Security Incident Investigation Solution
Monitor insider activity. Detect anomalies. Respond to incidents. ALL-IN-ONE
Suspect an internal data leak? Does something indicate that cyber crime or fraud has a foothold in your infrastructure? Are there signs of a persistent threat? It’s time to act!
Ekran System® provides you with simple yet powerful tools to investigate security incidents such as data leaks, fraud, and other potentially malicious activity inside your perimeter.

Screenshots
Incident investigation software
Being a universal insider threat protection platform, Ekran System can help you quickly investigate security incidents. Whether you need to investigate employees, audit third-party contractors, or research backdoor user accounts, Ekran is the tool for you.
Ekran System provides:
- Easy remote deployment on target servers and desktops.
- Flexible filtering options to focus on user groups, endpoints, and applications.
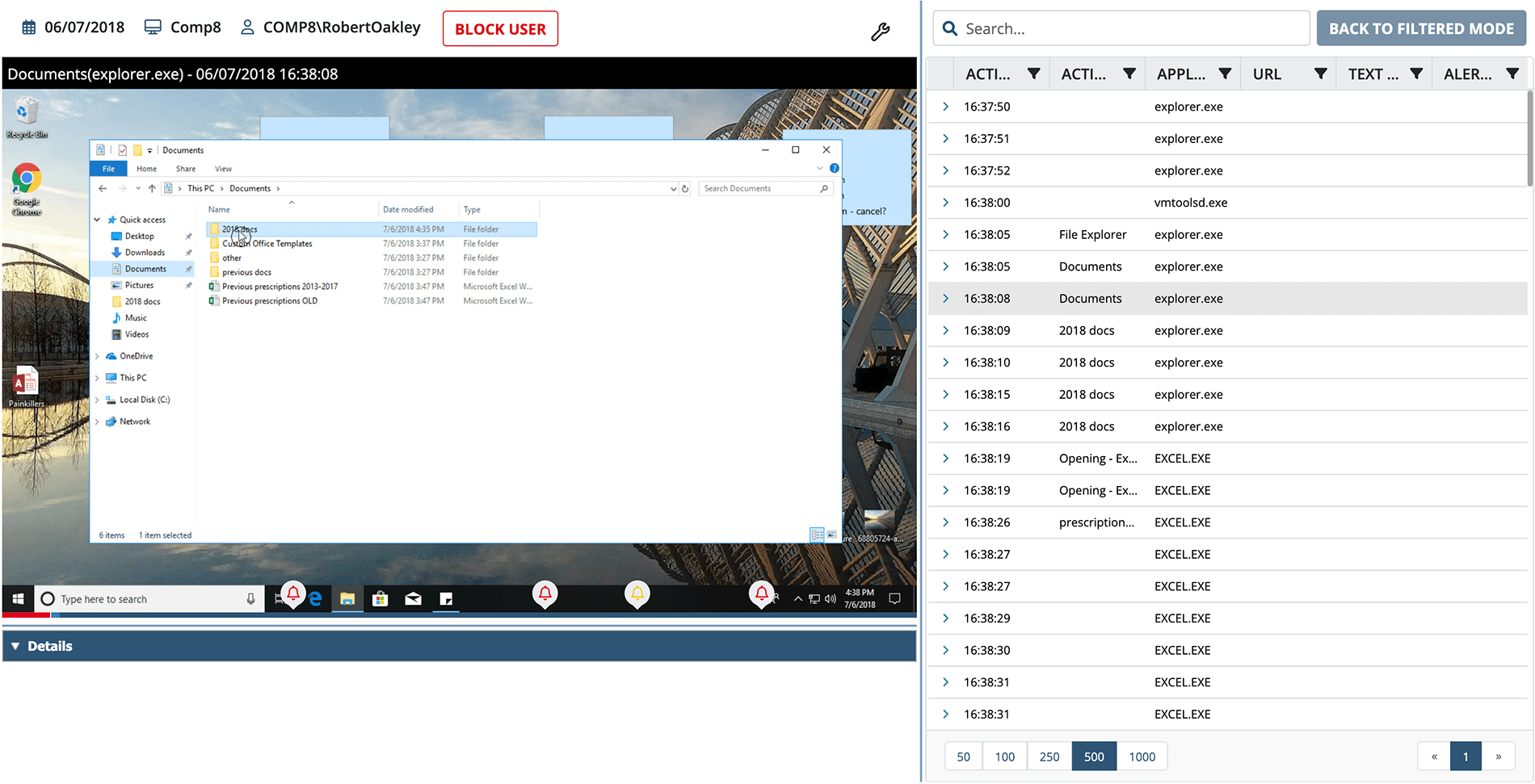
- Indexed session video records that are perfect for analysis.
- A rich tool set for search and reporting.
- Context-rich recordings, including application names, URLs, commands, keystrokes, and devices.
- Multiple incident response tools.
Сonduct a fraud investigation
Make Ekran System your data leak investigation software and get the possibility to detect and thoroughly research any user action in context.
- Install the Ekran System client on target endpoints.
- Configure monitoring rules (you’ll probably want to record all users and actions to start with).
- Get a complete searchable record of each user session.
- Search across all sessions to focus on particular objects, files, or actions.
- Replay key sessions and episodes to see the context of any situation.
- Easily add or transfer licenses between endpoints as your investigation unfolds.
- Export the results of your cyber crime investigation (including recorded sessions and episodes) in a forensic format.
Cyber incident response tools
Monitoring
Unlike many other massive security monitoring solutions, Ekran System has proven to be an effective and agile fraud investigation tool for detecting and investigating insider threats.
- Painless deployment doesn’t require global configuration changes.
- Integrated-by-design session video records catch any incident with full context.
- Analysis is easy with replay tools and advanced keyword-based search.
- UEBA and rule-based alerts generate instant notifications and create bookmarks in session records.
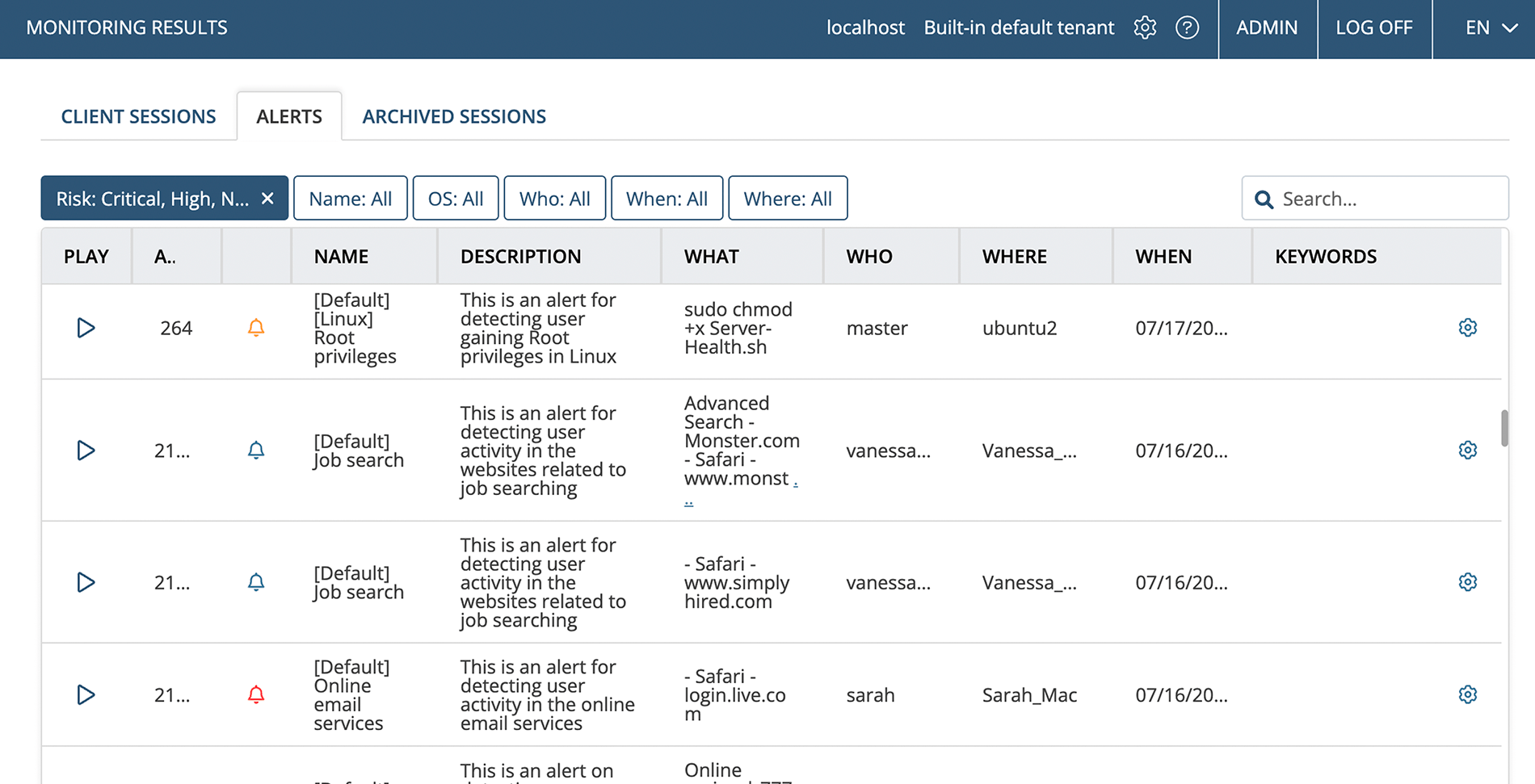
Alerting on critical actions
Although investigations usually center on retrospective data, it’s important to react to attacks as they unfold and get notified when a suspicious action is performed. Ekran System can deliver real-time notifications to your security team together with the full context.
The Ekran System alerting system includes two major components: rule-based alerts and user and entity behavior analytics (UEBA).
After configuring an optimal rule set, you can get alerts for events such as:
- A user logging in to a critical endpoint.
- An application being started.
- A file being opened.
- A command being entered manually or via a script.
- A specific USB device being connected.
The AI-powered UEBA module continuously checks user actions against baseline behavior and sends a notification when any behaviour anomaly is detected.
Manual and automated incident response
Being an efficient cyber security investigation tool, Ekran System also provides several incident response features including user warning and blocking, potentially dangerous process blocking, and USB device alerting and blocking.
When setting up alerts, you can configure automated responses: notifying a security officer, sending a warning message to the user, terminating the application, or blocking the user. After being alerted to an event, you can also connect to the still-running session and watch the activity in real time with the ability to block the user immediately.
When defining a device usage policy, you can not only set alerts for use of specific devices but also block them automatically.
Reporting
While hunting threats in session records, you can use Ekran’s broad reporting tools to summarize your data and localize incidents:
- Show all users accessing selected endpoints.
- Show all applications started within a given time period (with time spent using each application).
- Show the most and least used applications.
- Show all URLs visited within a time period.
- Show all user logins for an endpoint.
You can see more report types on the Ekran System website. If you’d like to use your findings as legal evidence, Ekran System provides you with a forensic export tool.
Access and identity management
Finally, you can clearly assign each session to an individual user and secure critical endpoints with Ekran’s built-in access management tools:
- Secondary authentication for users of shared credentials (like “admin”).
- Two-factor authentication for critical servers.
- Privileged account and session management.
- One-time passwords.
- Access request and approval workflow.
- Ticketing system integration.
- USB management.
Benefits of Ekran System®
Gain visibility over any desktop and server OS and network architecture
Get a single tool to look under any rock. Ekran System allows you to monitor all popular operating systems within physical and virtual infrastructures and on any network architecture. Track the activity of users as they jump from one endpoint to another.
Comprehensive base for any internal investigation
Ekran System equips your team with easy-to-interpret and easy-to-search indexed video records of all user activity, including the contents of uploaded scripts and details of connected devices. Besides session records, Ekran generates different kinds of reports on user activity to facilitate enterprise threat detection and analysis. The forensic export option helps you provide proper forensic evidence.
Get more than just a recording and analysis tool
Ekran System is a universal insider threat protection tool that delivers session recording and activity audits as well as real-time alerting, incident response, and comprehensive user identification and authorization functionality. Know exactly who initiates what actions when and request acknowledgement of actions and a rationale if needed.
Continuous non-intrusive monitoring
Designed to work smoothly with tens of thousands of endpoints, Ekran System demonstrates exceptional stability and performance without affecting your users’ work. At the same time, it collects complete records of any activity: Ekran System clients can work autonomously if the network connection is lost and are well-protected from blocking.
Low total cost of ownership
The unique licensing offered by Ekran System delivers rapid time-to-value for deployments of any size, from small pilots to enterprise projects. Due to its floating endpoint licensing, Ekran System allows you to perform targeted investigations and then easily scale to preventive overall monitoring.
Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.