Proper implementation of a user and entity behavior analytics (UEBA) tool can solve lots of cybersecurity challenges by detecting well-hidden and slowly executed attacks, automating the analysis of alerts and logs, and speeding up incident investigation. It can even help you improve employee productivity. But implementing a UEBA solution also requires a lot of time and effort along with a clear understanding of how you are going to use it.
In this article, we analyze what cybersecurity challenges you can address with the help of a UEBA solution. We also discuss how UEBA solutions work, why they are so popular, and what are the key advantages of deploying a UEBA tool and possible downsides of using them.
What is UEBA and why is it important?
User and entity behavior analytics is a cybersecurity technology that helps organizations detect malicious insider activity and external threats at the earliest possible stages. It leverages the power of artificial intelligence (AI) and machine learning (ML) to identify possible security violations and alerts IT and cybersecurity teams to them.
A UEBA’s work is based on behavioral datasets that contain logs of common user behavior: accessed files, visited URLs, work and idle time, typical activities, typing rhythm, and more. UEBA security solutions need this extensive, precise, and well-labeled set of data to study usual behavior and detect suspicious actions.
UEBA technology evolved from user behavior analytics (UBA). As the name suggests, UEBA solutions can detect threats coming from both human users (employees, customers, third parties) and non-human entities (machine accounts, network scanners, software).


UEBA solutions defined by Gartner
It’s especially effective to use UEBA technology to detect these security incidents:
- Suspicious changes in the behavior of employees and third parties
- Compromised user or entity accounts
- Data exfiltration
- Abuse and misuse of privileged access
- Violations of an organization’s security policies
All of these security incidents are hard to detect at early stages. The ability to pick up early indicators of such threats quickly has made UEBA a popular technology on the cybersecurity market.
According to research by ReporterLink, the global market for user and entity behavior analytics was estimated at $549.6 million in 2020. By 2026, it’s projected to reach $4.2 billion.
UEBA solutions sometimes get confused with security information and event management (SIEM) systems. They do have some similarities, but UEBA and SIEM solutions work differently, help you achieve different goals, and can never substitute each other. Let’s take a look at their key differences:
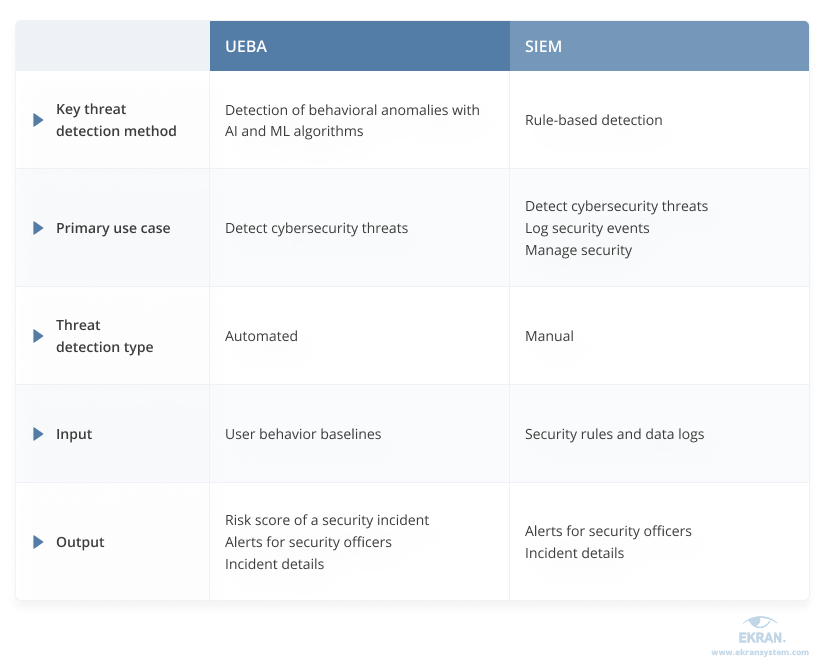

To get maximum efficiency out of UEBA and SIEM, it’s best to combine these tools. But while SIEM systems are common and relatively simple to implement, deploying UEBA tools can raise a lot of questions even with experienced cybersecurity specialists.
Before enhancing your cybersecurity with a UEBA solution, you’ll need to understand the possible advantages and disadvantages of this action. Let’s look at them in the next section.
5 Levels of User Behavior Monitoring
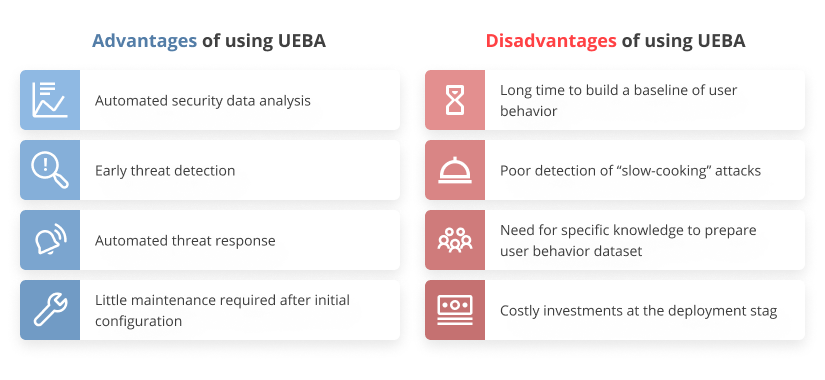
Pros and cons of using UEBA tools
Despite its popularity, UEBA isn’t a silver bullet for all cybersecurity issues in all organizations. Before deploying a UEBA tool, you need to research how UEBA works, clearly define your reason for engaging in user behavior analytics and the benefits of a UEBA solution you want to experience. Then you should analyze possible challenges and downsides of using UEBA and decide if the catch is worth the chase.

As part of a robust cybersecurity system, UEBA can cover the blindspots of traditional security tools like user activity monitoring, SIEM systems, and rule-based access management. Applying user and entity behavior analytics alongside user session recording solution and aforementioned tools allows you to make your security tools more flexible, reduce the number of false positive results, and detect more sophisticated threats.
You can significantly enhance your organization’s cybersecurity with a UEBA solution thanks to advantages such as:
Automated security data analysis. A UEBA tool collects and processes numerous logs of daily user and entity activities and events inside the organization’s infrastructure. Based on these logs, the tool calculates a risk score for each event. This saves security officers lots of time on manual analysis of logs. Instead, they can focus on analyzing high-risk events.
Early threat detection. Traditional cybersecurity tools can detect threats in real time at best. That means a malicious actor can inflict some damage on the organization before their activity is detected and stopped. A UEBA tool picks up changes in user and entity behavior before users or entities start breaking security rules. Detection at early stages often helps to prevent a security incident before any damage is done.
Automated threat response. When a UEBA tool detects suspicious activity, it can usually alert security officers of it or respond to it automatically by blocking the process, user, or entity behind that activity. Automated response stops an attack at early stages and gives security officers time to analyze the incident.
Little maintenance required after initial configuration. The initial configuration of a UEBA tool can be challenging: you have to collect all the data it requires, build user behavior baselines, and train algorithms. However, after the UEBA system starts working, it requires very little attention from security and IT teams. They only may need to fine-tune it from time to time or add a new behavior baseline. The tool’s self-learning algorithms can adjust to the changes in an organization’s security environment.
7 Best Practices for Building a Baseline of User Behavior in Organizations
When deploying and configuring a UEBA tool, you can run into a few challenges:
Lots of time required to build a user behavior baseline. A UEBA solution isn’t efficient out of the box — it needs to be trained on customized user behavior datasets before it starts detecting threats. Usually, training lasts from one to three months. That’s why a UEBA tool won’t be useful if you need to improve your organization’s security urgently. It’s only possible to experience the benefits of a UEBA deployment in long-term use.
Poor detection of “slow-cooking” attacks. UEBA tools are especially effective when a user or entity rapidly changes their usual behavior to attack an organization, e.g. during account compromise or one-time data theft. However, some malicious insiders prefer to take their time for attack preparation and execution. For example, they can access sensitive data and copy some parts of it on a daily basis. In this case, a UEBA tool may not consider these actions suspicious because they are usual for this user.
Need for specific knowledge to prepare a user behavior dataset. You can’t train a UEBA tool on a generic user behavior dataset because users and entities in each organization have different tasks and daily activities. Preparing such a dataset is a tricky task that requires both knowledge of AI and ML and an understanding of the data that constitutes the dataset. That’s why you’ll need to spend some time studying dataset preparation or get help from an external AI expert.
Costly investments at the deployment stage. Configuring, training, and integrating a UEBA tool with other cybersecurity tools takes a lot of time and effort. Since UEBA is based on complex AI technologies, you may need to hire AI experts or involve third-party vendors that can help you fine-tune the tool. Coupled with the price of the UEBA itself, these deployment investments may be too high for some organizations.
You can mitigate the majority of these challenges and disadvantages if you prepare a thought-through implementation approach and define which tasks you want to accomplish with a UEBA solution. Let’s take a look at some common reasons why deploy a UEBA solution.
7 common UEBA use cases
Reasons for implementing a UEBA solution vary greatly depending on the tool’s feature set. However, you can usually employ such software to:
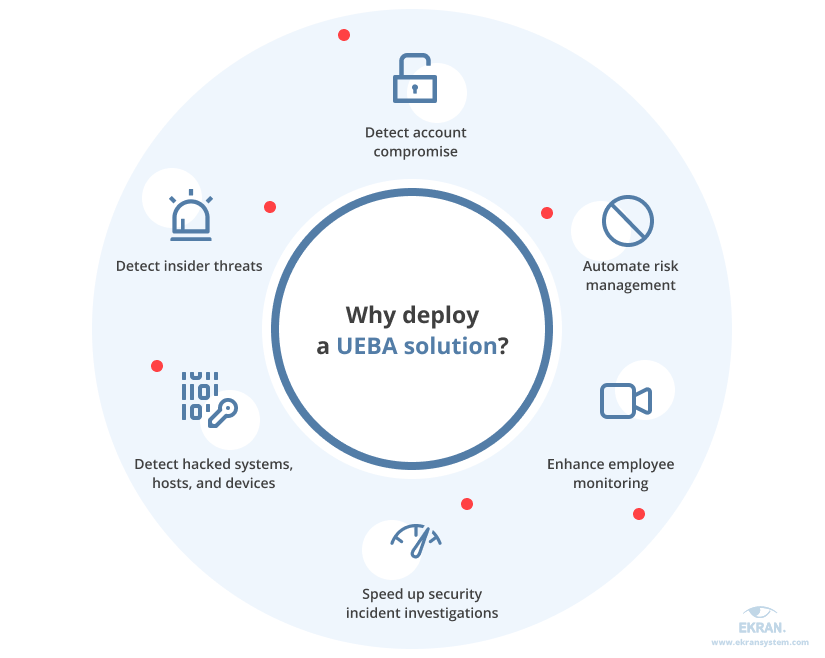

1. Detect insider threats
Protecting organizations against insider threats is the primary use case for a UEBA tool. Malicious or inadvertent insider activity is usually tricky to detect, since insiders know their way around an organization’s cyber defenses. Inside attackers may fly under the radar for months and even years before they trigger a security alert.
Behavior analytics isn’t based on security rules, and that’s exactly how UEBA technology protects from insider threats. It can detect unusual user and entity behavior that can indicate insider threats such as:
- Suspicious access requests that don’t violate access policies
- Installation and launch of new applications
- Sharing credentials with new users
- Data snooping
- Data exfiltration
Even the subtlest changes in user behavior can help to detect threats with UEBA. For example, Ekran System’s UEBA can alert you if an employee accesses a system during unusual hours. This can indicate that they want to be unnoticed while doing something suspicious like stealing data, or that their account has been compromised.
Examples of Human Error in Cybersecurity
2. Detect account compromise
Hacking employee accounts is one of the favorite ways for cybercriminals to attack an organization. It hides their activity from traditional security tools since malicious actors use legitimate credentials to log in to an account. Cybercriminals usually target employees with privileged access to the organization’s resources: IT administrators, security officers, employees that process sensitive data, third parties, etc.
Detecting account compromise is easy for a UEBA tool because hackers can’t emulate the regular behavior of the account owner. Even for a privileged user, it’s suspicious to suddenly start downloading, altering, or deleting tons of data. A UEBA tool will easily pick up on these changes and alert security officers of a possible compromise.
Shadow IT: What Are the Risks and How Can You Mitigate Them?
3. Detect hacked systems, hosts, and devices
Not only human users can access — and abuse — an organization’s sensitive data. In any security environment, there are dozens of privileged entities with no single owner: emergency accounts, network and data scanners, device and host accounts, etc.
Some cybersecurity teams pay less attention to such entities than to users. Malicious actors can leverage that to mask their activity: deploy spyware or a keylogger, or change the entity behavior.
UEBA solutions analyze usual entity activity the same way they analyze user behavior. That’s why they can easily notice when an entity account gets compromised.
People-centric Security for Remote Workers
4. Automate cybersecurity risk management
Implementing cybersecurity risk management procedures is one of the core requirements of many cybersecurity laws, standards, and regulations. It helps organizations keep track of their cybersecurity risks, adopt relevant practices to reduce them, and protect sensitive data.
A lot of risk management activities are done manually. For example, cybersecurity risk assessment requires security officers to describe each threat, its likelihood, and its possible outcome.
Deploying Ekran System can help you automate risk assessment, since Ekran’s UEBA module calculates a risk score for user actions. It also monitors those risks and can alert security officers only of actions that violate security rules or have a high risk score.
Insider Threat Risk Assessment: Definition, Benefits, and Best Practices
5. Enhance employee monitoring
Traditional user activity monitoring is a helpful tool that allows you to keep track of user actions and review them to detect security violations. But it isn’t always enough to detect sophisticated or well-hidden threats. Combining monitoring with UEBA, keylogger, and other tools can help you detect such threats in time and get actionable insights into user activity.


Prepare for Insider Threats by Building Trigger Scenarios report by Gartner (subscription required)
Ekran System provides you with both UEBA and extensive user activity monitoring tools for Windows and other platforms, thus eliminating the need for complex integration configurations. Ekran’s monitoring functionality includes:
- Comprehensive session recording of a user’s screen and metadata on each action
- Possibility to review user activity in real time and in records
- Intuitive review of user sessions with a built-in YouTube-like video player, record filtering, and search by any piece of metadata
- Exporting of monitoring data in a protected format for forensic activities
You can use monitoring data to build behavior baselines and train the UEBA module. After that, the UEBA module will enhance the quality of user activity monitoring and threat detection.
PECB Inc. Deploys Ekran System to Manage Insider Threats
6. Speed up security incident investigations
Analyzing alerts produced by cybersecurity tools can be a tedious task, especially for security officers in large organizations. Even with correctly configured tools, security officers have to deal with false alerts and notifications of low-risk incidents.
UEBA tools can take a lot of stress off security officers by assessing security incidents, prioritizing them, and highlighting important events that require an officer’s attention. They can also help you conduct an incident investigation by highlighting unusual and suspicious user actions.
You can further improve security investigation by creating scheduled and ad hoc incident reports. For example, you can configure Ekran System to send you reports on:
- User or user group activity
- Triggered alerts
- Sessions outside work hours
- Access to terminal servers, forbidden URLs, and sensitive data
- And more
Security Incident Investigation
7. Analyze employee productivity and workloads
Not all employees openly complain about productivity and workload issues. Yet these concerns can lead to employee disgruntlement, resignation, or even malicious activity. Usually, detecting such issues requires the deployment of a dedicated employee productivity management tool. However, you can also discover these issues by analyzing changes in employee behavior picked up by a UEBA solution.
For example, Ekran System can notice changes in an employee’s daily work time. If it detects that an employee has started to work fewer or more hours, it may indicate that they are avoiding doing their work or have too many tasks at hand.
Other ways to detect productivity decreases with a UEBA tool are analyzing the task completion rate, the average time spent on certain activities, and the balance between productive and non-productive time.
With timely alerts from a UEBA module, you can discuss these behavior changes with an employee, identify any issues, and fix them.
Remote Employee Monitoring: How to Make Remote Work Effective and Secure
Conclusion
User and entity behavior analytics helps take your cybersecurity system to a new level by adding AI-based user activity analysis and predictive incident detection. A UEBA tool is especially useful for detecting sophisticated attacks like account compromise, long-term insider activity, and privilege abuse. It can also help you improve employee productivity and balance your workflow.
However, a UEBA tool can’t substitute traditional security tools or become efficient right after deployment. It may take several months to train UEBA algorithms and properly integrate them with other security software.
With Ekran System, you get a UEBA module that is already integrated with user activity monitoring, privileged access management, and incident response functionalities, enabling you to detect, deter, and disrupt security incidents fast. You can also get help with configuring our UEBA module from our support team.






