Privileged Access Management
Manage access. Audit activity. Respond to incidents. ALL-IN-ONE
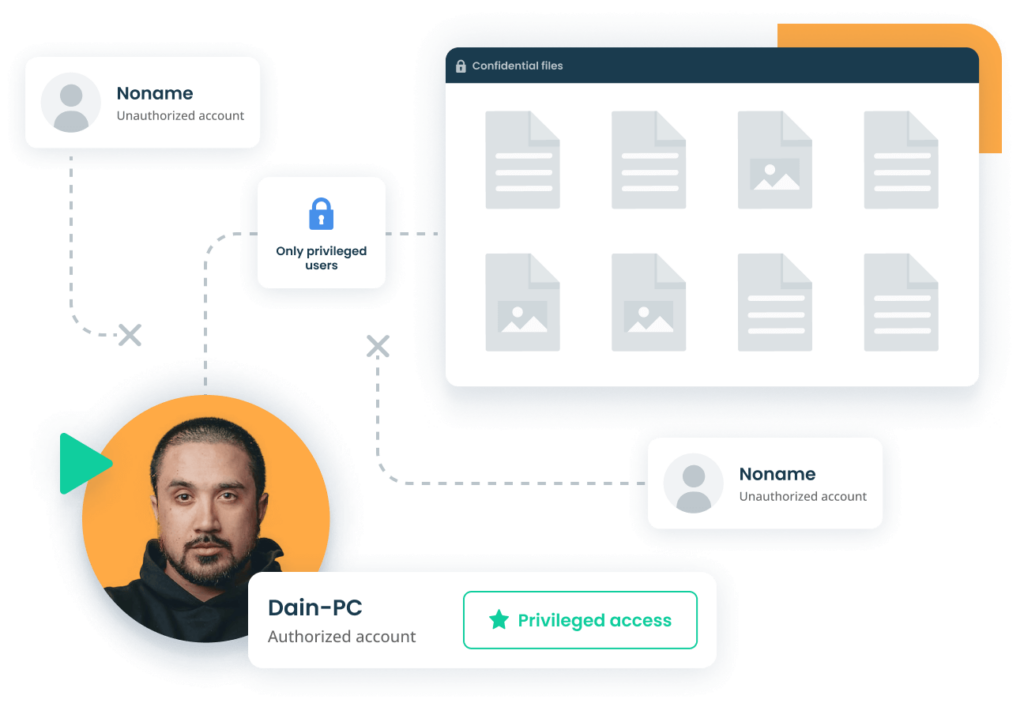
Manage privileged user access with Ekran System
Uncontrolled and excessive access privileges are dangerous, as they increase the risk of data breaches, accidental damage, compliance issues, and reputational harm.
90% of organizations experienced at least one identity-related breach from 2022 through 2023.
According to the 2023 Trends in Securing Digital Identities report by the IDSA
74% of all breaches include the human element, with people being involved either via error, privilege misuse, use of stolen credentials or social engineering.
According to the 2023 Data Breach Investigations Report by Verizon
With Ekran System’s privileged access management (PAM) capabilities, you get the necessary controls for dealing with the following challenges:
Monitor and audit privileged user activity
Secure critical endpoints and sensitive data
Granularly control access permissions
Ensure IT compliance and bypass cybersecurity audits
Ekran System privileged access management solutions
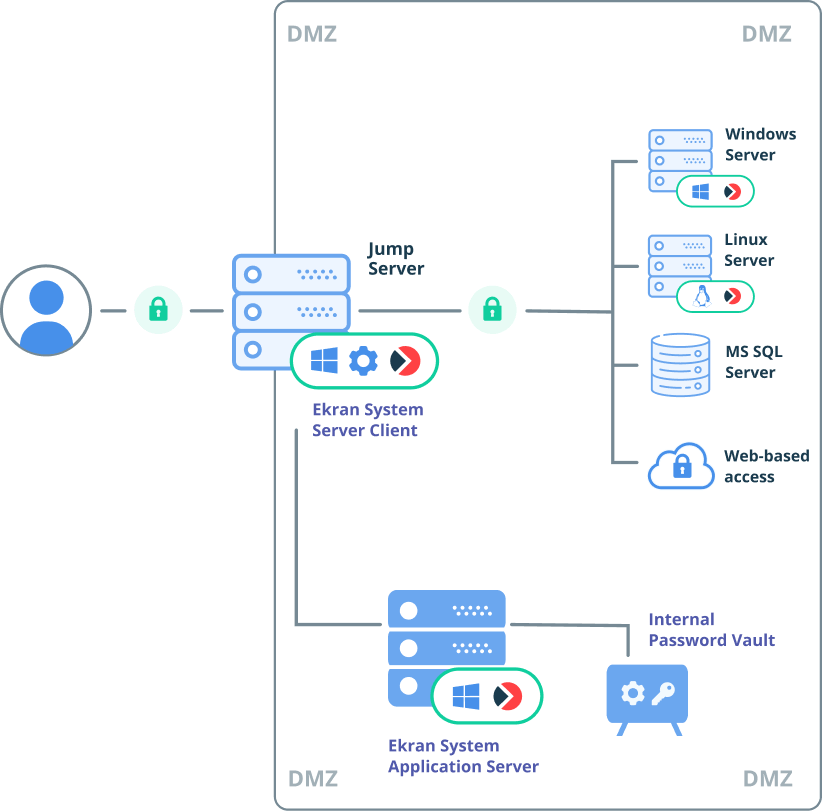
Ekran System’s PAM capabilities were built according to NIST recommendations. By managing RDP sessions initiated on your jump servers, you can use them to ensure secure remote access to critical endpoints.
With the PAM features in Ekran System, you can:
- Secure access to your Active Directory environment as well as to Linux/Unix and Windows endpoints
- Secure your web-based access
- Specify endpoints that can be accessed by particular privileged users
- Limit the time for which access is granted
- Deliver temporary credentials to specific users and groups
- Automatically generate, encrypt, and manage the credentials of privileged users
You can also use Ekran System’s PAM capabilities to ensure secure remote access to your critical endpoints for third-party vendors, contractors, and remote employees.
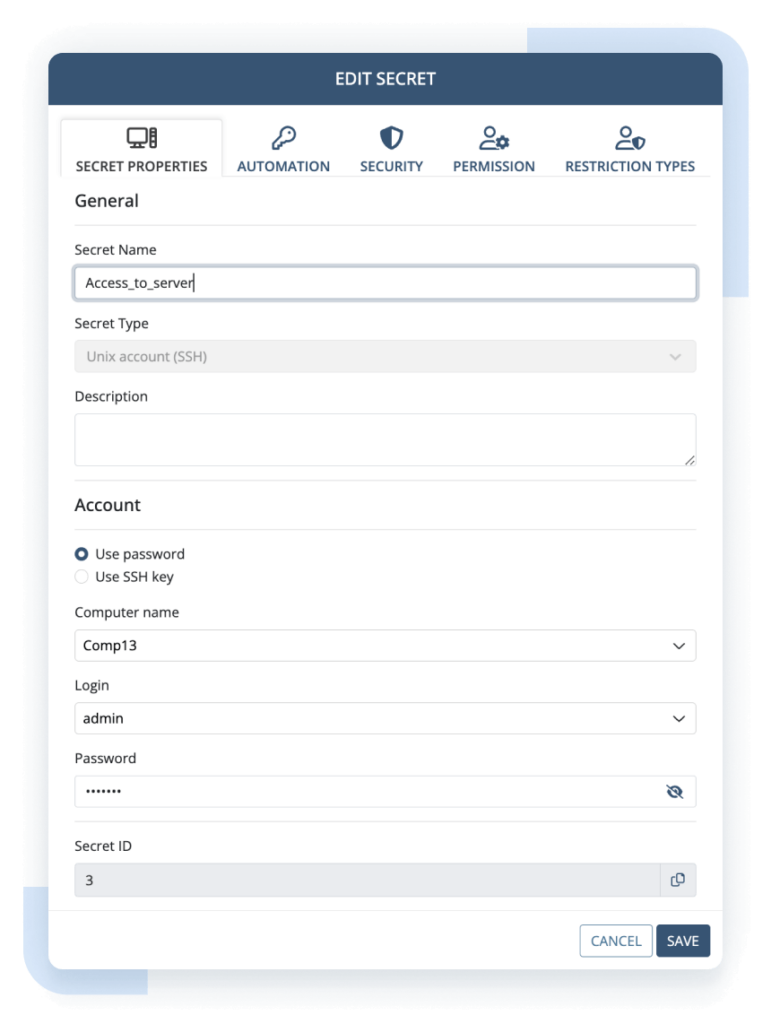
Forget about having to deploy extra-privileged password management software. Ekran System includes a sophisticated privileged password management solution with all the capabilities you need to properly handle and protect your secrets:
- Password Vault for securely storing and delivering secrets
- Automated and manual password rotation for Windows and AD accounts
- Role-based access control
- SSH key management
- Password management for shared accounts (Windows, Linux)
- Web account password management
Ekran System provides military-grade data encryption and uses only FIPS 140-2 compliant encryption algorithms. All data and connections, including privileged account credentials and client–server connections, are encrypted with AES-256 keys and an RSA-1024 or RSA-2048 algorithm.
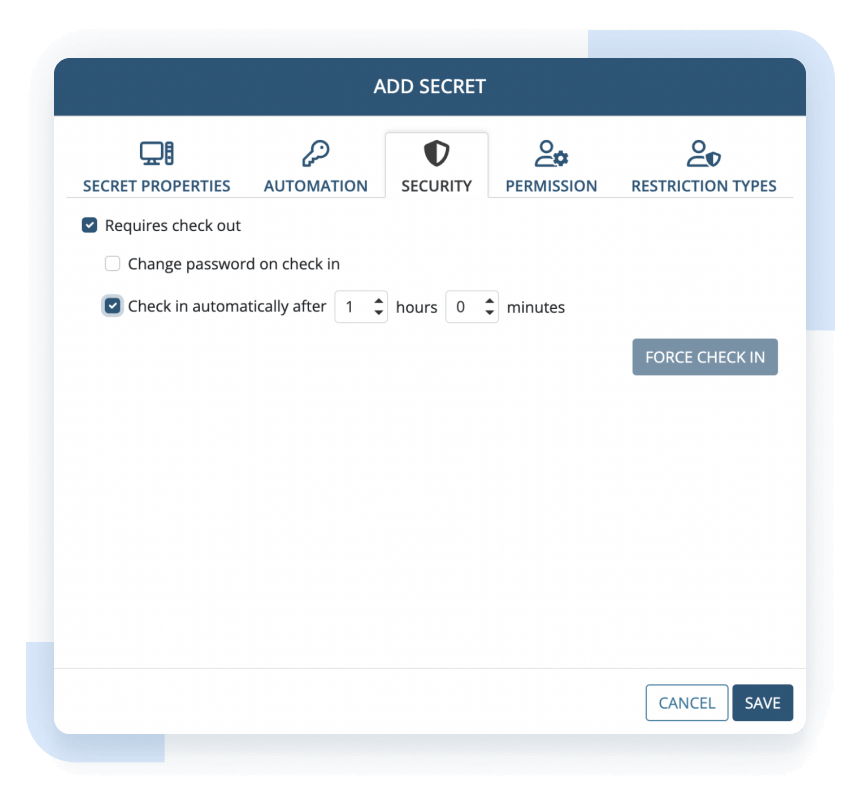
Get additional control over privileged accounts by preventing more than one user from accessing any secret at any one time, optionally limiting the time users can access secrets, and much more.
When a user logs into any particular secret, its password is checked out of the vault so that no other user can use it. When the user finishes using the secret, the password is checked back into the vault and is therefore freed up for other users.
With Ekran System’s password checkout capabilities, you can:
- Automatically check in a secret’s password after a specified period of time
- Automatically rotate a password after a user finishes using it
- Forcibly check in the password at any time to immediately disconnect the user from the secret
- Track the users currently using secrets with checked out passwords
Use the password checkout feature to track secrets, increase the accountability of shared account users, and enhance security in your organization.
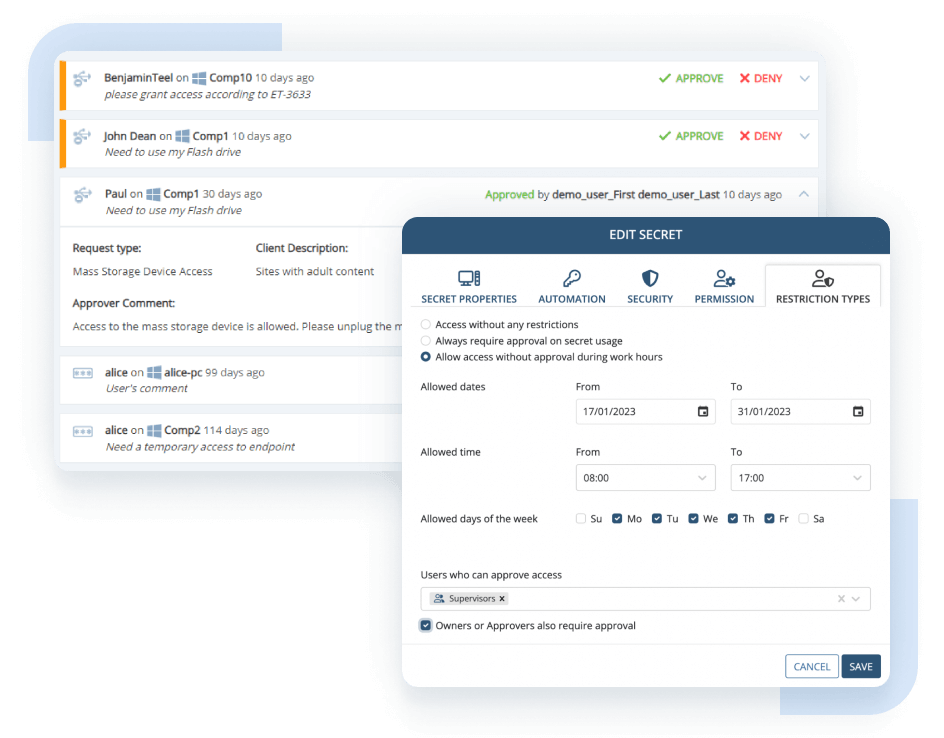
Minimize cybersecurity risks and control the number of simultaneously active accounts with Ekran System’s just-in-time PAM capabilities:
- Manual access approval for determining who can access what and when
- One-time passwords (OTP) for securing temporary access to specific endpoints, including emergency access
- Integration with leading ticketing systems including SysAid and ServiceNow for cross-checking and validating the reasons for privileged access requests
- Time-based user access restrictions for enhancing the protection of critical data and systems
Monitor, record, and manage user activity in all sessions started under temporary credentials.
Strengthen the protection of your critical assets with Ekran System’s two-factor authentication (2FA) tool. This tool is part of our rich set of identity and access management features.
Ekran System’s multi-factor authentication tool enhances the user verification process by combining user credentials and time-based one-time passwords. This privileged identity management solution is included with any Ekran System license and runs on Windows Server and Windows and macOS endpoints.

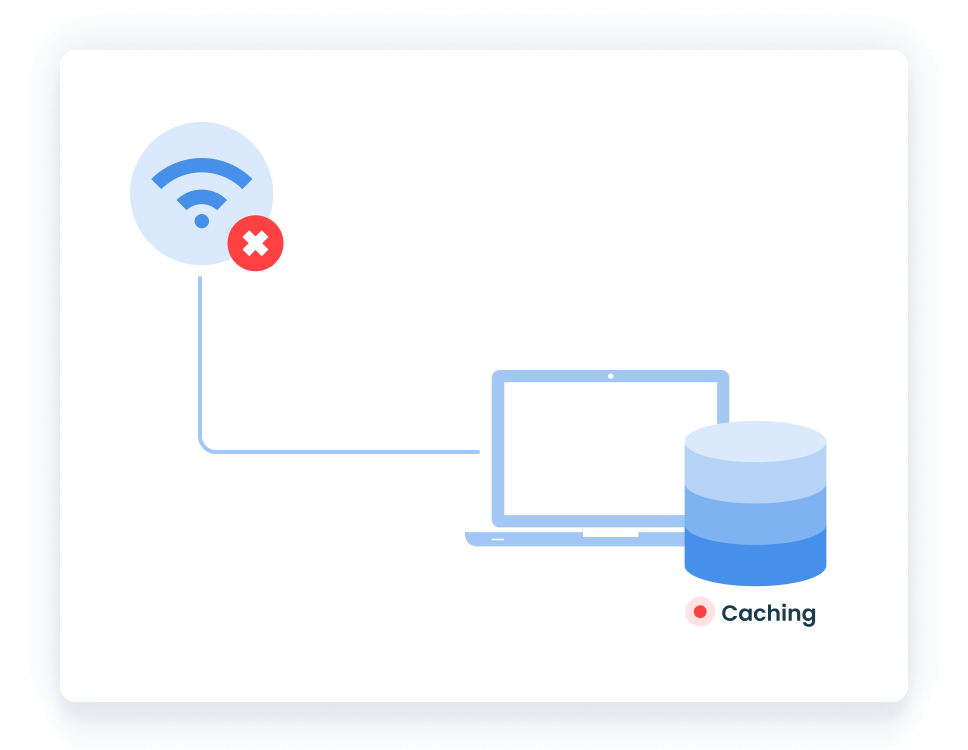
Monitoring is an essential part of privileged account management. With Ekran System, you can continuously monitor, record, and audit all privileged sessions on endpoints.
If a server connection is temporarily limited or lost, the lightweight Ekran System Client will continue recording the session in offline mode. Once the connection is restored, all information will be uploaded to the Ekran System Application Server.
In addition, Ekran System can automatically generate a large set of user activity reports, allowing you to get a close-up view of every user action and analyze overall user activity.
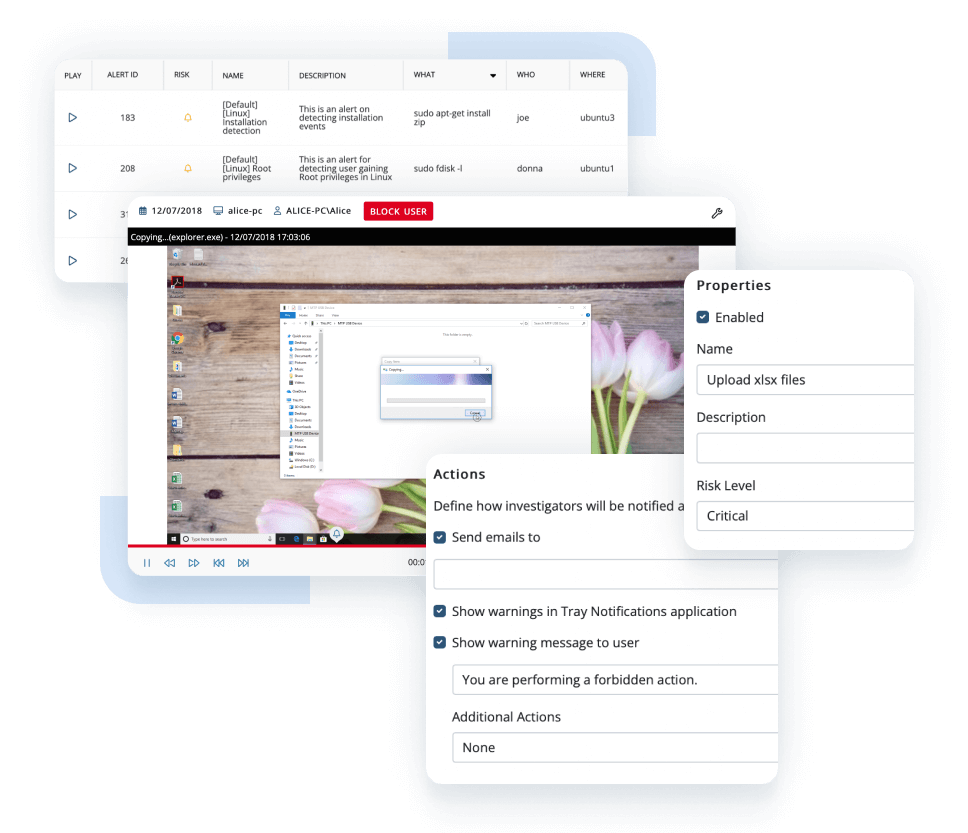
Enable proactive privileged activity monitoring with the help of Ekran System’s actionable alert system.
Use our extensive library of template rules or set custom targeted alerts for detecting abnormal user behavior. Block users, terminate applications, and send real-time notifications to pinpoint privileged access abuse in near real time.
For each alert, you can optionally assign an automated incident response action that will be executed along with notifying security staff: show a warning message to the user, kill an application, or block the user.
Manage access. Audit activity. Respond to incidents.
Watch a 6-minute overview of the Ekran System Insider Risk Management Solution showcasing access management, user activity monitoring, user behavior analytics, employee monitoring, and insider threat detection.
Ekran System® manages privileged access to ensure compliance
Ensuring a proper level of privileged account management and access management is one of the main requirements of major compliance regulations and standards. With Ekran System’s privileged access management security solution, you can meet compliance requirements with ease:
Get the most value for your business with other Ekran System’s capabilities
Password manager overview by Ekran System’s technology partner
Watch the video review from our partner UBX Cloud on how Ekran System password manager works together with the connection manager to streamline privileged account management.
Supported platforms
Manage privileged access with Ekran System®
Ekran System integrations
Ekran System privileged access management easily integrates with your existing infrastructure, including leading SIEM and ticketing systems.
Case studies
What our clients say about Ekran System’s insider threat prevention tools

FAQ
Privileged access management, or PAM, is a set of cybersecurity policies, principles, and tools that allow you to manage the access rights of privileged users. By applying a privileged access management platform, you can configure which users can access which resources, protect sensitive data from unauthorized access, and detect and prevent security incidents.
Managing privileged access can help you prevent cybersecurity risks like data theft, leaks and abuse, corporate espionage, and credential theft. Deploying a PAM toolset is also important for organizations that need to comply with cybersecurity laws, standards, and regulations like HIPAA, PCI DSS, and NIST SP 800-53. Protecting user access is an essential part of compliance.
While both PAM and IAM help to manage user access, they have a lot of differences:
- PAM controls only privileged accounts, while IAM can be applied to all accounts.
- PAM guarantees users will access only the resources to which they have access rights. IAM ensures that only the right people log in to an organization’s systems.
- IAM verifies users’ identities before providing access to an organization’s resources. PAM checks users’ credentials before providing access.
Achieving regulatory compliance often requires organizations to deploy both IAM and PAM tools to ensure the best possible protection. Ekran System provides you with PAM and IAM tools in one solution.
The main goal of using a PAM system is to protect an organization’s sensitive data from unauthorized access. PAM helps you make sure privileged users access only the resources they need for work purposes. Also, it alerts security officers if users do something suspicious with sensitive data.
PAM is useful for protecting both from insider threats like data theft and corporate espionage and from outside attacks like hacking, credential theft, and social engineering.
By deploying a PAM solution, an organization:
- Protects sensitive data it stores
- Mitigates possible insider and outsider threats
- Prevents privileged users from violating security policies without affecting their productivity
- Enhances compliance with cybersecurity requirements
No. Privileged access management is integrated into our insider risk management solution.
Ekran System also includes tools for:
- User activity monitoring
- Identity management
- Alerts on suspicious user actions
- Enhanced auditing and reporting
All of these functionalities help your security team protect sensitive data by efficiently monitoring and controlling user activity.
With Ekran System’s PAM solution, you can manage remote access privileges as easily as you can manage access privileges of in-house employees. You can configure access rights for remote users, manage their credentials and secrets, audit their activity, monitor access requests and interactions with sensitive data, etc.
Ekran System is highly flexible in terms of configuring access rights. For example, it allows you to:
- Create unique access configuration for a user
- Configure user roles and assign those roles to groups of users
- Allow access to sensitive resources for a certain period of time
- And do even more
Our PAM software is easy to customize. Also, our support team is always ready to help with customizations and any other questions.
You can implement the principle of least privilege using the following capabilities of Ekran System:
- Granularly configure access rights for privileged users to allow them to interact only with the resources they need
- Reconfigure users’ access rights at any moment in a couple of clicks
- Provide access to the most sensitive resources for a set period of time
To implement JIT, you can also use these privileged access management features:
- One-time passwords that provide users with access only when they need it and for a limited period of time
- Manual access approval, which is useful for controlling access to the most secured resources
Ekran System supports a high availability mode based on a Microsoft failover cluster. It’s designed in such a way that if the Ekran System server stops working, another server instance can replace it without data loss or reinstallation. To enhance availability, you can create a load balancer cluster for the AppServer or deploy an MS SQL cluster.
Ekran System encrypts privileged user credentials and other secrets with the Advanced Encryption Standard (AES) 256. These secrets are stored in an SQL database, which can be located on a separate machine.
We also use encryption to protect initial vectors for time-based one-time passwords, monitoring records, exported forensic data, and passwords of internal Ekran System users. You can learn more about Ekran System encryption mechanisms in our documentation.
We’ve prepared step-by-step guides for deploying Ekran System in the form of agents or jump server instances. The documentation also contains instructions on how to configure Ekran System components.
If you have any additional questions about our privileged access management tools, feel free to contact our support team.
Blog spotlight
Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.