Keylogger Software for Monitoring and Recording Keystrokes
Monitor insider activity. Detect anomalies. Respond to incidents. ALL-IN-ONE
Any recorded data on user activity would be incomplete without keystroke logs. Whether it’s a malicious user conversing with their accomplices via instant messaging, a system administrator writing a malicious script, or simply an employee spending time on personal matters while at work, employee keystroke monitoring coupled with user activity monitoring allows you to investigate all of these incidents and respond to them accordingly.
Ekran System® includes a robust keystroke logger feature that’s deeply integrated with the software’s main monitoring functionality.

Keylogger software for Windows
How exactly does the Ekran System keyboard monitoring software work for Windows?
When the keystroke recorder functionality is enabled for Windows PCs and servers, Ekran System will activate the keylogger with screen capture to also record video and audio along with metadata, regardless of the application used.
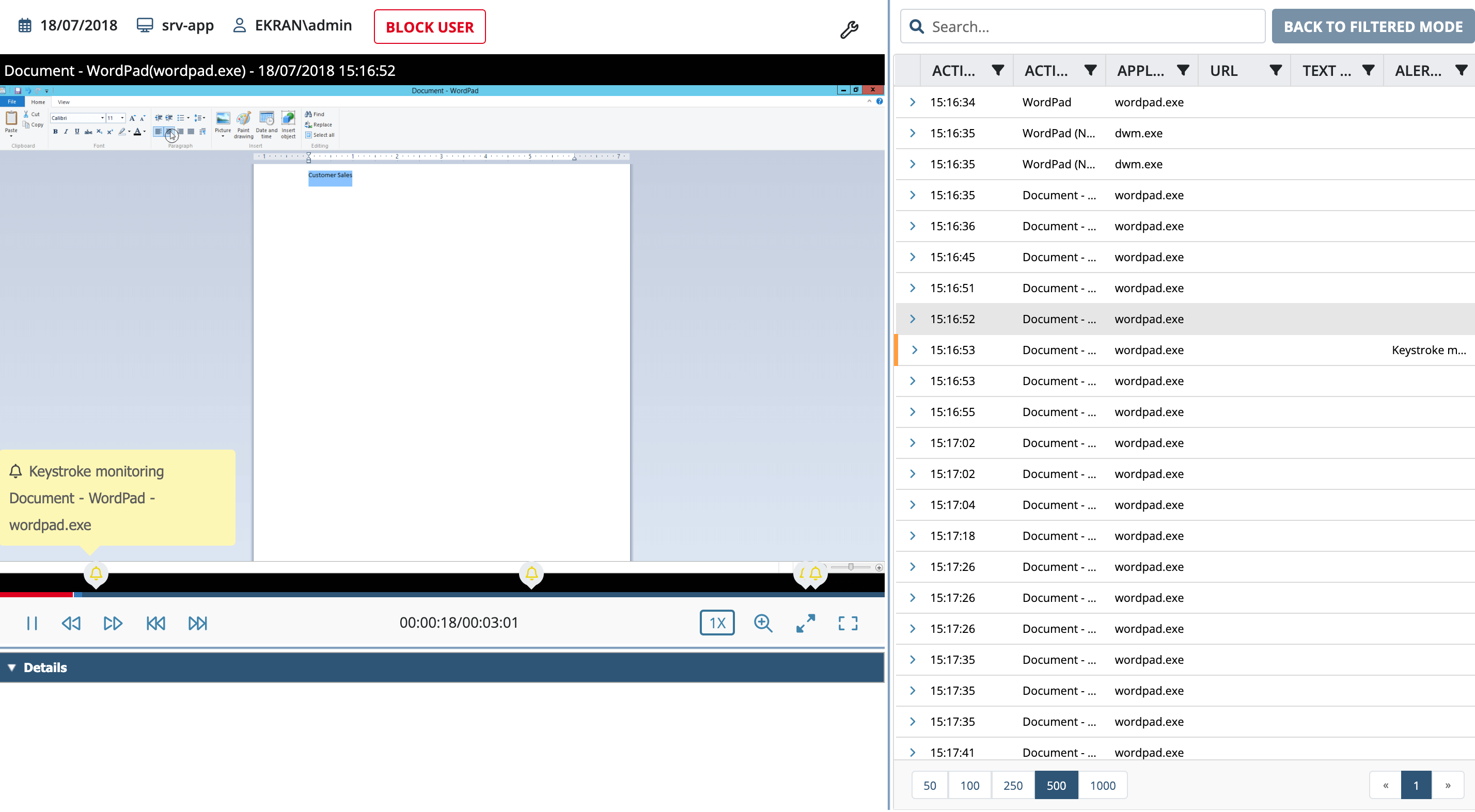
Recorded keystrokes are sorted and assigned to each individual frame of the video, making it easy to see when they were entered and what application was used. Ekran System is the program that records keystrokes continuously, meaning that a particular keyword can be used to initiate recording or to trigger an alert, providing a great way to limit the scope of the data you gather and let you react to incidents in a timely fashion.
Clipboard monitoring
Our keylogging software also continuously tracks copy, cut, and paste operations for any Windows computer and can record clipboard content, making it easy to track text data that isn’t entered directly via the keyboard.
Data recorded from the clipboard is coupled with the associated video frames, making it clear what was copied and to where, and allowing you to easily search for relevant associated events. Clipboard content can also serve as a trigger for alerts on potential incidents.
Benefits of employee keystroke monitoring
Using Ekran System as software that records keystrokes has the following benefits:
- Universal keystroke logging capability. All keystrokes and clipboard content for both local and remote sessions are recorded, including keystrokes entered in any browser, word processor, or any other application.
- GDPR-compliant keylogging. Switched on by default, this option ensures that Ekran System clients, while tracking keystrokes, do not show these keystrokes to security officers. All key logs are hidden but still searchable.
- Password hiding during monitoring. When this option is switched on, all recorded keystrokes except passwords are provided to security officers, thereby preventing this sensitive data from appearing in key logs.
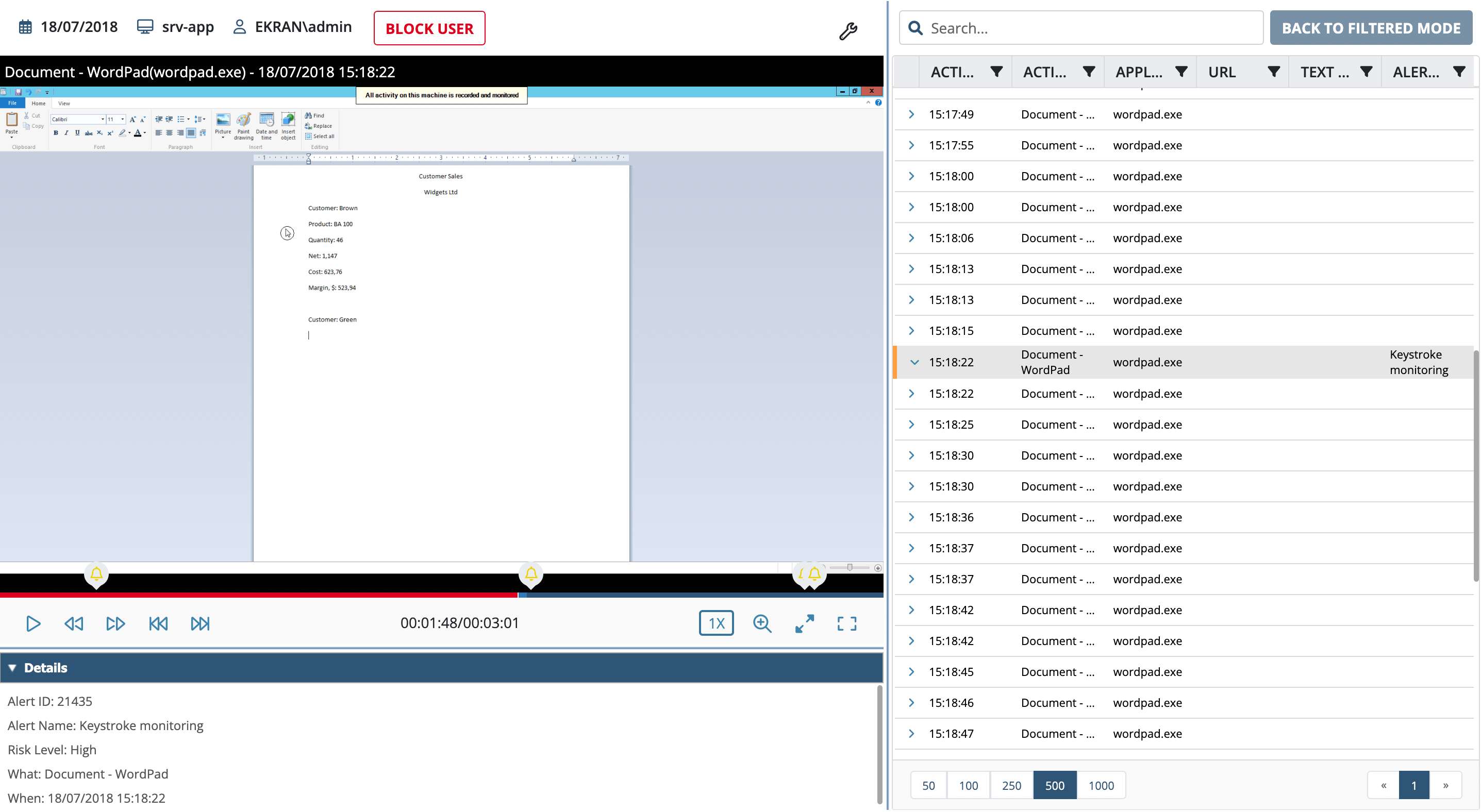
- Smart logging of edits. All edits to text are automatically detected and the final version of the text is displayed in the main window. You can also view every individual keystroke.
- Easy to search and analyze. Keystroke logger data is easily searchable, and when coupled with video recordings gives a clear picture of user actions in their proper context.
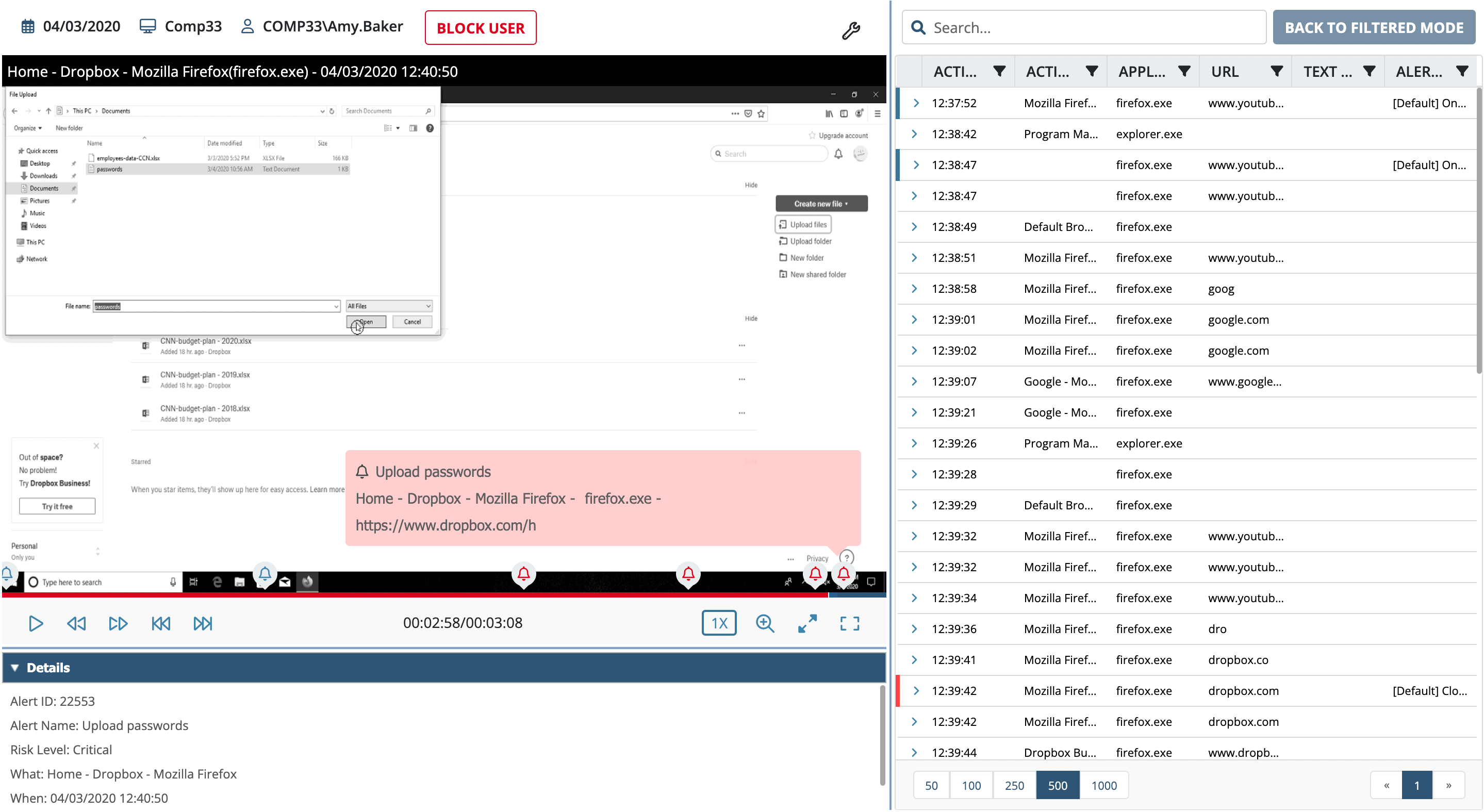
- Use keywords to initialize recordings. A specific keyword entered by the user can trigger video recording as well as recording of keystrokes and other metadata.
- Create alerts on specific keywords. A specific keyword entered by the user can trigger an alert, notifying your security personnel about potentially suspicious events and optionally also applying some incident response action, such as blocking the user or showing a warning message.
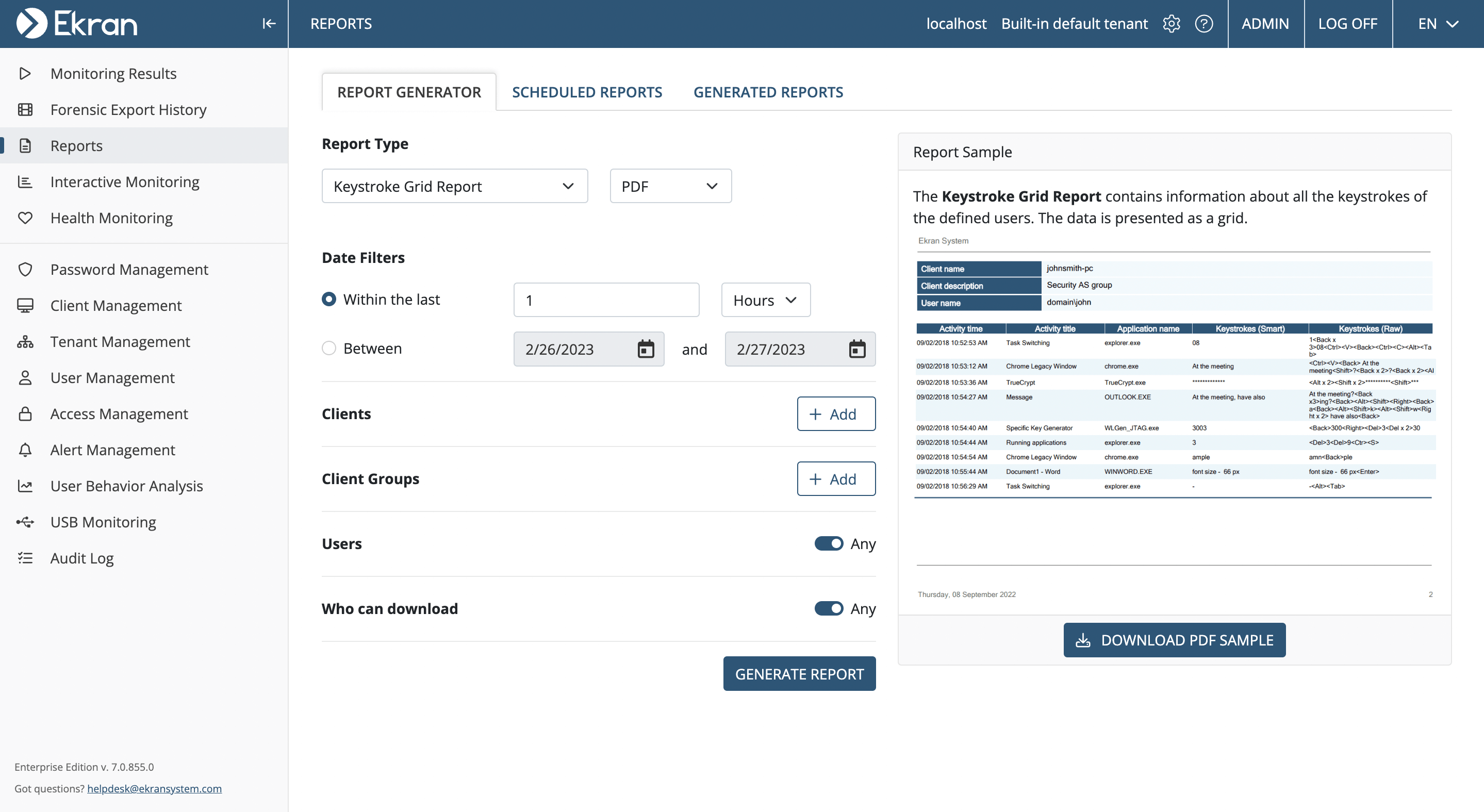
- Keystroke grid report. A summary report can be generated to review all keystrokes entered by specific users on specific endpoints during a specific time frame.
Screenshots of Ekran System keylogger software
RDP session recording and monitoring
Windows RDP monitoring includes:
- Recording of all RDP sessions including screen video recordings indexed with multilayer metadata
- Recording of other graphical sessions, regardless of the protocol or application: LogMeIn, Radmin, etc.
While the main use case is to monitor remote desktop sessions, Ekran System Windows session monitoring functionality also provides indexed video for local sessions on Windows servers.
All recorded sessions include searchable metadata with user activity details as well as all typed keystrokes and information about connected devices.
RDP session monitoring allows you to:
- Get notified in real time whenever an RDP connection is established
- Monitor all remote connections
- Record Windows terminal sessions
- Configure alert notifications
- Monitor server and endpoint activity in real time
- Export sessions in encrypted formats
- Define report parameters
Additional incident response tools include Windows Server user blocking, user warning with mandatory action acknowledgement, process termination, and device blocking.
The Windows user activity monitoring software offered by Ekran System is protected from any attempts to stop the service, block its work, or uninstall the agent.
Ekran System is continuous Windows desktop and Windows Server employee monitoring software. Even if the connection to the Ekran System managing server is temporarily lost, the endpoint client continues to record RDP sessions and local sessions, storing remote Windows desktop monitoring results locally and uploading them to the server when the connection is re-established.
How to use keystroke logging software
The functionality of the Ekran System keylogging software can be used in the following ways:
- As an assessment tool. Ekran System is not just an employee keystroke tracker. It can also assist you in assessing employee performance and help you learn whether employees are spending time productively or are engaged in personal matters.
- As a preventive measure. Knowing that specialized software records keystrokes can prevent employees from spending work hours on personal matters and from conducting malicious actions.
- As a detection tool. Keystroke logging is another tool in the toolset provided by Ekran System that allows you to detect malicious and inadvertent insiders and protect your data from insider threats.
- As an investigative tool. A keystroke log will prove a valuable source of information when investigating past incidents, providing details on communications and other actions conducted by a perpetrator.
- Use keywords to initialize recordings. A specific keyword entered by the user can trigger video recording as well as recording of keystrokes and other metadata.
More than a simple keylogger program
A simple employee activity keylogger provides only recorded keystrokes without any way to view them within their original context.
Ekran System keystroke tracker software, on the other hand, is an integral part of our user activity monitoring solution. It provides additional metadata to illustrate recorded video as well as an additional means of searching for, and alerting on, suspicious events.
The main benefits of the Ekran System corporate keylogger include:
- A rich set of features. Ekran System provides a wide range of functionality, including access control, user activity monitoring, alerting, incident response, and centralized reporting.
- Easy deployment. How to add the employee keylogger to computers? As an agent-based solution, Ekran System provides easy deployment and automatic agent updates.
- Affordable licensing. You can use Ekran System as enterprise keylogger software. Ekran System’s flexible licensing scheme with two types of licenses makes deployment affordable for both large enterprises and small companies.
- Legal and easy action monitoring. Ekran System does not provide either a hidden keylogger or any way to hide the monitoring process. We offer completely legal security software, focusing on insider threat detection and user activity monitoring.
FAQ
In most cases, the answer is yes if you are using an employee keystroke recording solution correctly. In general, organizations have the right to keep an eye on their employees during working hours to evaluate productivity, detect insider threats, and prevent employees from carrying out malicious actions.
Yet the legality of employee keystroke recording solutions depends on your local data privacy laws and regulations. Organizations in the United States must consider the Electronic Communications Privacy Act (ECPA) and state privacy laws, while organizations in the European Union and European Economic Area are subject to the General Data Protection Regulation (GDPR). The rule of thumb is to obtain consent from your employees and properly protect the monitored data.
Importantly, Ekran System offers GDPR-compliant keylogging to prevent legal issues. Also, Ekran System doesn’t provide a hidden keylogger, focusing on transparency and accountability.
That said, before implementing any user activity monitoring software, it’s crucial to ensure that it complies with all relevant laws and regulations in your region.
Ekran System keystroke recording software takes user privacy seriously and controls access to collected data. By default, access to all collected keystrokes and other monitored user activity data is limited to authorized personnel:
- IT security professionals responsible for monitoring and analyzing employee activity to detect security threats and vulnerabilities
- Managers and supervisors who monitor employees to make sure they are following established policies and procedures
- Compliance officers who perform IT compliance audits to ensure that the organization meets all applicable regulations and standards
- Legal professionals who may need to review keystroke recordings for an investigation or legal proceeding
Organizations should establish clear policies and procedures for accessing and using recorded user activity data. Additionally, organizations should ensure that all personnel who have access to keystroke recordings are fully trained and aware of their responsibilities.
There are several reasons why an organization should track employees’ keyboard activities:
- Security. Keystroke monitoring software can help organizations identify and prevent insider threats. By monitoring keystroke activity, organizations can quickly detect suspicious behavior and take proactive steps to prevent or mitigate data breaches.
- Compliance. In some industries, such as finance and healthcare, organizations need to comply with specific data security and privacy requirements. A keystroke monitoring solution can help organizations ensure that employees are following established policies and procedures.
- Evidence for security incident investigations. If a security incident happens, keystroke records can provide valuable evidence of this event.
- Increased productivity. Keystroke monitoring solutions can help organizations evaluate employee performance and identify individuals who spend time non-productively to optimize workflows. Also, keystroke monitoring may help organizations identify weak areas where employees need coaching.
Ekran System provides keystroke monitoring functionality that can help organizations identify and prevent insider threats by monitoring keystroke activity and quickly detecting suspicious behavior. Also, it can help organizations comply with specific requirements regarding data security, evaluate employee performance, and provide valuable evidence for security incident investigations if needed.
The Ekran System keylogger solution can help you detect and prevent insider threats such as negligent actions or malicious activities on the organization’s systems or data.
Security officers can use Ekran System’s preset or custom user activity monitoring alerts to get real-time notifications and take immediate actions to mitigate risks.
In addition, the AI-powered user entity and behavior analytics (UEBA) module in Ekran System automatically detects anomalous user activity, such as employees logging into your system outside of work hours.
Yes. Keystrokes logged are encrypted in the MS SQL and PostgreSQL databases by the proprietary Master Certificate, meaning that individuals having access to the databases won’t be able to review the keystrokes logged.
To safeguard personal data, Ekran System also offers:
- A monitored data anonymization mode, which pseudonymizes all personally identifiable user data (in case of a security incident, this data can be viewed by security officers or data protection officers).
- GDPR-compliant keylogging. Keystrokes are hidden but searchable. Plus, alerts can be triggered when specific words are typed.
- Password hiding. You can switch on this feature to prevent sensitive data like passwords from appearing in key logs. Passwords will be masked by asterisks and not sent to the Ekran Server.
Let’s get the conversation started
Contact our team to learn how our insider risk management software can safeguard your organization’s data from any risks caused by human factors. Book a call with us at a time that suits you best, and let’s explore how we can help you achieve your security goals.