The challenge
Cybercriminals are persistent in their attempts to appropriate personal information, financial and military data, and other critical assets. As a result, state and local governments face daunting challenges:
Protect critical government data from leaks and breaches
Detect insider threats and efficiently mitigate security incidents
Comply with security and data privacy requirements
Get up-to-date analytics to evaluate potential cybersecurity risks
Watch over third-party vendors’ and remote employees’ activity
Gather enough evidence for effective incident investigation
Ekran System helps government entities to


Protect sensitive
data
Control access to infrastructure by employees and partners and get visibility into how they process data.
Address insider
threats
Continuously analyze your employees’ and partners’ behavior, and automatically respond to suspicious actions.
Meet compliance requirements
Facilitate compliance with NIST SP 800-53, FISMA, and other data protection standards, laws, and regulations.
Improve network
visibility
Closely watch your organization’s attack surface by monitoring and logging activity across various endpoints.
Сomprehensive insider threat management for government institutions
Public administration
Defense agencies
Federal agencies
Government-funded organizations
Establish a secure way for remote employees to access your infrastructure and take control over who can access your critical systems.
Closely monitor your organization’s attack surface and react to incidents promptly to minimize damage.
Constantly monitor user activity and analyze how your employees and contractors process data to detect and deter malicious actors before it’s too late.
Industry recognition
A step-by-step guide to building an insider threat program for government institutions


Insider Threats in the Government Sector: Consequences, Major Challenges, and Mitigation Steps
Download the white paper to gain a deeper understanding of insider threat management in governmental institutions and learn best practices for effective prevention.
Download White PaperHow state and local governments can take control of insider threats with Ekran System
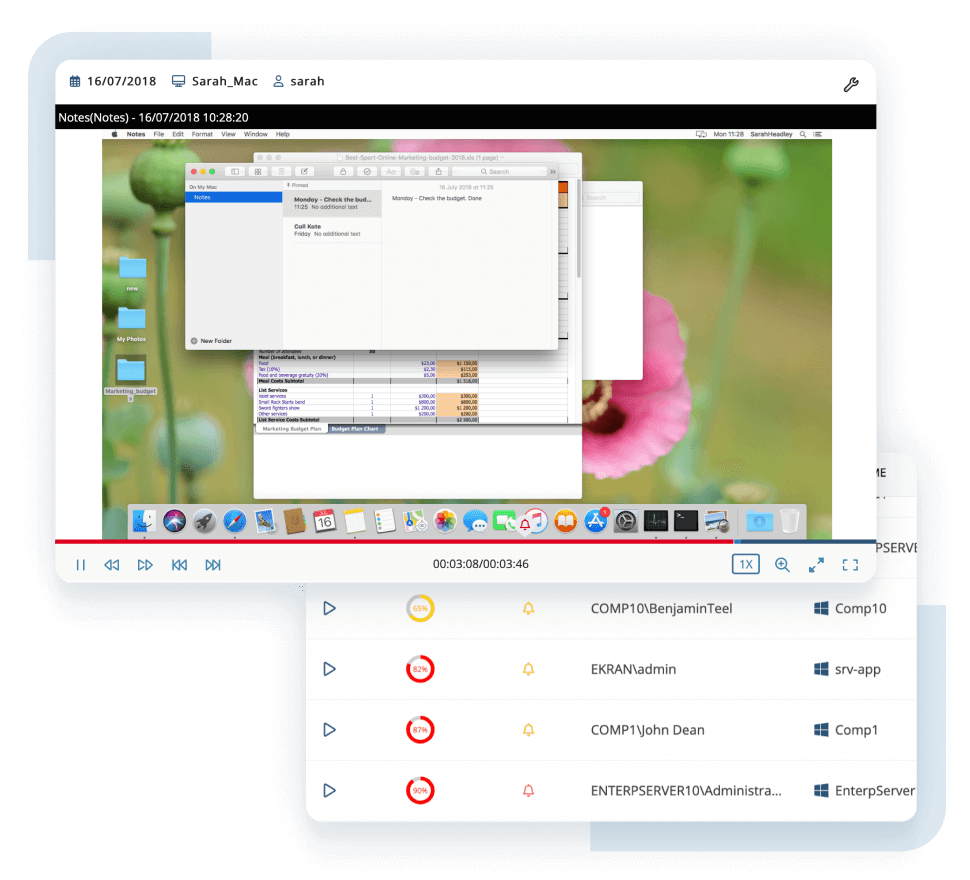
Know how your employees and partners handle your organization’s sensitive assets. With our insider threat protection solution, you can monitor user activity in real time and record it in a screen capture format along with insightful metadata such as visited websites, opened applications, and connected devices

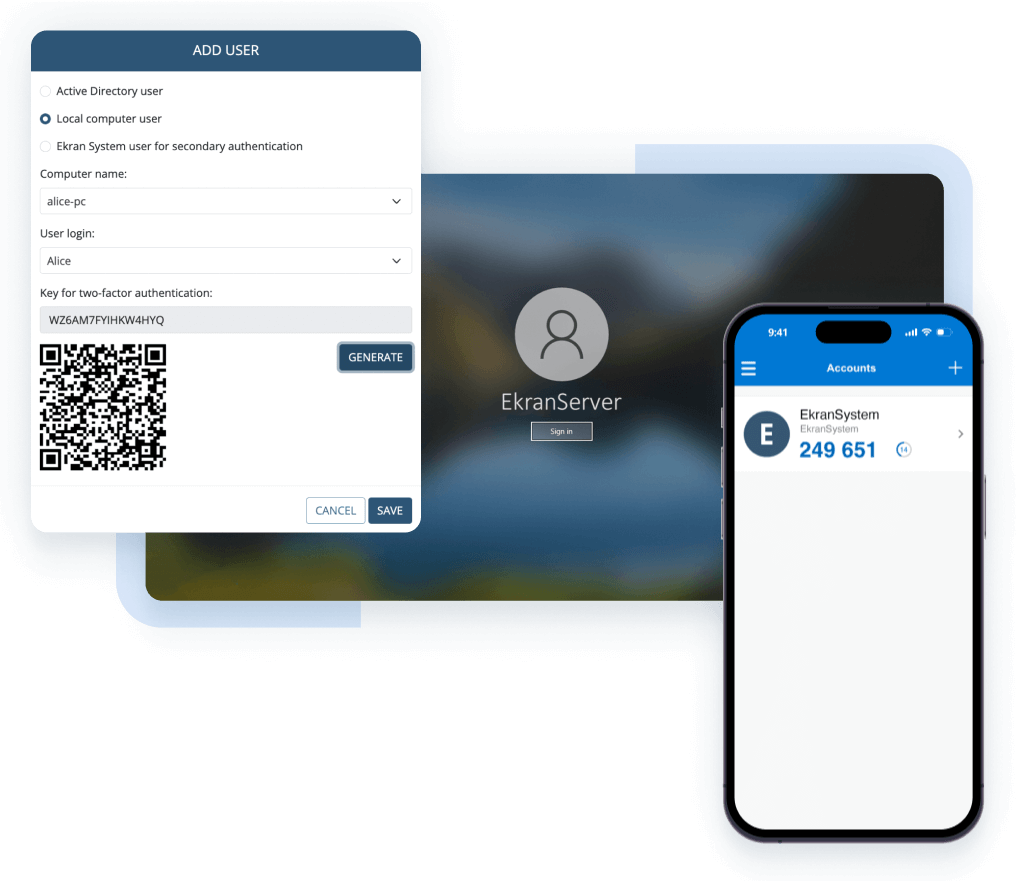
Securely authenticate users to ensure that only those who are authorized can access your critical assets. With Ekran System’s multi-factor authentication and secondary authentication features, you can validate user identities and secure the use of shared and default accounts within your network.

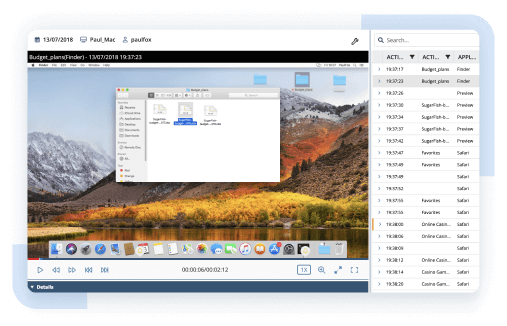
Strengthen the cybersecurity of your government entity by ensuring safe cooperation with third-party vendors. Ekran System allows you to verify users connecting to your organization’s endpoints from outside the network, manage access permissions for remote contributors, and improve visibility over their activity.

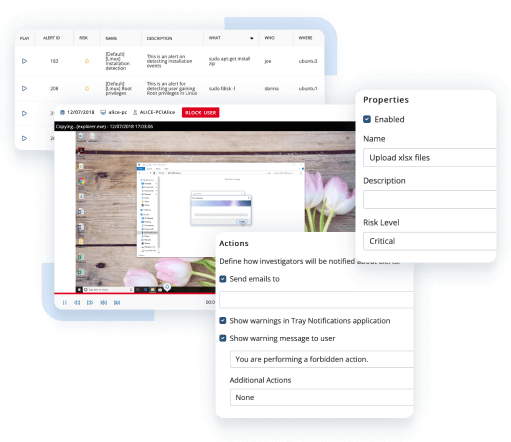
Keep abreast of suspicious activity within your network and timely address security incidents. Ekran System enables you to receive notifications on suspicious user behavior and security policy violations. You can also configure an automated incident response for various scenarios to immediately respond to potential threats.

Accurately analyze data to improve insider risk management in your government organization. Ekran System’s numerous reports and Microsoft Power BI integration provide you with the necessary information to examine the current insider threat landscape and investigate security incidents.

Safeguard privileged access to critical data assets within your organization. As insider threat management software for government entities, Ekran System allows you to manage users’ privileges and ensure that only users with sufficient privileges have access to sensitive areas of your network.

Protect your employees’ and vendors’ personal information and comply with data privacy requirements. Ekran System can remove personal identifiers from data collected during activity monitoring to ensure your users’ privacy. If an incident happens, security officers can de-anonymize data for investigation purposes.


Get more with enterprise-grade insider threat detection software
Visually structured evidence trail resulting in low incident response time
Context-rich recordings significantly reduce CERT and SOC response times. One-click search across suspicious activity makes investigations faster and more effective.
AI-based compromised account detection
Cybercriminals are constantly improving their ways of compromising privileged accounts. Powered by artificial intelligence, the Ekran UEBA module can detect a hacker who has penetrated a corporate system using stolen credentials.
Lightweight software agent and highly optimized formats for storing data
The lightweight agent works silently and isn’t noticeable to users or other programs. Collected data is saved in searchable and highly optimized video, audio, and text file formats for compact log storage and easy reporting.
Active in your environment in 20 minutes or less
Ekran System is quick to install and easily integrates with SIEM and ticketing systems. You’ll get a ready-to-use solution right after a coffee break.
Why companies choose Ekran System®
Ekran System continuously monitors various endpoints, including both end-user machines and servers, within any network architecture. Being one of the best user activity monitoring tools for Windows, Ekran System also works for macOS and is a powerful Linux/UNIX session audit tool. It even supports X Window System and all popular virtualization solutions. Ekran System allows agent-based and jump server-based deployments as well as any combination thereof.
Designed for tracking user activity on tens of thousands of endpoints, Ekran System demonstrates exceptional stability and performance. As for maintenance and reliability, the platform provides high availability and multi-tenant deployment, system resource and health monitoring dashboards, and automated maintenance tasks.
Besides tracking user activity, Ekran System provides enhanced incident alerting and response functionality. But that’s not all. Using Ekran System Client, you can set up access and identity management. Since Ekran System also provides server user activity monitoring, you always know what is happening in your network.
The unique licensing offered by Ekran System enables cost-effective deployments of any size, from small pilots to enterprise projects. Floating endpoint licensing enables license reassignment in a couple of clicks. For virtual environments, this process is automated.
FAQ
Insider threats pose a significant danger to sensitive government data, infrastructure, and national security. Insiders can engage in state espionage to provide intelligence for their native states. Malicious actors can also steal classified information and even disrupt critical systems. Effective insider risk management helps mitigate these risks for local and federal governments by identifying and responding to potential insider threats.
State espionage, also known as foreign espionage, involves other governments gathering intelligence about your nation’s activities, intentions, or capabilities. State espionage often focuses on classified information, including military secrets, foreign policy initiatives, and economic intelligence. Personal data of citizens, intellectual property, and research findings are also valuable targets for foreign spies.
The core components of a cybersecurity program for a government institution include robust risk assessment methodologies and data protection policies. Another key measure for a cybersecurity program is implementing government cybersecurity software for access management, threat detection and response, and insider risk management. Additionally, employee awareness programs play a vital role in fostering a cybersecurity culture and mitigating insider threats.
Popular cybersecurity solutions for government entities to fight insider threats include:
- Privileged access management (PAM) tools to manage access to critical resources.
- User activity monitoring (UAM) software to detect risky user behavior in real time.
Full-cycle insider risk management solutions like Ekran System are specifically designed to identify and investigate insider threats, combining UAM, PAM, and other cybersecurity capabilities.
Recommended resources
Ready to strengthen your defenses with Ekran System?
Consult our experts on the most efficient insider risk management approach to meet your organization’s cybersecurity needs.






