User Activity Monitoring (UAM) Software
Monitor insider activity. Detect anomalies. Respond to incidents. ALL-IN-ONE
Ekran System® is universal user activity monitoring software that tracks any user action on:
Physical and virtual desktops
Remote laptops
Jump servers
Corporate servers
Why monitor user activity?
Secure sensitive information
Detect insider threats
Oversee the implementation of cybersecurity policies
Comply with cybersecurity standards, laws, and regulations
Increase employee productivity
Investigate security incidents
User activity monitoring software features
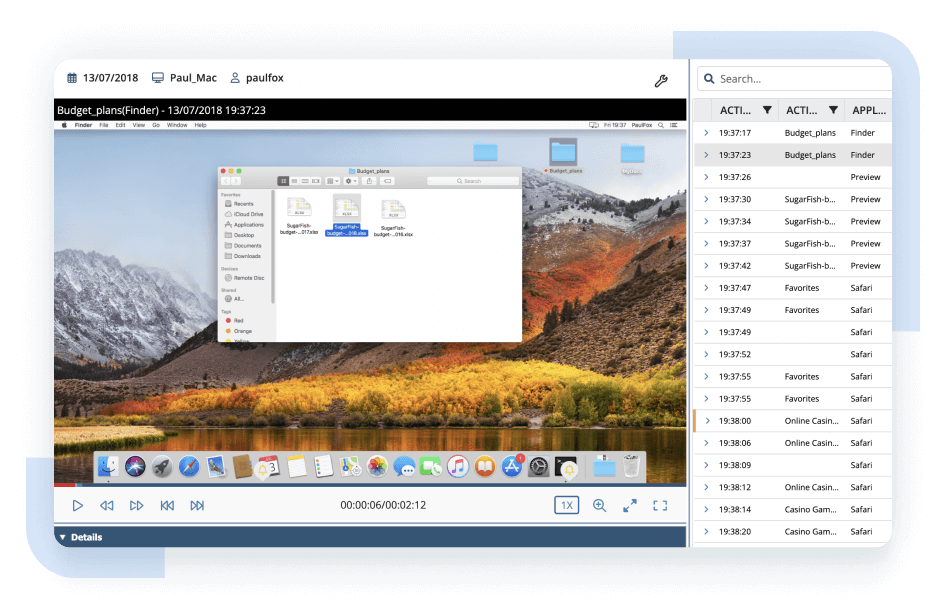
Ekran System® records on-screen user activity for all sessions in video format, indexed by accompanying text metadata.
Also, the UAM software captures input and output audio streams on the endpoints.
It provides Citrix and Windows user activity monitoring on servers and workstations with local, RDP, and terminal session recording. It also provides Telnet SSH session recording for Linux/UNIX servers.
Each session record includes important details about remote connections and connecting users. You can also export it for further investigation and analysis.
Ekran System substitutes user logins and device names with aliases to make it impossible to link this data to a specific user. For instance, if someone were looking for the user John-Smith that works on John-Smith-PC in the activity monitoring results and reports, they might see user USR-880B1A and CLN-E0CB5E.
Unique aliases are assigned randomly, making it impossible to discover a pattern and link an alias back to a user.
Ekran System hides user data in:
- User activity monitoring results
- Reports on user activity
- Screenshots of user sessions
- The Ekran System Management Tool
The de-anonymization process allows you to quickly identify a user in case of a security incident. At the same time, users’ private data is protected from anyone who has access to the Ekran System Management Tool.
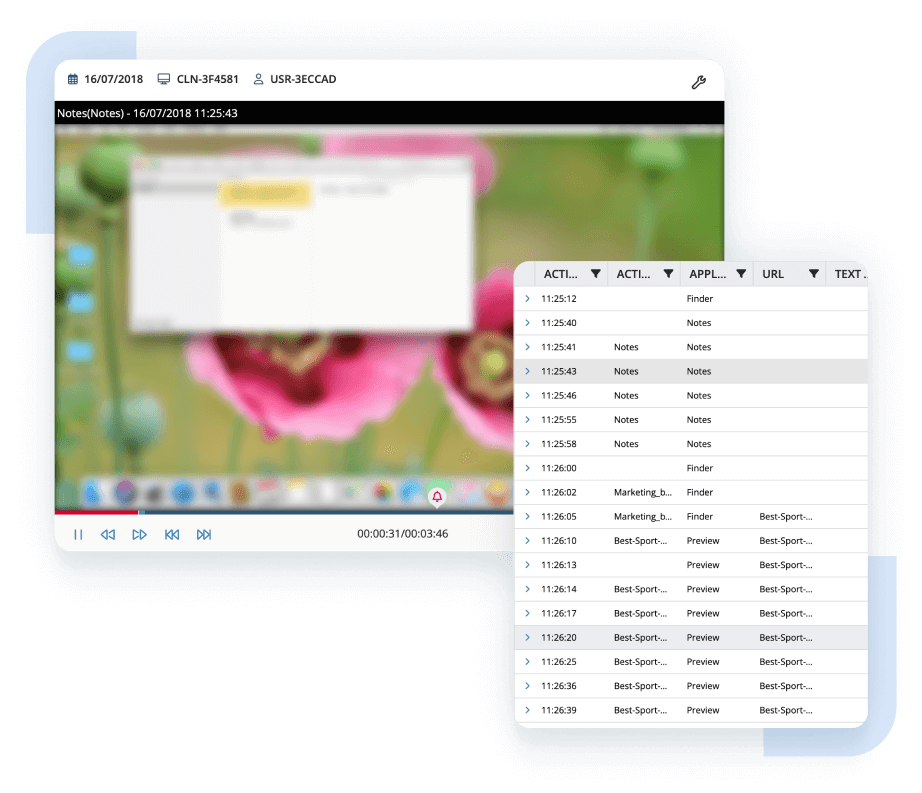
Ekran System’s core monitoring format is screen capture indexed with multilayer metadata including names of active applications, titles of active windows, websites (URLs) visited, keystrokes types, commands and scripts executed, and devices connected.
Screen capture is an efficient tool for logging and auditing user activity, as it’s all-inclusive and integrated, allowing for quick comprehension and reconstruction and providing the tools to respond to a security incident.
At the same time, multilayer text indexing makes the screen capture records searchable and allows for in-depth investigation.
Ekran System records are optimized to achieve exemplary performance.
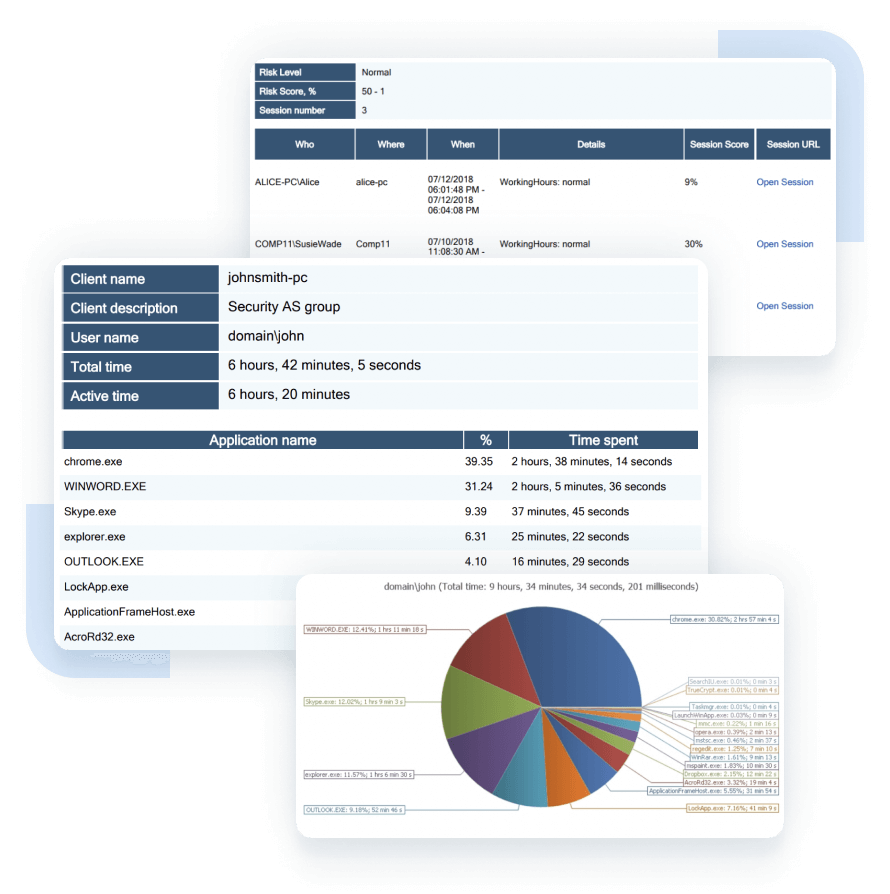
Ekran System not only records user sessions but also monitors user activities in real time.
It includes an AI-based user behavior analytics subsystem that continuously checks user activity against a normal baseline to detect deviations and possible account compromise in a timely manner. The Ekran System UEBA module can help security officers better detect insider threats when employees act maliciously during short periods of time or when they inadvertently exfiltrate corporate data.
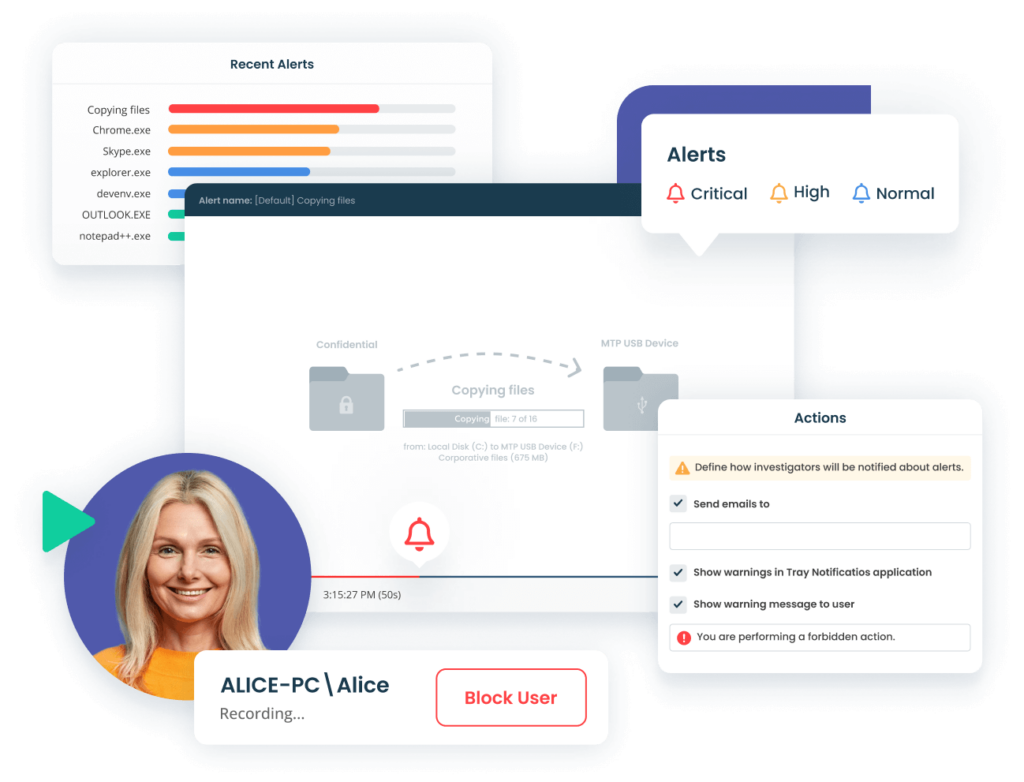
It also includes another alerting subsystem based on customizable rules that’s used to secure the most critical assets and scenarios. You can use alerts from the template library – which cover the most typical insider threat signals – or build your own rules using a variety of parameters.
After an alert is triggered, everything is set up for quick incident response. Notifications include suspicious session details and links to the corresponding video episodes for quick inspection. If the session is still running, a security officer can connect to it in real time. For the most critical alerts, you can assign automated blocking and warning actions.
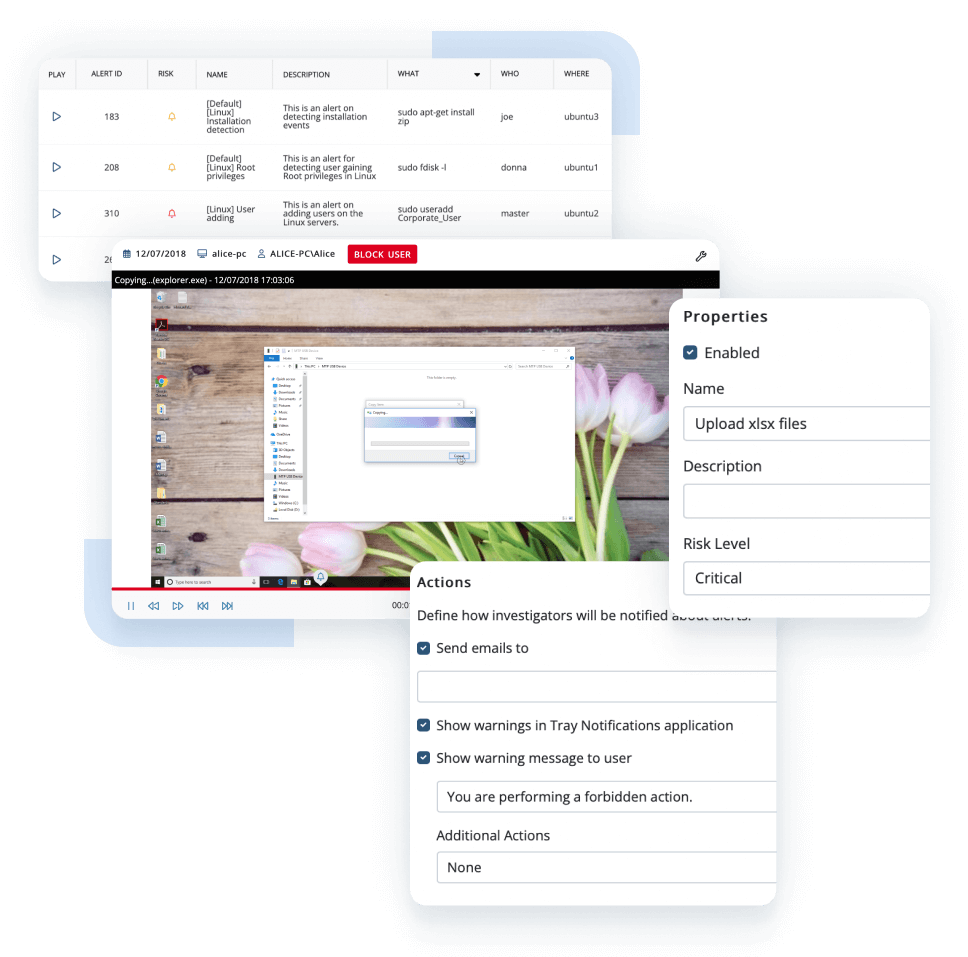
An important aspect of monitoring user activities is controlling the use of connected devices.
Ekran System user activity management software includes powerful USB device monitoring and management functionality for dealing with storage devices as well as any kind of USB equipment, including modems and keyboards.
The user activity monitoring system can track device connections and can be configured to notify your security team about them. Besides monitoring, Ekran System can be set up to allow or block devices according to rules, blacklists, and whitelists.
To add more flexibility, Ekran allows you to set up manual USB device approval for critical scenarios.
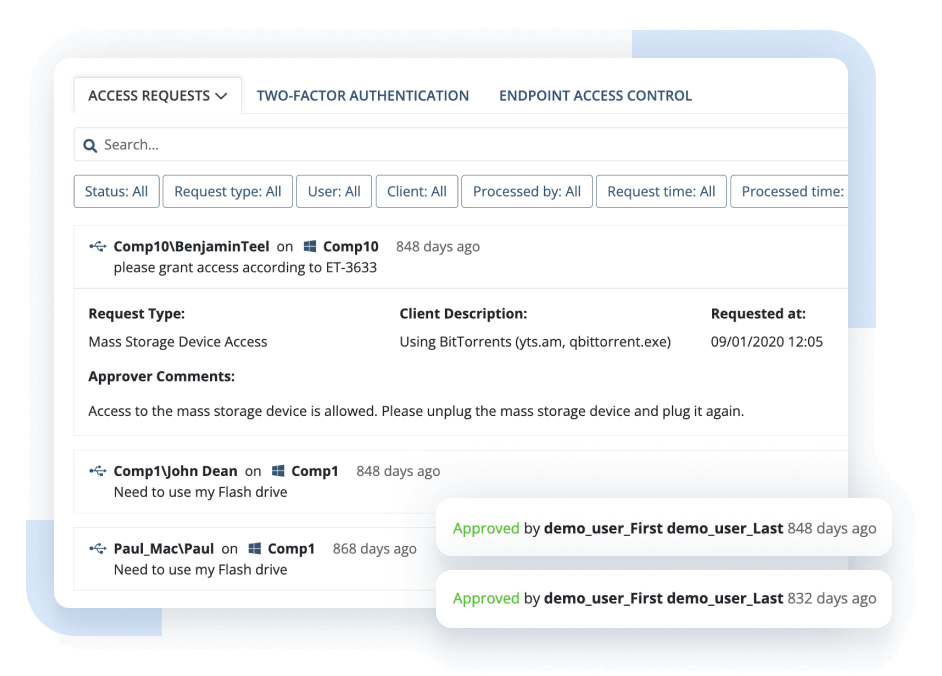
Software to track user activity will log thousands of user actions over a typical day. Solutions for monitoring computer activity of a number of privileged users should provide tools to make logging more focused.
To record user activity optimally, Ekran System gives you several filtering options. You can record a selected number of key applications or set up a list of private/non-critical applications or URLs you don’t wish to monitor.
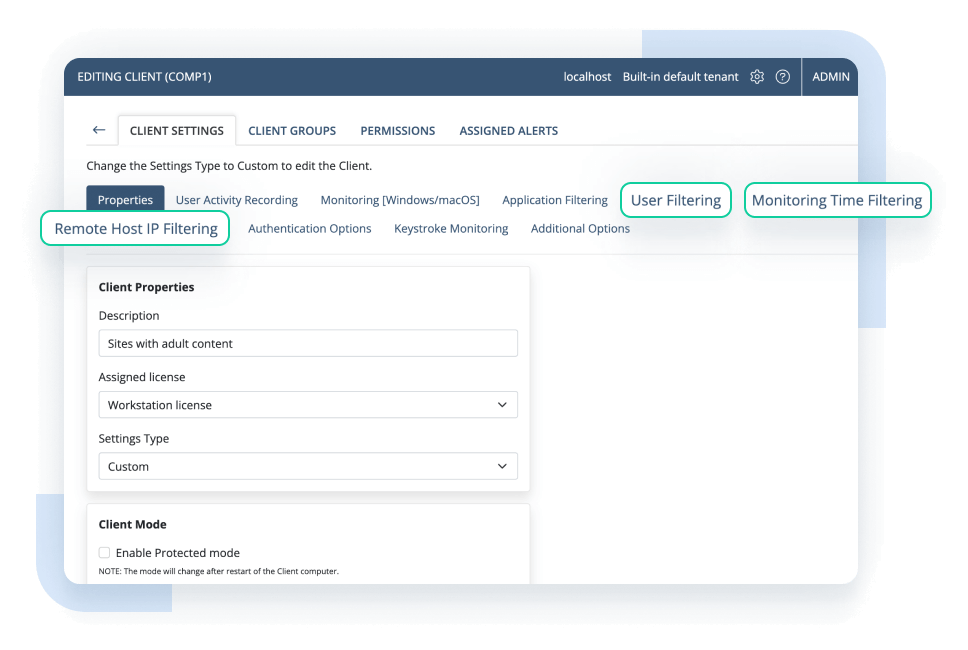
A big requirement for any user activity tracker is ensuring uninterrupted user activity tracking under any conditions.
Ekran System UAM software includes an offline monitoring option. If the network connection on the client goes down, the Ekran System Client will continue to work, collecting monitoring data in secure storage on the client to then send to the central storage according to a performance-aware protocol once the connection is restored.
Ekran System Client and its data are protected from intrusion by monitoring users with any level of privilege. By enabling Protection from Client settings modification, you can prevent client uninstallation, process interruption, solution component editing, and other actions to block monitoring.
Record user activity. Analyze and audit
Ekran System is a powerful yet easy-to-use UAM software helping SMBs and big enterprises to detect insider threats and comply with regulations.
Being user activity monitoring software, Ekran System works on Windows and Linux servers recording all connected sessions, and also on Windows desktops monitoring local and remote users.
Why companies choose monitoring user activity with Ekran System®
Ekran System continuously monitors various endpoints, including both end-user machines and servers, within any network architecture. Being one of the best user activity monitoring tools for Windows, Ekran also works for macOS and is a powerful Linux/UNIX session audit tool. It even supports X Window and all popular virtualization solutions. Ekran allows agent-based and jump server-based deployments as well as any combination thereof.
Designed for tracking user activity on tens of thousands of endpoints, Ekran System demonstrates exceptional stability and performance. As for maintenance and reliability, the platform provides high availability and multi-tenant deployment, system resource and health monitoring dashboards, and automated maintenance tasks.
Besides tracking user activity, Ekran System provides enhanced incident alerting and response functionality. But that’s not all. Using Ekran System Client, you can set up access and identity management. Since Ekran System also provides server user activity monitoring, you always know what is happening in your network.
The unique licensing offered by Ekran System enables cost-effective deployments of any size, from small pilots to enterprise projects. Floating endpoint licensing enables license reassignment in a couple of clicks. For virtual environments, this process is automated.
Get the most value for your business with other Ekran System’s capabilities
Supported platforms
Ekran System integrations
Ekran System user activity monitoring software integrates with your existing infrastructure, including leading SIEM and ticketing systems.
Case studies
What our clients say about Ekran System’s insider threat prevention tools

FAQ
User activity monitoring solutions allow you to track user activity within your corporate network, across devices, and throughout your entire IT infrastructure. With user activity tracking tools, you can identify which applications, sites, and data users access and how they interact with them.
With a user tracking system, you can strengthen your current cybersecurity, protect confidential data from malicious users, and enhance insider risk management.
Yes. Digital user monitoring is legal, but it’s regulated by legislation.
To know how to monitor user activity legally, you should check with applicable laws within your jurisdiction. Typically, legislation requires businesses to inform users of monitoring and receive their consent. If your organization operates in the US, you should pay attention to both federal and state laws, as state laws can have their own requirements. For example, businesses that operate in Connecticut and Delaware don’t have to notify employees about email or internet monitoring. Meanwhile, employers in Colorado and Tennessee must create written email monitoring policies.
Ekran System is a powerful insider threat management platform that ensures comprehensive user activity monitoring.
In particular, Ekran System monitors user activities in real time and makes video and audio recordings of user sessions so you can watch them later if needed. All records are searchable. Thus, you can find out whether a user has accessed certain data, launched specific applications, or visited particular websites during working hours.
Also, Ekran System continues monitoring user activity in the network even if the internet connection goes down.
No. Ekran System does not influence the user experience. It monitors user activity smoothly without disturbing users.
However, Ekran may interrupt a user’s work if the user acts suspiciously. According to customizable rules, users can receive notifications explaining that a particular action violates cybersecurity policies. Also, your security admins can automatically or manually block suspicious sessions, users, and actions as needed.
When monitoring user activity on an organization’s network, Ekran System gathers the necessary data and stores it securely using military-grade encryption. Ekran System doesn’t store passwords entered by monitored users.
Ekran System offers more than just monitoring. Using this platform, you can:
- Know who accesses your sensitive data and how they handle it by arranging robust real-time user monitoring
- Prevent data leaks and breaches caused by insiders by detecting suspicious activity and instantly responding to it
- Enhance your cybersecurity by automatically sending notifications when users violate cybersecurity policies
- Evaluate employee efficiency by analyzing productivity reports
- Ensure compliance with various standards, laws, and regulations including GDPR, NIST, FISMA, HIPAA, and SWIFT
As a robust insider threat management platform, Ekran System can easily be adjusted to the specific needs of your organization.
For example, you can receive automatic custom reports on a convenient schedule. Also, in case an incident occurs, you can quickly export a full monitored session or a fragment of a session into an independent file.
Ekran System is UAM software that supports various deployment options. You can install Ekran System Client on each endpoint or install just one Ekran System Terminal Server Client on a jump server to ensure user activity monitoring of all sessions that come through your server.
Installation is easy and takes less than an hour. If you have any questions or doubts during the process, our 24/7 customer support team will be there for you.
When used ethically and responsibly, user activity monitoring tools can offer the following advantages for your business:
- Enhanced security — UAM can help your organization detect insider threats, data breaches, and unauthorized access attempts.
- Improved compliance — Monitoring user activity can help your business comply with the GDPR, NIST, HIPAA, and other cybersecurity requirements.
- Increased productivity — You can assess the results of user activity monitoring to optimize workflows and detect what distracts your employees.
The benefits of user activity monitoring for employees are less clear-cut compared to those for businesses. These benefits include:
- Increased individual productivity — Employees can identify areas for improvement and optimize their own workflow based on employers’ feedback on users’ personal work patterns.
- Improved cybersecurity habits — With UAM, you can detect risky user behavior and tailor security awareness training, potentially contributing to employees’ and organizational security.
- Targeted approach to employee development — You can use the monitored data to identify skill gaps or areas where employees struggle the most and create targeted training and development programs.
To ensure that user activity monitoring benefits your employees and doesn’t evoke privacy concerns, it’s vital to maintain transparency and clear communication about the use of UAM in your organization.
The major disadvantages of user activity monitoring come down to a lack of transparency and privacy when using UAM unethically. If employees are unaware of the type of data being collected, how it’s being used, and for what purposes, it can foster mistrust and resentment, ultimately harming employees’ morale and productivity.
Therefore, clear communication and the establishment of policies to ensure user privacy are critical for user activity monitoring to be beneficial. Additionally, some UAM solutions allow you to anonymize your employees’ personal data to comply with data privacy regulations.
Blog spotlight
Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.