Insider threat protection is an essential activity for government institutions — and especially for national defense organizations. Although cybersecurity in branches of the armed forces is expected to be robust, it still may have flaws. A 2019 report by the Identity Theft Resource Center shows that there were 2,252,439 sensitive records exposed in the government/military sector in 2019.
In this article, we highlight the role of insider threats in the defense industry and list major features of an insider threat protection program for the military. This article will be interesting for cybersecurity officers in government institutions who are thinking of enhancing their insider threat protection program.
The importance of cybersecurity in the military
The goal of every army is to defend the citizens of its country. However, a military can’t protect people if it can’t protect itself.
Modern defense organizations have complex systems and networks along with numerous databases with sensitive data on employees and service members (social security numbers, addresses, banking information, etc.). Robust resilience against cyberattacks is required for the safety of people’s personal information and state secrets.
The defense industry has to continuously enhance its cybersecurity to protect:
- Government secrets
- Communications and information systems
- Personal information of employees and service members
A lack of information about innovations in the cybersecurity strategy of the U.S. Army is bad and good news simultaneously. On the one hand, such information has to be kept secret, at least partially. On the other hand, defense organizations may not pay enough attention to trends in the cybersecurity industry, which can lead to using outdated practices and methods.
Insider Threats in the US Federal Government: Detection and Prevention
Types of insider threats in military cybersecurity
Just like in any other industry, insider threats in the military come from people within the organization. This can be current or former employees or service members, contractors, and anyone else with access to sensitive data.
Insider threats in defense organizations can cause serious damage, compromising the personal information of citizens, government and military secrets, and more. We can classify five distinct types of insider threats in the military sector and why they happen:


- Sabotage is the act of deliberately destroying, damaging, or obstructing computer systems of a defense organization. An insider can sabotage a system because of a negative work-related event, to get revenge, or in response to a work-related conflict.
- Theft in military services is usually expressed in the form of stealing intellectual property (software, programs, tools) and sensitive data (government and military secrets, personal information of enlisted individuals and civilian personnel). The most frequent motives are the intent to resell information to third parties or to demand a ransom.
- Fraud is an act of disrupting computer services using various techniques such as phishing, DDoS attacks, hacking, and malware. Fraud is used to gain access to money.
- Espionage refers to a number of practices that malicious actors can use to obtain classified information. Cyberspies may use proxy servers, cracking techniques, and malware to gain access to the secrets of an enemy state and plan their military and political actions accordingly.
- Unintentional insiders are individuals who may cause serious damage to an organization’s cybersecurity inadvertently or due to negligence.
How to Build an Insider Threat Program [12-step Checklist]
Signs of potential insider threats
To detect potential insider threats, it’s essential to pay attention to the personal aspects of employees’ lives: whether they’re struggling with everyday stress, experiencing negative workplace events, going through a tough time in life (divorce, loss of a family member, etc.).
Often, a combination of personal and workplace issues provokes a person to perform a malicious action. Here are a few examples of warning signs in employee behavior:
- Working on an office computer without authorization
- Changing political or religious views
- Becoming more aggressive in communication with colleagues
- Showing signs of disgruntlement
- Breaking or trying to circumvent the rules
The United States Department of Defense (DoD) asks its employees to remain vigilant and pay attention to changes in their colleagues’ behavior. When an employee notices someone struggling, it’s essential to notify the appropriate security or insider threat program staff. Such intervention can not only prevent severe security incidents but also benefit the personal and professional lives of employees.
Employee Activity Monitoring Software
Data breaches in the military: examples and consequences
Although military organizations have cybersecurity departments responsible for continuous improvement of their security, data breaches can still happen.
Let’s explore some of the most significant and recent security breaches that concerned the US Military.
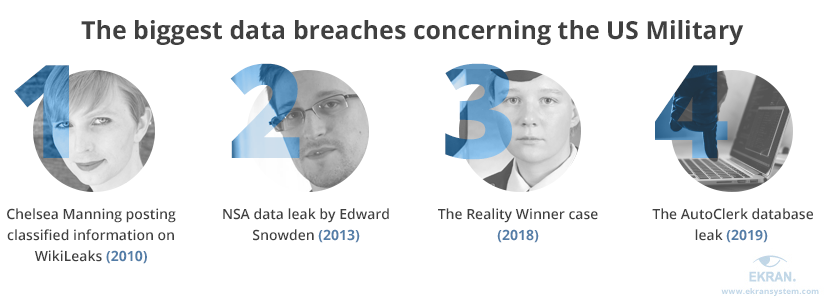

The Chelsea Manning case — A former U.S. Army soldier previously known as Bradley Manning disclosed nearly 750,000 documents to WikiLeaks in 2010. These documents were both classified and unclassified, including sensitive, military, and diplomatic information.
The Chelsea Manning case can be considered an example of an insider threat incident that happened because of work-related conflicts. Some sources claim that Chelsea suffered from bullying at the beginning of her military career.
Data leaked by Chelsea Manning includes various diplomatic cables and classified military reports that concern the wars in Afghanistan and Iraq.
The Edward Snowden case — American whistleblower Edward Snowden is responsible for one of the most significant leaks in US history. The motives behind this insider threat incident are still unclear. Although Edward Snowden claims he leaked information to expose the real surveillance state, some sources still suspect him of espionage.
In 2013, Snowden leaked highly classified information from the National Security Agency (NSA), revealing:
- The existence of the PRISM program
- Previously unknown details of a global surveillance apparatus run by the NSA
- The NSA’s top-secret black budget
- The existence of the MonsterMind program
The Reality Winner case — A former Air Force linguist and intelligence contractor, Reality Winner, was arrested in 2017 on suspicion of providing the news website The Intercept with confidential information. Reality Winner leaked a classified intelligence report about Russian interference in the 2016 US elections.
According to United States Attorney Bobby L. Christine, the leaked report contained sources and methods of intelligence gathering, and its disclosure “caused exceptionally grave damage to U.S. national security.” In 2018, Reality Winner was sentenced to five years and three months in prison as part of a plea deal.
The AutoClerk database leak — In 2019, 179 gigabytes of data was made accessible due to an unsecured cloud server run by a travel services company. Along with information about civilians’ trips, travel details of large numbers of US government and military personnel were exposed.
The AutoClerk database leak is an example of how third-party contractors can become insider threats for defense organizations. The exposed data included:
- Names
- Birthdates
- Addresses
- Phone numbers
- Travel details, including flights to sensitive locations such as Moscow and Tel Aviv
- Arrival times at hotels
- Room numbers (for some travelers)
Each breach in an organization’s cybersecurity reveals a weak point that has to be eliminated. Now let’s take a look at the process of insider threat program development for military organizations.
How to develop the DoD Insider Threat Program
According to a Department of Defense memorandum on Army Directive 2013-18 (Army Insider Threat Program), an insider threat protection program is an integrated departmental effort to manage the risks of employees or service members who may represent a threat to national security. Such a program is required to save and secure soldiers, families, civilians, contractors, infrastructure, and information.
An insider threat protection program in the army aims to strengthen the protection of personnel, information, and resources. Its main goals are:
- Ensuring the security and safety of army computer networks
- Facilitating information sharing to recognize and counter insider threats
- Evaluating employees’ security information
- Educating personnel about insider threats and their reporting responsibilities
- Gathering information to establish centralized analysis, reporting, and response capabilities
Each insider threat protection program has to be formalized as a written document so that all employees can read it and understand which actions are allowed and which are not. Such policies usually include information and best practices that show how to detect, respond to, prevent, and mitigate security incidents.
An insider threat protection program has to be updated on occasion. Usually, new rules and small edits are added after periodic audits, misunderstandings, and security breaches of any size. Also, programs have to be revised when new security tools and best practices appear.
The National Insider Threat Policy and Minimum Standards for Executive Branch Insider Threat Programs from 2012 point to five minimum standards that an insider threat protection program should meet:
- Gather, integrate, and centrally analyze and respond to critical threat-related information
- Assign personnel to the insider threat program
- Manage personnel access to classified information
- Monitor employees’ use of networks
- Provide personnel with insider threat awareness training
Now let’s take a look at the major five steps to develop an insider threat protection program for the military.


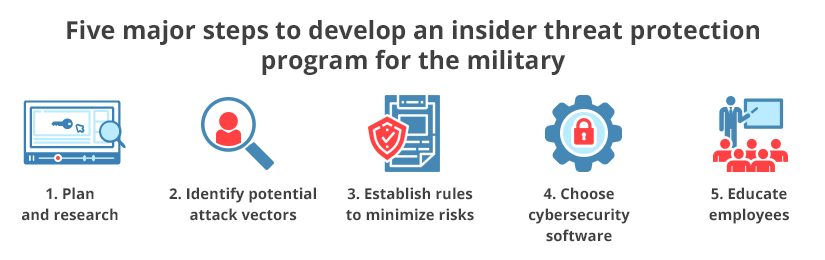

1. Plan and research
Before creating a program, thorough research and planning are required.
First, military organizations have to comply with existing laws, explore recommended programs, conduct independent research and reviews of cybersecurity in the defense industry, and explore various documents related to the issue of insider threats within government and military organizations.
Here are a few essential documents to review during the planning and research stage:
- Federal Information Security Management Act of 2002
- Cybersecurity Readiness Review prepared at the request of the Secretary of the Navy
- Cybersecurity of NATO’s Space-based Strategic Assets by Chatham House
- Assessment of the Military Services’ Insider Threat Programs by the Department of Defense (redacted version below the email)
- SECNAV Instruction 5510.37, signed by the Secretary of the Navy on August 8, 2013
The next step is to analyze industry incidents caused by insider threats and think of ways to avoid similar situations in the future. The major goal is to prevent corporate espionage, unauthorized access, and sabotage that may lead to the leak of sensitive data and cause a threat to national security.
2. Identify potential attack vectors
Although insider threat protection programs are developed for each particular organization — while considering particular risks that may occur in specific industries — they have many commonalities.
For instance, every security program for a military organization should include information about about groups of employees that often pose a threat to the organization’s cybersecurity.
An insider attack may come from:
- Former employees
- Current employees with a history of violating the rules
- Contractors and other third-party vendors that have access to systems and networks
- Users with privileged access
- New employees that may be inadvertent insiders due to lack of knowledge about cybersecurity rules
3. Establish rules to cover key threats
After the planning stage, military organizations already know the weak points of cybersecurity systems that may be used by malicious actors to compromise sensitive data.
Now it’s time to complete the insider threat protection program with basic rules designed to prevent data breaches when working with employees and contractors.
To minimize the risks of insider threat incidents, organizations should:
- Conduct a thorough background check for each employee and contractor
- Manage privileged accounts and apply the principle of least privilege
- Block all access for employees during their last day at work
- Remove all access for contractors during the last day of collaboration
- Make sure new employees know and understand all cybersecurity rules before providing access to critical assets
4. Implement cybersecurity software
Monitoring and logging information about user access and actions is one of the best insider threat detection and prevention techniques.
In case of a security incident, military software protection will provide you with details of who accessed critical assets and which actions this user performed.
Different insider threat detection software have different sets of features. The most important ones for arranging robust cybersecurity for the military are:
- Monitoring and logging functions to record all information about user activity
- Robust authentication and authorization systems to secure critical data from unauthorized users
- Incident response to instantly notify security officers about breaches or other issues
- The opportunity to customize cybersecurity software to meet the specific needs of defense organizations
Insider Threat Management Software
5. Educate employees
Cybersecurity awareness among an organization’s employees is crucial.
The more efforts are made to educate employees about cybersecurity rules, the less chance there is of unintentional data breaches. Moreover, trained employees are more attentive while handling data and can spot rule violations by their colleagues.
Educating employees usually consists of the following steps:
- The obligation for each employee to read about the insider threat protection program
- The opportunity for employees to ask questions about anything that is unclear
- Regular training for employees to remind them about basic rules and the consequences of insider threat incidents and to inform of new security tactics and procedures
- Controlling employees’ knowledge by conducting tests or doing practical checks (for example, sending mock phishing emails and checking how many employees click on them)
Since any malicious insiders can put at risk the security of employees’ personal information and classified documents, awareness of this issue has to be increased. The DoD has established an Insider Threat Awareness Month that aims to educate employees about the department’s insider threat programs.
Incident Response Planning Guideline for 2020
How can Ekran System protect the military from insider threats?
When considering Ekran System for your military insider threat protection program, you should pay attention to the following features:
Monitor user activity
- Ensure comprehensive user monitoring by recording video and audio sessions to get more details about users’ actions.
- Apply solutions for third-party vendor monitoring to control critical system configurations and secure your sensitive information.
- Improve analysis and investigation processes with an opportunity to search for required information by various parameters within the current session and across all recorded sessions.
Detect suspicious activities
- Implement AI-based user and entity behavior analytics, which analyzes user behavior against multiple factors to detect abnormal activity.
- Use a collection of alert templates that cover the most common insider threat indicators.
- Customize alert rules to cover even more potential insider threat indicators.
Respond to insider threat activity
- Use Ekran’s incident response feature to prevent security incidents by sending warning messages or instantly blocking users once abnormal activity is detected.
- Prevent uploading of malware to systems or theft of sensitive information with USB management functionality.
- Export a full monitored session or a fragment of a session in a forensic format.
US-Based Defense Organization Enhances Insider Threat Protection with Ekran System [PDF]
Conclusion
Creating and enhancing an insider threat protection program for military organizations is a complicated task that requires thorough research, planning, analysis of security incidents, searching for comprehensive threat monitoring software to protect networks and systems, and educating employees.
The key for every insider threat protection program is choosing the most suitable tools that will take care of cybersecurity within the organization. As a comprehensive insider threat protection platform, Ekran System offers a wide range of features that help organizations across various industries to secure their sensitive information and mitigate insider threats.






