The Covid-19 pandemic has changed the way we work forever. Although some part of the workforce returned to the office as soon as restrictions loosened, many employees wish to continue working remotely. According to data from Gartner, 60% of knowledge workers are remote, with at least 18% not planning to return to the office anytime soon.
A hybrid office is a great option for both types of workers. However, a hybrid work environment may pose considerable security risks for organizations and expose them to insider threats. In this article, we review ten practices to help you reduce insider threat risks in a hybrid office.
What is a hybrid office?
According to Gartner, a hybrid office is a flexible work model in which employees need to go to the office at least once a week while being permitted to work remotely the rest of the week.
The hybrid office model may differ from organization to organization. Here are the most popular variations:
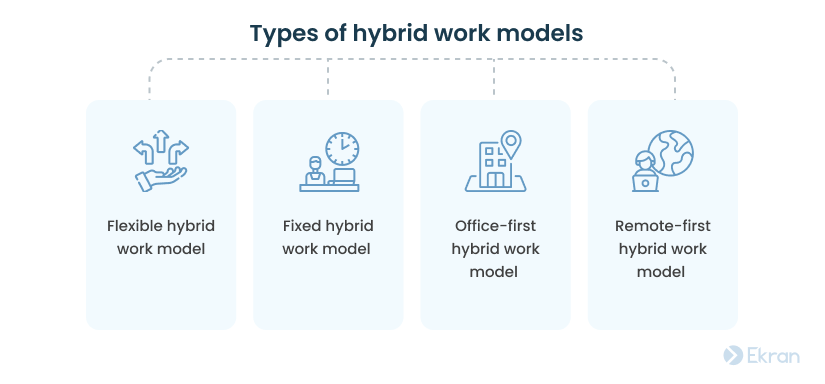

- Flexible hybrid work model – Employees choose their location for work according to their own priorities.
- Fixed hybrid work model – The organization sets dates and times for employees to work remotely or come to the office.
- Office-first hybrid work model – Employees mostly work in the office but can choose to work remotely for one or two days a week.
- Remote-first hybrid work model – Employees work remotely most of the time but visit the office occasionally.
The model you personally choose will carry some risks no matter which model that is.
Remote Employees: How to Manage Insider Risks
Why is a hybrid office environment risky for cybersecurity?
Most of the security risks of a hybrid workforce model are associated with remote workers. It’s vital to pay close attention to possible threats, as they may result in resource-exhausting cybersecurity incidents. For example, at Ubiquiti Networks an employee stole internal data using a VPN and demanded a ransom from the employer.
There are several reasons why the hybrid office model can be dangerous for your organization’s security:
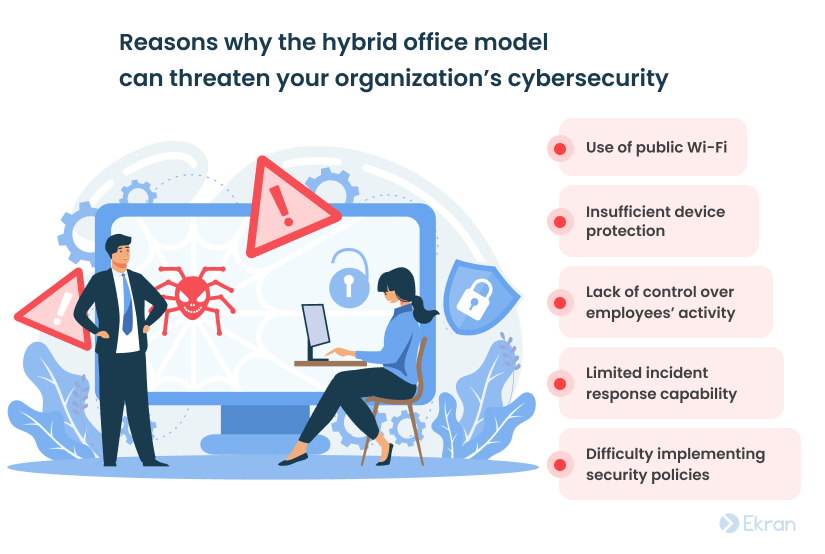

- Use of public Wi-Fi. When employees connect to your network through public Wi-Fi, there’s always a chance that a hacker may intercept the session. A malicious actor can then access all the information sent from the employee’s device to your network and may be able to use it for malicious purposes. Moreover, hackers can infect employees’ devices with malware that, in turn, can endanger your organization’s cybersecurity.
- Insufficient device protection. Employees’ personal devices often lack tools such as antivirus software, properly configured firewalls, and encryption software. Even when an employer provides devices for remote work, employees can unintentionally expose the organization’s sensitive information to outsiders. For instance, employees can leave devices unattended at home, lose them, or have them stolen.
- Lack of control over employees’ activity. It’s hard to watch and control remote employees’ activity. While security officers can restrict access to certain high-risk websites through firewalls within the organization, they rarely can do the same for remote workers.
- Limited incident response capability. It’s challenging to detect and mitigate security incidents in a timely manner if many devices reside outside the organization’s security perimeter.
- Difficulty implementing security policies. In many organizations using a hybrid model, employees often use personal devices with no security and monitoring tools installed. It’s tricky to follow an established security policy in such conditions.
A hybrid office model may seem risky for organizations from the financial and healthcare industries that work with sensitive data. However, there’s a way to improve the cybersecurity of a hybrid work setting. In the next section, we give ten best practices to help you secure your hybrid work environment against insider threats.
Top 10 Mistakes of Security Officers in Protecting Remote Workplaces
Best practices to reduce the risk of insider threats in a hybrid office environment
If your organization already uses the hybrid office model or is planning to do so, consider implementing the following security best practices to ensure a sufficient level of cybersecurity.


1. Assess insider threat risks
Insider threat risk assessment helps you identify those data assets and areas of your organization’s network that need protection the most. When you thoroughly prioritize insider risks, it’s easier to select and implement security procedures that are likely to help you successfully prevent and deter insider threat attacks in a hybrid environment.
When performing a risk assessment, pay close attention to aspects related to hybrid and remote work. Think of how you can protect your remote workers and the devices they use for work as well as about methods to improve visibility over remote endpoints.
2. Create an insider threat program
An insider threat prevention and detection program is a set of measures an organization uses to prevent and deal with insider threats. An established insider threat program can help your organization deter, detect, and mitigate insider threats in an organized and timely manner.
Building an insider threat program [PDF] requires a whole range of activities, from estimating resources needed to implement the program to selecting employees in charge of incident detection and remediation to creating incident response strategies. Taking your organization’s specific objectives, security priorities, and resources into account is critical to make your insider threat program as effective as possible.
Responding to Change: How to Improve Your Organization’s Cybersecurity
3. Develop a remote access policy
As a considerable share of employees work remotely in a hybrid office environment, it’s vital to establish a remote access policy (RAP). An RAP outlines the methods used for controlling access, establishing a connection with the organization’s data and systems from outside the network, protecting login credentials, and more.
A comprehensive RAP will tell your employees precisely how to safeguard their remote access to the organization’s resources. This, in turn, can reduce the risks of cybersecurity incidents coming from the hybrid office model.
4. Adopt a zero-trust architecture
Enforcing a zero-trust architecture can significantly improve your organization’s security without substantially increasing costs. In practice, zero-trust entails verifying every user before giving access to any of the organization’s resources.
This approach can help you reduce the risk of attacks on your organization’s network, increase visibility into who accesses your organization’s resources, and improve your ability to detect potential threats.
7 Key Measures of an Insider Threat Program for the Manufacturing Industry
5. Implement the principle of least privilege
The principle of least privilege is yet another security approach that can help you minimize the attack surface within your hybrid environment and reinforce the security of sensitive data. When using a hybrid office model, it’s especially vital to limit users’ privileges and prevent malicious insiders or outside attackers from accessing the organization’s most valuable assets.
The principle of least privilege dictates minimizing the privileges of all your employees to only those that are necessary. That means your employees should have access only to the systems and data they require to perform their duties – nothing more, nothing less.
6. Use multi-factor authentication for all accounts and devices
Not only is multi-factor authentication (MFA) one of the best time-tested security practices; it’s also a requirement of many data privacy and security standards, laws, and regulations, such as the Payment Card Industry Data Security Standard (PCI DSS), the Sarbanes-Oxley (SOX) Act, and the Health Insurance Portability and Accountability Act (HIPAA).
MFA can help organizations using a hybrid workplace model establish a secure connection with remote workers to increase the protection of sensitive corporate data. Adopting MFA in your organization can enhance cybersecurity without hampering your employees’ productivity.
7. Control the use of passwords in your organization
Letting all employees know login credentials to an organization’s critical endpoints is a risk that nobody can afford. Instead, organizations can deploy password management solutions that allow employees to access certain endpoints without disclosing the actual passwords to those endpoints.
A lot of these solutions also provide manual or automated password rotation and password checkout to further protect login credentials to critical resources.
8. Monitor employee activity
Whether deliberately or carelessly, both in-office and remote employees can put your organization’s network at risk. User activity monitoring can help you increase visibility and see signs of employee negligence or malicious actions before it’s too late.
Having a robust user activity monitoring tool in your hybrid office environment can be of great help for securing hybrid teams against insider threats. Monitoring employee activity is also great for gathering evidence and comes in handy for incident investigation.
9. Deploy UEBA tools
Even with a monitoring solution in place, it may be hard to track when an employee’s actions start being malicious. However, deploying a user and entity behavior analytics (UEBA) solution can help your security team mitigate insider threat risks in a hybrid work environment.
When new employees start working in your network, a UEBA tool establishes their baseline behavior (i.e. normal behavior). Whenever an employee’s behavior diverges from the baseline, the UEBA tool notifies you about it so you or your security officers can look into the matter and identify if the employee’s actions are malicious.
10. Conduct cybersecurity awareness training
When employees lack cybersecurity awareness and don’t understand the organization’s security policies, they tend to overlook required security measures. According to the 2022 Cost Of Insider Threats Global Report [PDF] by the Ponemon Institute, 56% of insider incidents are caused by negligence.
By conducting regular cybersecurity training for in-office and remote employees, you can significantly reduce the number of security mistakes.
Minimize the risk of insider threats in a hybrid office environment with Ekran System
Ekran System is an insider risk management tool with a wide range of features for securing your hybrid workplace:
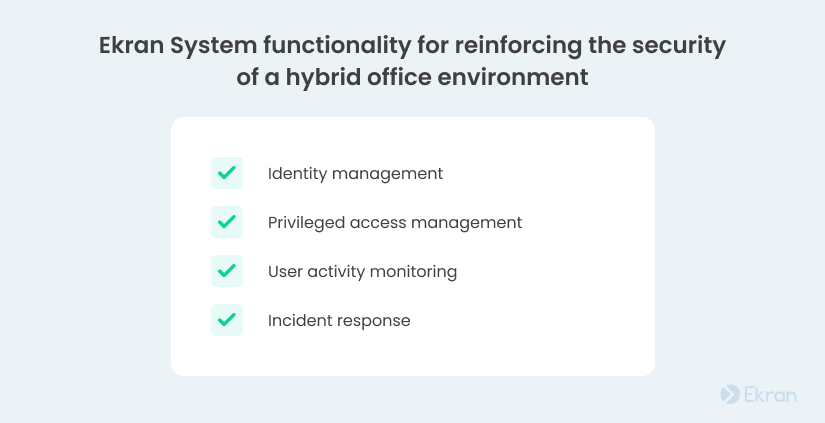

With the help of identity management functionality in Ekran System, you can:
- Securely and conveniently authenticate on-site and remote employees
- Differentiate activity of users under shared and default accounts
- Verify user identities with two-factor authentication (2FA)
Ekran System’s privileged access management functionality can help you reinforce your hybrid office IT security by enabling you to:
- Specify what endpoints privileged and regular users can access
- Grant and terminate users’ access privileges
- Manage employees’ secrets and passwords
Your security officers can leverage Ekran System’s user activity monitoring to:
- Watch live user sessions of on-site and remote employees connecting to your organization’s endpoints
- Record monitored user activity in a video format supplemented with useful metadata
- Search user activity by key episodes using parameters such as opened applications, visited URLs, and typed keystrokes
With Ekran System’s incident response capabilities, your security team can:
- Configure custom alert rules to be notified about suspicious user activity
- Use an AI-powered UEBA module [PDF] to track deviations in employees’ behavior
- Automate the response to security incidents
A Travel Agency Ensure Remote Employee Productivity and Data Security [PDF]
Conclusion
A hybrid office model сan help your organization expand its hiring opportunities and lower costs while providing your employees with flexibility in how they work. But it’s vital to take into account the insider threat risks that come with this model.
Your organization can address these risks with time-proven security practices, systematic security audits, and the use of dedicated software solutions. Consider leveraging Ekran System’s user activity monitoring, identity and access management, and incident response capabilities for a safe hybrid office.
Request a free trial to see how Ekran System can help you protect your hybrid work environment.





