


Set a meeting with us at RSA Conference 2024
Take people-centric approach to safeguarding your sensitive data

With insider threats becoming more frequent and detrimental, it’s daunting for companies to ensure the safety of internal systems and data while establishing effective cooperation among all contributors.
In-office and remote employees, third-party vendors, partners, and others who have authorized access to your infrastructure can put your valuable assets at risk, either carelessly or intentionally.
That’s why organizations worldwide are in need of a unified solution for managing and mitigating insider risks.

82% of data breaches involve a human element, be it clicking a phishing link, misusing privileges, or making a simple mistake.*
62% of system intrusion incidents happen because of breaches in the supply chain.*
67% of companies experienced over 21 insider-related incidents in 2022. That’s 7% more than in 2020.**
Large organizations spend an average of $22.68 million annually to resolve insider-related incidents. Small organizations spend an average of $8.13 million.**
* According to Verizon’s 2022 Data Breach Investigations Report
** According to the Ponemon Institute’s 2022 Cost of Insider Threats Global Report
Ekran System is a full-cycle insider risk management platform providing a wide variety of tools for detecting abnormal behavioral patterns as well as deterring and disrupting malicious insider activity.
Gartner lists Ekran System as a representative vendor in its recent Market Guide for Insider Risk Management Solutions.
Ekran System offers a versatile set of features and tools to control insiders’ actions in your infrastructure and timely detect breaches in corporate security.
Obtain a 360-degree view of your infrastructure with continuous employee and third-party activity monitoring and session video recording complemented by rich metadata indexing.
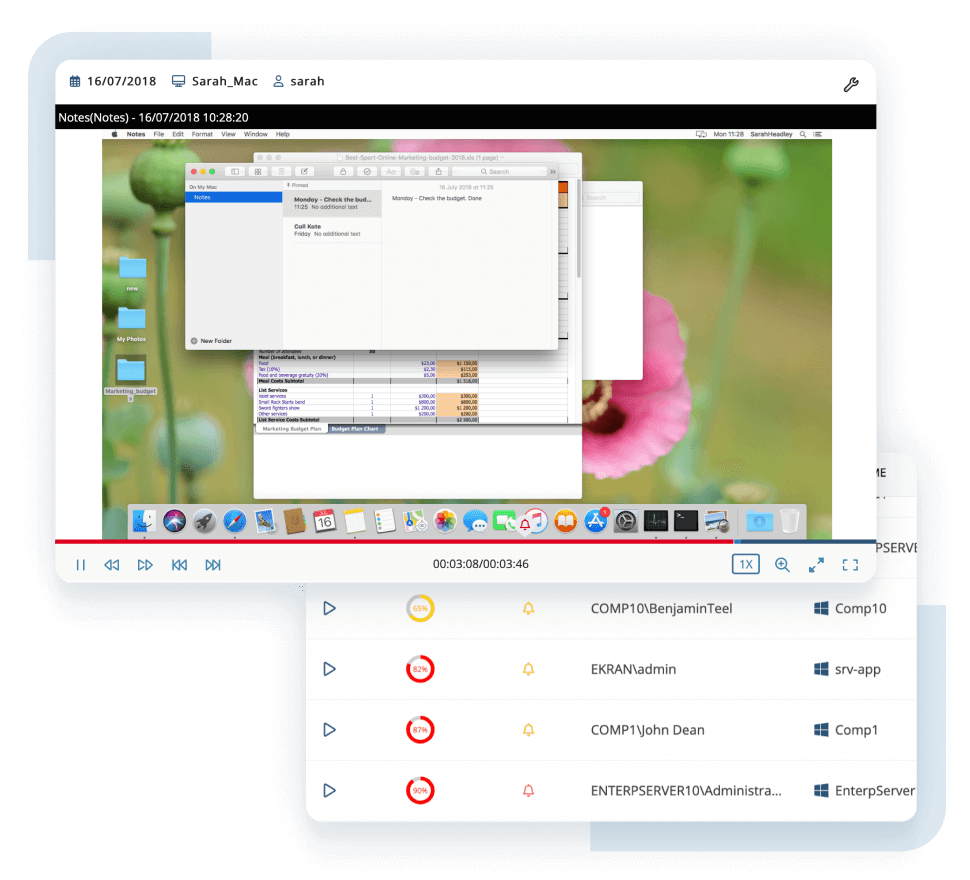

Promptly respond to suspicious insider activity by leveraging user and entity behavior analytics (UEBA) and customizable alerts and rules for blocking malicious actions.
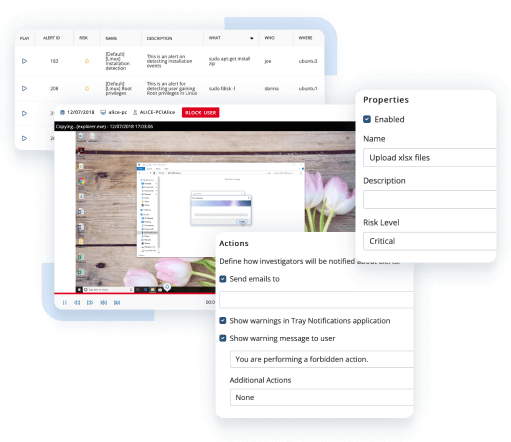

Accurately assess your insider risk landscape by taking advantage of numerous reports and smooth integration with Microsoft Power BI. If required, provide tamper-proof evidence to forensics teams and investigators.
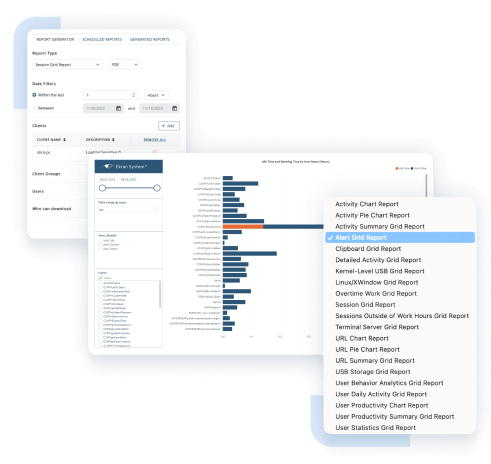

Meet the majority of IT security requirements by securely authenticating users, effectively controlling access permissions, and continuously monitoring user activity with no risk to users’ privacy.
Ekran System continuously monitors various endpoints, including both end-user machines and servers, within any network architecture. Being one of the best user activity monitoring tools for Windows, Ekran System also works for macOS and is a powerful Linux/UNIX session audit tool. It even supports X Window System and all popular virtualization solutions. Ekran System allows agent-based and jump server-based deployments as well as any combination thereof.
Designed for tracking user activity on tens of thousands of endpoints, Ekran System demonstrates exceptional stability and performance. As for maintenance and reliability, the platform provides high availability and multi-tenant deployment, system resource and health monitoring dashboards, and automated maintenance tasks.
Besides tracking user activity, Ekran System provides enhanced incident alerting and response functionality. But that’s not all. Using Ekran System Client, you can set up access and identity management. Since Ekran System also provides server user activity monitoring, you always know what is happening in your network.
The unique licensing offered by Ekran System enables cost-effective deployments of any size, from small pilots to enterprise projects. Floating endpoint licensing enables license reassignment in a couple of clicks. For virtual environments, this process is automated.
Visually structured evidence trail resulting in low incident response time
Context-rich recordings significantly reduce CERT and SOC response times. One-click search across suspicious activity makes investigations faster and more effective.
AI-based compromised account detection
Cybercriminals are constantly improving their ways of compromising privileged accounts. Powered by artificial intelligence, the Ekran UEBA module can detect a hacker who has penetrated a corporate system using stolen credentials.
Lightweight software agent and highly optimized data storage formats
The lightweight agent works silently and isn’t noticeable to users or other programs. Collected data is saved in searchable and highly optimized video, audio, and text file formats for compact log storage and easy reporting.
Active in your environment in 20 minutes or less
Ekran System is quick to install and easily integrates with SIEM and ticketing systems. You’ll get a ready-to-use solution right after a coffee break.
Ekran System employee tracking software seamlessly integrates with your infrastructure, including with leading SIEM and ticketing systems.


Organizations across various industries take advantage of insider risk management software — especially those that handle sensitive information.
Insider risk management software like Ekran System helps many organizations minimize insider risks, detect and prevent insider threats, secure sensitive data, and ensure compliance with IT security standards, laws, and regulations.
While insider risk management software may seem costly, it can help you prevent the high expenses associated with recovering from insider-related security incidents.
The cost of insider risk management software can vary depending on several factors, such as the size of your organization, the specific features you choose, and the required level of customization.
Moreover, some insider risk management software providers offer their services through a subscription model, while others may charge a one-time fee. As well, the cost depends on the licensing scheme software providers offer. For instance, the Ekran System licensing scheme is transparent — Ekran System is licensed based on the number of endpoints you need to monitor.
To get a better idea of how much insider risk management software costs, consider requesting quotes from different vendors and comparing them based on the features and services offered. Leave a quote request to get a cost estimate for deploying Ekran System in your infrastructure.
Ekran System software can help you proactively manage insider risks in your organization. Here is what Ekran System can help you do:
In combination, Ekran System’s capabilities can become your technological foundation for effective insider risk management. To learn more about using Ekran System after deployment, take a look at our technical documentation.
An insider threat is the risk that a user with authorized access to your organization’s sensitive resources may misuse that access to harm the organization.
Insider threats pose a significant danger to an organization since they may have various negative consequences, such as financial losses, reputational damage, loss of intellectual property, and compromise of sensitive data.
Here are some effective strategies that can help you reduce the risk of insider threats:
Ekran System’s functionality enables you to implement these and other security strategies in your organization. Request a free trial and start building your insider threat protection today.
Insider risk management solutions help organizations streamline their efforts in managing insider risks. There are a few reasons to deploy an insider risk management solution in your organization:
Overall, using an insider risk management solution is beneficial for your organization’s security. Ekran System offers numerous insider risk management tools to help you efficiently control insider risks; comply with industry laws, standards, and regulations; and enhance the protection of your sensitive data.
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.

