Insider Threat Prevention for Insurance Companies
Monitor user activity, manage access, and streamline incident response in your
insurance organization with a full-cycle insider risk management platform.
The challenge
Company insiders are behind 34% of data breaches in the financial and insurance industries, states Verizon’s 2023 Data Breach Investigations Report. The behavior of your employees can also contribute to external attacks such as phishing and credential theft. Consequently, insurers are looking for cybersecurity services for insurance companies to manage insider risks and address the following challenges:
Seсuring sensitive customer data from cyberattacks
Preventing cases of fraud and privilege abuse
Overcoming vulnerabilities of legacy systems in the insurance sector
Increasing visibility into the organization’s network and user activity
Managing security risks from partners and other external users
Complying with data privacy regulations and cybersecurity requirements
Ekran System helps insurance companies to


Improve visibility across IT systems
Monitor employee activity and manage the use of USB devices in your organization’s IT infrastructure.
Manage privileged and third-party access
Ensure granular and secure access provisioning for your privileged users and third-party service providers.
Prevent sensitive data
theft
Oversee interactions with your organization’s sensitive assets and promptly respond to data security violations.
Meet data protection requirements
Implement measures required by the GDPR, GLBA, and other data protection standards, laws, and regulations.
Protect your insurance assets from cyber threats
When choosing data security solutions for insurance providers, it is vital to know what needs to be protected and from what threats. With Ekran System, you can monitor and manage access to your most sensitive assets, thereby protecting them from the common threats in the insurance industry:
Personal customer data
Health information
Financial data
Privileged accounts
Cloud IT infrastructures
Insider threats
Human errors
Account compromise
Third-party exploits
Social engineering attacks


A holistic cybersecurity solution for the insurance industry
Property and casualty insurers
Life insurance companies
Health insurers
Cyber insurance organizations
See how your employees process personally identifiable information and financial data.
Limit employee and third-party vendor access to critical assets to reduce the attack surface.
Detect and contain malicious insider activity and other human-related cybersecurity threats.
Minimize cyber risks by ensuring compliance with security requirements.
Industry recognition
Structure your journey to an insider threat program


A Modern CISO’s Guide to Running a Successful Insider Threat Program
Get detailed guidance on how to build an effective insider risk management program and measure its effectiveness, with ready-to-use worksheets.
Download White PaperHow Ekran System enhances cybersecurity for insurance companies
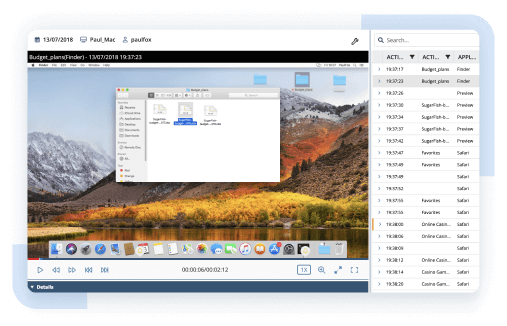
Enable your security officers to track employees’ actions in real time and record user sessions for post-analysis. Recordings contain screenshots of user activity and extensive metadata, including visited URLs, launched applications, and typed keystrokes.


Securely authenticate users to prevent unauthorized access to sensitive data. Employ Ekran System’s two-factor authentication (2FA) and secondary authentication capabilities to verify user identities and distinguish users of shared accounts.
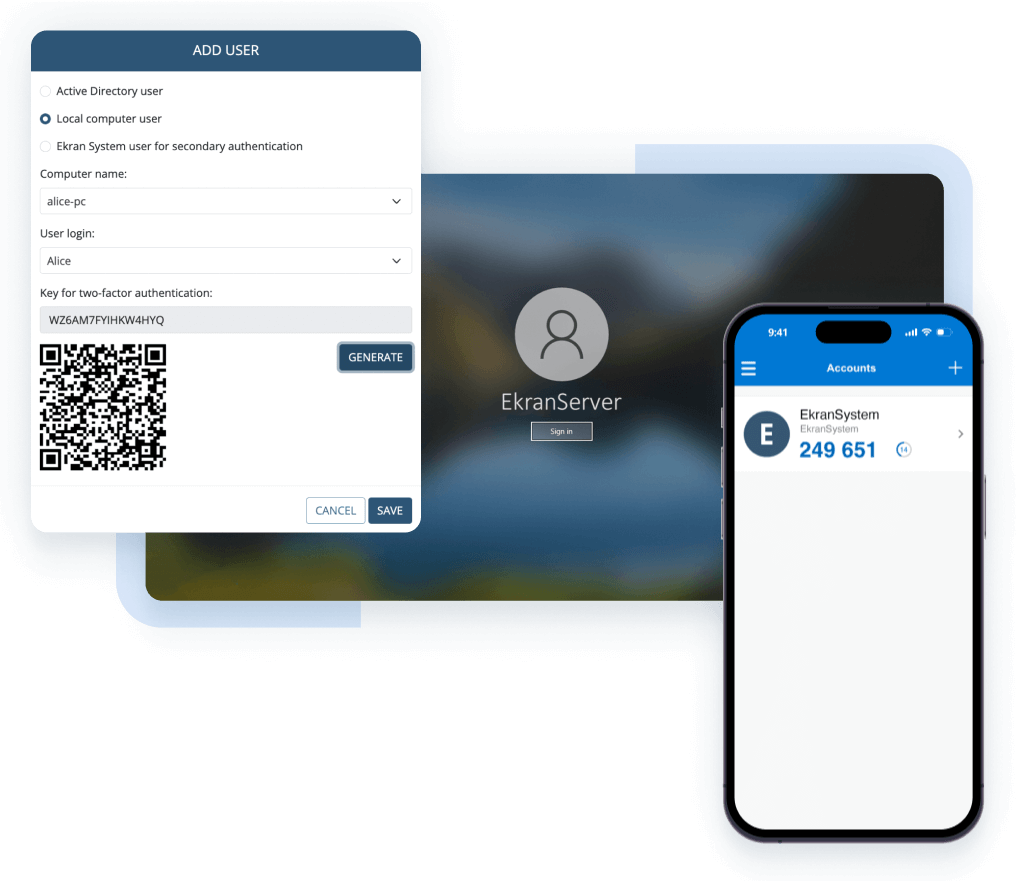

Granularly control access to critical endpoints for your privileged and regular users. Configure an access and approval workflow, set time-based access restrictions, and provide one-time passwords for external users.
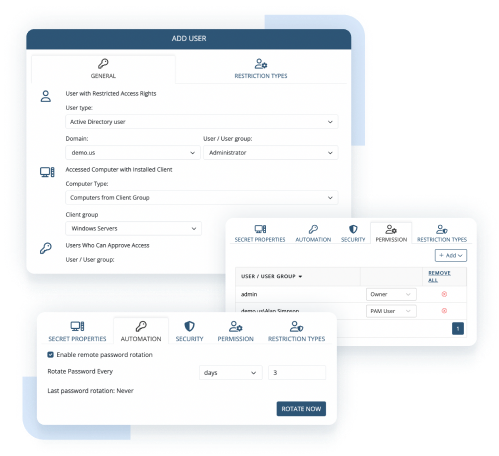

Manage risks from users outside your network. Provide your partners, vendors, and third-party service providers with securely limited access to sensitive assets and monitor the activity of remote users in your IT infrastructure.

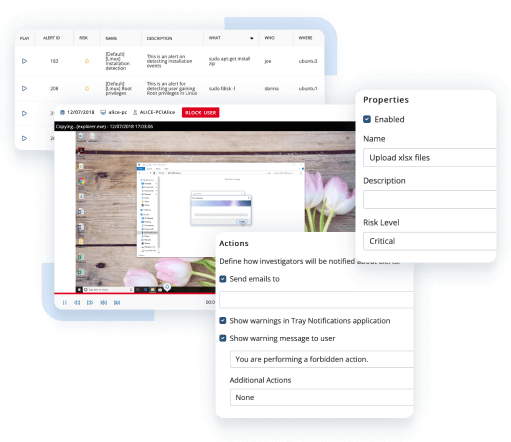
Leverage Ekran System’s predefined and custom security alerts to promptly notify your security officers of suspicious user activity. Respond to threats manually or configure real-time automatic responses to certain user actions.

Generate detailed reports on user activity to analyze your internal threat landscape and support your organization’s security audits. Provide forensic investigators with cybersecurity evidence by exporting user session recordings in a tamper-proof format.

Pseudonymize the recorded personally identifiable information of your employees and third parties to meet the requirements of data privacy regulations. You can later de-anonymize data for incident investigation.


Get more with enterprise-grade insider threat detection software
Visually structured evidence trail resulting in low incident response time
Context-rich recordings significantly reduce CERT and SOC response times. One-click search across suspicious activity makes investigations faster and more effective.
AI-based compromised account detection
Cybercriminals are constantly improving their ways of compromising privileged accounts. Powered by artificial intelligence, the Ekran UEBA module can detect a hacker who has penetrated a corporate system using stolen credentials.
Lightweight software agent and highly optimized formats for storing data
The lightweight agent works silently and isn’t noticeable to users or other programs. Collected data is saved in searchable and highly optimized video, audio, and text file formats for compact log storage and easy reporting.
Active in your environment in 20 minutes or less
Ekran System is quick to install and easily integrates with SIEM and ticketing systems. You’ll get a ready-to-use solution right after a coffee break.
Why companies choose Ekran System®
Ekran System continuously monitors various endpoints, including both end-user machines and servers, within any network architecture. Being one of the best user activity monitoring tools for Windows, Ekran System also works for macOS and is a powerful Linux/UNIX session audit tool. It even supports X Window System and all popular virtualization solutions. Ekran System allows agent-based and jump server-based deployments as well as any combination thereof.
Designed for tracking user activity on tens of thousands of endpoints, Ekran System demonstrates exceptional stability and performance. As for maintenance and reliability, the platform provides high availability and multi-tenant deployment, system resource and health monitoring dashboards, and automated maintenance tasks.
Besides tracking user activity, Ekran System provides enhanced incident alerting and response functionality. But that’s not all. Using Ekran System Client, you can set up access and identity management. Since Ekran System also provides server user activity monitoring, you always know what is happening in your network.
The unique licensing offered by Ekran System enables cost-effective deployments of any size, from small pilots to enterprise projects. Floating endpoint licensing enables license reassignment in a couple of clicks. For virtual environments, this process is automated.
Meet IT security requirements with Ekran System’s cybersecurity solutions for insurance companies
ISO 27001
Global information security management standard
PCI DSS
Worldwide financial security standard
SWIFT CSP
Cybersecurity for financial institutions
SOX
Cybersecurity for financial institutions
FISMA
U.S. law safeguarding government data
GDPR
EU data privacy regulation
NIST 800-53
U.S. government cybersecurity framework
NIST 800-171
Cybersecurity standard for U.S. contractors
NERC
Standards for North American power systems
GLBA
U.S. law on financial data protection
NISPOM Change 2 and H.R. 666
Protecting classified information in the U.S.
SOC 2
Audit standard for data security
HIPAA
U.S. law protecting medical data privacy
DORA
Enhancing software development practices
NIS2
EU law for critical infrastructure cybersecurity
Recommended resources
Ready to strengthen your defenses with Ekran System?
Consult our experts on the most efficient insider risk management approach to meet your organization’s cybersecurity needs.






