Cybersecurity Solutions for Education
Protect sensitive data, manage insider risks, and meet cybersecurity requirements
with a full-cycle insider risk management platform.
The challenge
2,297 attacks
against educational institutions are reported weekly.
According to the Cyber Attack Trends: 2022 Mid-Year Report by Check Point.
$3.65 million
is the average cost of a data breach in education.
According to the Cost of a Data Breach Report 2023 by IBM Security.
Educational institutions now increasingly rely on digital platforms to store and manage students’ and employees’ personal information, faculty records, financial details, and research data. That’s why they’ve become vulnerable to cyberattacks and insider threats, which emphasizes the importance of deploying reliable protection.
Malicious actors target both private educational institutions and public educational institutions due to the huge amount of sensitive data in the network that can be used for financial gain, espionage, convenience, or even just for fun.
The education sector faces many challenges in protecting sensitive information:
Preventing data leaks and intellectual property theft
Securing cloud and on-premises assets from privilege misuse
Improving network visibility
Building an effective incident response plan
Managing third-party cybersecurity risks
Complying with privacy laws and cybersecurity requirements
Deploying cybersecurity solutions for education is crucial for preventing privacy breaches and maintaining the trust of your students, parents, and stakeholders
Ekran System enables educational institutions to


Enhance network visibility
Prevent insider threats — gain full visibility into user actions.
Manage user access
Ensure secure, granular access to your critical resources.
Prevent the loss of sensitive data
Detect and promptly respond to data security violations.
Comply with cybersecurity requirements
Ensure data privacy under FERPA, HIPAA, PCI DSS, and other laws and standards.
Human-centric security software for educational organizations
Schools and community colleges
Higher education institutions
Education ministries and departments
Online academies
Establish education network security and efficient insider risk management across all platforms in your environment.
Track user interactions with sensitive personal data and intellectual property.
Minimize the attack surface by limiting access to critical systems for students, staff, and third-party service providers.
Prevent insider threats by promptly detecting and responding to suspicious activity within your network.
Meet compliance requirements to enhance your cybersecurity posture and foster trust among students, partners, and stakeholders.
Whether you’re looking for effective school cybersecurity solutions, higher education cybersecurity solutions, or education cybersecurity solutions for online academies, ministries, and departments, Ekran System has you covered.
Industry recognition
Create an effective insider threat program


CISO’s Practical Guide & Set of Worksheets for Building Insider Threat Program
Learn how to create a comprehensive insider threat program and use the included worksheets to measure its effectiveness.
Download White PaperHow Ekran System helps enhance cybersecurity in educational institutions
Get a clear view of how your students, employees, and stakeholders interact with your sensitive assets. Monitor user activity in real-time or review recorded user sessions in a screen capture format backed with detailed metadata.


Grant, broaden, and terminate access to your sensitive resources. Approve access requests and allow temporary access to your critical data only when users need it to perform specific tasks.
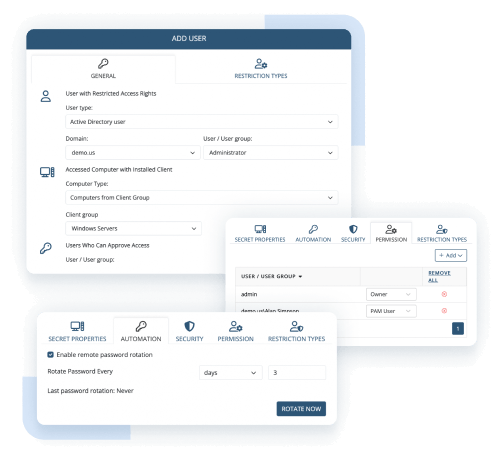


Verify users’ identities with two-factor authentication (2FA) before providing them with access, and distinguish user actions in shared accounts with secondary authentication.
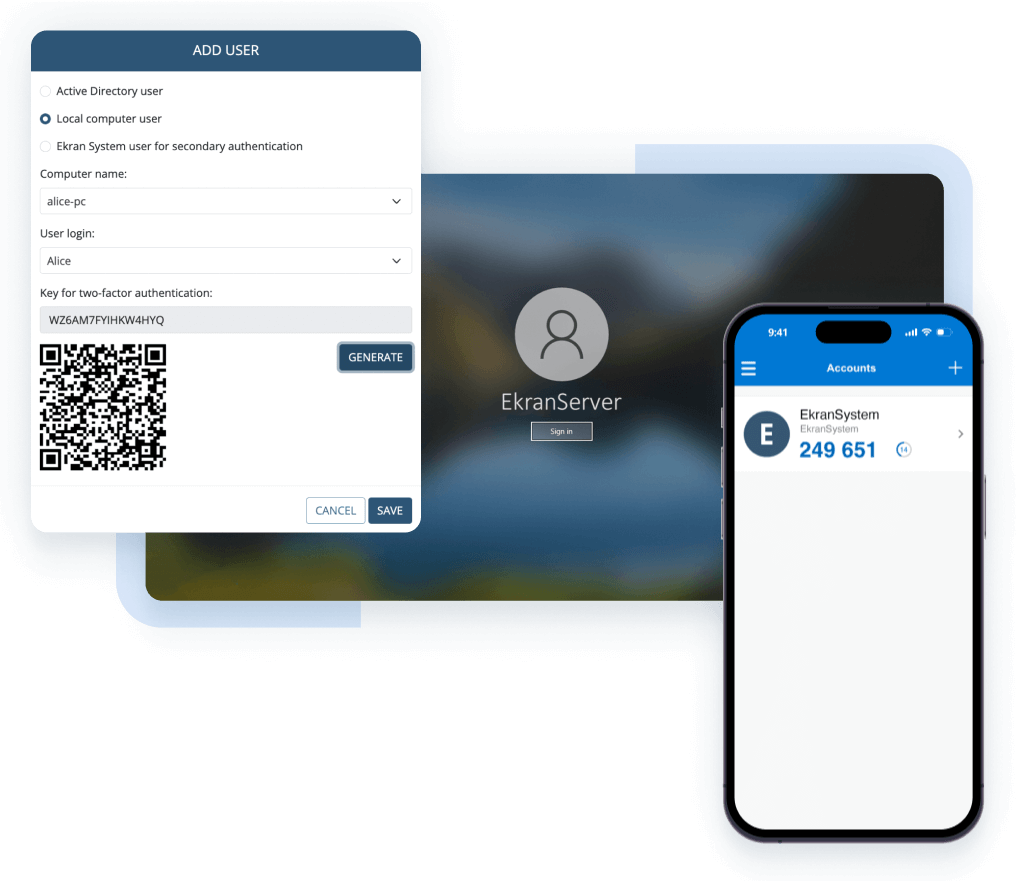

Ensure secure access to your organization’s endpoints for remote students, third-party service providers, and other external users. Monitor how they handle your sensitive data and put a stop to any suspicious activity.



Receive real-time alerts for risky user behavior and security policy violations. Swiftly respond to threats manually or automatically: display a warning message, block the user, and kill the process.
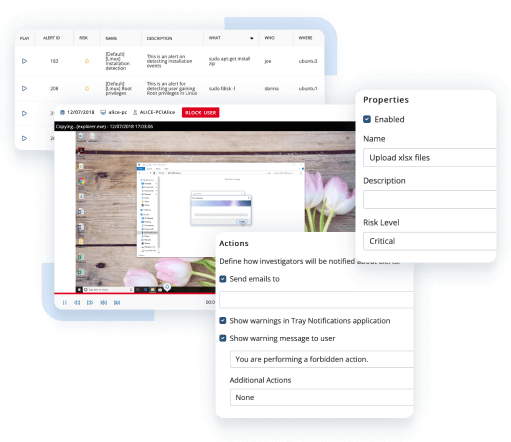

Receive real-time alerts for risky user behavior and security policy violations. Swiftly respond to threats manually or automatically: display a warning message, block the user, and kill the process.
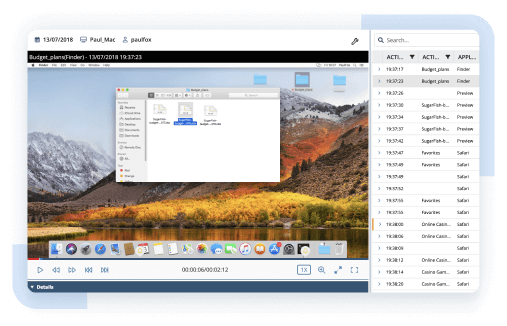

Anonymize monitored data to protect your users’ personally identifiable information and comply with data privacy standards, laws, and regulations. If you need to inspect security incidents, you can de-anonymize the data required for investigation.


Get more with enterprise-grade insider threat detection software
Visually structured evidence trail resulting in low incident response time
Context-rich recordings significantly reduce CERT and SOC response times. One-click search across suspicious activity makes investigations faster and more effective.
AI-based compromised account detection
Cybercriminals are constantly improving their ways of compromising privileged accounts. Powered by artificial intelligence, the Ekran UEBA system can detect a hacker who has penetrated a corporate system using stolen credentials.
Lightweight software agent and highly optimized formats for storing data
The lightweight agent works silently and isn’t noticeable to users or other programs. Collected data is saved in searchable and highly optimized video, audio, and text file formats for compact log storage and easy reporting.
Active in your environment in 20 minutes or less
Ekran System is quick to install and easily integrates with SIEM and ticketing systems. You’ll get a ready-to-use solution right after a coffee break.
Why companies choose Ekran System®
Ekran System continuously monitors various endpoints, including both end-user machines and servers, within any network architecture. Being one of the best user activity monitoring tools for Windows, Ekran also works for macOS and is a powerful Linux/UNIX session audit tool. It even supports X Window and all popular virtualization solutions. Ekran allows agent-based and jump server-based deployments as well as any combination thereof.
Designed for tracking user activity on tens of thousands of endpoints, Ekran System demonstrates exceptional stability and performance. As for maintenance and reliability, the platform provides high availability and multi-tenant deployment, system resource and health monitoring dashboards, and automated maintenance tasks.
Besides tracking user activity, Ekran System provides enhanced incident alerting and response functionality. But that’s not all. Using Ekran System Client, you can set up access and identity management. Since Ekran System also provides server user activity monitoring, you always know what is happening in your network.
The unique licensing offered by Ekran System enables cost-effective deployments of any size, from small pilots to enterprise projects. Floating endpoint licensing enables license reassignment in a couple of clicks. For virtual environments, this process is automated.
Recommended resources
Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.






