Insider Threat Prevention for Energy and Utility Companies
Ensure operational resilience, prevent espionage, and meet cybersecurity
requirements with a full-cycle insider risk management platform.
The challenge
With complex supply chains and heavy reliance on information and operational technology, energy and utility companies face many challenges when trying to minimize security risks:
Preventing misuse and abuse of user privileges
Complying with relevant cybersecurity requirements
Protecting sensitive data and systems from cyberattacks and insider threats
Ensuring the security of the IoT ecosystem and supply chain
Responding swiftly to cybersecurity threats
Mitigating vulnerabilities in legacy systems
The importance of cybersecurity for energy and utility companies
The energy and utilities industry is an attractive target for both external and internal attacks. According to the Cost of a Data Breach Report 2023 by IBM Security, the energy industry ranks fourth-highest in average data breach costs at $4.78 million.
Without proper energy and utilities cybersecurity solutions, organizations throughout the industry may face severe consequences, such as:
Operational disruptions
Financial losses
Reputational damage
Non-compliance liabilities
Ekran System helps energy and utility companies to


Manage privileged and third-party access
Grant access to critical endpoints only for employees and third parties who need it to do their jobs.
Improve visibility across digital infrastructures
Continuously monitor and record how users handle critical data and systems within your IT environment.
Prevent sensitive data
theft
Implement in-depth insider risk management to protect your intellectual property from espionage and minimize the risk of operational sabotage.
Comply with cybersecurity regulations
Streamline compliance with industry-specific cybersecurity requirements, including those stipulated by NERC and FERC.
Common vectors of insider threats in
the energy and utilities sector
Nation-states engaging in espionage
Disgruntled employees damaging IT infrastructure, data, or equipment as retaliation
Malicious insiders committing fraud or data theft for financial gain
Negligent employees causing security breaches
Adversaries harming organizations by compromising their vendors’ security systems
Cybercriminals exploiting employees’ lack of cyber awareness
Protect your critical operations from insider threats
Ekran System’s comprehensive cybersecurity capabilities can help energy companies protect their most valuable assets and combat insider threats.
Privileged accounts and user credentials
Critical systems and workstations
Intellectual property and mission-critical data
Cloud infrastructure
Personal information and financial data
Account compromise
Human errors
Malicious insider activity
Espionage
Privilege abuse


The ultimate cybersecurity solution for energy companies
Oil, gas, and coal extraction companies
Power production companies
Energy retailers
Equipment and service providers
See how users interact with sensitive data and critical systems within your IT environment.
Restrict employee and vendor access to critical assets to minimize security risks.
Detect suspicious insider activity and respond to it in real time.
Fulfill relevant compliance requirements and enhance your overall cybersecurity.
Industry recognition
Expert advice on building an impactful insider threat program


A Modern CISO’s Guide to Running a Successful Insider Threat Program
Get in-depth instructions on how to build a strong and actionable insider risk management program. Find ready-to-use worksheets and learn how to measure your program’s effectiveness.
Download White PaperHow Ekran System enhances cybersecurity for energy and utilities
Gain visibility into your IT infrastructure through continuous monitoring of employee and vendor activity, enhanced with screen-capture recordings and indexed metadata.


Validate users’ identities before giving them access to your endpoints, securely manage passwords, and distinguish between users of shared accounts.
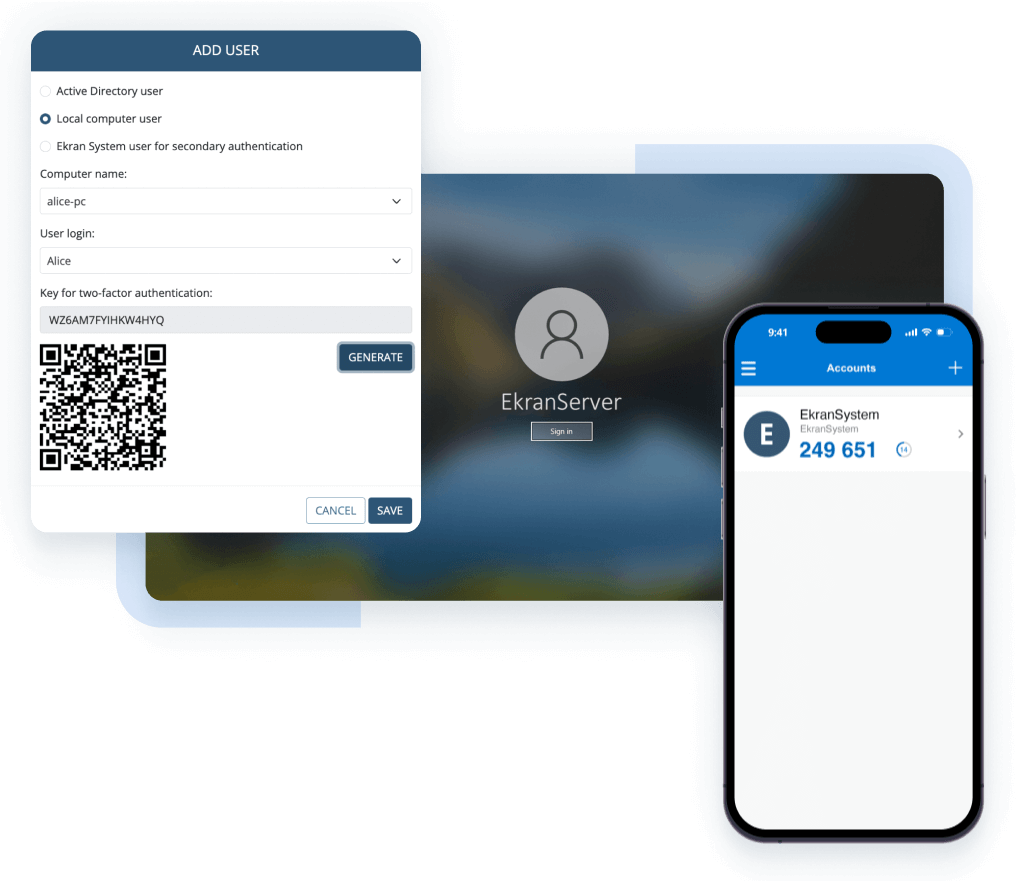

Secure privileged access by limiting user permissions to only those necessary for employees to do their jobs. Leverage manual access approval workflow to protect your most valuable endpoints.
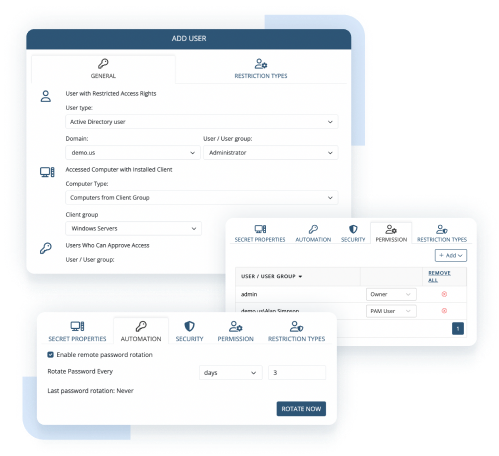

Mitigate security risks and ensure data and infrastructure integrity by providing third-party vendors with temporary access to your IT environment and monitoring the activity of all remotely connected users.
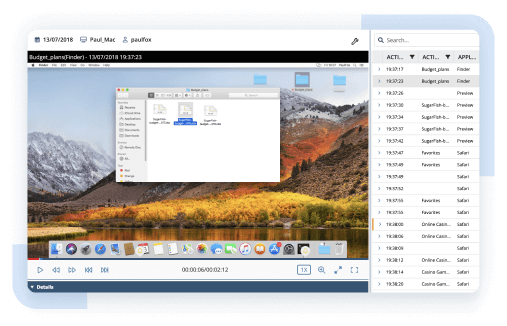

Promptly respond to suspicious user activity by activating predefined or custom alerts. Implement rules to automatically block malicious actions.
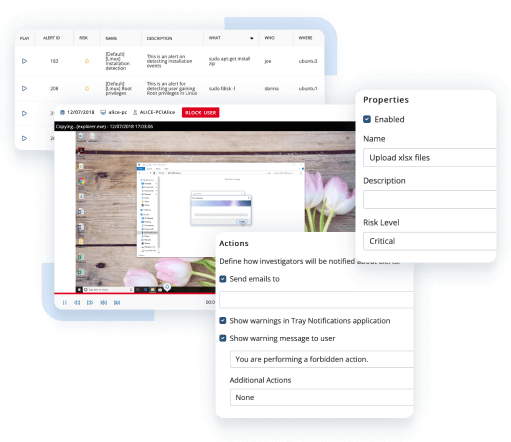

Evaluate your current insider risk landscape through a variety of reports and seamless integration with Microsoft Power BI. Export tamper-proof evidence of malicious user activity for forensic audits and investigations.

Protect sensitive user data from disclosure with pseudonymization of personal information in the monitoring results. For investigation purposes, you can easily de-anonymize the needed data.


Get more with enterprise-grade insider threat detection software
Visually structured evidence trail resulting in low incident response time
Context-rich recordings significantly reduce CERT and SOC response times. One-click search across suspicious activity makes investigations faster and more effective.
AI-based compromised account detection
Cybercriminals are constantly improving their ways of compromising privileged accounts. Powered by artificial intelligence, the Ekran UEBA module can detect a hacker who has penetrated a corporate system using stolen credentials.
Lightweight software agent and highly optimized formats for storing data
The lightweight agent works silently and isn’t noticeable to users or other programs. Collected data is saved in searchable and highly optimized video, audio, and text file formats for compact log storage and easy reporting.
Active in your environment in 20 minutes or less
Ekran System is quick to install and easily integrates with SIEM and ticketing systems. You’ll get a ready-to-use solution right after a coffee break.
Why companies choose Ekran System®
Ekran System continuously monitors various endpoints, including both end-user machines and servers, within any network architecture. Being one of the best user activity monitoring tools for Windows, Ekran System also works for macOS and is a powerful Linux/UNIX session audit tool. It even supports X Window System and all popular virtualization solutions. Ekran System allows agent-based and jump server-based deployments as well as any combination thereof.
Designed for tracking user activity on tens of thousands of endpoints, Ekran System demonstrates exceptional stability and performance. As for maintenance and reliability, the platform provides high availability and multi-tenant deployment, system resource and health monitoring dashboards, and automated maintenance tasks.
Besides tracking user activity, Ekran System provides enhanced incident alerting and response functionality. But that’s not all. Using Ekran System Client, you can set up access and identity management. Since Ekran System also provides server user activity monitoring, you always know what is happening in your network.
The unique licensing offered by Ekran System enables cost-effective deployments of any size, from small pilots to enterprise projects. Floating endpoint licensing enables license reassignment in a couple of clicks. For virtual environments, this process is automated.
Meet IT security requirements with Ekran System’s cybersecurity solutions for insurance companies
ISO 27001
Global information security management standard
PCI DSS
Worldwide financial security standard
SWIFT CSP
Cybersecurity for financial institutions
SOX
Cybersecurity for financial institutions
FISMA
U.S. law safeguarding government data
GDPR
EU data privacy regulation
NIST 800-53
U.S. government cybersecurity framework
NIST 800-171
Cybersecurity standard for U.S. contractors
NERC
Standards for North American power systems
GLBA
U.S. law on financial data protection
NISPOM Change 2 and H.R. 666
Protecting classified information in the U.S.
SOC 2
Audit standard for data security
HIPAA
U.S. law protecting medical data privacy
DORA
Enhancing software development practices
NIS2
EU law for critical infrastructure cybersecurity
Recommended resources
FAQ
Cyberattacks and data breaches may lead to financial losses, reputational losses, non-compliance fees, and operational disruptions. These negative consequences may disrupt the transfer of power or fuel supplies to the population, jeopardizing the public’s welfare.
The energy sector mainly faces the following cybersecurity threats:
- Ransomware attacks
- Nation-state espionage
- Social engineering
- Insider threats
- Advanced persistent threat attacks.
Ekran System is a full-cycle insider risk management platform that helps enhance cybersecurity for energy and utilities and protect their critical data and assets from human-induced cyber threats.
Since energy firms must maintain their operations, cyberattackers assume that these companies are more likely to pay ransoms. Moreover, state-sponsored cyber threat actors may use cyberattacks within the energy and utilities sector as a means to escalate political tensions and exert strategic influence.
Because of its critical infrastructure status, the energy and utilities sector faces unique cybersecurity challenges. Energy and utility companies must ensure the security of their complex supply chains, address security vulnerabilities in legacy systems, and enhance operational resilience.
Tailored cybersecurity software for energy companies is required to address these challenges. Ekran System is a comprehensive insider risk management solution that helps energy and utility companies minimize security risks.
Ready to strengthen your defenses with Ekran System?
Consult our experts on the most efficient insider risk management approach to meet your organization’s cybersecurity needs.






