
Third-Party Vendor Security Monitoring Software
Monitor activity. Manage privileged access. Respond to incidents. ALL-IN-ONE
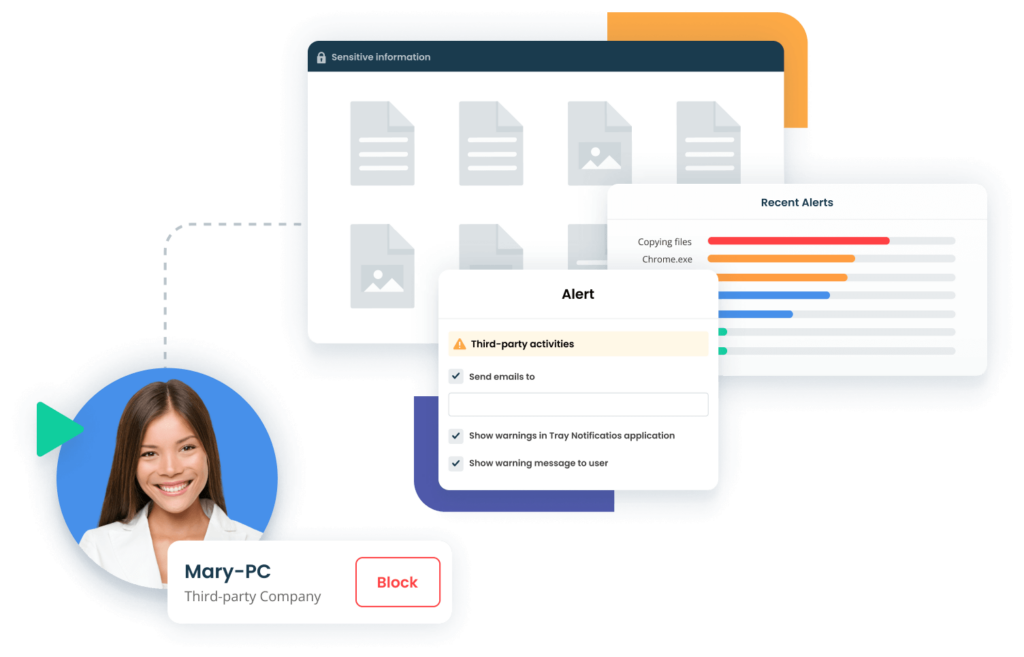
The third-party security monitoring challenge
While the term “corporate infrastructure insider” is frequently used to refer to in-house employees, there’s one more category of users with access to corporate infrastructure — those who work for third-party organizations providing professional outsourcing services.
These organizations can be:
- Managed service providers (MSPs), in particular, managed security service providers (MSSPs)
- IT outsourcing service providers, frequently referred to as IT providers
- Remote third-party vendors
- Independent auditors and experts
These people can administer your databases, configure and maintain your servers and critical applications, monitor security perimeters, test system vulnerability, and perform other important tasks to ensure business continuity.
Due to their roles and tasks, they have privileged access to critical endpoints and are in touch with sensitive information. But how to monitor third parties? The answer lies in using dedicated third-party risk monitoring software.

Why you need a third-party vendor monitoring and auditing solution
IT provider monitoring and remote third-party vendor management and auditing are essential parts of overall risk management and regulatory compliance.
Outsourced administrative service providers can change the configuration of critical systems, and thus their actions need to be monitored closely.
Outsourcing service providers have access to the enterprise protected perimeter and, naturally, third-party monitoring solutions should be part of a company’s security strategy.
Outsourcing staff can access, modify, or even delete sensitive data. Third-party security monitoring is crucial to ensure data security.
A comprehensive subcontractor security solution
Continuous third-party monitoring software
Syteca meets all of a company’s needs by setting up third-party vendor security monitoring processes.
The solution can be easily deployed on critical endpoints, providing visibility with the help of detailed video logs of any SSH and RDP sessions by third-party service providers.
You can configure Syteca to record sessions by all users or only sessions by selected usernames or IP addresses, allowing you to focus on 3rd party monitoring.
Due to the typically escalated privileges of such third-party providers, MSP monitoring software and third-party security monitoring services must provide a comprehensive set of privileged user activity control features.
Syteca third-party monitoring software does just that:
- Records user sessions with privileged user activity monitoring
- Advanced client protection mode prevents unauthorized administrative attempts to block monitoring
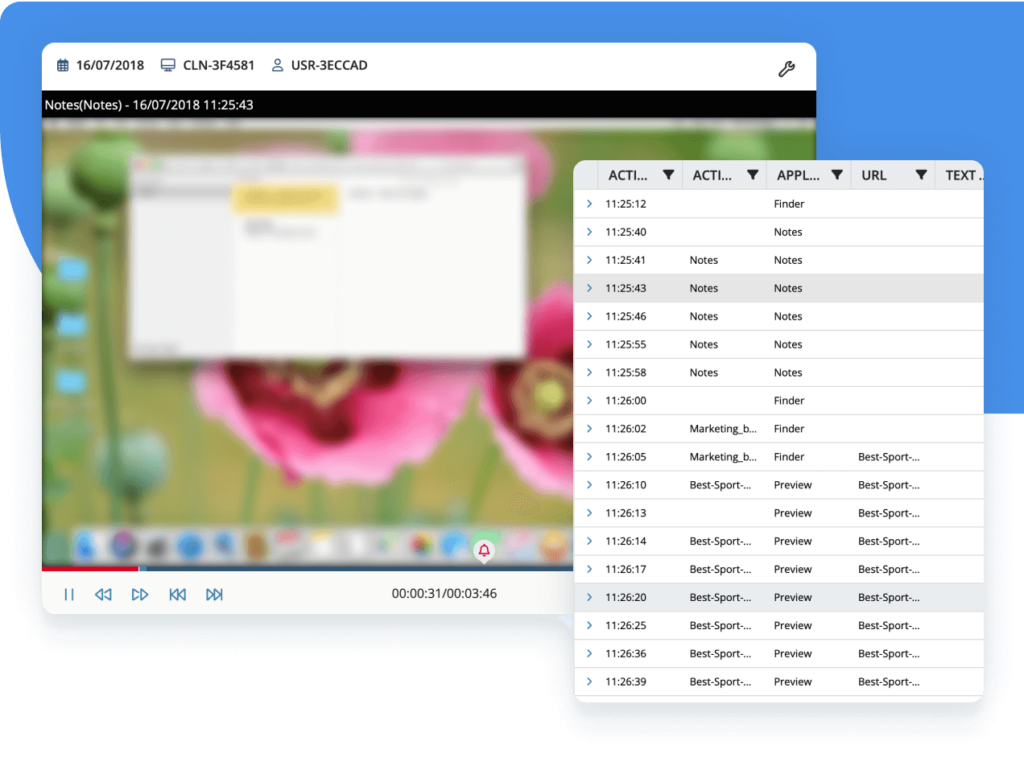
Third-party identity verification
As subcontractor sessions are typically remote, thorough identity verification for each connection is crucial.
Syteca equips your team with:
- Multi-factor authentication (MFA) based on credentials and mobile devices.
- Secondary authentication for shared logins to deal with default logins like admin and root, which are frequently used by remote administrators. Secondary authentication allows activity to be clearly assigned to an individual user.
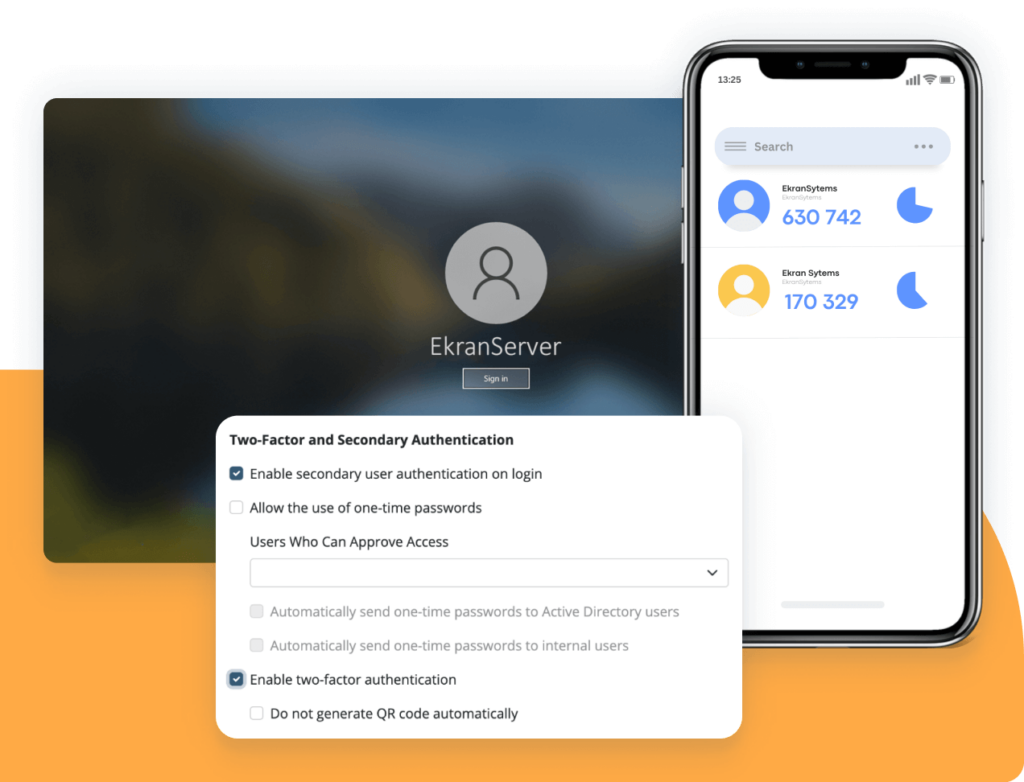
Third-party access control
Syteca third-party access security solutions provide granular access control:
- Terminal Server clients deliver a complete privileged account and session management (PASM) tool set for granting and managing temporary access.
- One-time passwords can be used for the most critical endpoints or emergency access.
- For the most high-risk scenarios, you can set up access request and approval workflow.
- Ticketing system integration allows you to implement purpose-based access.
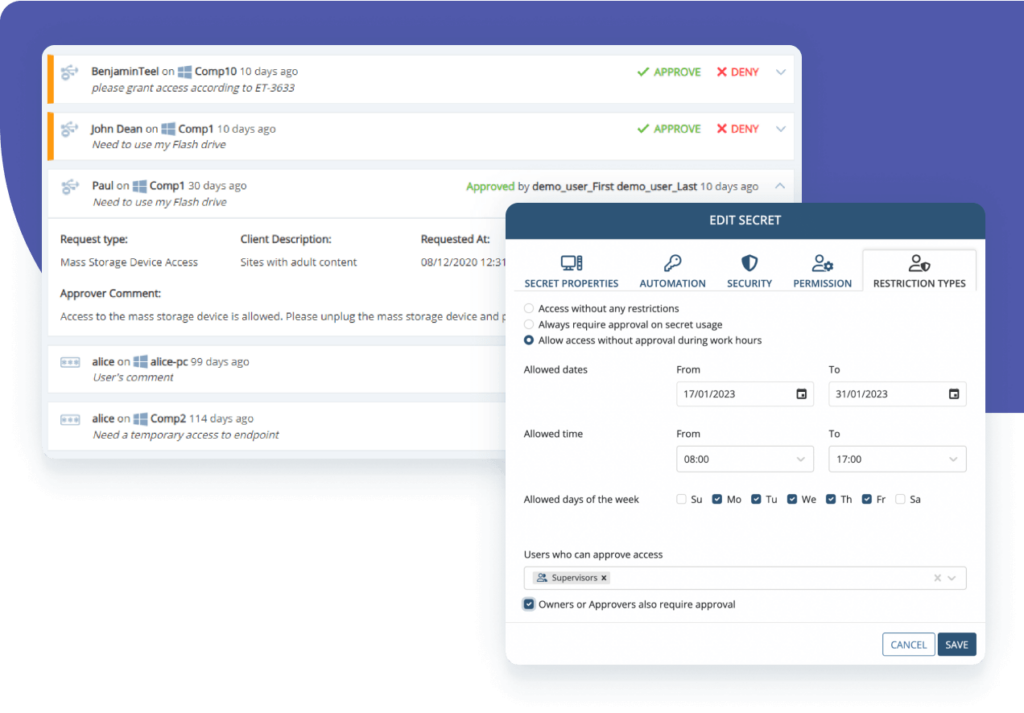
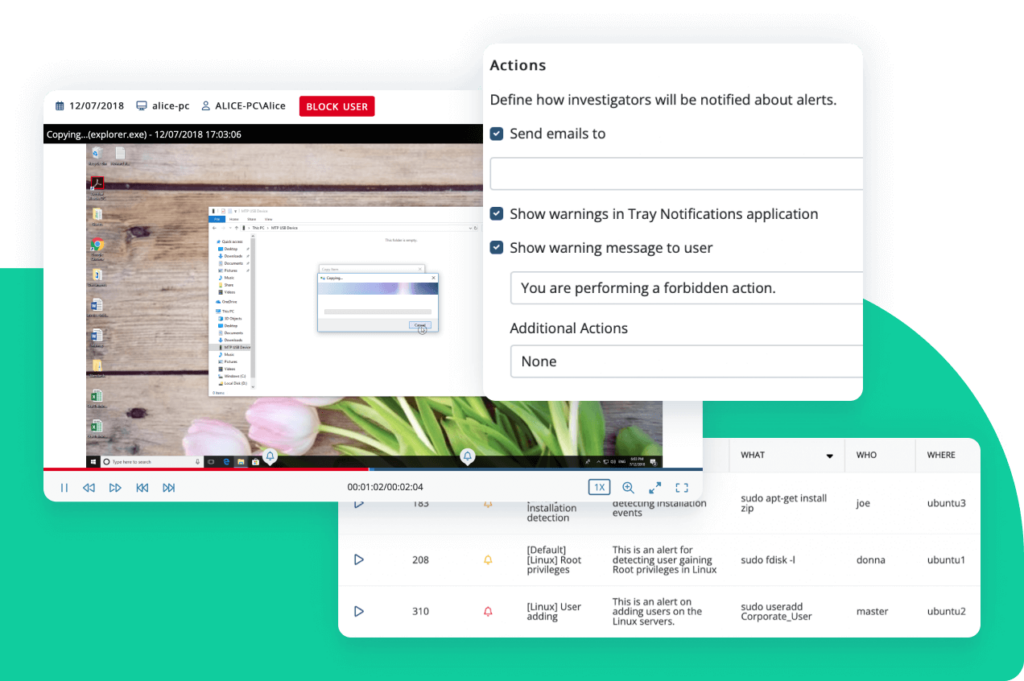
Real-time alerts and activity reports
When an IT provider or third-party vendor performs an abnormal or security-critical action, your team will be notified and provided with context of the incident so they can respond immediately.
Besides real-time alerting on potentially dangerous actions within sessions, the system can also notify your security team when a session is being established by specific users or from specific IPs. Critical alerts can trigger automated incident response actions, such as terminating a session or blocking a user.
Various general user activity reports make it even simpler and more efficient to monitor IT providers and third parties.
Get more with an enterprise – grade third-party security monitoring solution
Combining powerful MSP and third-party vendor risk management software features, Syteca offers flexible licensing while remaining cost-effective for deployments of any size.
The platform includes enterprise-ready features such as support for multi-tenant deployments, high availability, advanced archiving, SIEM, and ticketing system integration.
Lightweight software agent and highly optimized formats for storing data
The lightweight agent works silently and isn’t noticeable to users or other programs. Collected data is saved in searchable and highly optimized formats.
Active in your environment in 20 minutes or less
Syteca is quick to install and easily integrates with SIEM and ticketing systems. You’ll get a ready-to-use solution right after a coffee break.
Syteca provides universal third-party vendor security for any network architecture, including hybrid
Get the most value for your business with other Syteca’s capabilities
Supported platforms
Syteca integrations
Syteca privileged access management easily integrates with your existing infrastructure, including leading SIEM and ticketing systems.
Case studies
Watch our customer’s experience with Syteca’s third-party monitoring
What our clients say about Syteca’s insider threat prevention tools

Monitor user activity with Syteca
FAQ
Consider taking these steps when monitoring third-party risks in your organization:
- Identify the potential risks associated with your third-party vendors. These can include compliance, cybersecurity, reputational, and operational risks.
- Establish a set of third-party monitoring procedures. Specify the tools your security team should use for monitoring and the types of reports and audits they need to perform. Clarify how often your security officers need to generate reports and perform third-party security audits.
- Leverage third-party monitoring solutions. Dedicated third-party risk monitoring software like Syteca can help you automate the monitoring process and scale your organization’s third-party risk management efforts.
Major challenges in establishing an efficient third-party monitoring process include the following:
- Lack of transparency. Third-party service providers may not provide complete information about how they work with critical data and systems, making it difficult for your organization to identify actual risks.
- Lack of control. Although your organization is responsible for making sure that your supply chain vendors meet all necessary cybersecurity requirements, you may have limited control over your third parties.
- Ever-changing risk landscape. Third-party relationship risks are constantly evolving, with new threats emerging regularly. It can be challenging to keep up with changes and update your monitoring procedures accordingly.
Your organization may face third-party cybersecurity risks due to external entities within the supply chain. Such risks may arise due to your vendors, service providers, suppliers, partners, or contractors that have access to your organization’s systems and/or sensitive data.
Here are the most common types of third-party risks:
- Cybersecurity risks: Cyber attacks, data breaches, or other security incidents that could damage your organization
- Operational risks: Risks related to disruption of business operations caused by vendors and contractors
- Compliance risks: Possible negative impacts of third parties on your organization’s compliance with laws, regulations, or standards applicable to your industry
The security of third-party vendors you cooperate with is critical, as it may influence your organization’s security as well. Here are some negative consequences your organization may suffer due to a lack of cybersecurity in a third-party vendor:
- Unauthorized access. Cybercriminals often target small service providers to gain access to a larger organization’s systems and data. If your vendor’s security is compromised, it can provide an entry point for attackers to your organization’s systems.
- Data breaches. Cybercriminals may use improperly protected systems of third-party vendors to access and steal your organization’s sensitive data and intellectual property.
- Non-compliance issues. You are responsible not only for complying with IT requirements applicable to your organization but also for the compliance of your third-party vendors. Thus, if your third-party vendor is not compliant with some requirements, your organization could face fines, legal action, or reputational damage.
Relationships with third-party vendors and service providers can expose your organization to a wide range of risks, including compliance, financial, reputational, and operational. By implementing third-party risk management processes, you can identify and assess these risks and take appropriate steps to mitigate them.
In brief, a well-implemented third-party risk management process can help you to:
- Meet regulatory compliance
- Protect your organization’s critical data
- Prevent financial and reputational losses
- Build trustful relationships with third-party service providers
Managing insider risks in complex supply chains can be a daunting task. However, leveraging third-party vendor risk monitoring services can simplify the process. Syteca offers a set of comprehensive third-party vendor risk management tools, including continuous user monitoring, identity verification, access control, real-time notifications, and activity reports.
Third-party monitoring software is designed to help organizations manage and mitigate insider risks that can arise from contractors and outsourcing service providers. With third-party risk monitoring software, your organization can improve supply chain visibility, reduce the risks of insider threats, and comply with industry regulations and standards.
Syteca is a good example of third-party monitoring software. It provides a complete set of third-party risk detection and management tools such as continuous user activity monitoring, identity management, access control, real-time incident response, and activity reporting.
Blog spotlight
Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.















