Linux User Activity Monitoring
Manage access. Audit activity. Respond to incidents. ALL-IN-ONE
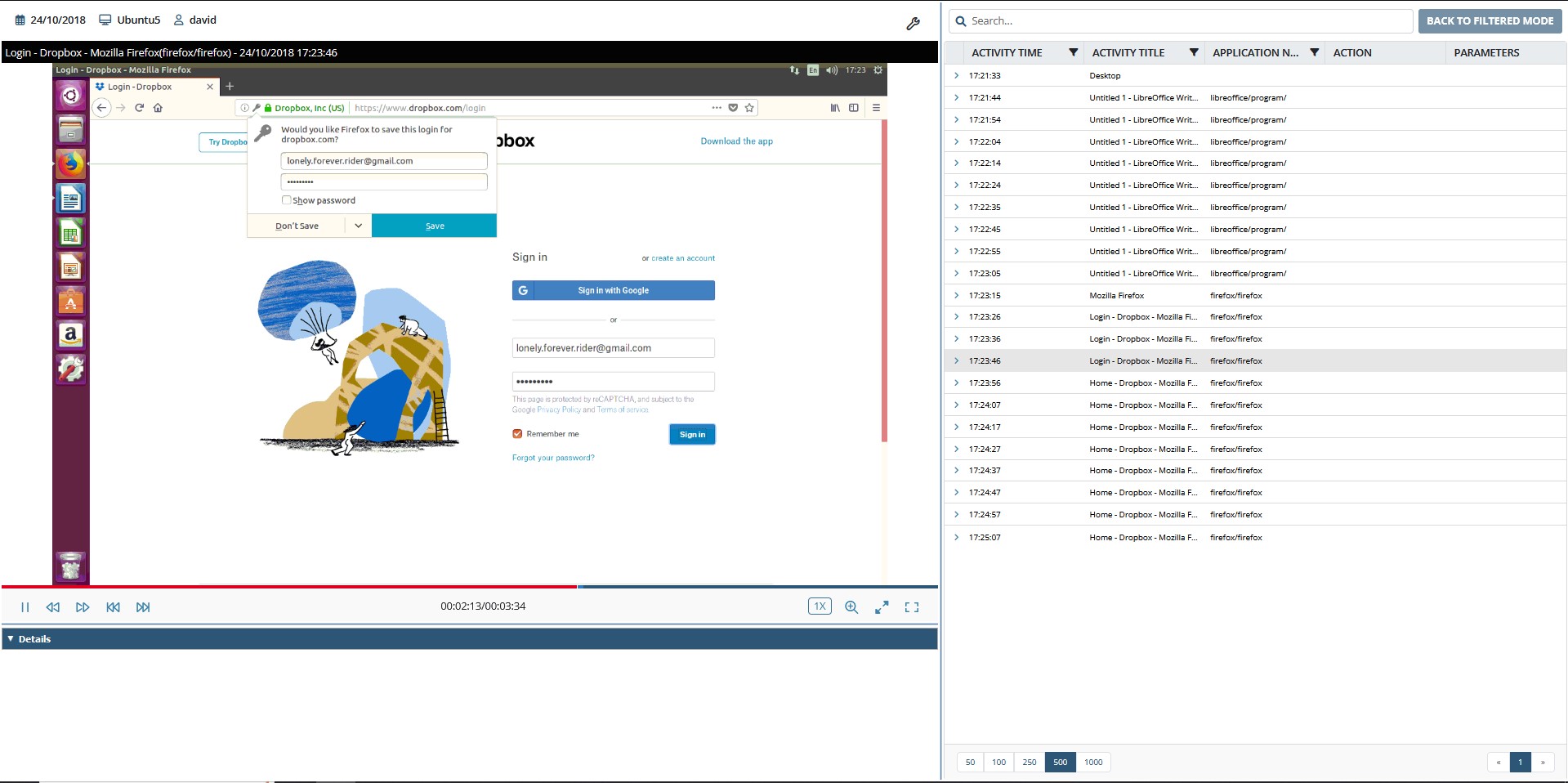
Ekran System® is a powerful tool for Linux user monitoring, providing both SSH session recording and X Window session recording as well as local console session logging.
UNIX SSH session monitoring is available on request for your custom configuration. This way you can easily audit UNIX sessions to identify insider threats in real time.
If you’re using Oracle Solaris or IBM AIX to improve data center security and performance, we have good news for you. We meet the needs of our enterprise clients by supporting monitoring and auditing on Solaris and AIX out of the box.
Ekran System is also the user activity monitoring tool for Linux that works on cloud desktops provided by Amazon Linux WorkSpaces. If you want to expand your hardware capacities with cloud desktops built on Amazon Linux 2 LTS, there’s no need to worry that your employees’ activity will be out of your control and can’t be audited.

Screenshots of Linux session recording and monitoring tool
Ekran records Linux session activity from the moment the terminal opens till it closes, whether a session is initialized remotely via SSH/telnet or locally. It even supports pseudographics.
Tracking SSH sessions provides the ability to monitor not only commands executed in the terminal but also applications forwarded by X Window. Ekran can also track live Linux sessions started locally via the graphical interface.
Not just text session logs – get video analysis
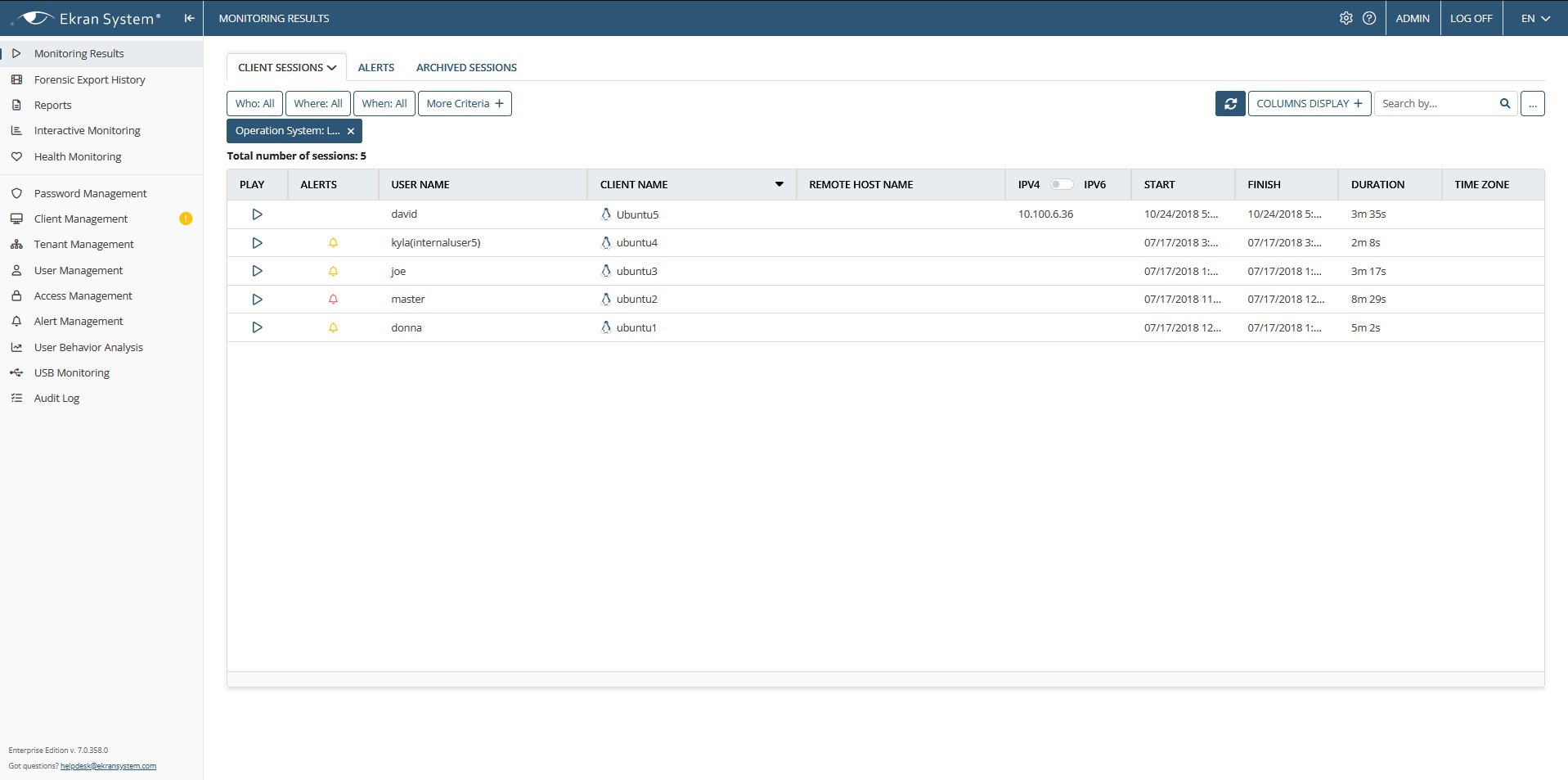
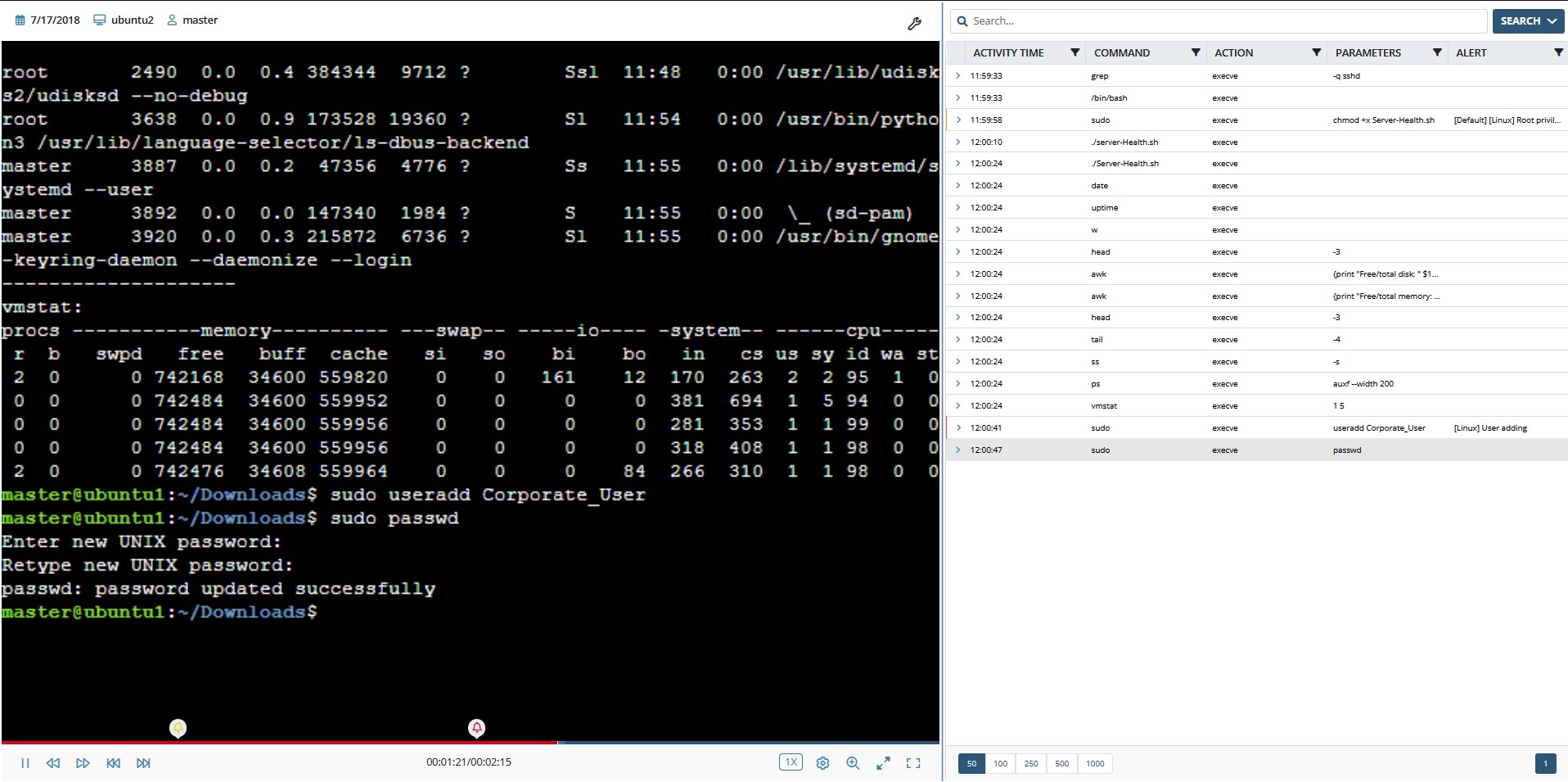
Unlike other user activity monitoring software for Linux, Ekran System provides session replays in video format with indexed and searchable metadata, including host name, user name, and commands and parameters entered.
With Ekran, an investigator can check SSH sessions on Linux remotely in real time with a synchronized text log of the important data. This log also contains records of Linux user activity with commands that aren’t displayed on the screen, in particular those in executed Linux scripts.
Video-like logs of user activity are an innovative way to monitor Linux terminal sessions. An easy-to-analyze visual format with all DVR-like playback features is complemented with search by executed command, entered parameter, user name, host name, and date/time.
Learn how to track activity in SSH sessions and record it in Linux in the demo video below.
Actionable Linux session monitoring
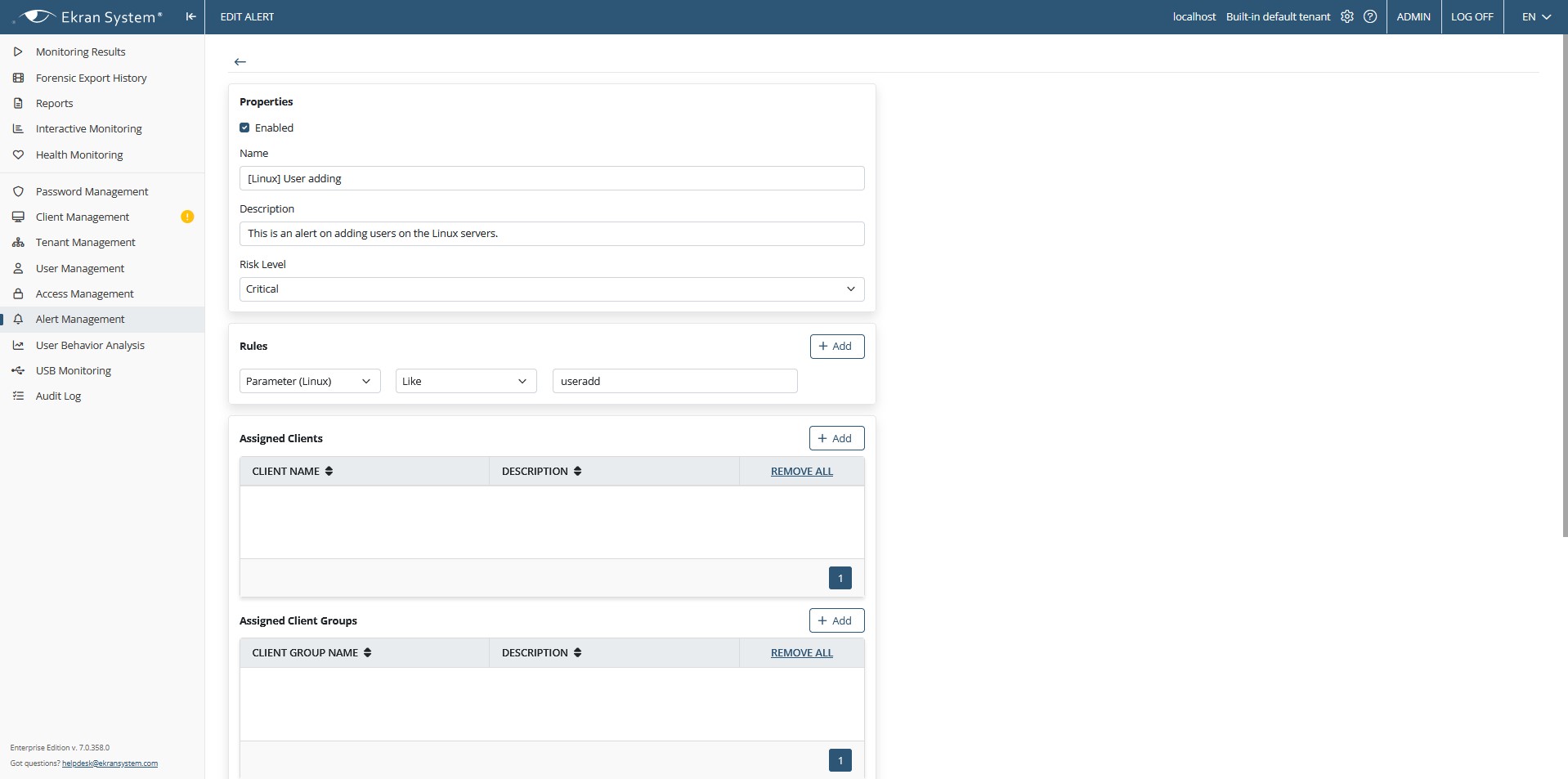
To enable quick incident response on your Linux servers, Ekran System provides alerts.
Investigators can set up alerts for specific commands/parameters entered or included in running scripts and get real-time notifications when these alerts are triggered – along with a quick link to the corresponding episode in the video log. They can then view suspicious sessions in real time and respond appropriately if malicious actions are detected.
As Linux session auditing software, Ekran provides a specific type of report containing all commands executed on Linux servers with timestamps and user names to track user activity within Linux sessions. General reports on all user sessions initiated on target endpoints show access details, all user activities, activity outside of working hours, and other details.
Cost-effective Linux monitoring solution
As a universal tool for Linux, UNIX, and Windows-based endpoints, Ekran System can help you control and audit Linux sessions at each node in your infrastructure, in both virtual and hybrid environments.
Ekran System provides the most transparent and flexible licensing scheme among competitors. The deployment cost is based on the number of target endpoints only, supporting any number of users and simultaneous sessions without any hidden fees. Get more details about Ekran System licensing.
Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.