Full Cycle Insider Risk Management
Monitor insider activity | Control access | Respond to incidents



Full Cycle Insider Risk Management
Monitor insider activity
Control access
Respond to incidents



Manage insider risks
$16.2 M
Average annual cost of insider threats
according to 2023 Cost of Insider Threats: Global Organizations report by the Ponemon Institute
19%
Share of insider-driven data breaches
according to the 2023 Data Breach Investigations Report from Verizon
Meet compliance requirements
74%
Share of data breaches that include the human factor
according to the 2023 Data Breach Investigations Report from Verizon
34%
Share of breaches involving internal actors in finance organizations
according to the 2023 Data Breach Investigations Report from Verizon
All-in-one insider risk management platform
Proactive
Deter
With the Ekran System extensive capabilities for identity management and access control, you can effectively deter any insider threat risks.
active
Detect
Any malicious activity will be immediately detected with the Ekran System functionality for user activity monitoring and alerts and notifications management.
REactive
Disrupt
Leave no changes to insiders by disrupting any efforts of enterprise data exfiltration with the Ekran System powerful tools for incident response and investigation.
How Ekran System mitigates insider risks
Insider Threat Management Solutions
Ekran System covers each node of your infrastructure and provides insights into user activity while securing critical data and commercial secrets.

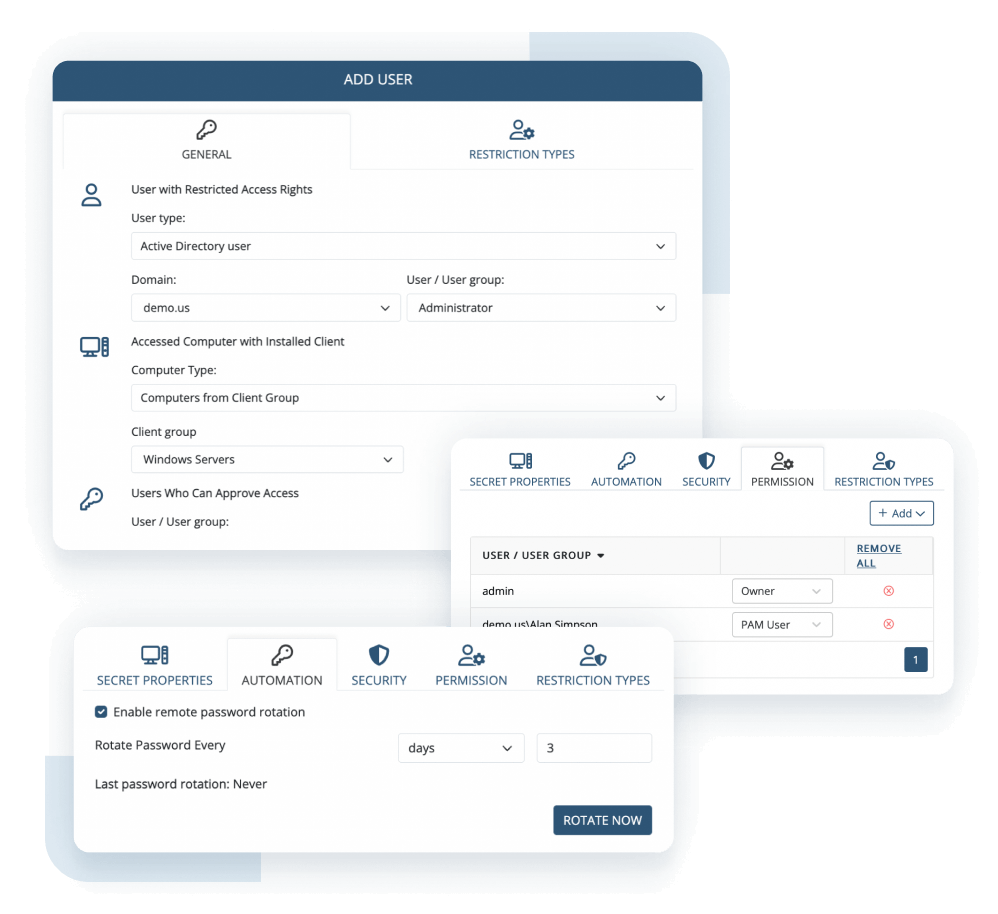
Leverage the lightweight Ekran System Client to secure access for privileged users and ensure they access only the resources they need for work purposes.

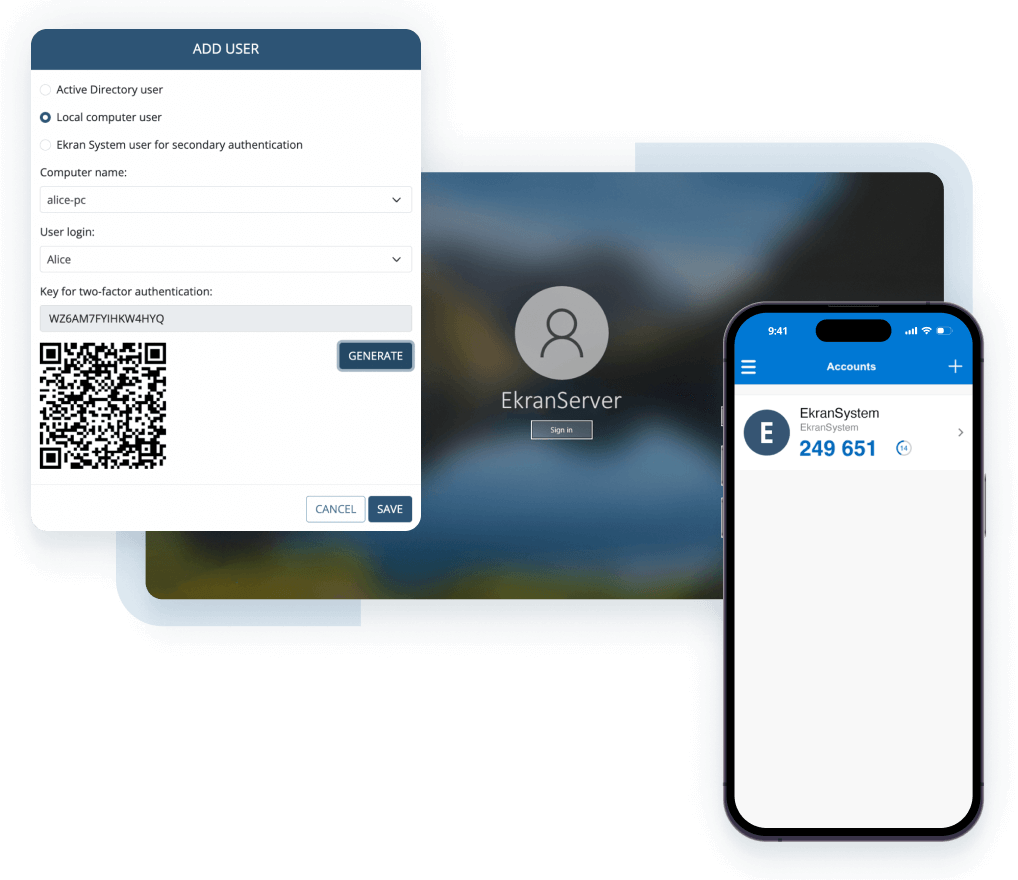
Ekran System addresses an organization’s vital need for reliable validation of users’ identities and the unambiguous attribution of each action to a specific person.

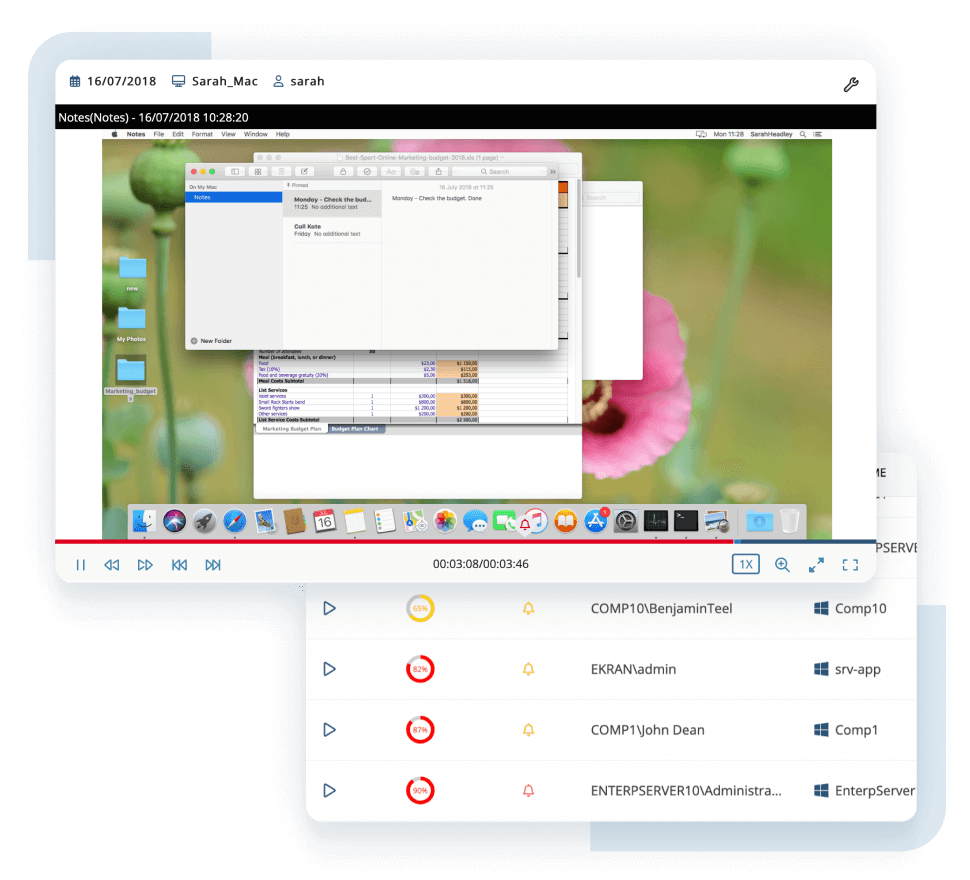
Ekran System immediately informs security officers about security incidents with activity alerts and lets them take quick incident response actions.
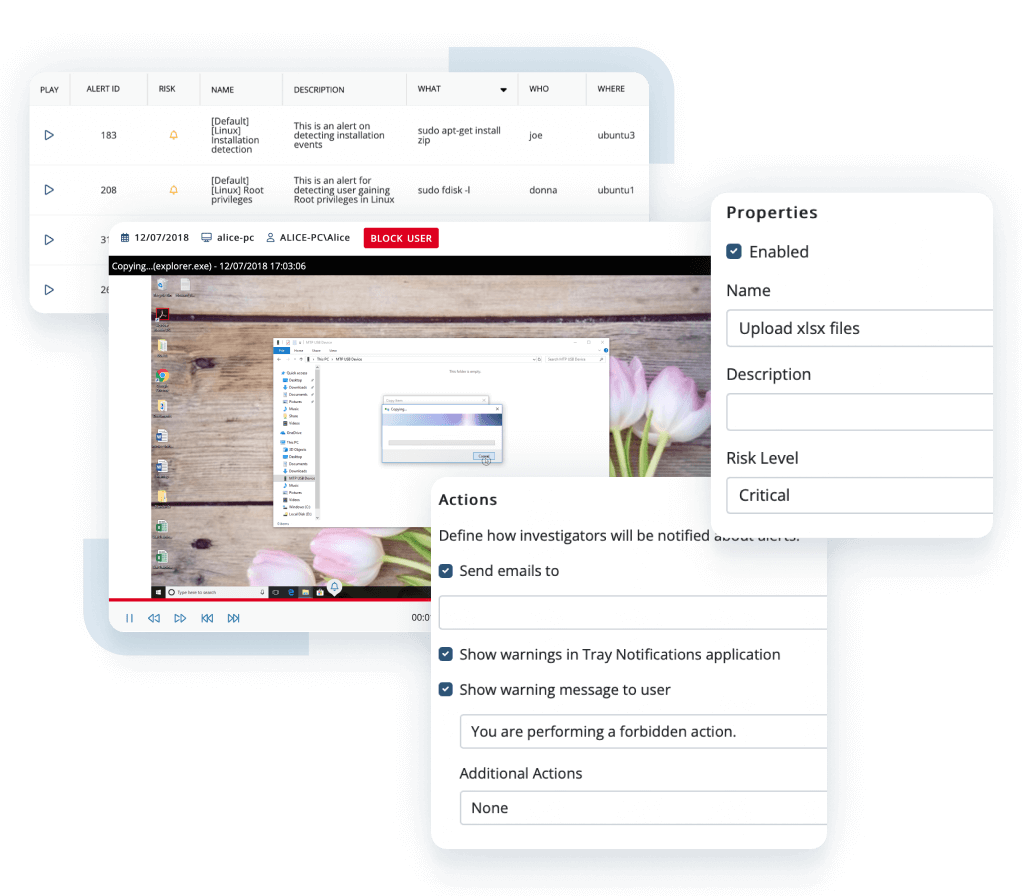

The Ekran System powerful tools help to analyze a potential cyber threat landscape for a specified time period and cross-check incident response activities.
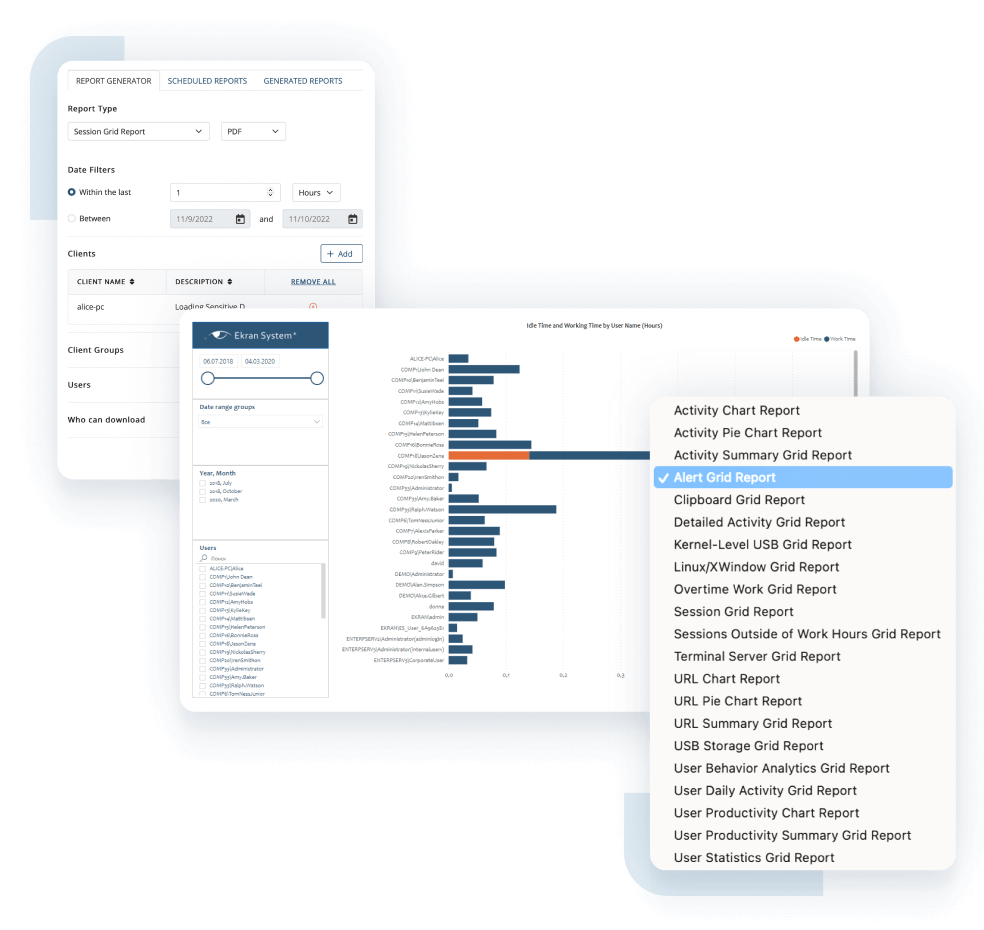

Ekran System ensures the implementation of numerous IT cybersecurity tools and practices required by most security laws, standards, and regulations.
Reviews
Insider risk management insights


How to build an insider threat program in 10 steps
Download Ekran System’s white paper and learn what an insider threat program is, how to develop one, and why it’s beneficial for any organization.
Download White PaperSee why over 2,500 organizations across the world rely on Ekran System
Get more with enterprise-grade
insider threat management software
Fast incident response
with a visually structured evidence trail
Context-rich recordings significantly reduce CERT and SOC response times. One-click search across suspicious activity makes investigations faster and more effective.
AI-based compromised account detection
Cybercriminals are constantly improving their ways of compromising privileged accounts. Powered by artificial intelligence, the Ekran UEBA system can detect a hacker who has penetrated a corporate system using stolen credentials.
Lightweight software agent and highly optimized formats for storing data
The lightweight agent works silently and isn’t noticeable to users or other programs. Collected data is saved in searchable and highly optimized video, audio, and text file formats for compact log storage and easy reporting.
Active in your environment in 20 minutes or less
Ekran System is quick to install and easily integrates with SIEM and ticketing systems. You’ll get a ready-to-use solution right after a coffee break.
Industry recognition


Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.
Get in Touch

Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.
Get in Touch






