Real-time User Activity Alerts
& Incident Response
Detect threats. Receive alerts. Respond to incidents. ALL-IN-ONE
Strengthen your incident response
Ekran System allows you to quickly and efficiently respond to incidents thanks to its flexible rule-based system and automated response functionality. Streamline your incident management with Ekran System’s unified user activity monitoring and alert system.
Get notified of suspicious activity in real time
Identify and disrupt security threats
Investigate security incidents
Ensure business continuity
Minimize the damage from and impact of insider threats
Meet IT compliance requirements
From detection to investigation, Ekran System has got you covered
Ekran System’s alerting and incident response capabilities provide your organization with all the tools necessary to detect insider threats, disrupt them, and investigate incidents.
Stay on top of user actions with a rule-based activity alert system
Ekran System’s alerting and incident response functionality incorporates a system of granular alert rules. Once an event meets rule conditions, the system notifies your security officers or automatically responds to the event.
Ekran System’s security incident management and alert system offers:
- Predefined alerts. Use alert templates to detect common cybersecurity threats such as fraud, data leaks, and other insider actions.
- Custom alerts. Create your own alerts for unique user activity scenarios such as opening a specific application, visiting a particular website, or typing certain words.
Respond to incidents in a timely manner
When a security event is detected, Ekran System facilitates a quick manual response or automatically blocks the user or process.
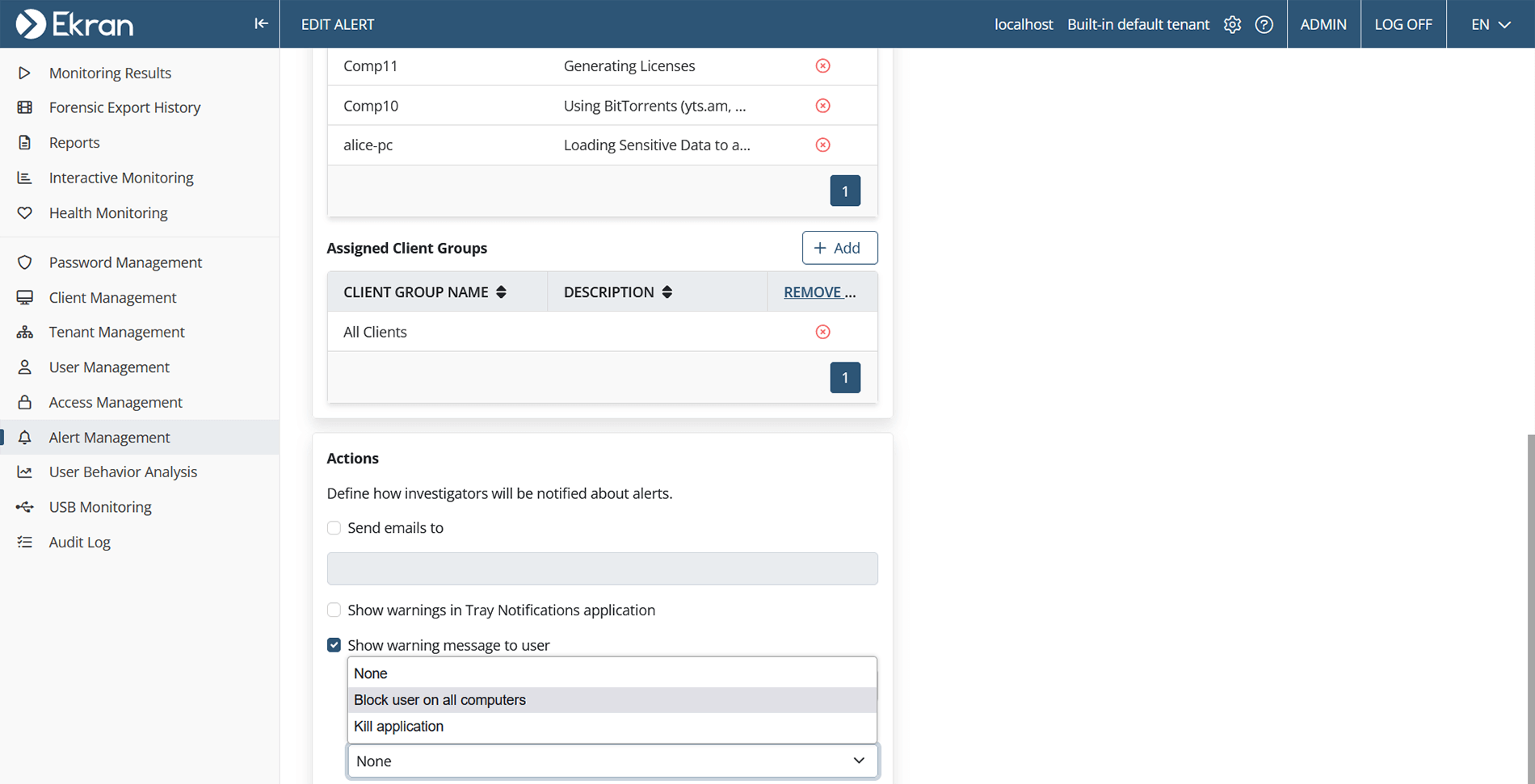
You can configure different types of responses for different incidents:
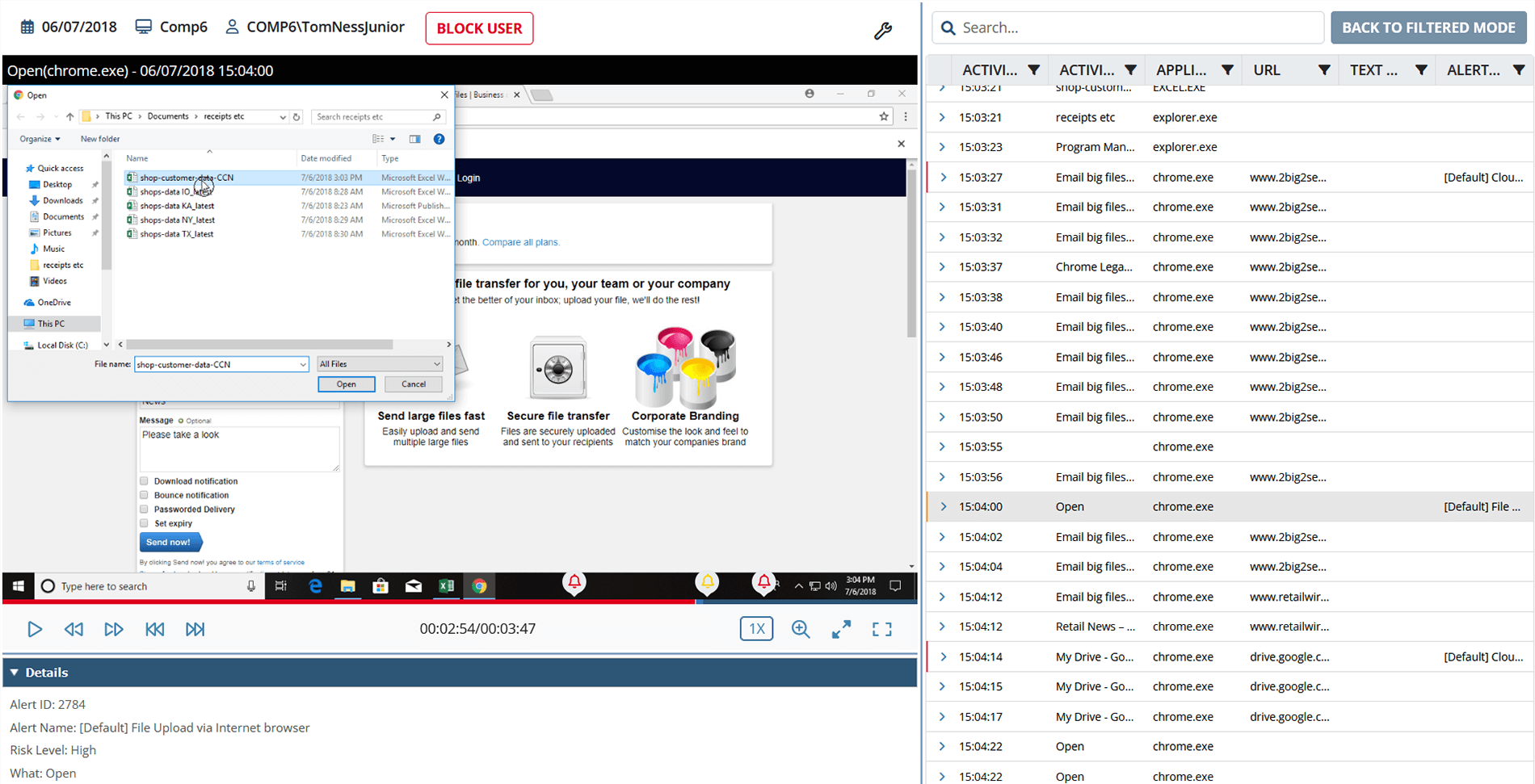
- Inform with a notification. After receiving a notification, your security officers can replay the user session to analyze the context and quickly respond if they identify a threat.
- Display a warning message to the user when they perform a specific action. You can choose to display the default message or create your own.
- Block the user. User blocking can stop critical events such as running of malicious scripts or sharing of sensitive data. You can block a user manually, or the system can automatically log the user out of their session and prevent them from logging back in.
- Block USB devices. When a user inserts a restricted USB device, Ekran System can block it and notify security officers about the event.
- Kill processes. The system can forcibly stop a detected application so it cannot be used for malicious activity.
Promptly detect signs of insider threats with UEBA
Ekran System’s AI-powered user and entity behavior analytics (UEBA) module detects unusual user behavior, such as logging into the system outside of work hours.
The system automatically analyzes users’ work patterns to create a baseline of user behavior. When a user’s work hours differ from the established pattern, the system notifies security officers of the anomaly.
After receiving an alert, your security officers can view user sessions with behavioral anomalies and ensure a quick response to suspicious user activity.
View security events in the way that works best for you
Ekran System offers a flexible alert viewing experience:
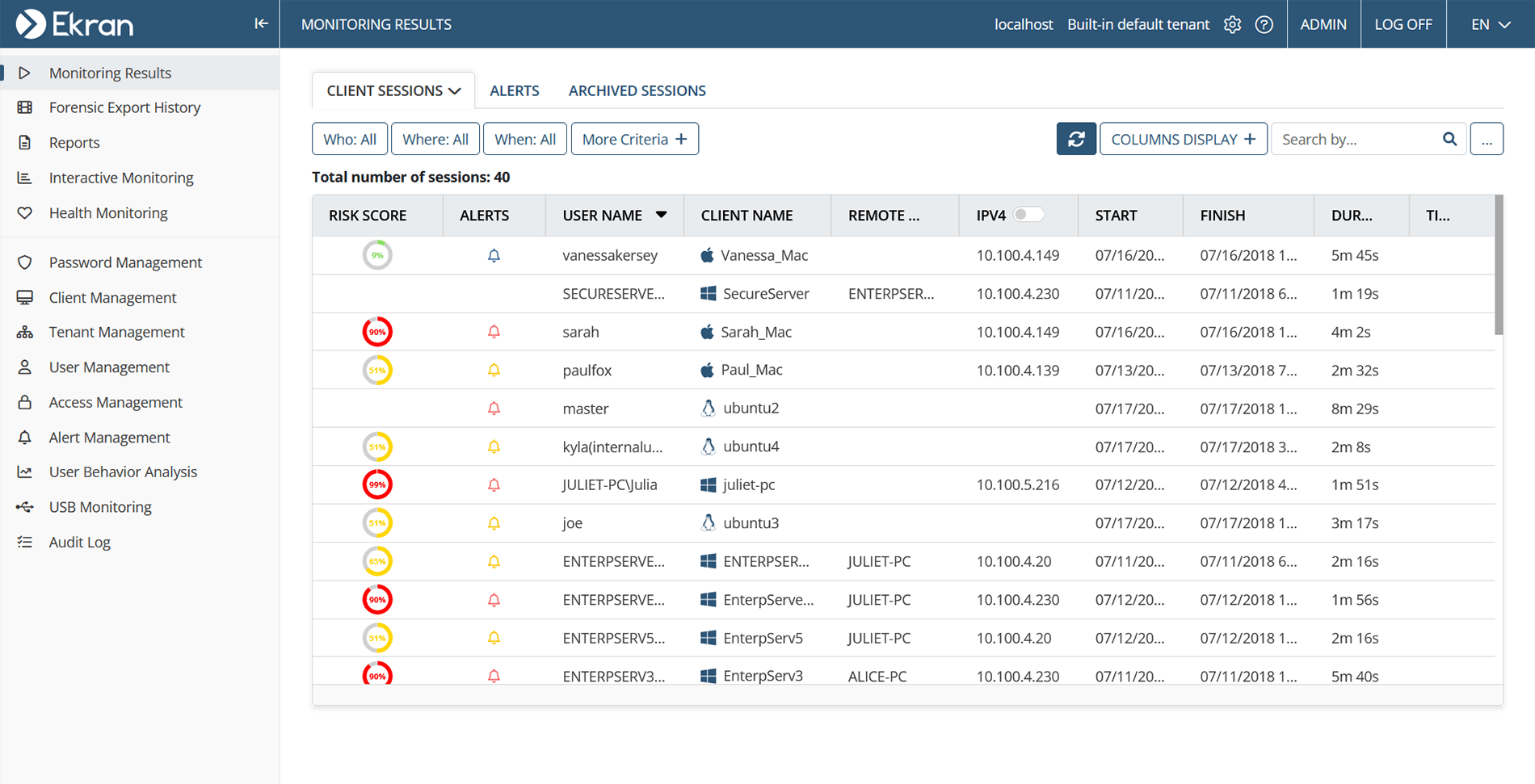
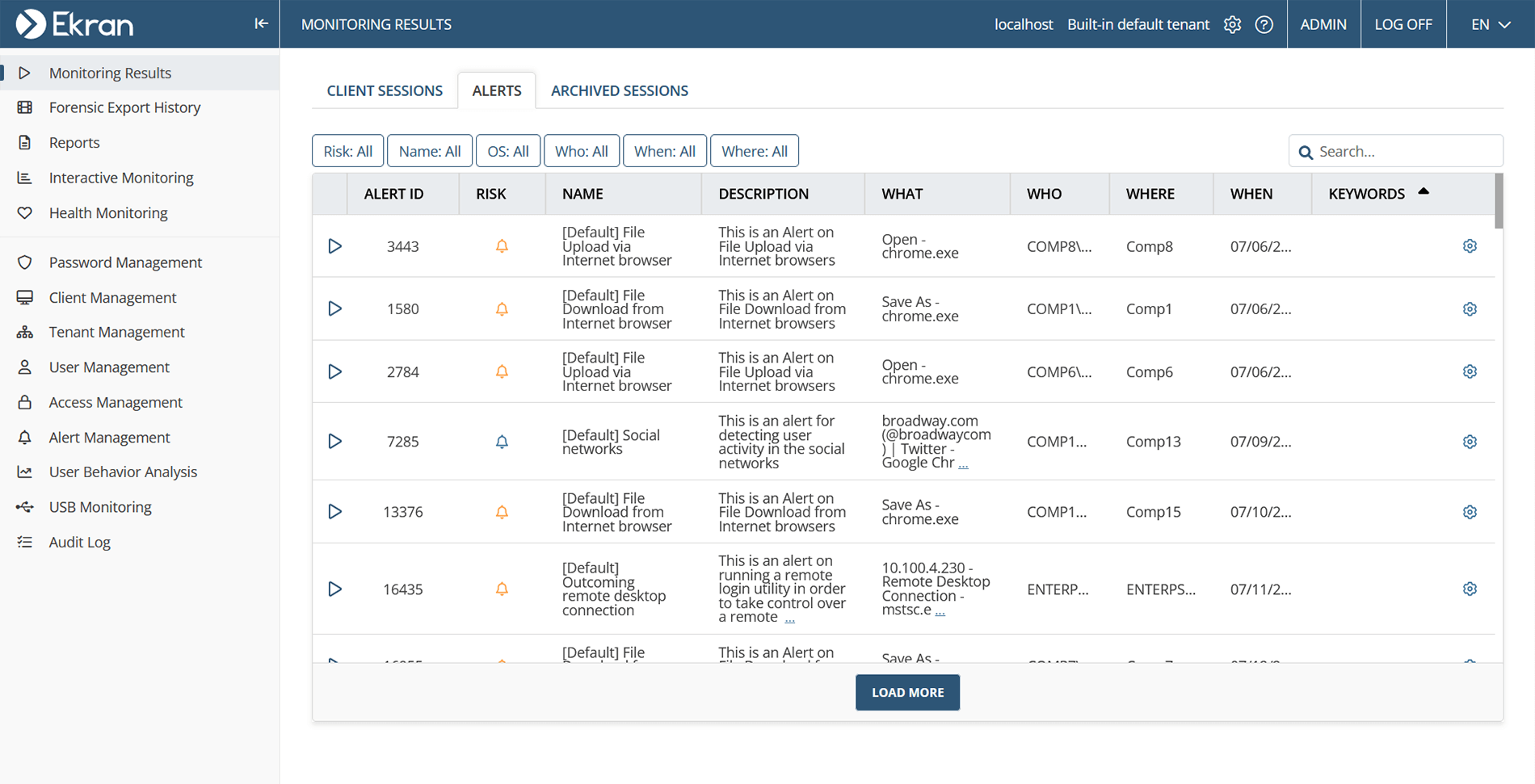
- Use the Alerts tab to view all alert events in your system. Filter records by risk levels, specific users, active applications, and other useful criteria.
- Generate informative alert reports containing details on all triggered user activity monitoring alerts for a specified period.
- Send your data to Microsoft Power BI and generate visualized reports on security alerts to identify signs of security violations quickly and conveniently.
- Easily view security events and alert risk levels in the Recent Alerts dashboard on the homepage of the Ekran System Management Tool.
Ekran System’s security incident management and notification system allows you to customize the way you analyze, audit, and cross-check your incident response actions.
Screenshots of user activity alerts in Ekran System
See how Ekran System can strengthen your incident response in practice
There are three common use cases for Ekran System’s alerting and incident response capabilities:
One of your privileged users with access to sensitive data uploads a file using a web browser.
A corresponding predefined alert is triggered.
The user sees a warning message, and security officers can review the event after receiving a notification.
An employee logs into the system outside working hours.
Ekran System’s UEBA module automatically detects a deviation from baseline user behavior.
Security specialists receive a notification and connect to the user’s live session to see what the user is doing.
A remote employee tries to install an unauthorized application on one of your office endpoints.
An associated default alert is triggered.
Ekran System blocks the user and logs them out of the session. Security officers later analyze the recorded session.
FAQ
Incident response is the process of identifying, containing, and resolving security incidents that may potentially harm your organization’s infrastructure, data, or operations.
A well-structured incident response process helps organizations minimize damage, reduce downtime, and quickly restore normal operations while preserving evidence for further investigation.
Effective incident response involves having an incident response plan and a dedicated security incident management and alerting system.
An incident response plan (IRP) is a set of predefined procedures and guidelines to follow when an organization experiences a security incident.
An IRP usually includes steps for identifying and containing the incident, assessing the damage, notifying relevant parties, and implementing measures to prevent future incidents. The plan may also outline roles and responsibilities of incident response team members.
An IRP can help your security officers stay focused and organized in the face of a real cybersecurity incident.
Real-time user activity alerts allow organizations to quickly detect and respond to security threats, such as insider attacks or data breaches, before they cause significant damage or losses.
Ekran System continuously monitors user activity in your organization and sends automated user activity alerts and notifications to your incident response team when it detects suspicious activity. This allows your security officers to act immediately and prevent an incident.
Ekran System user activity alerts and incident response functionality can also automatically block users and restricted USB devices. Moreover, Ekran System has all the tools required for efficient incident investigation.
Recommended resources
Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.