementing possession factors into the 2FA process. The three most popular and widely used are:
- Security tokens
- Mobile-delivered tokens
- Time-based one-time passwords
Let’s look closer look at each of these methods.
A security token is a device that contains software that can generate validation codes. There are two types of tokens:
- Connected tokens are generated when the device is connected to the target endpoint.
- Disconnected tokens are generated independently, without the need to connect the device with the endpoint.
A certain level of inconvenience is one of the main drawbacks of using security tokens. There are just too many things to take care of: the production, management, maintenance, and replacement of numerous devices. Not to mention that you need to carry along an extra device every time you want to access a protected endpoint.
Mobile-delivered tokens can be seen as an improvement to the original device tokens. In contrast to dedicated devices, this method uses the one thing almost everyone always has with them – a smartphone.
Today, mobile-delivered tokens are one of the most popular and widely used MFA methods. Usually, a user requesting access to a protected endpoint or data receives a confirmation code in an SMS or a message in an app.
While being convenient, this approach also has several drawbacks:
- Token generation – Tokens need to be generated dynamically, and the security of the process will heavily depend on the corresponding algorithm. Passcodes should be valid only for a limited time, expire after the first use, and constantly change to avoid blind guessing.
- Secure delivery of the code – The security of message delivery fully depends on the mobile operator’s operational security. There are techniques like wiretapping and SIM cloning that can provide cyber criminals with the knowledge they need to get access to protected assets.
- Network connection – In contrast to device tokens, in order to be able to receive a verification code via a smartphone, the user should be connected to the cell network or the internet.
Time-based one-time passwords. To answer the drawbacks of mobile-delivered tokens, the industry has introduced some analogs of disconnected tokens for smartphones, one of which is known as the time-based one-time password algorithm, or TOTP. Popularized by Google and Amazon, this approach is increasingly being adopted.
In a nutshell, at the authentication stage, a user starts an app on their smartphone and generates a passcode they then enter in the authentication window of the service they’re trying to access. On the system side, the algorithm generates a validation code based on the same time slot and initial vector assigned to this specific user and device. If the provided passcode and verification code match, access is granted.
Challenges of implementing 2FA
Although all the approaches to dual-factor authentication that we’ve described improve security, there are several general problems that still need to be addressed.
First, there’s the problem of a somewhat longer and more complex process from the user’s standpoint. But from the 2FA security perspective, the weakest part of many two-factor authentication products is the account recovery process.
Usually, the recovery process includes only one identity verification factor – such as resetting a password using a link sent by email – and thus is vulnerable. Several big two-factor authentication system breaches discussed in the media have been attributed to this very factor. One of the possible scenarios of such a breach was described by Matthew Prince, chief executive of web content delivery system CloudFlare.
In internal business systems, when the number of users is comparably small and the authentication process is controlled by the in-house team, the recovery process can be manual or semi-manual, which takes more time but provides much better security.
Secondly, man-in-the-middle attacks and SMS intercepting are two threats that the standard 2FA mechanism is vulnerable to. Cyber criminals may use different forms of MITM attacks to intercept internet connections, redirect victims to a fake website or application, and steal legitimate one-time passcodes. Attackers can also use SIM cloning techniques and various malware to hijack messages with verification codes. In fact, SMS interception was what made the Reddit hack possible in 2018.
One possible solution to these challenges is to implement MFA in conjunction with more sophisticated tools and functionalities, such as a token-based SMS system (as opposed to the regular mobile phone-based systems), behavioral biometrics, and data encryption. But even though two-factor authentication has its limitations, the benefits of this cybersecurity practice should not be underestimated.
Rethinking IAM: Continuous Authentication as a New Security Standard
When two-factor authentication is used
Is 2FA a must for you?
For regular users, using 2FA to protect their personal data is optional. Today, you can switch on MFA for many social media platforms including Facebook, Twitter, LinkedIn, and Instagram. It’s also available for Dropbox, Google products, Microsoft systems, and many other popular solutions and cloud-based platforms.
For businesses, however, multi-factor authentication, and 2FA in particular, is a recommended practice and, in some cases, even a regulatory requirement. For example, PCI DSS requirement 8.3 (from version 3.2) prescribes the use of multi-factor authentication for all network access to the card data environment, both remotely from outside the network and within the trusted network. The use of MFA is also required by NIST.
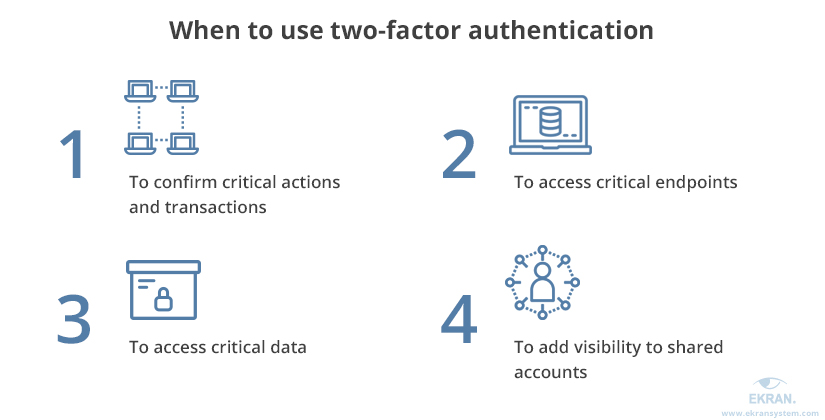
According to the best security practices, here are the four types of tasks that this enhanced identity validation should be used for:
- Confirmation of critical actions and transactions
- Access to critical endpoints
- Access to critical data
- Secondary authentication for shared accounts

Although these tasks are naturally interconnected, we distinguish them to better specify the business processes in which multi-factor authentication is required.
Benefit from Ekran System’s free 2FA solution
You can implement true MFA capabilities with Ekran System’s free 2FA tool. Ekran System delivers built-in two-factor authentication options for protecting valuable corporate assets as part of our growing set of identity and access management solutions.
Our 2FA tool uses centrally managed TOTP-based authentication as the second authentication factor. Verification codes can be sent to Android and iOS devices via either the Google Authenticator or Microsoft Authenticator app. Plus, you can enable 2FA functionality on any Windows and Linux server with an Ekran System client installed.
Also, you can also use Hideez key as an alternative to Ekran System 2FA functionality.
Ekran System Two-Factor Authentication (2FA) Solutions
Conclusion
Two-factor authentication is essential for ensuring a proper level of access granularity and user identity verification. Contrary to common belief, multi-factor authentication and multi-step authentication are not the same. The distinctive characteristic of true MFA is the use of at least two out of three identity verification factors: knowledge, possession, inheritance.
Ekran System offers a free 2FA tool based on the factors of knowledge (user credentials) and possession (a verified user device). This combination of factors is effective, cost-saving, and comfortable, as a user’s mobile phone is all you need to verify their identity.
With the help of Ekran System’s 2FA tool, you can protect critical systems and endpoints, limit access to valuable data, and add one more layer of identity verification to the login procedures of privileged users, remote employees, and third parties.





