Each year, cyber attacks and data breaches are becoming more devastating for organizations. According to the 2022 Cost of a Data Breach Report by IBM, the global average cost of a data breach reached a record US$4.35 million in 2022. However, security teams are often not ready to detect all security gaps in their organizations. The scope of their monitoring is usually so broad that it’s challenging to anticipate where a potential threat might come from.
However, identifying security gaps is easier if the security team can understand the logic of threat actors. Fortunately, the MITRE ATT&CK framework provides a comprehensive approach to better detect and mitigate adversarial behavior.
What is MITRE ATT&CK in cybersecurity?
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. It’s a knowledge base of cyberattackers’ tactics, techniques, and procedures that reflect various phases of the hacking lifecycle. Initially, MITRE designed this framework to structure adversarial behavior for conducting penetration testing. But now you can use ATT&CK to advance cyber threat models, help security officers better understand attackers’ actions, and ensure timely incident detection and mitigation.
Particularly, the ATT&CK framework allows you to go beyond traditional cyber threat indicators of compromise and move to behavioral detection analytics. It provides security teams with knowledge of how cyber attackers interact with particular platforms to achieve their malicious goals.
The MITRE ATT&CK model structures adversarial behavior into matrices to show relations between tactics and techniques used by attackers and how you can effectively mitigate attacks.
As of today, MITRE offers three collections of matrices associated with different subject matters.
- ATT&CK for Enterprise contains data on adversarial tactics and techniques malicious actors use for Windows, Linux, macOS, and other desktop operating systems.
- ATT&CK for Mobile unites exploit knowledge for iOS and Android.
- ATT&CK for Industrial Control Systems (ICS) includes information about malicious actions within an ICS network.
Let’s look closer at how these matrices are organized.
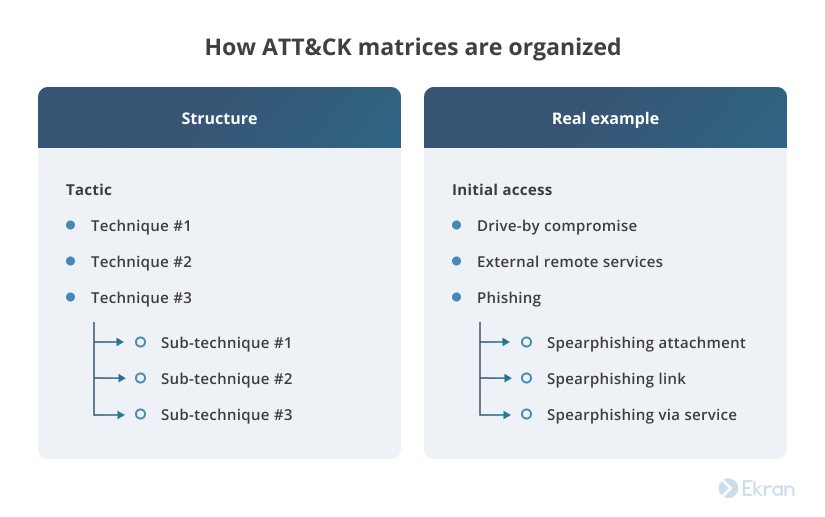
Each matrix includes a set of tactics and techniques that attackers may use to achieve their malicious goals at a particular stage of an attack. Tactics describe what a perpetrator is trying to achieve, while techniques explain how they accomplish their goals. Each tactic includes a range of techniques that an attacker can use. Techniques, in turn, can have several sub-techniques.
All information on techniques is structured in the following way:
- The procedure examples section lists malicious software often used to carry out the particular technique.
- The mitigation section provides advice on what actions you should take to prevent the execution of a certain technique.
- The detection section suggests what kind of processes should be monitored in order to detect this technique.
- The references section provides links to additional resources for deeper analysis.
Cyber criminals won’t necessarily use all the tactics described in the ATT&CK matriсes. Probably, a malicious actor will execute the minimum number of tactics and techniques to remain unnoticed while achieving their goals.
Responding to Change: How to Improve Your Organization’s Cybersecurity
ATT&CK for enterprise
In this section, we discuss how you can use the ATT&CK Enterprise matrix to enhance the security of your organization. By mastering the MITRE ATT&CK matrix for enterprises, you can find answers to the following questions:
- What adversarial behaviors are common across most attacks?
- What is the evidence of adversarial behavior?
- How do attackers act?
- What user behaviors can be considered abnormal and suspicious?
The answers to these questions will help you understand what you need to look for to detect suspicious users and how to mitigate their malicious actions. You can use the ATT&CK framework as a starting tool for your organization to develop behavioral analytics for detecting malicious behavior within the organization’s environment.
15 Cybersecurity Best Practices to Prevent Cyber Attacks in 2022
Currently, the ATT&CK for Enterprise matrix contains 14 tactics and 224 techniques cybercriminals can use for compromising an organization’s network and operating within it. Understanding these tactics will allow security officers to prioritize their corporate network defense strategies.
Let’s briefly explore all 14 tactics described in the ATT&CK Enterprise matrix:

1. Reconnaissance includes techniques malicious actors use to gather information for future attacks.
2. Resource development enlists techniques for creating, purchasing, compromising, and stealing resources that penetrators will use to support their attack.
3. Initial access refers to the vectors hackers exploit to access the targeted network or system.
4. Execution contains techniques aimed at executing malicious code after penetrating the network.
5. Persistence includes techniques that allow malicious actors to maintain their access on the network.
6. Privilege escalation contains techniques that allow perpetrators to exploit system weaknesses and vulnerabilities to gain privileged access to internal systems.
7. Defense evasion allows penetrators to go unnoticed by intrusion detection software.
8. Credential access includes techniques for obtaining legitimate credentials to gain access to systems and make perpetrators harder to detect.
9. Discovery consists of techniques that let malicious actors gain knowledge about the network so they can learn how to take advantage of their current objective.
10. Lateral movement is used by hackers to ensure access to and control of remote systems.
11. Collection includes techniques that attackers use for gathering targeted data across the system.
12. Command and control contains techniques that perpetrators use to establish communication with compromised systems within a victim’s network.
13. Exfiltration consists of techniques that allow cyber criminals to steal sensitive data from the targeted system.
14. Impact shows how attackers manipulate, interrupt, or destroy systems and data to alter the victim’s business processes in a way that’s beneficial for attackers’ goals.
Let’s explore one of these tactics, initial access, in detail. In order for an adversary to access the targeted system or network, they will apply one or more of the techniques listed in the initial access column, such as phishing or a valid account.
Even though MITRE ATT&CK matrices were primarily created to prevent outsider threats, they can also be used for behavioral analytics inside your organization. But it’s critical to remember that many MITRE techniques and tactics aren’t applicable to attacks caused by insiders. Insiders don’t usually use preliminary stage tactics and techniques used by external attackers.
In the next section, we review how you can use MITRE ATT&CK techniques to detect insider threats.
7 Key Measures of an Insider Threat Program for the Manufacturing Industry
Applying the ATT&CK matrix for insider threat detection
Let’s take a closer look at how MITRE ATT&CK mitigation and detection recommendations can help you deal with data beaches. Say a malicious insider wants to send trade secrets to a competitor by email. To accomplish this goal, an opportunistic employee needs to successfully execute several intermediate actions.
First, an insider will try to obtain access to sensitive data. To do this, they can use the privilege escalation tactic, for example. Then, they can apply an abuse elevation control mechanism or, in particular, its sub-technique, bypassing user account control, to elevate their privileges. If an attacker knows the credentials for an account with administrator privileges, they can also bypass user account control through lateral movement techniques.
To prevent such an incident, your security team needs to detect the account control bypass technique. Therefore, security analysts should monitor the following:
- Executed commands and arguments
- Newly executed processes
- Contextual metadata
- Changes in user-accessible registry settings
To mitigate this attack, you can use high-risk alerts for privilege elevation commands and user account manipulations.
Second, an insider might try the collection tactic. For instance, they may use the data from local system technique to collect sensitive data from local sources, such as the file system or databases. At this stage, a malicious actor can be detected by monitoring sensitive files, including access to and operations on them.
If a malicious insider successfully executes the previous tactic, they come to the exfiltration tactic. To steal data for further transmission to a competitor, an insider may use the exfiltration over web service technique, sending the data to a personal cloud data storage. To transfer trade secrets over the network, a perpetrator may use the data transfer size limits technique and send data in fixed size chunks to avoid triggering network data transfer threshold alerts. Exfiltration over web service can be detected through monitoring, while data transfer size limits can be detected by analyzing traffic flows.
Data breach arranged by an insider
| Tactics | Techniques | Attacker’s actions | Detection |
| Privilege escalation | Bypass user account control by using valid accounts:
use a colleague’s privileged credentials OR misuse granted privileged credentials OR perform unauthorized privilege elevation operation | Elevating user privileges | Monitoring of:
executed commands and arguments executed processes contextual metadata changes in user-accessible registry settings |
| Lateral movement | |||
| Collection | Data from the local system | Collecting sensitive data from the local system | File monitoring |
| Exfiltration | Exfiltration over web service | Transmitting data to an external cloud storage | Activity monitoring |
| Scheduled transfer | Sending out data in fixed size chunks | Email monitoring, network traffic analysis |
In the beginning of 2022, MITRE Engenuity created the Insider Threat Knowledge Base where they highlight even more techniques that malicious insiders typically use to carry out their attacks.
Preventing Privilege Escalation in the Enterprise
Benefit from combining Syteca and ATT&CK
The ATT&CK matrix for enterprises describes what an attacker usually does after they enter your corporate network. Syteca, in turn, provides you with a set of helpful tools for both preventing and mitigating cybersecurity threats. Using these two solutions together, you can enhance your organization’s defenses to counteract malicious users’ actions at any stage of the attack lifecycle.
Syteca includes identity management capabilities and a privileged account management system to prevent abusing elevation control mechanism and similar techniques:
- With Syteca’s multi-factor authentication feature, you can make sure that users logging into your network are who they claim to be.
- Syteca’s role-based access control helps you establish a fine-grained access management process to efficiently administer users’ permissions within your network.
- Just-in-time PAM capabilities of Syteca let you set up a straightforward access request and approval workflow. Use OTP passwords and time-based restrictions to ensure secure temporary and emergency access to endpoints.
Syteca also provides you with a number of monitoring tools that you can set up the way you need to ensure full visibility of your infrastructure. With these tools, you can transparently address adversarial tactics described in MITRE ATT&CK for enterprises:
- User session recording enables you to capture users’ on-screen activity in a video format with accompanying metadata, which is of great help for incident investigation and analysis.
- Syteca’s flexible and transparent system of alerts allows you to use predefined alerts or create custom alerts. In case any malicious action is detected, you’ll be immediately notified.
- The incident response functionality provided by Syteca allows you to terminate suspicious actions or block a compromised user account altogether.
These features make Syteca a comprehensive and easy-to-use tool for researching perpetrators’ tactics, mitigating cyber attacks, detecting their sources, and preventing new security incidents from happening.
US-Based Defense Organization Enhances Insider Threat Protection with Syteca
Conclusion
The MITRE ATT&CK framework is a useful knowledge base that systematizes information about tactics and techniques used by cyber attackers for penetrating enterprise networks. ATT&CK has already proven to be a trusted data source for security officers who work on behavioral analytics. Using this framework in addition to Syteca will help you define what user behavior and system security gaps to focus on to improve the cybersecurity of your corporate network.
Start a free trial today to see how Syteca can help you efficiently mitigate and prevent security incidents.




