
Insider Threat Management Software: Detection, Prevention & Monitoring
Control access. Monitor insider activity. Respond to incidents. ALL-IN-ONE
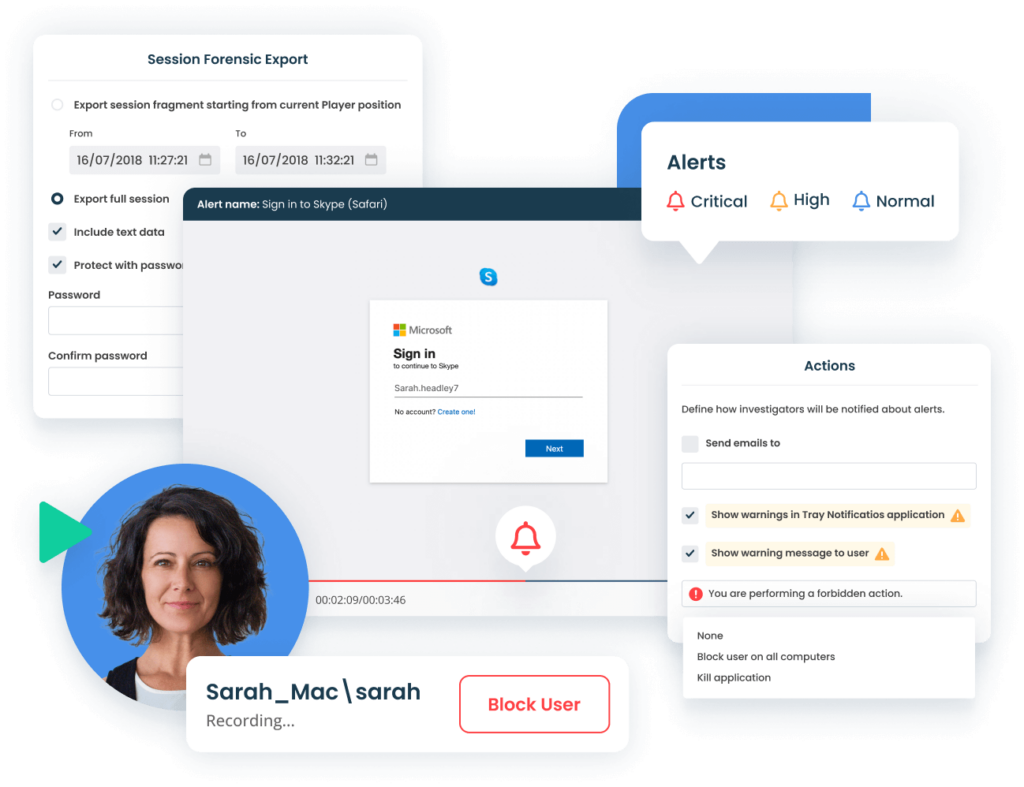
The сhallenges of insider risk
Insiders are employees, third-party contractors, and other business partners that have legitimate access to corporate data and infrastructure.
Insider threats can entail abuse of privileged access in order to steal, corrupt, or destroy valuable corporate or employee data. But security incidents can also be caused inadvertently by those with access to corporate assets. While data breaches are the most common security issue, critical configuration changes and misuse of corporate assets also should be covered by an insider security policy.
When developing an insider threat management program to mitigate and prevent insider threats, security officers must consider specific approaches and dedicated insider threat management tools. Detecting and investigating incidents caused by insiders is quite challenging for various reasons:
- Insiders have authorized access.
- One insider performs up to 10,000 operations per day, every day.
- Insiders know the ins and outs of the system.
- Insiders may collude and hide their tracks.
Recent industry research demonstrates the increasing importance of insider threat management, with security experts defining these attacks as the most silent and devastating. Building a robust insider threat prevention and detection program and investing in reliable insider threat detection solutions can provide your organization with an additional layer of protection, helping to prevent potential security incidents before they cause considerable harm.
See insider threat prevention in action
In this video, we examine a popular insider attack pattern, called a leapfrog attack, on corporate servers. Learn how you can use our insider threat prevention software to detect and stop it.
Prevent insider threats with Ekran System®
Ekran System is universal enterprise insider threat management software that meets the full spectrum of security needs on all kinds of infrastructure nodes, from desktops to jump servers.
The platform combines robust insider threat detection technology, including comprehensive activity monitoring and alerting functionality, advanced access management and identity control toolset, manual and automated incident response, and powerful reporting. This makes Ekran System a one-stop solution to implement your insider security policy.
Monitor and investigate activity
Ekran System is a comprehensive insider threat monitoring solution that provides all the necessary tools to log user activity, flag suspicious user behavior, and provide investigators with the information required to respond to security incidents.
As professional insider threat monitoring software, Ekran System monitors both generic and privileged user accounts, providing advanced protection techniques to guarantee that even privileged IT personnel can’t cover their tracks.
Session video recording
Ekran System allows you to record all user sessions on target endpoints. IP-based and username-based record filtering options are available.
The platform records user sessions in screen capture format indexed with multiple layers of text metadata, from application names to typed keystrokes and details of connected devices.
Depending on the type of endpoint, Ekran System clients may record one, several, or all concurrent user sessions.
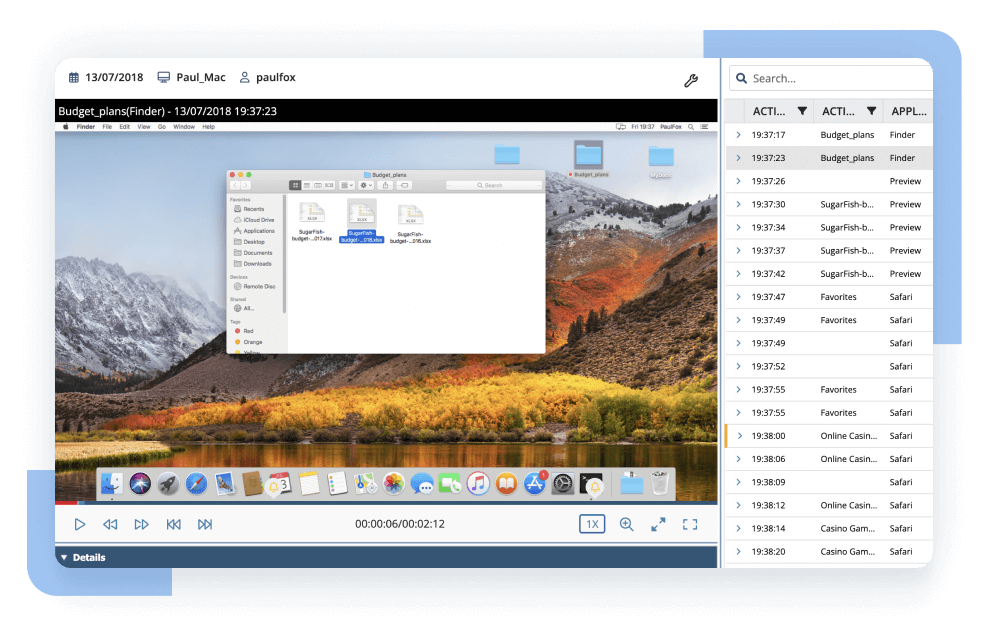
Key episode search
Besides providing comprehensive connection details – which are important when auditing remote sessions – Ekran System enables further session analysis. Investigators can search by various parameters (name of the active application, visited URL, command entered, or even text typed) within the current session and across all recorded sessions. Search even extends to the content of uploaded scripts.
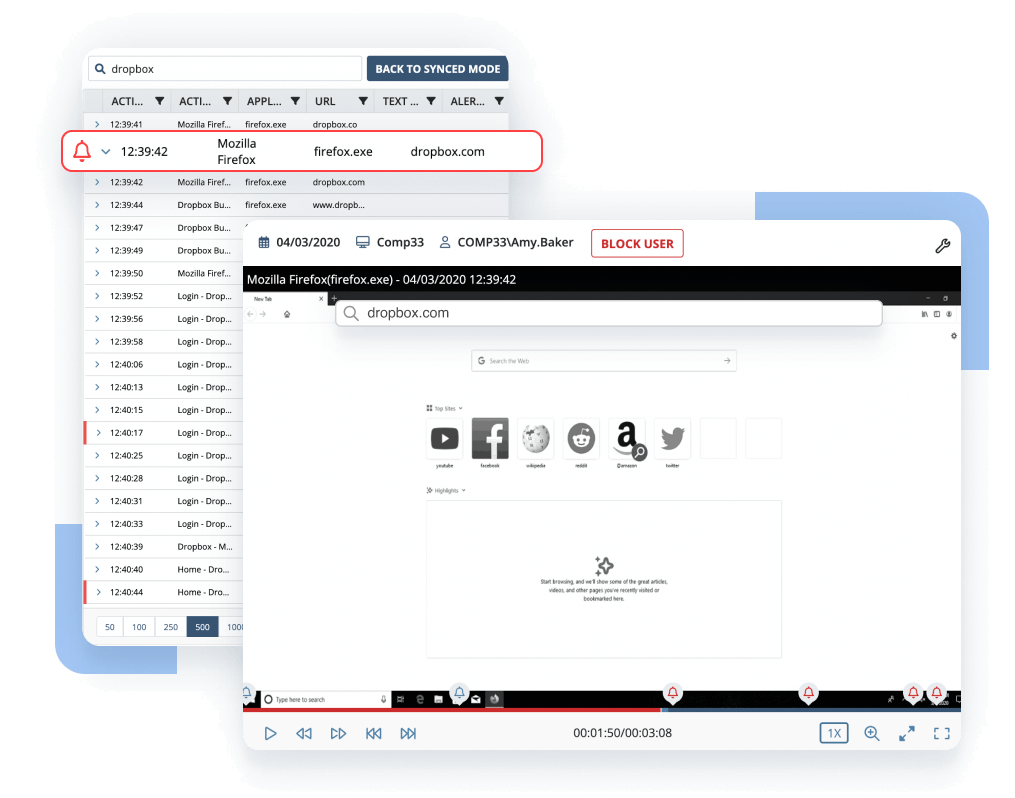
Client protection
To ensure continuous monitoring of any user with any permissions, Ekran System’s insider threat monitoring software includes a smart combination of watchdog and driver-level process protection mechanisms to prevent monitoring disruptions. Session recording continues locally even when the server connection is lost.
Monitor user activity with Ekran System®
Detect threats and respond in real time
Our insider threat detection solution provides highly configurable alerting tools that include both customizable rules based on generic behavioral indicators of potential insider threats and an AI-powered user behavior analytics module for detecting anomalies in the routines of internal users.
Predefined and custom alerts
Ekran System’s comprehensive insider threat detection solution includes a rule-based incident flagging functionality. Its collection of alert templates covers the most common insider threat indicators. At the same time, you can enhance the system with your own alert rules using a variety of activity parameters: process names, opened web addresses, connected USB devices, typed keystrokes, or executed Linux commands.
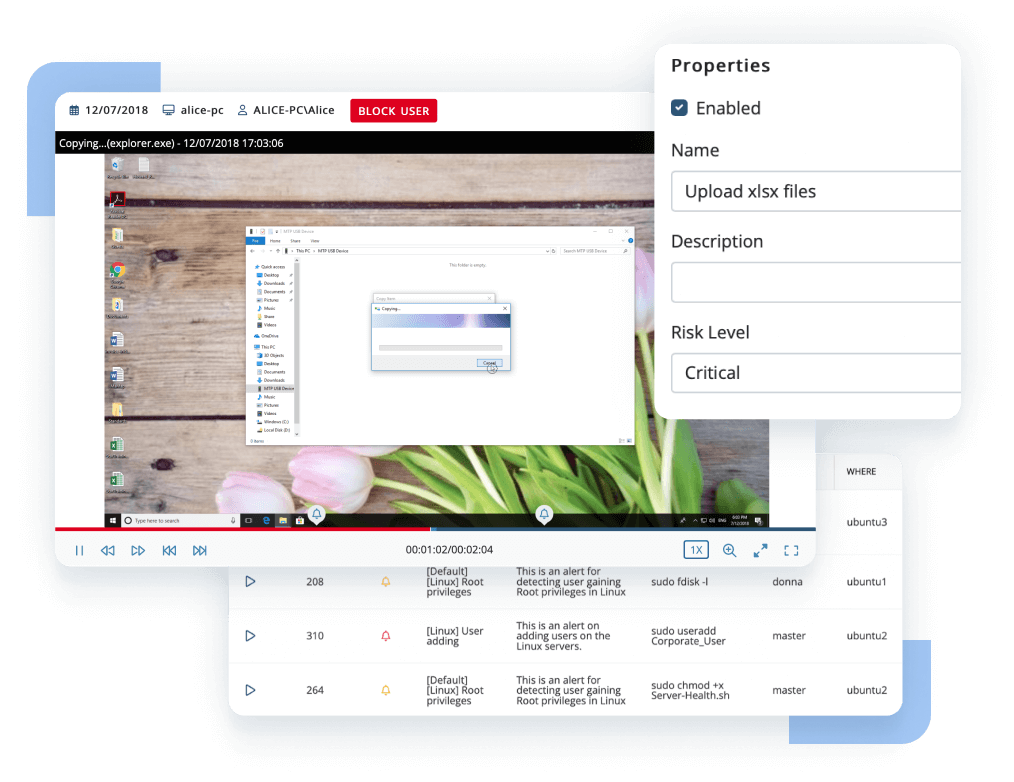
User and entity behavior analytics (UEBA)
Ekran’s alert system includes an artificial intelligence module that baselines user behavior against multiple factors to further detect abnormal user activity and possible account compromise.
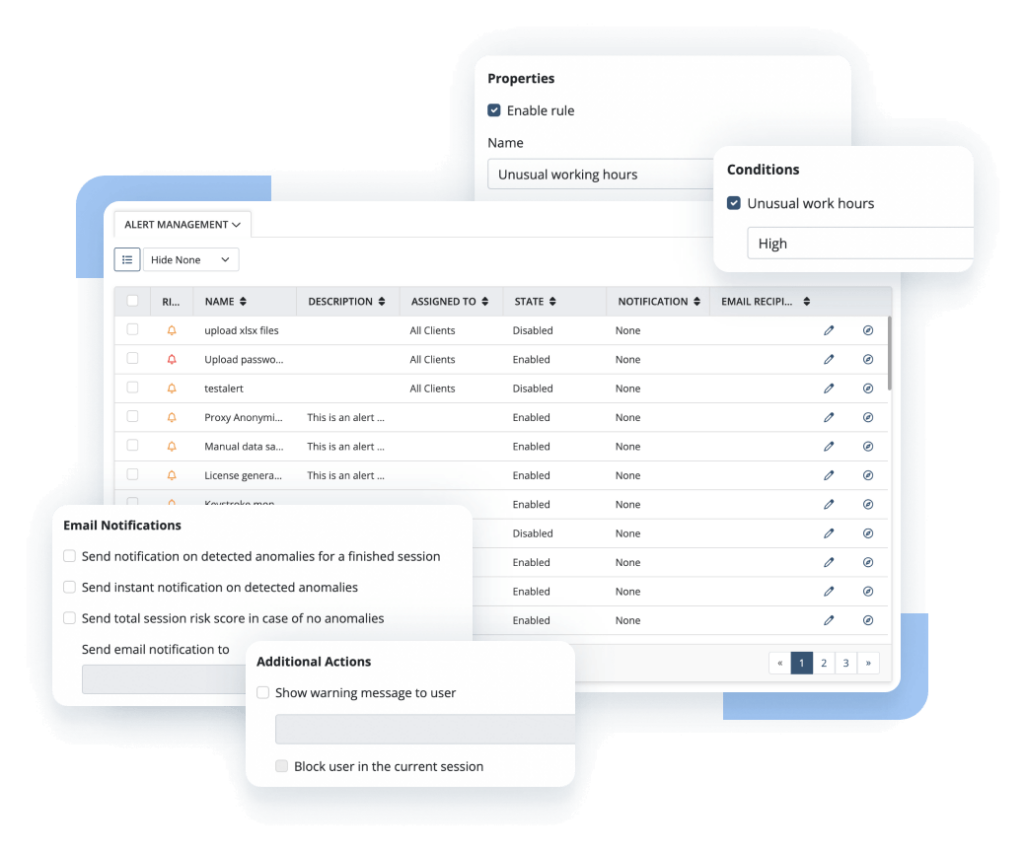
Automated incident response
To act on triggered alerts beyond merely notifying the security team, Ekran System provides options to set up automated incident response actions. These vary from warning messages obligating users to acknowledge their actions to application termination and user blocking.
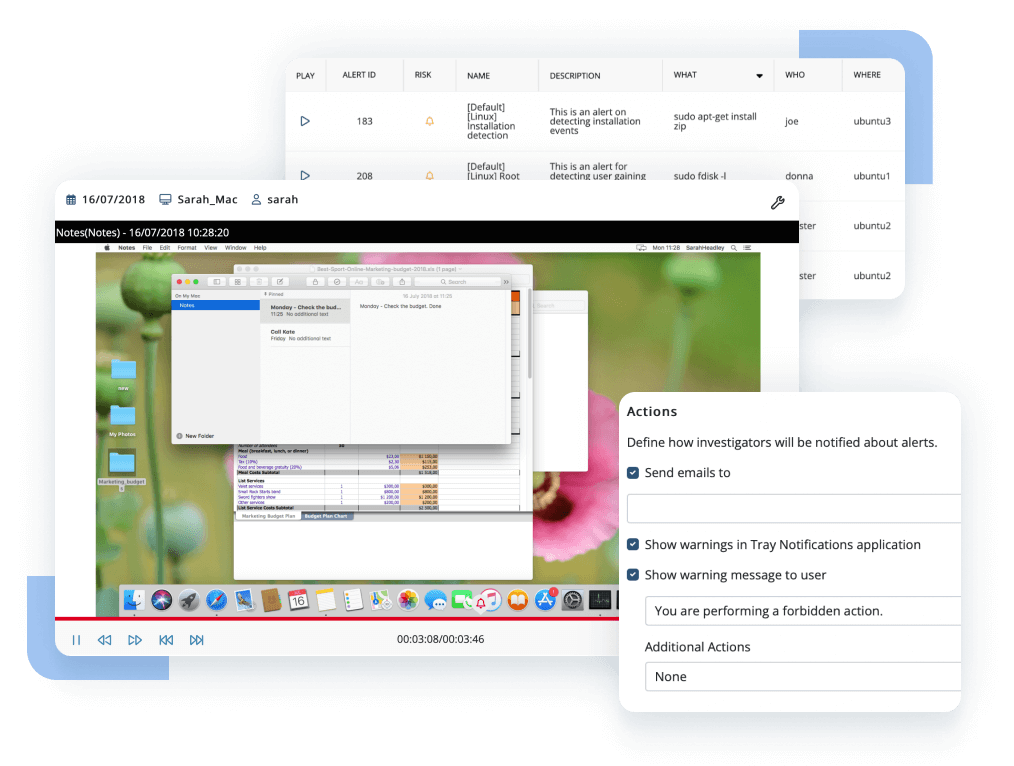
USB management
USB device control is a mandatory component for insider threat detection technology. The Ekran System platform detects, tracks, and may trigger alerts upon connecting various types of USB devices. It also delivers a toolset to block specific devices and device types that aren’t on the list of allowed USB devices and to apply manual approval for certain USB device usage scenarios.
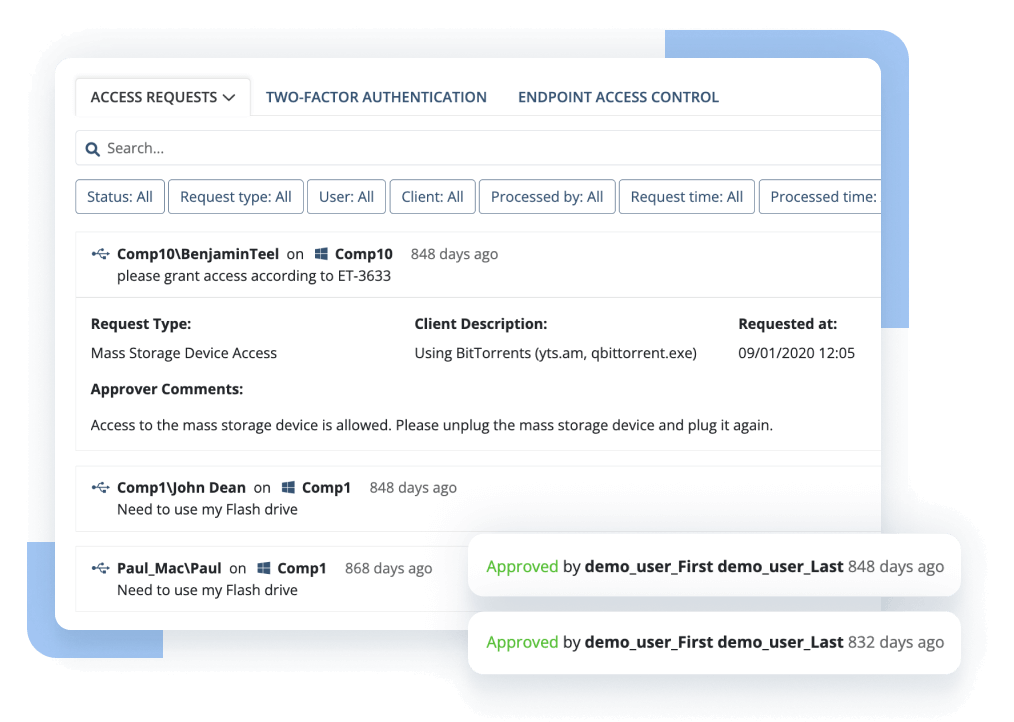
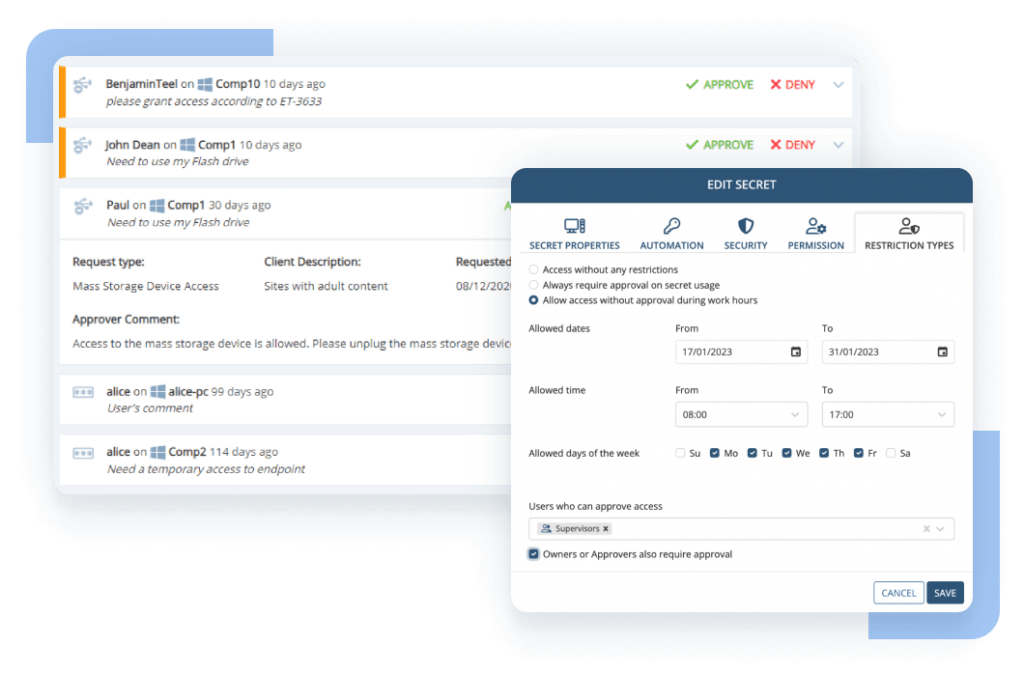
Control access to user accounts
Ekran System enables granular access management for both privileged and general user accounts. It includes complete privileged account and session management functionality, password management, and access request workflow support. Ekran can also integrate with your ticketing system to reinforce the purpose-based access principle.
To control user identity, it includes reliable and efficient two-factor authentication options.
Take advantage of other Ekran System’s insider threat detection and monitoring tools to:
Why companies choose Ekran System®
As an agent-based software platform, Ekran System offers clients for all popular operating systems and supports virtual environments as well as any network architecture. With Ekran System, you can combine agent-based and jump server deployment schemes.
Ekran System delivers user activity monitoring and incident detection together with identity and access management functionality via a single software agent installed on target endpoints. Forget about installing and configuring multiple modules, addons, and extensions. Ekran can entirely support your insider threat-related risk mitigation plan since it’s built in accordance with NIST 800-53 and most IT security standards.
Aimed at employee monitoring and corporate subcontractor control, Ekran System is built and tested to support tens of thousands of endpoints while maintaining exceptional stability and performance. With high availability and support for multi-tenant deployments, system resource and health monitoring dashboards, and maintenance routine automation, Ekran System scales easily and functions perfectly on big heterogeneous infrastructures.
The unique and transparent licensing offered by Ekran System allows for clear cost estimates and rapid time to value for deployments of any size, from small pilots to enterprise projects. Floating endpoint licensing enables license reassignment between endpoints in a couple of clicks. For virtual environments, the license provisioning process is automated to enhance your organization’s agility.
Get more with enterprise-grade insider threat detection software
Visually structured evidence trail resulting in low incident response time
Context-rich recordings significantly reduce CERT and SOC response times. One-click search across suspicious activity makes investigations faster and more effective.
AI-based compromised account detection
Cybercriminals are constantly improving their ways of compromising privileged accounts. Powered by artificial intelligence, the Ekran UEBA system can detect a hacker who has penetrated a corporate system using stolen credentials.
Lightweight software agent and highly optimized formats for storing data
The lightweight agent works silently and isn’t noticeable to users or other programs. Collected data is saved in searchable and highly optimized video, audio, and text file formats for compact log storage and easy reporting.
Active in your environment in 20 minutes or less
Ekran System is quick to install and easily integrates with SIEM and ticketing systems. You’ll get a ready-to-use solution right after a coffee break.
Ekran System integrations
Ekran System employee tracking software seamlessly integrates with your infrastructure, including with leading SIEM and ticketing systems.
Case studies
What our clients say about Ekran System’s insider threat prevention tools

FAQ
An insider threat is the potential for someone with authorized access to an organization’s critical assets to abuse that access and harm the organization.
The nature of an insider threat can be:
1. Malicious — harming your organization on purpose by exposing, stealing, or damaging your sensitive assets
2. Inadvertent — posing an unintentional threat due to human errors like neglecting security policies or opening phishing emails Since insiders have legitimate access to your infrastructure, they know where the most valuable data is stored and know your cybersecurity system from within. Insider activity is a common reason for data breaches.
The main goal of deploying insider threat protection solutions is to detect and address incidents caused by insiders as quickly as possible. By doing so, organizations can prevent data leaks or at least minimize the consequences of a security incident.
Ekran System incorporates an extensive set of insider threat detection and protection tools that can significantly enhance your cybersecurity program. Our platform provides you with helpful insights on the activity of regular employees, privileged users, and third parties. Being able to see who does what is essential for early detection of possible insider threats.
Yes. You can deploy Ekran System to manage insider risks posed by remote workers. In particular, you can use the platform’s functionality to
- Monitor remote employee activity in real time
- Review video and audio records of remote user sessions
- Verify the identities of remote users with multi-factor authentication
- Configure access rights for each user or group of users
- Manually approve access requests for the most critical assets
- Leverage instant alerts to detect suspicious events and respond to them manually or automatically
No. Ekran System doesn’t interrupt employees’ work while monitoring user activity.
The only scenario in which Ekran System can disturb a user’s work is when a user acts suspiciously. For instance, you can configure insider attack prevention rules so that users receive notifications explaining that particular actions violate cybersecurity policies. Also, your security team can manually block suspicious sessions, users, and actions after receiving notifications from Ekran System, or you can automate this process for securing the most critical assets.
Ekran System is available for a number of operating systems and platforms:
- Windows
- Linux/Unix
- macOS
- X Window System Monitoring
- VDI platforms: Citrix, VMware Horizon, Hyper-V, Microsoft Azure Windows Virtual Desktop (WVD), Amazon Workspaces, and more
Yes. Ekran System monitors the activity of admins and other privileged users. Our insider threat detection tool can also help you with privileged access management, account and session management, auditing the activity of privileged users, and responding in real time to suspicious activity of privileged users.
As a user activity monitoring and insider risk prevention solution, Ekran System is designed with cybersecurity requirements in mind. Our platform offers various features that help businesses meet key IT cybersecurity laws, regulations, and standards, including the GDPR, HIPAA, PCI DSS, ISO 27001, NIST SP 800-53 and SP 800-171, SWIFT CPS, and FISMA.
Yes. You can integrate Ekran System with:
- SIEM systems: Splunk, ArcSight, and QRadar
- Ticketing systems: SysAid, ServiceNow, API Bridge
- Active Directory
Ekran System is available for both on-premises and cloud deployments, including in hybrid environments.
If you’d like to prevent insider risks in the cloud, Ekran System can help you do that efficiently. With our platform, you can monitor any number of endpoints and adjust which endpoints are monitored as needed. Ekran System also offers automatic client updates and monitoring data backups so you can always use the latest version of the platform and protect your data from accidental loss.
There is no one-size-fits-all answer to this question. What insider threat detection tools are “the best” for you depends on a variety of factors, including the specific needs and requirements of your organization. However, here are some tools that your insider threat detection software should provide:
- Comprehensive coverage: The solution should have tools to detect a wide range of malicious activity, such as data exfiltration, privilege abuse, unauthorized access, and more.
- User and entity behavior analytics (UEBA) [PDF]: Pay attention to solutions with AI-based tools that can analyze user behavior. Ekran System provides an artificial intelligence module that detects suspicious activity before a cybersecurity incident happens.
- Real-time alerts and automatic incident response: The solution of your choice should provide real-time alerts when suspicious activity is detected. Ekran System has both pre-installed and custom alerts, as well as functionality to automatically respond to insider threats by blocking user accounts or killing applications (processes) related to suspicious activity.
- Audit and reporting: Auditing and reporting capabilities can help your security team investigate incidents and generate compliance reports. Ekran System offers a wide variety of reports to enable your security officers to see a complete picture of your organization’s cybersecurity landscape at a glance.
Deploying Ekran System for detecting insider threats is a straightforward and fast process. If you have any troubles, questions, or suggestions, our technical support team is always available to help.
If you want to check out how our insider threat protection solution works before you commit, you can request a free 30-day trial or an online demo version.
When you’re ready to deploy a full version of the Ekran System platform, check out the available licensing schemes to choose the edition that best meets your needs.
To get a cost estimate for deploying Ekran System in your infrastructure and according to your specific requirements, please get in touch with us using this form.
Blog spotlight
Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.

















