Establishing proper privileged account management procedures is an essential part of insider risk protection. There are some common mistakes companies make when managing accounts of privileged users.
In this article, we overview eight widespread poor account management practices, analyze their consequences, and discuss ways to improve them. We also take a look at Ekran System’s account management capabilities that you can benefit from.
1. Approving all access requests manually
Manual access approval is widely used in small and medium-sized companies. This practice allows a security officer to review each request and provide access manually.
Approving access manually is sufficient in two cases:
- For companies with up to 10 employees. In this case, a security officer can keep up with access requests. However, it may take a lot of time for security officers to monitor whether employees misuse their access permissions. Moreover, an administrator can make a mistake and grant access to a user who doesn’t need it.
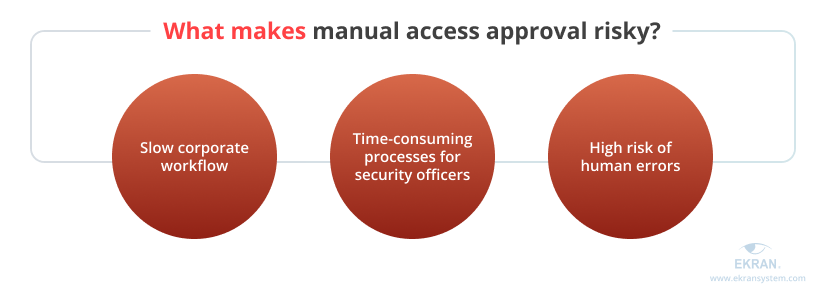
- For securing the most sensitive resources. Some types of corporate data and resources are highly valuable, so you really need to manually examine any requests to access them. But when working with many ordinary resources, manual approval slows down the corporate workflow because employees have to wait for access permission.
When applied outside of these use cases, manual approval of all access requests can subject your organization to additional security risks. This poor account management practice gives more room for wrong decisions and human errors made by security officers.
According to the 2022 Satori State of DataSecOps In the Cloud Report, 61% of 20,000 data and analytics professionals in North America faced errors and limitations of capabilities when requesting access to data because of manual tools and processes.
Here are the key drawbacks of manual approval of all access requests:

Instead of completely relying on manual access provisioning, you can leverage automated access control that helps your security officers establish quick and reliable access approval procedures.
Dedicated access control solutions allow for creating custom access rules for regular privileged users and user groups. Based on the rules you set, access will be granted or blocked automatically. Also, such software can alert security officers about suspicious access requests and possible security violations.
You can also combine automated and manual access approval to configure different protection levels for different resources. For example, you can automate access provisioning to ordinary resources and have your security officers manually review requests to access sensitive resources.
2. Granting privileged access to everybody
Privileged access is called privileged for a reason. It must be granted only to those who need it for day-to-day duties. But users often end up with additional privileges assigned to their accounts.
Overprivileged accounts can appear for several reasons:
- The organization doesn’t have a strict privileged access policy and each user is assigned the same set of access rights.
- A user requests one-time access to a sensitive resource, but the administrator doesn’t revoke privileges after the task is completed.
- An employee acquires a new position within the company and possesses privileges for both the old and new positions.
- A third-party vendor gets a default privileged account instead of an account with a custom set of access rights.
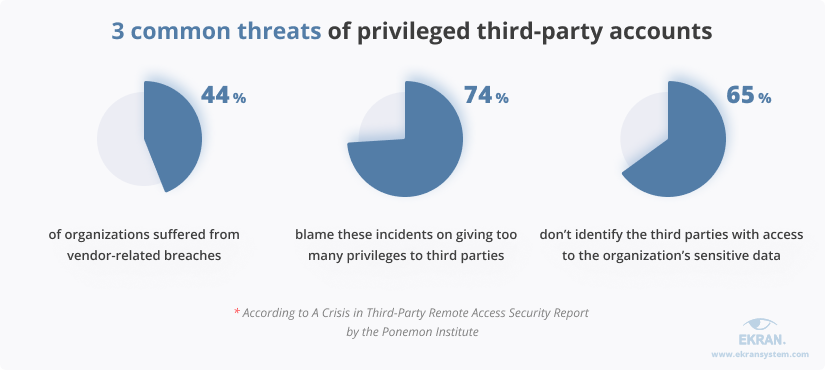
Third parties are one of the most dangerous types of insiders, as it’s hard to make sure that they pay attention to cybersecurity and don’t have malicious intentions. A Crisis in Third-Party Remote Access Security Report by the Ponemon Institute shows that 63% of organizations choose their vendors by reputation and don’t assess a vendor’s cybersecurity posture. And 44% of organizations suffered from vendor-related security incidents in 2021.

However, some vendors like IT service providers and auditors really need privileged accounts to do their work. This calls for strengthening security measures, performing regular user access reviews, implementing Active Directory auditing best practices, as well as deploying privileged access management and vendor monitoring.
Such capabilities allow your security officers to take privileged accounts under full control. They can define custom access control rules for various groups of privileged users, including vendors. With continuous third-party monitoring, security officers can review user activity, detect threats associated with privileged user accounts, and respond to them in real time.
Ginegar Secures Third-Party Access and User Activity with Ekran System [PDF]
3. Using an overcomplicated PAM policy
As with any good deed, it’s easy to go overboard with a privileged access management policy. An overly complex cybersecurity policy is a typical PAM risk for large organizations that have many types of sensitive resources and levels of privileged access.
Due to this, resetting user passwords may take up to 30 minutes. Providing a new employee with all the necessary access permissions can take a few days or even weeks.


If your company is like this, it’s a good call to reconsider your cybersecurity policies. Complicated procedures may cause the appearance of shadow IT. And to avoid shadow IT problems, you should review your policies and make them less complex.
One of the most dangerous outcomes of complicated security policies is leaving privileged accounts unregistered. These unregistered accounts can be used to carry out attacks similar to the one that targeted Colonial Pipeline.
Colonial Pipeline suffered a ransomware attack carried out via an unused VPN account. Hackers gained privileged access to the company’s Active Directory and stopped the company’s operations for approximately a week, forcing Colonial Pipeline to pay $5 million.
You can simplify your security-related procedures by deploying automated privileged account and session management (PASM) as well as access management solutions. They provide security officers with the ability to track privileged accounts as well as to grant, revoke, and manage their access rights automatically. These solutions can also record privileged sessions, which is useful for investigating suspicious activity.
Privileged Account and Session Management: How To Deploy It
4. Sharing privileged accounts
Many companies have admin and root accounts with credentials known to any network administrator.
Such accounts are dangerous for several reasons. First, the more people know the credentials of a privileged account, the higher the chance for a hacker to obtain those credentials. Second, it’s hard to determine which employee logs into a shared privileged account. Therefore, it’s difficult to connect a security incident with a particular user.


Unauthorized access via shared credentials is the most common way of hacking web applications and services according to the 2022 Verizon Data Breach Investigation Report. However, that doesn’t mean you should ban shared privileged accounts for good. You can protect these accounts from access abuse with additional security mechanisms.
You can enforce secondary or multi-factor authentication (MFA) to positively identify users. Secondary authentication checks the identities of people behind shared privileged accounts. And MFA adds additional authentication factors to confirm the identity of the person logging into the system.
5. Mismanaging accounts of terminated employees
A fired or soon-to-be-fired employee is one of the common types of malicious insiders. They know what sensitive data a company possesses, what security policies are implemented, and which vulnerabilities may be abused.
While they still have their privileged account permissions, they may create:
- A backdoor. A privileged account with access to sensitive data won’t trigger a monitoring system alert. A hacker or a disgruntled ex-employee may use it to access an organization’s critical data.
- A way to blackmail the company. This is possible if the employee had exclusive access to some resources.
There are plenty of ex-employee revenge cases out there. For example, a former employee of a medical device packaging company, Christopher Dobbins, damaged corporate data in March 2020, after he’d been fired. He sabotaged electronic shipping records by using a fake administrative account he created before his termination.
To avoid this risk, make deleting ex-employee accounts a regular task. You can do it by conducting regular audits of privileged user activity or making account termination a necessary step of the employee termination procedure.
Another way to secure unused accounts is to automate the management of user credentials. With dedicated software, you can regularly change credentials and reset them every time an employee with access to a shared privileged account leaves.


7 Best Practices to Prevent Data Theft by Departing Employees
6. Overlooking cloud security gaps
Because of the COVID-19 pandemic, many businesses went through rapid and unplanned adoption of cloud services. In doing so, they prioritized the usability and productivity of new services over security mechanisms and access controls.
A lack of focus on cybersecurity often leads to gaps in cloud protection in terms of:
- Identity governance
- Privileged access control
- Visibility into privileged cloud activity

Multi-cloud identity and access management (IAM) and cloud infrastructure entitlement management (CIEM) systems can help you close the security gap in the cloud. These solutions detect the accumulation of privileges, anomalies in entitlements, and other cloud access problems mostly by using analytics and machine learning.
You can also benefit from a privileged user activity monitoring system that can be deployed in the cloud. With it, your security officers can configure flexible access rights for privileged users, reconfigure overprivileged accounts, and secure connections to cloud services.
7. Mismanaging privileged machine accounts
A lot of organizations leave default security settings for privileged machine accounts, as they don’t realize that privileged access isn’t limited to humans. Non-human accounts are used by:
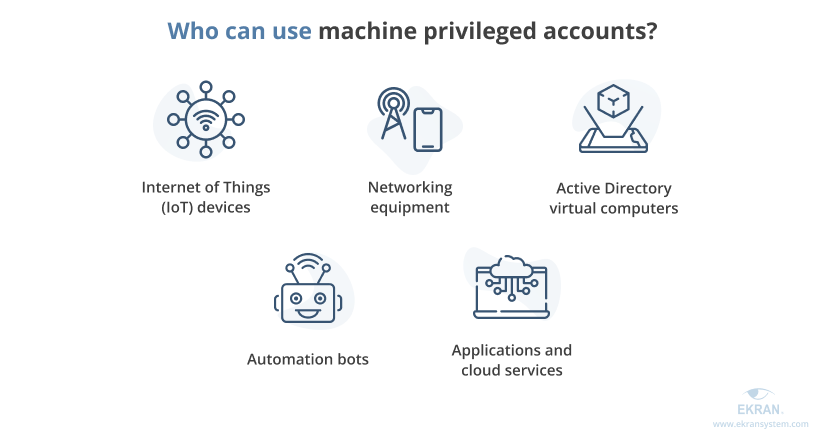

All these accounts can access an organization’s network and sensitive data even if they aren’t assigned to a specific human user. Attackers can use non-human accounts to gain privileged access and get past the security system. You can protect such accounts with the following measures:
- Limit machine access to the specific purpose or functions these machine accounts were created for
- Include privileged machine account access rules in your corporate cybersecurity policy
- Investigate unusual machine account activity picked up by user and entity behavior analytics
- Implement automated activity monitoring for non-human activity
- Set up custom alerts on any abnormal machine activity
- Manage credentials for machine privileged accounts automatically
Remote Employee Monitoring. How to Make Remote Work Effective and Secure
8. Leaving credential management to users
Privileged accounts belong to those who can make the biggest changes to your systems and access your most sensitive data. When you leave privileged credentials unmanaged, you leave the main door open. What are the risks of this? Let’s take a look:
- Privileged users might accidentally leak their credentials by falling for phishing attacks or leaving their passwords written on a piece of paper. Such actions can lead to exposing your sensitive resources to hackers or malicious insiders.
- Employees may use weak passwords or reuse old ones that can be guessed or brute forced.
- Privileged users can share their credentials with other users, reducing the transparency of access control and increasing the risk of unauthorized access to sensitive data.

With automated credential management, you can protect access to privileged accounts on your own. Such solutions create, provide, rotate, and dispose of credentials in a secure manner and with no direct user involvement. They also encrypt the passwords they store, adding another level of protection.
Privileged Password Policy Compliance Overview: NIST 800-63, HIPAA, PCI DSS, GDPR
Manage privileged accounts with Ekran System
You can eradicate poor PAM practices and improve your account management routine by establishing clear and easy to follow security rules, as well as by automating routine security checks. Ekran System is an all-in-one insider risk management solution with privileged access management and privileged user monitoring functionalities that can help you take control over the privileged accounts in your network.


You can use the following Ekran System capabilities:
- User activity monitoring to track and record the activity of all user accounts on protected endpoints. Constant privileged user monitoring and audit can help you see which privileged users misuse their accounts and violate security rules.
- Identity management to verify the identities of users that access privileged accounts and critical resources. With multi-factor and secondary authentication procedures, you can be sure that only authorized users can log into privileged and shared accounts.
- Privileged access management provides you with numerous tools to configure access rules for privileged accounts and groups of accounts and provide access to the most sensitive resources manually.
- Password management automates all credential-related procedures: creation, rotation, encryption, storage, delivery, and termination. Your security officers can set requirements for the strength of created passwords and the rotation period, and they can edit stored credentials manually.
These capabilities will help you implement privileged account management best practices and eradicate possible gaps in your organization’s protection.
Conclusion
Poor practices of privileged account management can reduce the efficiency of your cybersecurity systems and put sensitive data at risk of accidental leaks and hacking attacks. Ekran System helps to improve your account management practices with the ease and convenience of an all-in-one solution.
Our insider risk management platform provides a robust toolset to control privileged accounts, manage access and user identities, and monitor privileged activity.
Deter, detect, and disrupt insider threats in your IT infrastructure.
Take a proactive approach to managing human-related risks with Ekran System. Manage users’ access, monitor their activity, and respond to threats in real time.






