More than 446 million records were leaked during 2018, according to the 2018 End-of-Year Data Breach Report by the Identity Theft Resource Center. If you’ve been waiting for a sign to start enhancing your data security, here it is. Choosing a reliable monitoring solution is half the battle. But first, you’ll have to figure out the pros and cons of the major types of security systems.
Active data leak protection (DLP) and passive monitoring are two classic and trusted approaches to data protection. The debate between users of both methods has been going on for years. We’ve compared DLP and passive monitoring, analyzed their strong points and limitations, and made recommendations as to which approach may better suit your requirements.
What is a data leak protection solution?
Data leak protection (DLP) solutions are designed to prevent potential data breaches from the inside. Depending on the type of solution, a DLP can monitor, detect, and block operations with sensitive data at rest, in use, or in motion. Such solutions make a system transparent and allow you to set up constant data monitoring.
DLP technology has been around for years. It has proven a worthy tool in defending against both insider and outsider threats. Today, it’s become more complex, able to differentiate between several types of sensitive information and compatible with cloud applications.
A DLP solution requires a data classification policy. This policy defines what information inside the network is considered sensitive and therefore needs protection. A policy can identify the following types of data:
- public – data that can be made available to the public. Publishing this data wouldn’t harm your organization in any way.
- business use only – data that defines the workflow of your company (e.g. company structure, a list of company phone numbers, etc.). Such information is useful only inside the organization, and its leakage could hardly result in losses.
- confidential – data that’s important for key business processes. This includes trade secrets and personal and payment card information of employees and clients. If this data were leaked, it would surely cause substantial damage to the company.
A DLP system is a good choice for protecting confidential data, as it identifies such data in motion and prevents unauthorized disclosure. Some DLP software can also encrypt sensitive data when it’s sent outside your protected perimeter. This functionality can prevent a data leak through sending an email or copying data to a storage device. There are three major types of DLP solutions commonly used in organizations: network, endpoint, and cloud. Let’s consider their pros and cons.
Network DLP
A network DLP (NDLP) solution is an internet gateway or proxy server and does not use software installed on client computers. An NDLP can be a virtual machine or a physical box that scans all data in motion in the network. If a violation of the corporate security policy is detected, the NDLP system blocks this action. For example, if an employee sends some sensitive data via email or uploads it to Dropbox, an NDLP can:
- audit the content
- notify security personnel about a suspicious activity
- notify the user of a rule violation
- encrypt the data
- quarantine the secure transmission
- block the transmission.
However, there are two major cons of a DLP of this type:
- It can only protect data hosted inside your network. If an employee needs to work from home or any other location, you lose control over what’s happening with your data.
- An NDLP doesn’t offer reliable protection against insider threats. Employees or anyone who has stolen their credentials has authorized access to your data. Moreover, some insiders know NDLP settings and can try to bypass the system.

Endpoint DLP
An endpoint DLP (EDLP) system deals with data at the source. Unlike network-based solutions, an endpoint DLP can analyze both internal activities and external communications of a given workstation. It runs client software on end-user workstations, intercepting and analyzing data such as:
- user inputs
- internet connections
- application activities
- USB connections
- data copied/pasted in sensitive files.
As a result, a typical corporate EDLP solution offers data protection even when a monitored device is connected to a public network. It detects suspicious activity performed by a trusted employee. These are the main pros of a DLP of this type.
Monitor Employees Who Work From Home
The downside of EDLP solutions is that they’re difficult to deploy and maintain. EDLP software has to be installed on every company machine. So the bigger your company is, the harder it is to introduce an EDLP system. Also, this type of DLP monitoring requires more elaborate policies and interferes with the company workflow.

Cloud DLP
Several solutions offer data leak protection that focuses on cloud services. With most company activities moving to the cloud, this type of DLP is becoming popular. Such a solution allows:
- scanning and auditing data stored in the cloud
- blocking, encrypting, and alerting on suspicious activities
- maintaining visibility in your network.
There are cloud solutions that offer agent-based monitoring for each endpoint or observe a single proxy server. Network activity analysis and data encryption are performed in the cloud. This saves company machine time and resources.
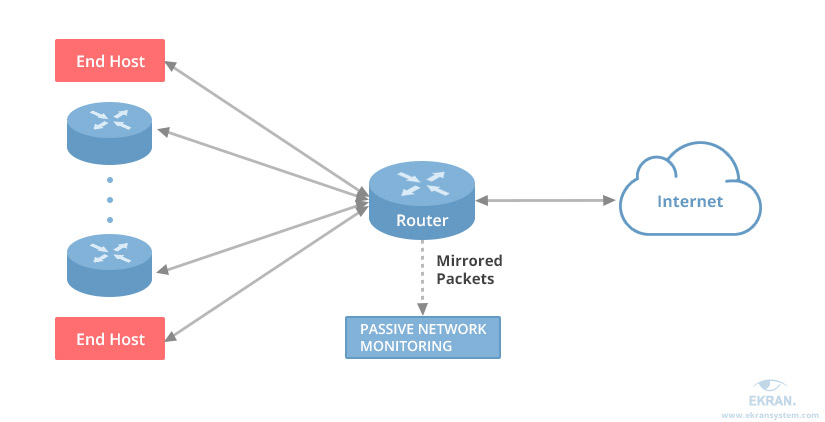
What is a passive network monitoring solution?
A passive network monitoring system analyzes network activity continuously. To do that, the software creates a span or mirror port and copies all traffic coming through it. Such a solution can collect a vast amount of data on user activity over a long period of time. For example, it can record:
- protocols
- applications used (if they require an internet connection)
- data sent through a port
- bandwidth usage (pegged to network users, allowing you to detect if some of your employees send a large amount of data)

Linux User Activity Monitoring
There are a few pros of passive monitoring:
- It doesn’t overload a network with additional traffic.
- It provides an overview of network activity.
Passive monitoring is useful for both monitoring user activity and troubleshooting network issues.
The cons of passive monitoring are that it’s resource-intensive, time-consuming, and requires significant financial investment. Many passive monitoring solutions aren’t exactly easy to use, as they generate a set of log files for various aspects of system use and data access operations. Passive monitoring solutions won’t help with catching attackers in the act, but they can collect all data about their activity.
Experts recommend using passive, non-intrusive monitoring of all network users combined with instant alerts and fast incident response. This approach takes away the guesswork of common DLPs and gets rid of roadblocks that intrude on business process.
Take a look at the best cyber security practices.
Does an ideal solution exist?
User activity monitoring combines the pros of both active and passive monitoring. It collects extensive data on user activity both in your network and on endpoints, alerts security officers to suspicious events in real time, and offers tools to suspend or terminate activities.
Modern user activity monitoring software intercepts user activities and supplements raw logs and text-based reports with live video streams captured on user workstations.
These systems index the video stream with other text-based information collected from the same workstation, placing searchable markers onto the video stream. As a result, discovering information relevant to a certain incident becomes easier, while watching the video stream reveals far more detailed information regarding the incident than any text-based log can.


Conclusion
Both active DLP and passive network monitoring solutions are well-known and widely used to protect corporate data. But as the market and cybersecurity landscape change, they’re sometimes considered old-fashioned. The best decision would be to combine both approaches or to deploy a more advanced solution.
While not replacing your data encryption system, Ekran System monitors and audits any actions inside your network performed by independent service providers, employees, and other insiders. This computer surveillance system captures on-screen user activities of regular and privileged users and creates fully indexed and easily searchable video streams. Ekran System can monitor all workstations and servers on the corporate network including local sessions, RDP connections, and AVD environments.
Besides monitoring, Ekran System provides you with a robust toolset for incident alerting and immediate incident response. When suspicious activity is detected, the software alerts security officers and enables them to alert the user, terminate the activity, or block the user completely. Also, Ekran System uses monitoring data to create scheduled and ad-hoc reports. If a data breach happens, information about this incident, all involved parties, and the context can be gathered and exported to an encrypted file for further forensic activities.
In our white paper, you can find more details about the debate between users of active DLP and passive monitoring approaches to help you choose the best solution for your company.





