Enhanced Auditing and User Activity Reporting
Leverage Ekran System’s reporting and statistics functionality to protect your organization from insider threats.
Enhance your organization’s security posture with comprehensive and informative reports that shed light on potential insider threats. With well-organized and insightful reports, you can:
- Identify patterns of behavior that put your organization at risk
- Foresee malicious activity and prevent damage
- Mitigate and investigate cybersecurity incidents
Ekran System offers robust reporting and statistics functionality that helps companies to
Detect insider threats early
Respond to incidents efficiently
Build a clear evidence trail
Maintain IT compliance
With Ekran System, you can generate detailed reports in multiple formats and analyze the threat landscape over specific periods of time. Easily conduct security and IT compliance audits and enhance your incident response activities.
Bring security audits to a new level with Ekran System’s advanced reports
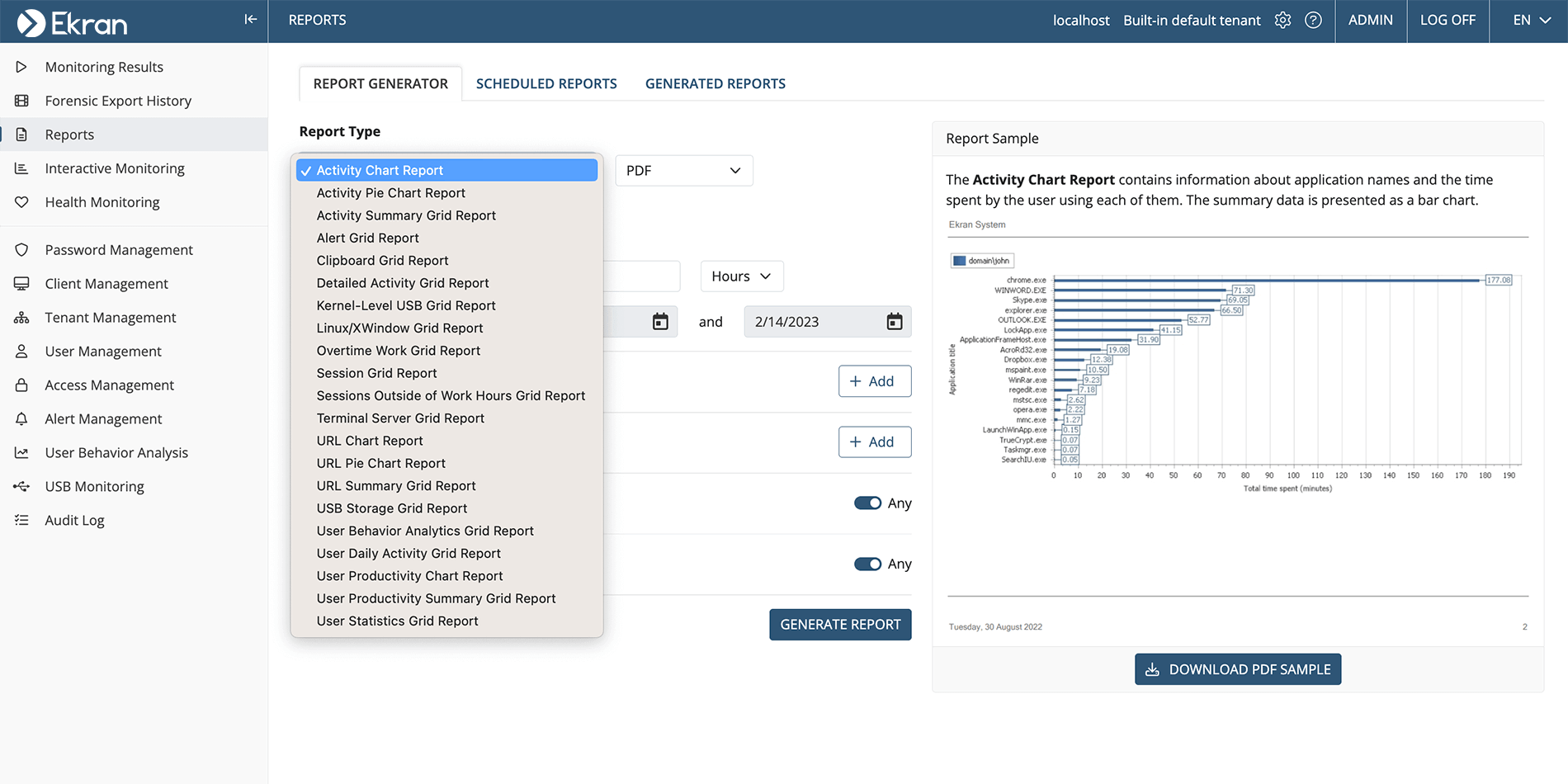
To help you gain valuable insights into your organization’s security and compliance, Ekran System offers 20+ types of reports, and this number is constantly growing. Discover the four most popular types of reports among Ekran System users:
Application usage
Select specific users to get a clear view of the time they spend in each application. Reports show you user activity across multiple clients over a selected period of time.
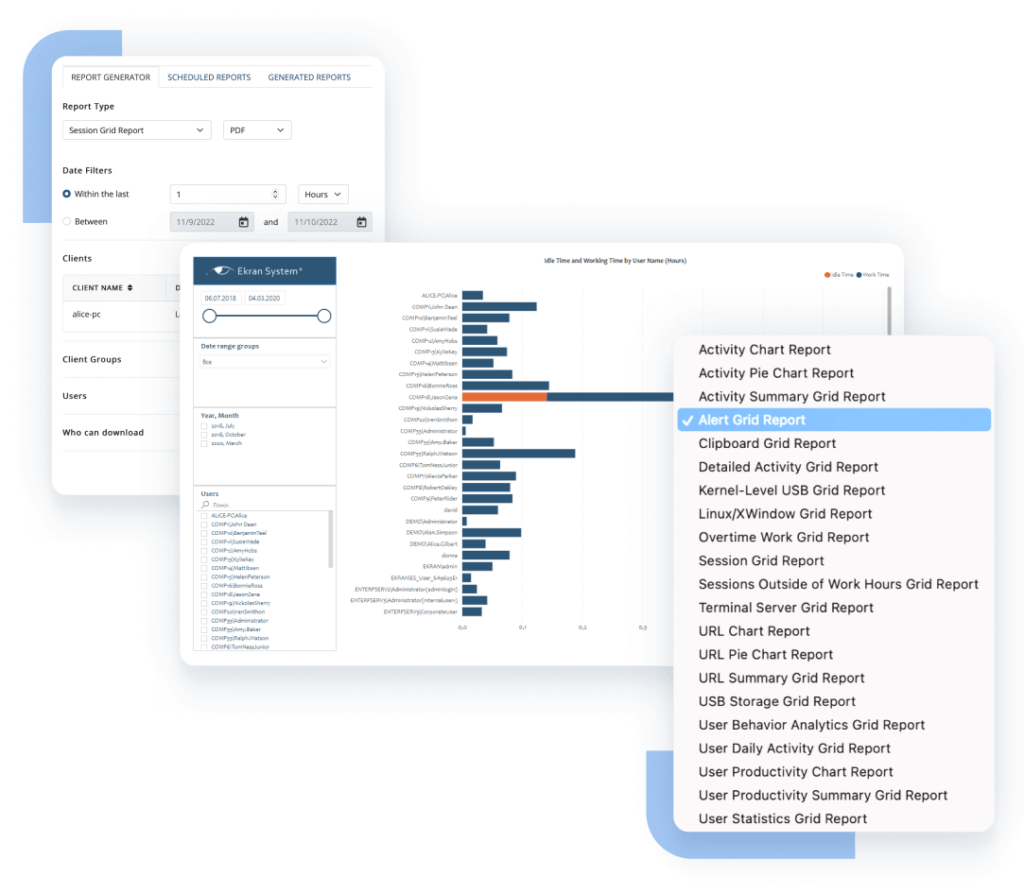
User productivity
Check the productivity of all users over a specified time period in an easy-to-read bar chart. Idle time is excluded from the report, providing you with a clear picture of actual user activity.
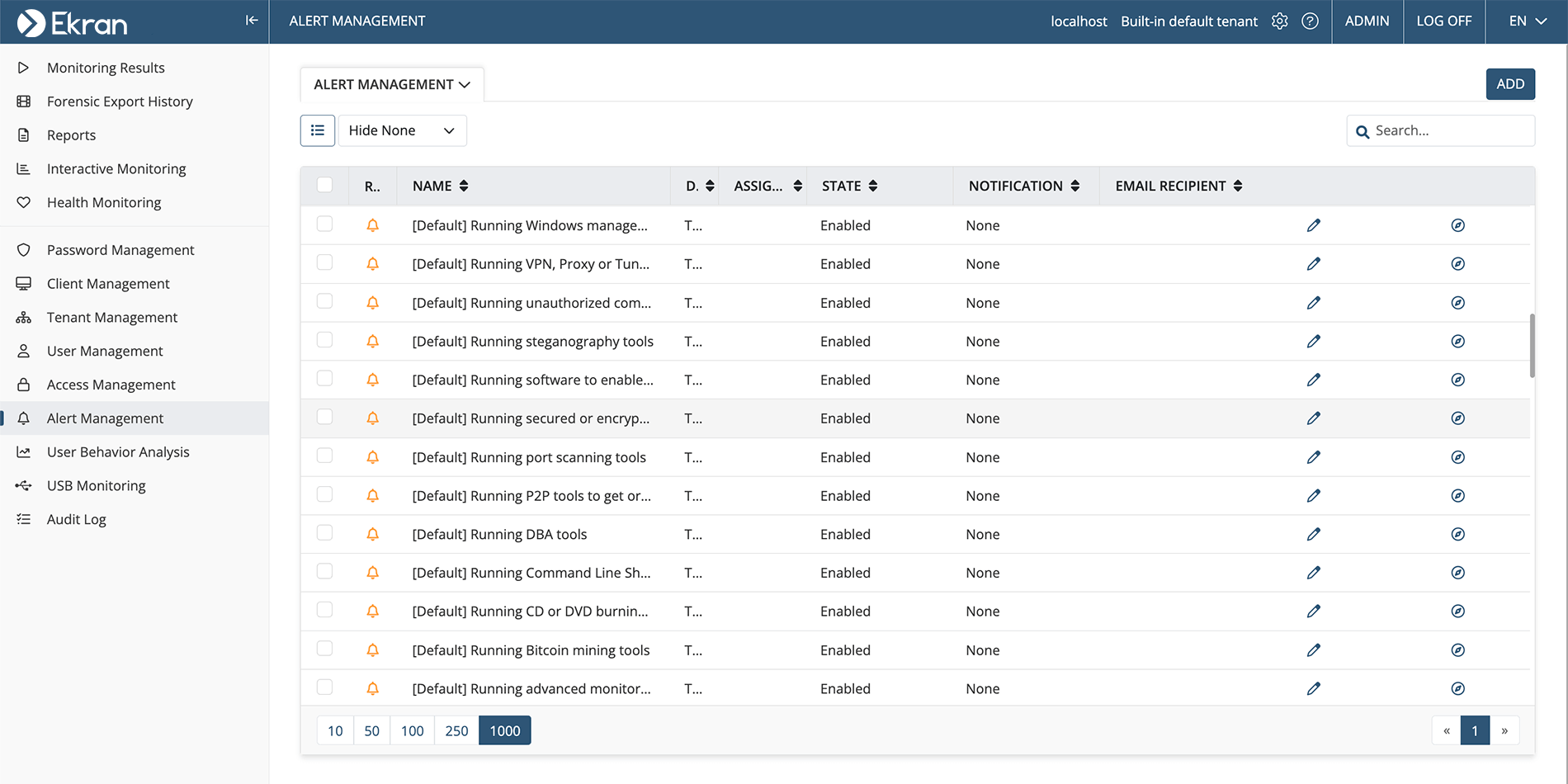
Security alerts
Get a comprehensive view of all security alerts triggered by selected users and see a holistic perspective of potential insider threats.
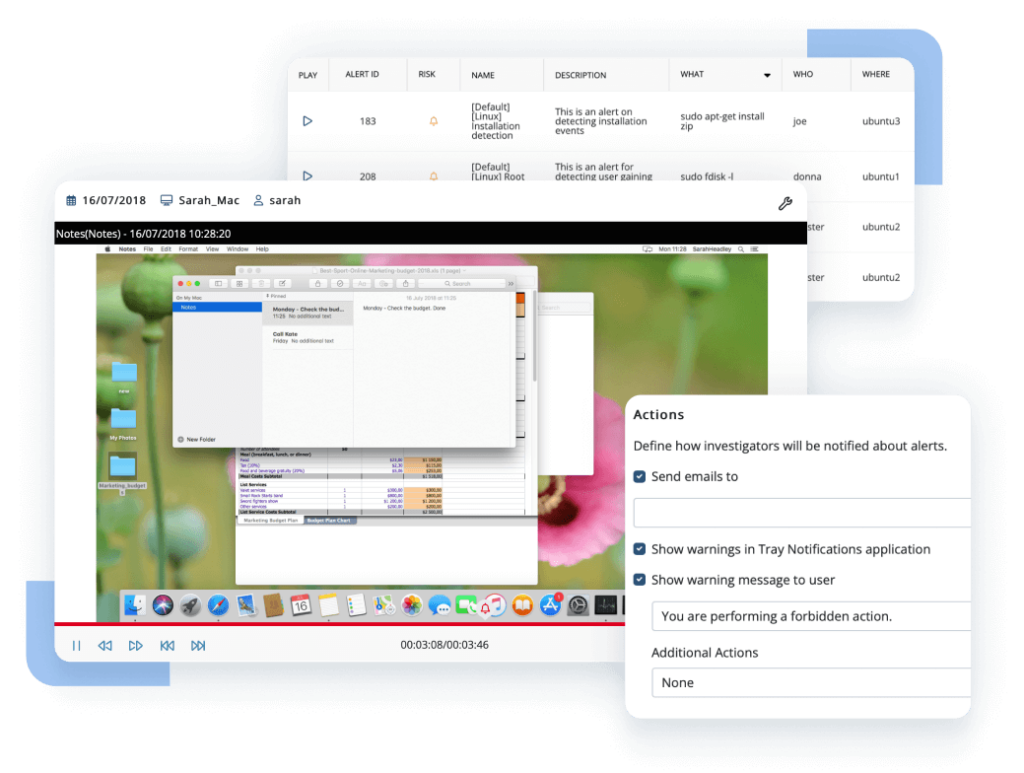
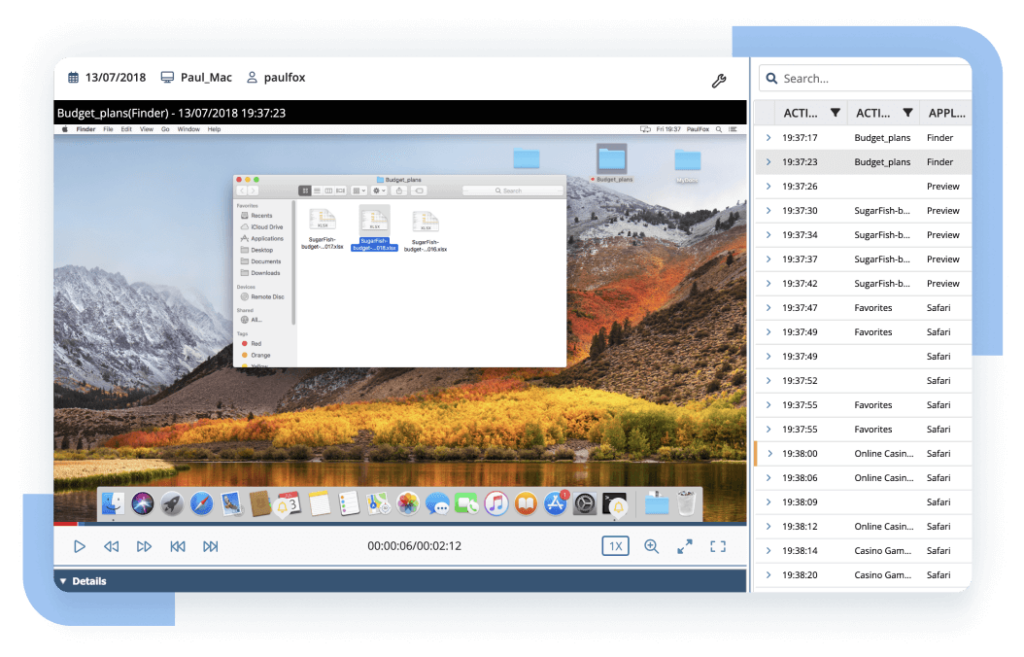
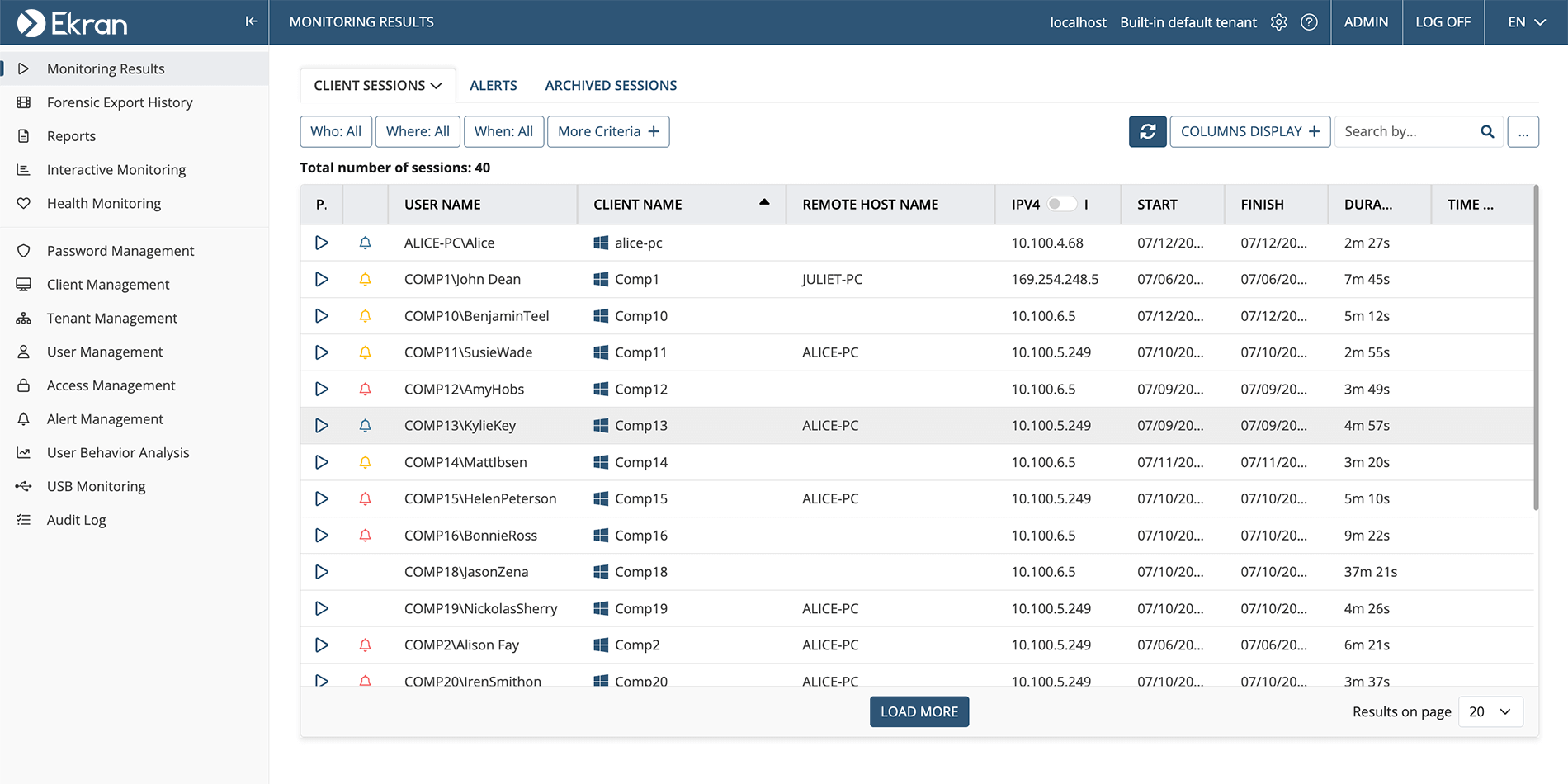
User sessions
Receive an exhaustive summary of all user sessions, allowing you to detect possible threats by noticing suspiciously long sessions or unusual IP addresses. You can also access session recordings straight from the report.
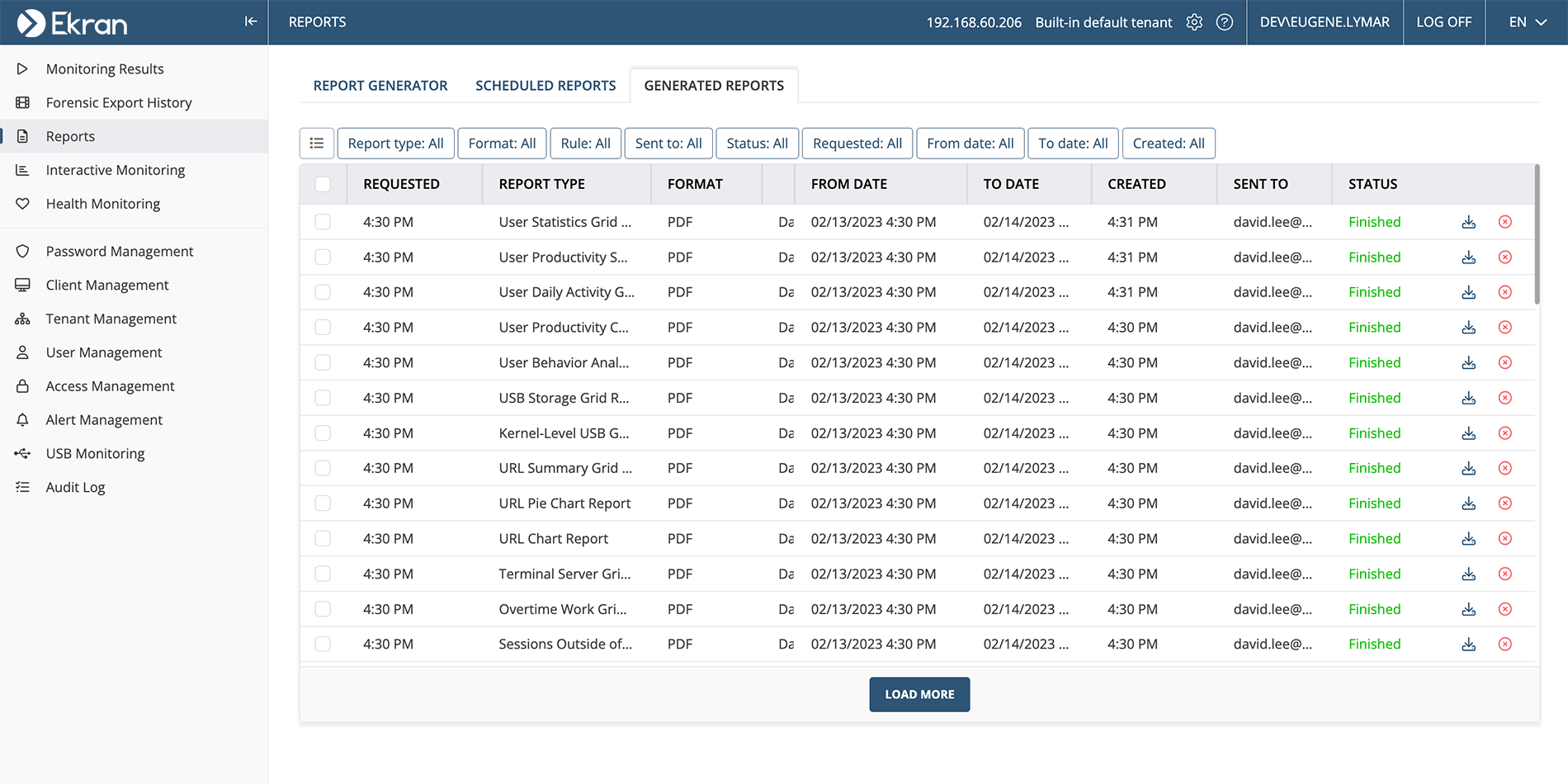
Leverage the flexible reporting and statistics functionality in Ekran System to generate ad hoc reports manually, or schedule the emailing of automatically generated reports to specific recipients.
You can create reports in a variety of formats including PDF, HTML, Excel, CSV, and both plain and rich text. Thanks to Ekran Systems’s integration with Microsoft Power BI, you can present collected data in a custom, interactive, and user-friendly way.
Screenshots
Empower your organization’s cybersecurity with Ekran System’s insightful reports today!
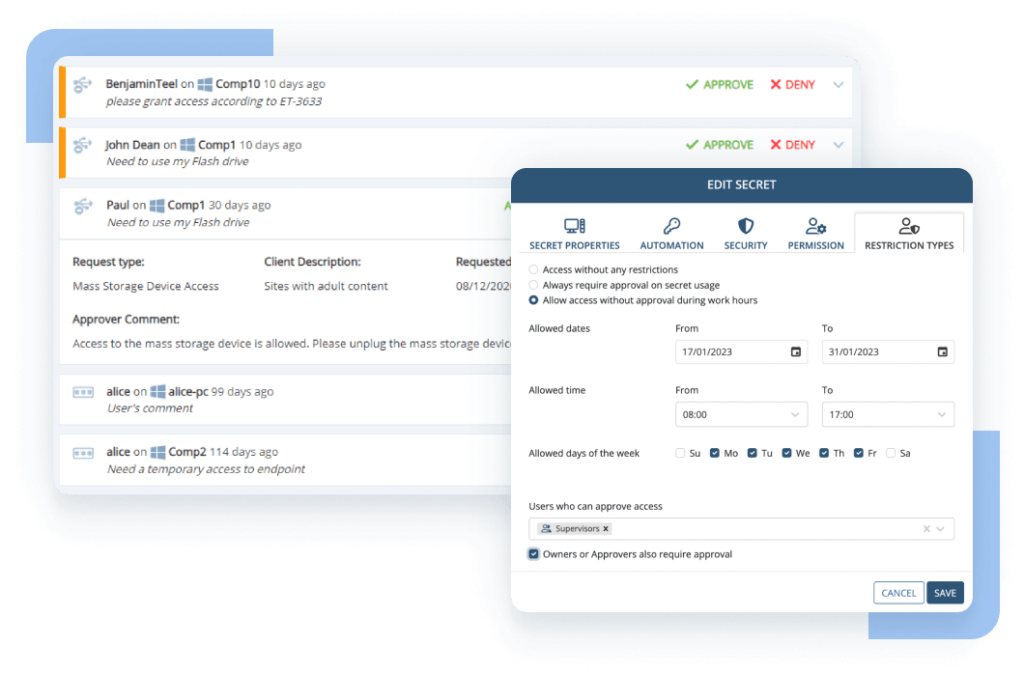
Keep track of admins’ activity with a thorough audit trail
Ekran System’s Audit Log helps you ensure that no one can hamper the insider threat management process in your organization. This feature logs all user actions within Ekran System’s Management Tool, including blocking and unblocking users, changing monitoring settings, and enabling and disabling alerts.
With Audit Log, you can obtain an audit trail of all administrative activity performed in Ekran System and track access to security monitoring records. Besides facilitating security process audits, it also helps you meet regulatory IT compliance requirements.
Detect anomalies.
Generate reports.
Investigate incidents.
Watch a 6-minute overview of the Ekran System insider risk management solution, showcasing access management, user activity monitoring, user behavior analytics, reports and statistics, and insider threat detection.
Export encrypted evidence for forensic investigation
Ekran System provides a secure method for exporting encrypted data of fully monitored sessions or their fragments for investigation purposes. Exported data includes:
Video logs
Synchronized metadata
When you export encrypted data, you receive a .efe file that Ekran System signs with a server-specific e-key, transforming it into a protected format. The format of this file guarantees the integrity and authenticity of exported monitored data, which means you can validate it at any time and use it for further investigation and forensic activities.
How your organization can benefit from Ekran System’s reporting and auditing
Explore common scenarios in which you can use Ekran System’s reports and statistics functionality to enhance your cybersecurity.
Ekran System alerts your security team of suspicious employee behavior.
Security officers generate an ad hoc report and analyze it to define if this user activity is accidental or intentional.
Your security team sees that an employee attempted to access a restricted folder with confidential information. They block the user to prevent a security incident and start a thorough internal investigation.
Your security team gathers data in Ekran System for a cybersecurity audit or IT compliance audit.
They analyze the data and identify areas where the organization isn’t fully compliant with regulations and policies.
The organization takes corrective actions to address compliance issues. For example, you might update policies and procedures or provide additional training to employees.
Your security team conducts an internal investigation using Ekran System’s reporting features.
The security team exports a protected .efe file with encrypted evidence of an employee’s malicious activity.
Your organization cooperates with the legal investigation team and submits the .efe file with forensic data. The insider is prosecuted and held accountable for their actions.
Get the most value for your business with other Ekran System’s capabilities
Supported platforms
Ekran System integrations
Ekran System employee tracking software seamlessly integrates with your infrastructure, including with leading SIEM and ticketing systems.
Case studies
What our clients say about Ekran System’s insider threat prevention tools
FAQ
Cyber attackers are constantly looking for new ways to gain access to sensitive information. By monitoring user activity and leveraging the user and entity behavior analytics (UEBA) module in Ekran System [PDF], you can detect potential security threats before they become security incidents and can prevent data breaches and other risks.
In addition, organizations in many industries including healthcare, finance, and insurance are subject to strict regulatory requirements. Failure to comply with those requirements can result in fines and reputational damage for organizations. By monitoring user activity, you can take the steps necessary to protect sensitive information and comply with IT requirements.
User activity monitoring solutions like Ekran System can also help you to identify insider threats, such as employees who intentionally or unintentionally mishandle sensitive data. Using Ekran System, you can quickly respond to suspicious user activity and prevent damage to your organization.
Choosing the right software for suspicious activity reporting is essential to protect your business from security threats and comply with regulatory requirements. Here are some factors to consider when selecting what product to use:
Scalability: Look for a dedicated solution that can scale with your business so you can monitor and report on suspicious activity across all your systems and devices as your company grows.
Real-time monitoring: Choose software that provides real-time monitoring of user activity so you can quickly identify and respond to potential threats.
User and entity behavior analytics (UEBA): Consider software that uses AI to identify deviations from baseline behavior and notifies security officers about suspicious actions.
Ekran System is insider threat management software that satisfies all these criteria and allows for efficient user activity reporting. Ensure that your security and IT compliance audits are as informative and insightful as possible with Ekran System’s user activity monitoring, internal audit trail, huge selection of reports, and integration with Microsoft Power BI.
Here are two major strategies that can help you to identify suspicious behavior and respond before it results in damage to your organization.
- Monitor for anomalies or deviations from normal patterns of behavior. If a user suddenly begins accessing files or systems outside of their normal work hours or geographic location, this could be a sign of unauthorized activity. Similarly, if a user accesses large amounts of data or attempts to transfer files to external devices without a valid reason, this could be a sign of malicious activity.
- Monitor for behavior that is inconsistent with the user’s job duties or level of access. If an employee attempts to access systems or data not consistent with their role in your organization, this can be a sign of malicious intent. Consider keeping an eye out for cases when users with basic access permissions attempt to access protected confidential data or make changes to system settings beyond their level of access.
Identifying suspicious user behavior requires a combination of technical tools and cybersecurity awareness. By using Ekran System to monitor user activity within your network and leveraging its user and entity behavior analytics (UEBA) module [PDF], you can instantly notice malicious activity and act quickly to prevent an incident from occurring or to remediate the consequences.
Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.