While organizations are spending a good deal of money protecting their data against unauthorized access from the outside, malicious insiders may pose no less harm. According to the 2021 Data Breach Investigation Report [PDF] by Verizon, 36% of all data breaches experienced by large organizations in 2020 were caused by internal actors. For small and midsize businesses, it was 44%.
Organizations that become victims of malicious insider attacks face many negative consequences: from loss of confidential data, revenue, and clients to reputational harm or even going out of business. Let’s look closer at how organizations can detect a malicious insider before they cause harm.
What is a malicious insider?
The United States Computer Emergency Readiness Team (CERT) defines a malicious insider as one of an organization’s current or former employees, contractors, or trusted business partners who misuses their authorized access to critical assets in a manner that negatively affects the organization.
Malicious insiders are harder to detect than outside attackers, as they have legitimate access to an organization’s data and spend most of their time performing regular work duties. Thus, detecting malicious insider attacks takes a long time. The 2020 Cost of Insider Threat [PDF] Report by the Ponemon Institute states that it takes on average 77 days to detect and contain an insider-related security incident.
In their guide to insider threats, CERT describes the classification of malicious insider activities:
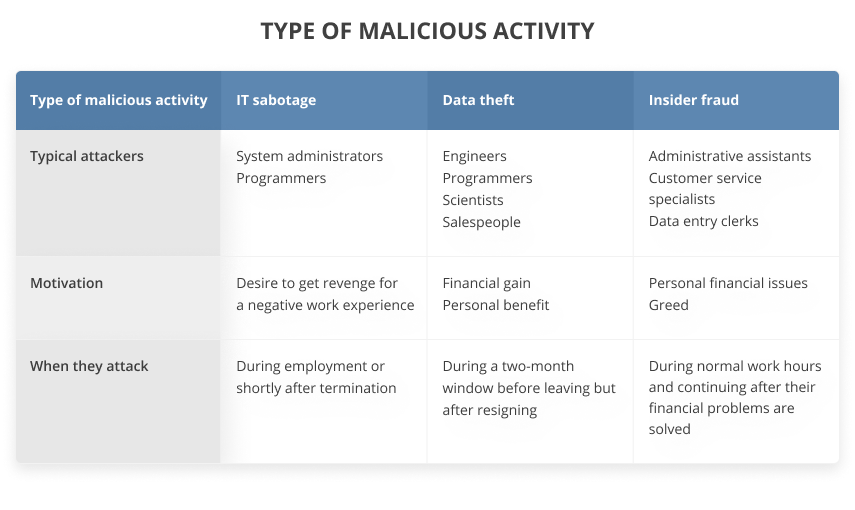

- IT sabotage is abusing information technology to direct specific harm to an organization or individual. These types of attacks are usually performed by system administrators, programmers, or other technically savvy employees who can hide their malicious actions and disable an organization’s operations. These people are typically motivated by a desire to get revenge for a negative work experience and generally execute their attacks during employment or shortly after termination.
- Data theft is stealing intellectual property or sensitive data from an organization for monetary gain or personal benefit. Insiders who steal data are usually current employees: engineers, programmers, scientists, salespeople, etc. Most of them steal the same information that they access during their normal work activity with the intention to sell it, use it on their new job, or start their own business. This type of insider can act alone or in cooperation with other employees. Corporate espionage also belongs to this category of insider incidents. During corporate espionage, insiders steal trade secrets so a third party can gain a competitive advantage. Data theft is usually performed during a two-month window before an employee leaves but after they’ve resigned.
- Insider fraud is unauthorized access or modification of an organization’s data. Usually, the motivation for fraud is personal gain or data theft with the intention of identity theft or credit card fraud. These attacks are usually committed by lower-level employees like administrative assistants, customer service specialists, or data entry clerks. In most cases, these people are motivated by personal financial problems or greed, and only in some cases are they hired by outsiders. Most perform their malicious actions during normal work hours and continue to act maliciously even after their financial problems are solved.
It’s necessary to understand that attacks by malicious insiders are rarely committed randomly, as insiders usually thoroughly plan their actions or act after a triggering event. Thus, we can notice typical behavioral indicators of malicious insiders and technical indicators of planned attacks. It will help us respond to a threat and avoid intellectual property theft.
What Is an Insider Threat? Definition, Types, and Countermeasures
Factors that influence malicious activity
There are four factors that influence whether a malicious insider will act and which type of activity they will choose:


- Organizational factors — These factors include the corporate culture and cybersecurity policies and influence whether a potential insider decides to act. For example, the culture inside an organization shapes cyber security and insider threat awareness and employees’ education on the consequences of an attack. Cybersecurity policies (if they are explicit and implemented to the letter) show potential insiders how well protected sensitive data is and how seriously the organization takes cybersecurity.
- Technical factors — Cybersecurity solutions implemented in an organization are the keys to detecting and stopping insider threats. Such solutions include user activity monitoring tools, access management solutions, identity management systems, and other tools. A cybersecurity system also influences the type of attack an insider can choose. For example, if an organization has a monitoring system, an insider may gain access to another user’s account to act undetected. Or they can try to abuse access to sensitive data if there’s no access management system.
- Environmental factors — The external environment such as political agendas, company reputation, and cultural and ethical norms can motivate an employee to act maliciously. For example, an employee might sabotage a production line if they believe it pollutes nature.
- Individual factors — Personal motivation includes a person’s self-image, beliefs, psychological profile, personal or financial issues, relationships with the organization and colleagues, etc. For example, employees can try to illegally profit from an organization to pay personal debts or harm the organization’s infrastructure because they didn’t get a promotion.
With this in mind, let’s reveal indicators of insider threat behavior, which will help you recognize a rogue employee by their behavior or technical activities.
Behavioral indicators of malicious insiders
Not all employees become malicious insiders, so there’s no need to suspect everyone. The following things that you can identify during the hiring process can be warning signs of a potentially risky insider:
- Official records of arrests, harassment, hacking, or security violations at former workplaces
- History of non-compliance with corporate policies
- Falsification of hiring information
- Cases of unprofessional behavior
- Abusive behavior towards other employees
- Personality conflicts
- Misuse of travel, time, or expenses at former workplaces
- Conflicts with former coworkers or supervisors
Behavioral indicators can also appear during work at your organization and signal an employee’s disgruntlement and potential readiness to take malicious actions. Your human resources (HR) department should pay closer attention to employees or contractors who:
- Violate corporate policies
- Have conflicts with colleagues
- Perform poorly
- Are deeply interested in projects they aren’t involved in
- Use sick leaves too often
- Work without vacations
In these cases, the HR department should discuss the reasons for such behavior with an employee and try to help them. They also should inform security officers so they can conduct targeted technical monitoring of these employees. While there may be no signals of an ongoing attack during these periods, it’s important to constantly monitor critical events and detect anomalies.
Technical indicators of malicious insiders
Technology-related indicators include actions of malicious insiders that involve computers or electronic media. To execute their attacks, insiders misuse their authorized access to critical corporate data or create a new path in order to access unauthorized assets and conceal their identity or actions. Let’s learn the indicators of types of malicious insider activities — IT sabotage, data theft, and fraud.
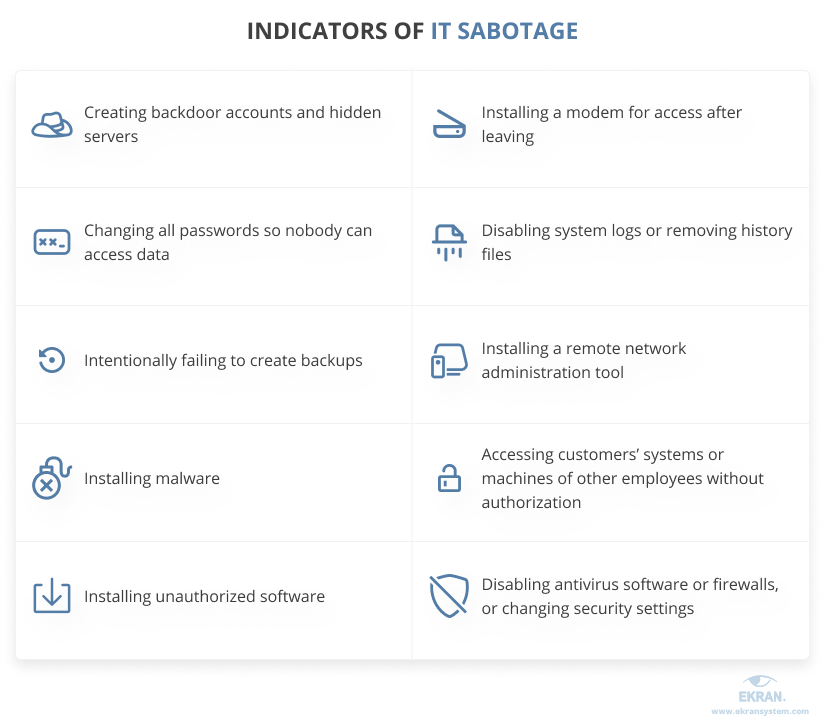
Indicators of IT sabotage
Technically savvy insiders usually try to bypass protection measures and conceal their activity or identity. Common techniques of malicious insiders include:

Insider attacks coming from technically savvy employees can lead not only to financial losses but also to IT system crashes and downtime. That happened to a Cleveland-based organization that fell victim to a denial of service attack which crashed servers and prevented the organization’s employees from accessing the damaged servers for a long time. An investigation of this incident showed that senior developer Davis Lu deployed malicious code that caused server crashes and deleted files associated with user profiles, making it impossible for users to log in to the system.
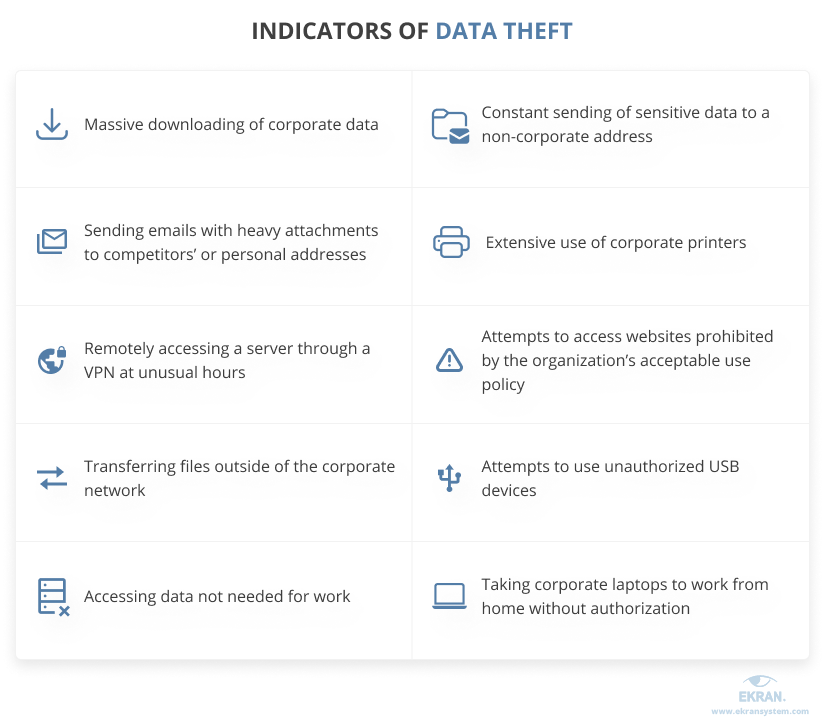
Indicators of data theft
In case of data theft, insiders try to access, steal,and share critical data with competitors or future employers or keep it for personal use. Since insiders may regularly access data when performing their duties, it may be quite difficult to detect data theft. However, security officers should pay attention to the following actions that may be a sign of data exfiltration:

Poor data management practices and lack of access control led to the biggest data breach in the Canadian financial sector. At Desjardins, employees had to copy private customer information, including financial details, to a shared drive in order to work with it. A malicious employee used their access to this drive and collected sensitive data for at least two years. At the end of 2019, Desjardins discovered that this employee had leaked the data of 9.7 million of its customers.
The incident is still being investigated, but it’s estimated that Desjardins will have to spend $108 million to mitigate the breach.
Insider Data Theft: Definition, Common Scenarios, and Prevention Tips
Indicators of insider fraud
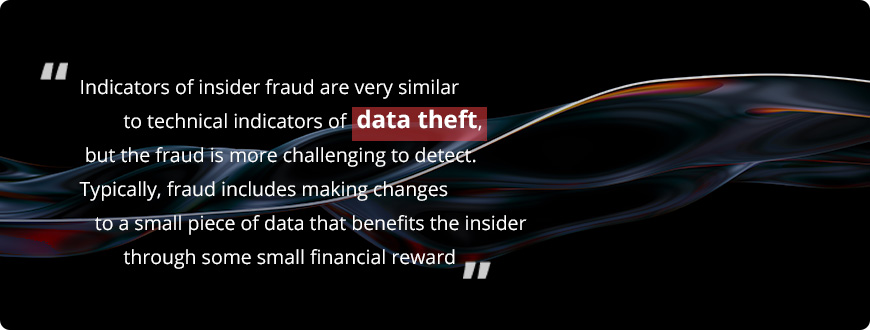
When it comes to fraud, insiders try to steal or alter information to which they have access. In some cases, they cooperate with their coworkers and share credentials to access sensitive data. Indicators of insider fraud are very similar to technical indicators of data theft, but the fraud is more challenging to detect.
Typically, fraud includes making changes to a small piece of data that benefits the insider through some small financial reward. While these actions are hard to notice, the fraud can continue as long as an insider wants. Insiders can also abuse their authorized access and sell data to external parties who might carry out identity theft.

One of the most well-known types of fraud is insider trading, which is the trading of a public company’s stocks based on private or classified information. For example, in 2020, a federal jury in Manhattan convicted businessman Telemaque Lavidas of being part of an international insider trading scheme and leaking private information about Ariad Pharmaceuticals Inc. to his partners. Based on this information, partners traded the company’s stocks and “rewarded” Telemaque Lavidas with $500,000.
European Bank Ensures Compliance and Combats Insider Threats
Fortunately, all these malicious insider techniques and activities can be detected by security operators or system administrators who use special tools for employee monitoring, log management, and data loss prevention.
How to detect malicious insiders
Security specialists can detect insider fraud activity and other insider threats through technical means by leveraging Windows, Citrix, and Amazon WorkSpaces session recording tools, setting up alerts for suspicious actions, and using means to detect abnormal user behavior. Let’s find out how these measures help to combat insider threats and which types of protection Ekran System can provide.

You can detect unusual access requests using the access management toolset in Ekran System. It helps security officers define access rights for each user or user role and detect access policy violations. For example, with Ekran System, it’s possible to:
- Detect requests to access data that employees don’t usually need
- Deny access if a user requests it during non-working hours or during a vacation
- Make a user state a reason for accessing sensitive data
- Enforce additional authentication measures to confirm a user’s identity
- Audit a user’s access history
- Manage credentials to avoid credential theft
User activity monitoring helps to control all activity inside your infrastructure and review security incidents. This functionality records all user actions inside the protected network by taking screenshots of the user’s screen and recording metadata: opened folders, files, accessed websites, keystrokes, executed commands, and more. Using these records, security officers can review security incidents to determine whether a user is acting with malicious intent and has done damage to the organization. They can search by a particular user, time, or activity, which speeds up the review.
If security officers detect malicious insider activity, they can export records in a protected format to use as proof in forensic activities.
8 Best Practices of Privileged User Monitoring
To be able to detect insider threats in real time, it’s crucial to set up and prioritize alerts. This functionality sends a notification to security officers when a user violates security rules. Using this notification, an officer can watch user sessions online and determine the threat.
For example, you can establish high-priority alerts that inform about:
- Unauthorized access to critical or sensitive information that’s inconsistent with job duties
- Use of unauthorized USB devices
- Installation of any additional software
- Blocking of security software
- Uploading data to cloud storages
- Accessing of log data
To check your system’s readiness to withstand insider attacks, you can launch an attack against yourself and refine the rules as needed. If alerts are triggered too often, you can tune the thresholds.
A modern alternative to predefined correlation rules is user and entity behavior analytics (UEBA), which provides more precise detection of malicious activity by using machine learning algorithms and advanced analytics. UEBA systems create a baseline of normal behavior for each user and then correlate it with the user’s current activity. If it detects characteristics of a malicious insider activity, UEBA will inform a security officer about it. This approach allows security officers to reveal abnormal user activity that’s typically not easily found or is missing from logs.
When employees are familiar with security solutions applied by their organizations, they can try to fly under the radar. However, UEBA solutions can identify behavioral patterns and detect even slight changes in user behavior. For instance, with Ekran System’s UEBA module, it’s possible to find out if employees access sensitive data during unusual hours, which is one indicator of an insider threat.
Behavioral analysis also allows you to compare a user’s activity to activities of other employees with similar duties. Thus, the system can detect when a user exceeds their authority or begins to look for something that might be stolen and sold for financial gain.
5 Levels of User Behavior Monitoring
Conclusion
Detecting a malicious insider is a complicated task for organizations, as it’s not only a technical problem. With close cooperation between human resources and IT security departments, you can identify early indicators of insider attack. This allows companies to implement targeted monitoring and detect malicious insiders before they cause damage.
Using Ekran System for insider threat protection, you can identify malicious insider threats in real time and stop any actual attack immediately. Try the 30-day trial to see for yourself how our platform can enhance your cybersecurity!







