Using unapproved tools, software, and devices is risky. You never know what vulnerabilities so-called shadow IT may have. The pandemic that began in 2020 put a new spin on the shadow IT problem. The sudden need to handle all processes remotely was a true challenge, since the majority of corporate networks were not configured to be safely accessed by employees from home.
Although it may seem that telecommuters got used to the security rules for remote work, there’s a risk they learned how to get around them. Using unauthorized third-party software while accessing corporate networks may pose a danger to an organization’s critical assets. In this article, we define what shadow IT is and why employees use unapproved software. We also specify major cybersecurity risks that can be caused by shadow IT and offer six ways to effectively address them.
Shadow IT: definition and types
What is shadow IT?
Shadow IT refers to any IT system, solution, device, or technology used within an organization without the knowledge and approval of the corporate IT department.
Common examples of shadow IT are cloud services, file sharing applications, and messengers that aren’t explicitly allowed according to an organization’s cybersecurity rules and guidelines. The risk of using such software is that it can have cybersecurity flaws and lead to various incidents like sensitive data exposure.


Definition of shadow IT by Gartner
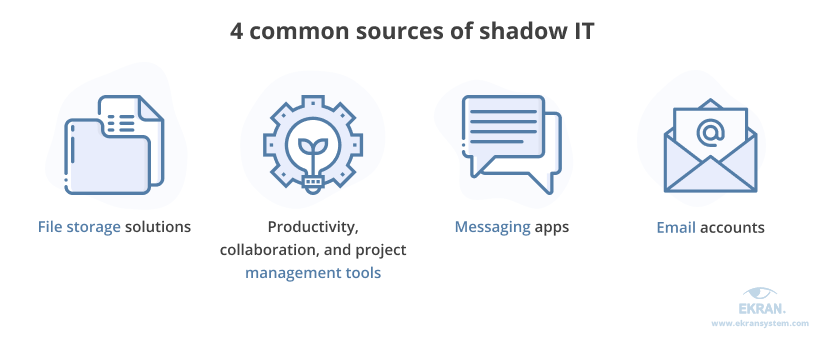
There can be various sources of shadow IT. The four most common are:
- File storage solutions. Employees often need to share files, folders, and screenshots with each other. The danger is that they can choose solutions that don’t secure data well enough, such as Lightshot, whose captured screenshots can be openly accessed. Using personal Dropbox and Google Drive accounts also constitutes insecure data sharing.
- Productivity, collaboration, and project management tools. Aiming to better organize teamwork, collaborate with colleagues, and improve productivity, employees often experiment with online services. But using insecure tools like Trello, Asana, and Zoom for sharing work-related information may be a cause of unintentional data leaks.
- Messaging apps. People often use messengers for both work-related and non work-related chats. This can be a severe cybersecurity issue if workers share corporate files, data, and credentials within insecure messengers like WhatsApp, Signal, or Telegram. To avoid that, it’s essential to ensure the communication tools your employees use are consistent and secure.
- Email services. The majority of employees have at least two email addresses: a personal and a corporate. With an average of 121 sent and received business emails per employee each day, workers can get mixed up between their email accounts and unintentionally expose sensitive data to third parties.

To efficiently address the risks of shadow IT, we need to understand why employees turn to unapproved IT solutions in the first place. Let’s explore the most common reasons in the next section.
7 Best Practices to Prevent Intellectual Property Theft
Why do people use shadow IT?
In most cases, employees find an organization’s IT solutions inefficient. Instead of sticking to them, workers adopt new technologies that help them do their jobs faster and achieve better results. Another possible reason is that employees simply have their own set of preferred software and services they feel comfortable working with.
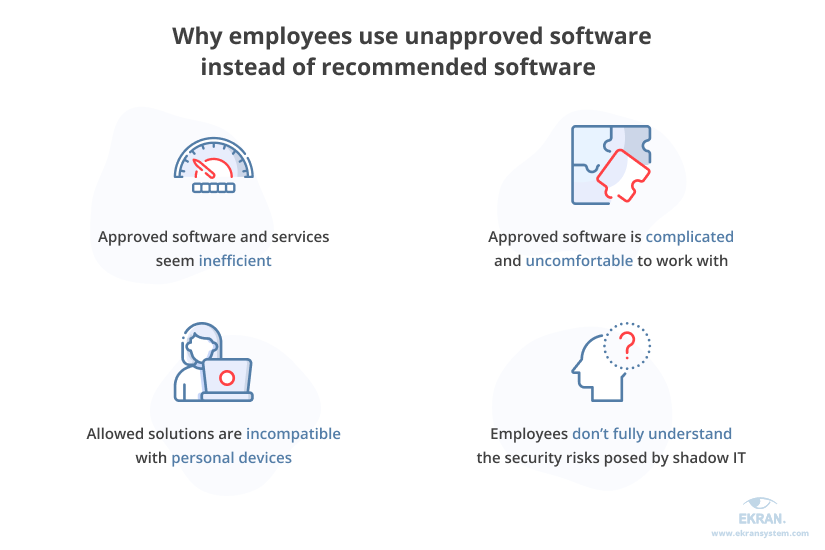
Let’s explore the most common reasons why people choose unapproved IT solutions over standard software packages:
- Employees find approved software and services inefficient
- Approved software is complicated and uncomfortable to work with
- Allowed solutions are incompatible with employees’ devices
- Employees don’t fully understand the security risks posed by shadow IT

As you can see, a common problem is that corporate IT infrastructure operates slowly and makes day-to-day work processes inconvenient. Plus, regular users often don’t know which solutions belong to shadow IT and what risks they pose. So instead of turning to the corporate IT department for help and assistance, employees start using unapproved software and services for their day-to-day work.
Why do you need to keep an eye on shadow IT?
What are the risks of shadow IT?
The presence of unknown and unapproved software and devices within organizational networks creates a lot of issues for cybersecurity departments.
In April 2021, Insight Global admitted that the personal information of some Pennsylvanians was exposed to third parties. This unintentional data leak was caused by employees who used several Google accounts for sharing information as part of an unauthorized collaboration channel. This data included names of people who may have been exposed to COVID-19, emails addresses, and other information needed for social services.
Security gaps caused by shadow IT can also create new opportunities for hackers. Hackers can hijack a vulnerable device that’s connected to a corporate network (this could be someone’s personal laptop or smartphone) and use it to exfiltrate data or launch a DDoS attack.
Here are the six most significant risks and challenges posed by shadow IT:


Lack of IT control
If your IT department doesn’t know about software that exists within the corporate network, they can’t check whether it’s safe to use and ensure that corporate assets are secured. This lack of control over the solutions used within the corporate network can expand attack surfaces.
Data loss and data leaks
When using shadow IT solutions, some employees may get access to data they aren’t supposed to have access to. Another problem is the risk of losing critical data. There’s a chance that an unapproved application doesn’t ensure data backups and that employees haven’t thought about creating a proper recovery strategy. Thus, if something happens, important data may be lost.
Unpatched vulnerabilities and errors
Software vendors constantly release new patches to resolve vulnerabilities and fix errors found in their products. Usually, it’s up to a company’s IT team to keep an eye on such updates and apply them in a timely manner. But when it comes to shadow IT, administrators can’t keep all products and devices up to date simply because they’re unaware of their existence.
Compliance issues
Shadow IT may break compliance with various regulations, standards, and laws, which in turn may lead to fines, lawsuits, and reputational losses. For instance, under the General Data Protection Regulation (GDPR), organizations are obliged to process users’ personal data lawfully, fairly, and transparently. But without knowing all of the software used by their employees, companies can’t ensure that only authorized workers can access sensitive data.
Meeting IT Compliance Requirements
Inefficiencies
Even though boosting efficiency is one of the reasons many people start using shadow IT in the first place, chances are high that the result will be the complete opposite. Every new technology needs to be checked and tested by the IT team before being implemented in the corporate infrastructure. This is necessary to ensure that new software works correctly and that there are no software and hardware conflicts or serious failures.
Financial risks
Unapproved software and services often duplicate the functionality of authorized ones, meaning your company spends money inefficiently. Apart from that, shadow IT risks may lead to real incidents, which in turn incur expenses for damage control, fines for non-compliance with cybersecurity requirements, and legal fees.
Remote Employees: How to Manage Insider Risks
What to do with shadow IT in your organization?
The short answer is to improve management of all technology resources.
There’s no sense in trying to get rid of shadow IT completely, since workers will always find ways to use solutions they want. Moreover, shadow IT can help your organization improve the efficiency of its business processes.
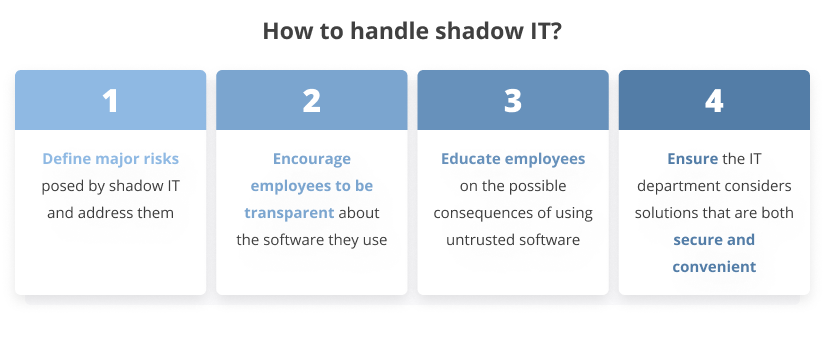
The best tactic for dealing with shadow IT is to:
1. Define major risks posed by shadow IT and address them. We’ll take a closer look at mitigation tactics in the next section.
2. Encourage employees to be transparent about what software they use. First, this will help you detect the use of risky solutions. Second, new tools adopted by your employees may turn out to be more efficient than your standard software.
3. Educate employees on the possible consequences of using untrusted software. Overwhelmed with their routine work, people may forget to mention additional tools they use. But clearly understanding the potential risks and consequences of adopting new solutions will make workers think twice before trying new software without consulting the IT department.
4. Ensure that your IT department considers solutions that are both secure and convenient. There’s a chance your system administrators and IT specialists only pay attention to security details of software, ignoring its convenience for workers. Establish communication between employees and the IT department to make sure they agree on software that meets both security requirements and employees’ expectations.

When approaching the shadow IT problem carefully, you can not only detect cybersecurity risks but also test various technologies and choose more efficient tools for your organization. Doing so may help you optimize your expenses and find weak spots in current work processes.
Now, let’s explore in detail how you can address common shadow IT risks.
Third-Party Security Risk Management
How to mitigate shadow IT risks
In order to get the most benefits out of your employees’ initiatives, you should be able to mitigate risks coming from the use of shadow IT. Here are six efficient strategies for mitigating shadow IT security risks in your organization:
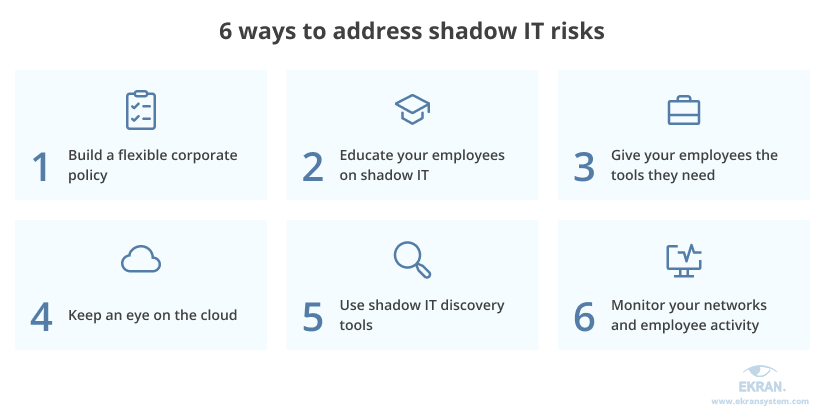

1. Build a flexible corporate policy
A well-thought-out corporate policy that addresses your business’s most critical cybersecurity issues is a must.
To achieve it, start with establishing comprehensible guidelines around the use of personal devices, third-party applications, and cloud services. For starters, you can divide your software into categories to help employees better understand the risks of using shadow IT and offer them alternatives.
Here are examples of categories in which you can place shadow IT resources:
- Sanctioned. Tools that are approved by an organization’s IT department and recommended for use within the corporate network
- Authorized. Additional software whose use is allowed
- Prohibited. Potentially dangerous solutions that may have vulnerabilities or store data insecurely
In case employees want to use solutions absent from the lists of sanctioned and authorized software, they should first ask your IT department to check their security. After checking a tool’s security, the IT department will then add it to the sanctioned, authorized, or prohibited category.
2. Educate your employees on shadow IT
One of the most effective ways to mitigate shadow IT risks is to educate your employees about the true dangers of using unapproved software. People often don’t fully understand the possible consequences of their actions and don’t realize the risks.
By explaining the true reasons behind shadow IT prohibitions, you can significantly lower the number of unsanctioned software installations. Also, it will help you encourage workers to be more transparent about the difficulties they have with approved solutions and the true reasons for secretly deploying alternatives.
People-centric Security for Remote Workers
3. Give your employees the tools they need
Remember why people usually turn to shadow IT in the first place? In most cases, it’s because the standard corporate tools aren’t effective and convenient enough.
A good practice is to create a space for open communication between workers and the IT department. When you learn what your employees really need, you can find efficient software and eliminate the risks of employees using unapproved software in secret.
In case a solution your employees want to use isn’t secure enough or may lead to non-compliance with requirements, it’s essential to clearly explain potential risks. And if possible, offer alternatives that provide the required data security.
4. Keep an eye on the cloud
Not all cloud-based services provide decent data security. Various SaaS products and cloud services like Salesforce and Dropbox hold a special place in shadow IT.
According to a 2021 survey, among 86% of respondents, the annual cost of cloud accounts was over $500,000. The risks of data leaks are especially high if your employees choose freemium models and continuously move from one tool to another, leveraging free trials and putting sensitive data at risk.
This is why it’s crucial to make sure that cloud-based solutions approved for use within your organization are secure and consistent.
5. Use shadow IT discovery tools
Without knowledge, there’s no control. Detecting unapproved applications will help you instantly take necessary actions and minimize possible consequences.
To do that, adopt solutions that monitor your corporate networks and detect:
- Anomalous network activities
- Software downloading and installation
- Data and workload migrations
- Other indicators of possible shadow IT practices
6. Monitor your networks and employee activity
Monitoring what happens within your corporate network is an effective way to gather information about the software, applications, and web resources your employees work with. Based on this knowledge, you can detect who in your company starts using unapproved IT solutions and when.
Apart from that, you can apply user activity monitoring to detect and address insider threats. Also, employee monitoring can help you comply with various cybersecurity laws and regulations, since a lot of requirements oblige you to ensure that only authorized users can access sensitive data.
Ensure efficient and robust monitoring with Ekran System
Ekran System is an insider risk detection platform that provides you with complete information about user activities, whether users are in-house employees, remote workers, or subcontractors.
Our solution thoroughly records employees’ activities, capturing a wide range of metadata such as launched applications, keystrokes, and opened websites. When reviewing user session records, you can easily search for parameters and detect the use of prohibited software in only a few clicks.


Ekran System can help you:
- Monitor software use. See what kind of software your employees use and how. This allows you to not only discover shadow IT sources but also understand how shadow IT originated and why it persists.
- Monitor internet use. Receive information about the websites visited by your employees and the time spent on each. In this way, you can discover unauthorised use of cloud services.
- Monitor and block USB devices. Detect connected USB devices and block them automatically or manually. This can be useful in stopping shadow IT, particularly if the use of USB devices is prohibited by your company’s security policy.
- See firsthand what happens to your sensitive data. With Ekran System, you can see exactly how your sensitive data is accessed and used — and by whom. This can help you detect and target shadow IT applications that directly interact with sensitive data. Then, you can adjust the selection of approved software in order to improve the effectiveness of current processes and mitigate the need for shadow IT.




Conclusion
Shadow IT is not only a cybersecurity issue but also can be a symptom of an inefficient IT strategy. By listening to the needs of your employees and providing them with tools that are both effective and secure, you can significantly reduce shadow IT-related risks and increase your employees’ productivity.
Still, clearly understanding the possible danger from shadow IT is vital for ensuring proper security of your organization’s critical assets. Once you define shadow IT risks, you can better detect the use of insecure software, establish continuous user activity monitoring, and plan employees’ cybersecurity education.
If you’re ready to enhance your cybersecurity strategy with an efficient user monitoring solution, try Ekran System. Request a 30-day trial to see how exactly our solution can meet your needs.





