New hires bring fresh ideas and unique skills but can also pose a threat. They can endanger your organization’s sensitive data and IT systems due to carelessness, lack of cybersecurity awareness, or malicious intent. The potential insider threats stemming from new employees are especially concerning for large organizations with a high flow of personnel who may find it challenging to thoroughly monitor and supervise all new hires security-wise.
Read our post to figure out why this is the case and learn how to reduce insider threat risks from new employees in your organization.
New employees as a source of insider threats
Employees are often snowed under in their first days at a new company with tons of information, paperwork, and meetings. Having to concentrate on their new projects and responsibilities, newcomers may lack attention when it comes to cybersecurity requirements. Some new hires do not find cybersecurity a priority or may even want to compromise a company’s cybersecurity intentionally.
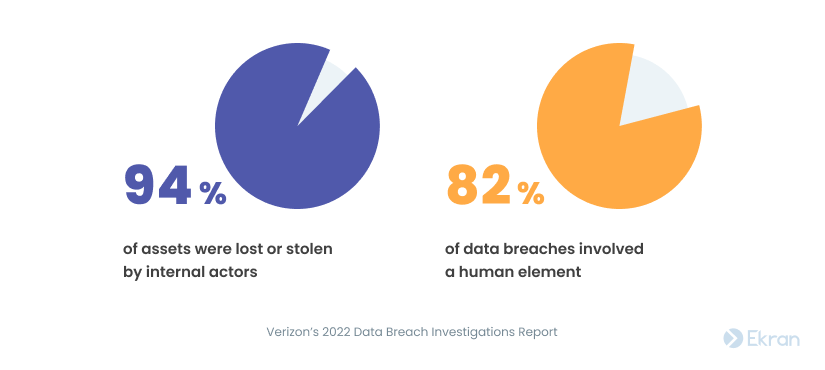
That’s why you should focus on protecting your organization from insider threats as much as from external threats. Internal actors are responsible for 94% of all lost and stolen assets, while the human element impacted 82% of data breaches in 2021 according to Verizon’s 2022 Data Breach Investigations Report.

What is considered an insider threat?
The Cybersecurity and Infrastructure Security Agency (CISA) defines an insider threat as “the potential for an insider to use their authorized access or understanding of an organization to harm that organization.” Harm includes “acts that negatively affect the integrity, confidentiality, and availability of the organization, its data, personnel, or facilities.”
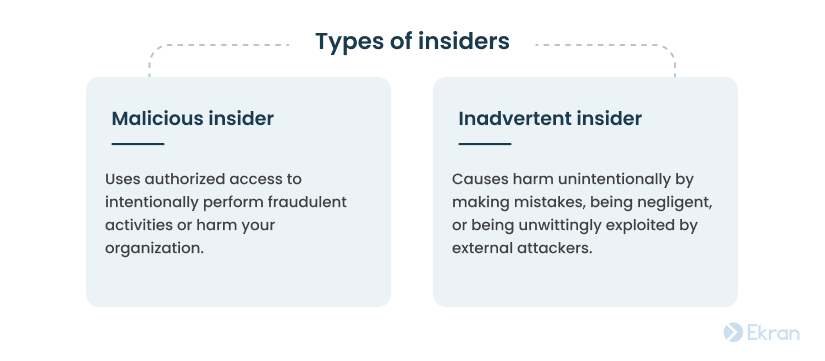
Each new employee in your company may become a malicious or inadvertent insider. It’s vital to pay attention to both types.

Learn about more types of insiders from our article What Is an Insider Threat? Definition, Types, and Countermeasures.
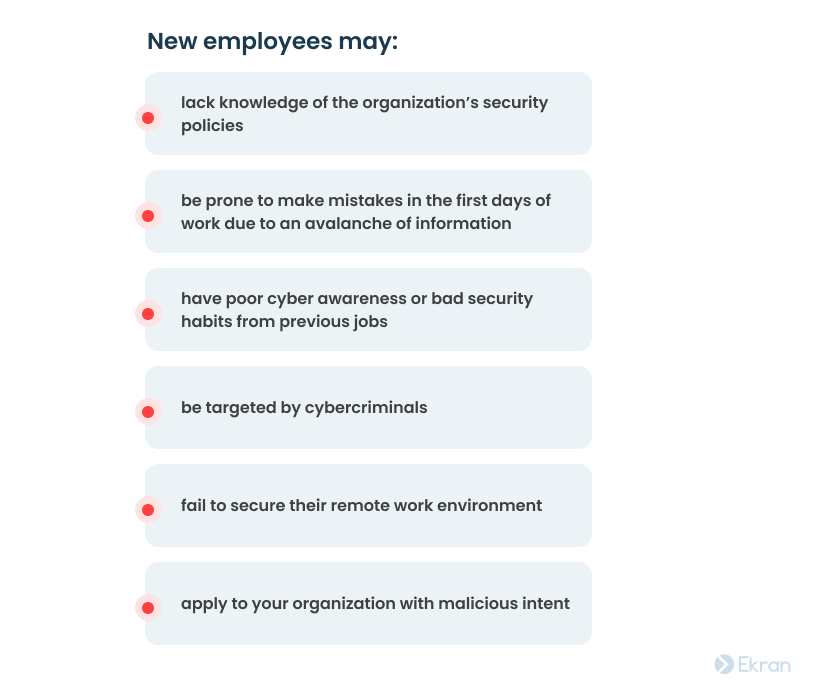
Why may newcomers be an issue?
New employees may consciously or unconsciously compromise your organization’s security. Top reasons for watching newcomers are the following:

With each new batch of recruited employees and with many of them working remotely, mitigating insider threat risks from new employees must be a top priority for every organization. It’s crucial to detect internal malicious actors and negligent employees before they cause any harm.
What risks do insiders pose?
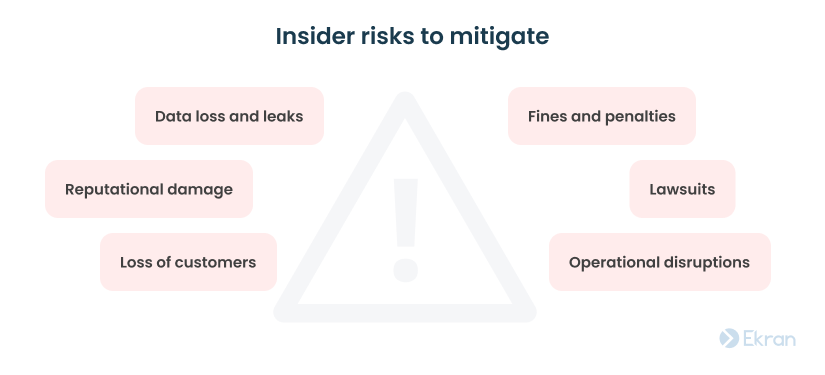
If your organization ever suffers from malicious or unintentional insider attacks, it may face some of the following negative consequences:

To help you avoid these unwanted scenarios, we have prepared a list of practices to consider when hiring new recruits.
5 Real-Life Data Breaches Caused by Insider Threats
How to reduce the insider threat risks coming from new employees?
Integrating the following seven steps into your insider risk program can help you significantly lower the possibility of your new hires causing cybersecurity incidents.
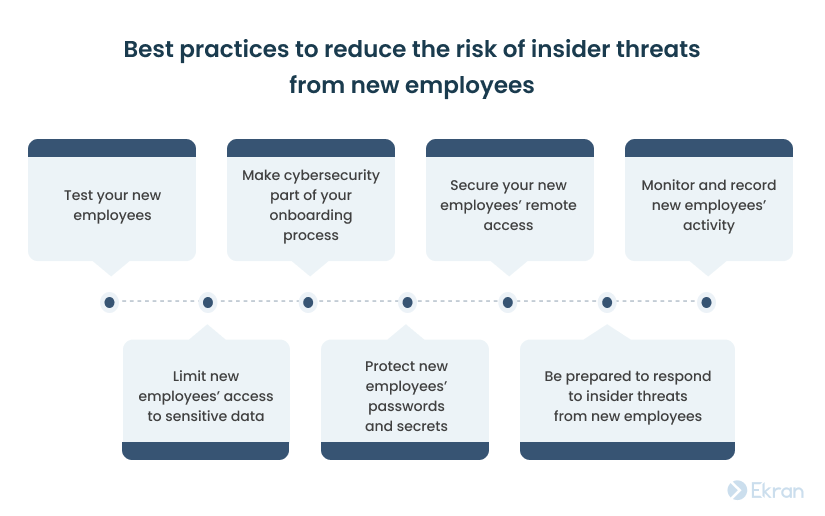

1. Test your new employees
To cut off potential risks even before an employee starts their journey in your company, make sure that the HR department properly checks candidates’ backgrounds and security skills prior to hiring them.
Background checks not only help you ensure that a candidate has what it takes to succeed in the job but can also filter out individuals that may act fraudulently or recklessly in your workplace.
Consider the following when screening applicants:


Alongside running a background check, it’s also important to test your future employee’s general cybersecurity awareness. While you shouldn’t necessarily avoid hiring people with poor security knowledge, by testing people’s knowledge you’ll know what to focus on when instructing new hires on your organization’s cybersecurity practices.
2. Make cybersecurity part of your onboarding process
The first days in your organization are the most overwhelming for newcomers. It’s vital to provide new recruits with sufficient time and resources to master your cybersecurity requirements well enough to avoid inadvertent mistakes.
Consider including all cybersecurity rules in your onboarding policy. Make it your HR department’s priority to ensure that new employees:
- Know important cybersecurity policies. By introducing new recruits to relevant information security policies and guidelines, you’ll give them an understanding of your organization’s security goals and procedures. Employees will know what cybersecurity behavior you expect of them from the beginning of their journey.
- Arrange cybersecurity training for newcomers. Extensive cyber awareness training is one of the key steps towards fostering a cybersecurity culture in your workplace. Training forms healthy cybersecurity habits among new employees, teaches them to detect various types of attacks, and provides real-life examples of cybersecurity incidents.
- Read and sign important documentation. It’s essential for new employees to take time to read and sign documents such as non-disclosure agreements and employment contracts that help ensure your data security and increase accountability.
Responding to Change: How to Improve Your Organization’s Cybersecurity
3. Secure your new employees’ remote access
Telecommuting multiplies the risks coming from newcomers, as extensive remote work environments expand the attack surface. Gartner’s article on seven top trends in cybersecurity states that 60% of knowledge workers are remote and at least 18% won’t return to the office as of 2022.
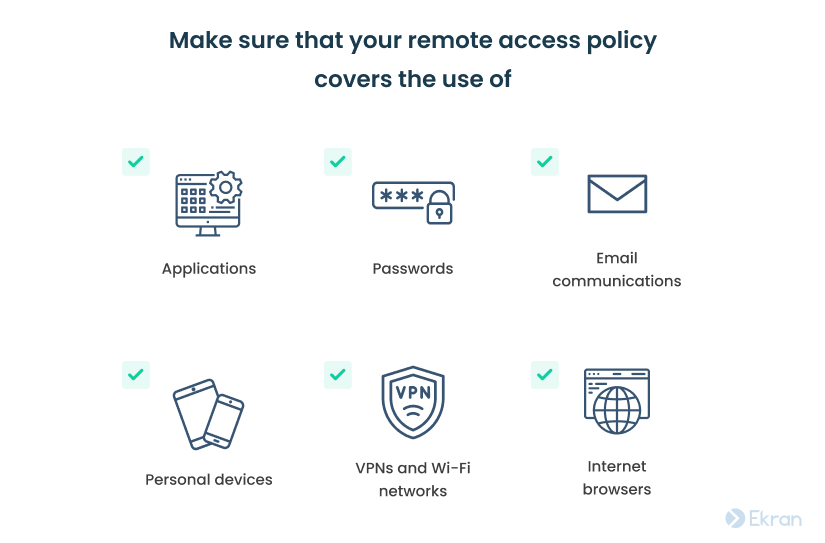
As a result, you might want to provide telecommuters with additional help and guidance to secure their remote work environment. Consider standardizing and describing security standards for remote work in a remote access policy. It defines all security procedures for accessing your organization’s data via remote networks, VPNs, and other means.
Give your new employees a list of what they should do to protect their remote work environment. Make sure that you cover the use of:

4. Monitor and record new employees’ activity
It’s quite challenging to detect malicious actions of new hires, as they are usually disguised among day-to-day duties. Even if caught, new employees may explain away their suspicious behavior as a lack of experience.
Using dedicated software to monitor employees’ activity in your infrastructure can help you spot suspicious actions or detect negligent behavior of unintentional insiders. Once you can monitor your new employees, consider focusing on detecting signs of malicious activity in your organization. Indicators include the following:
- Failure to stick to work schedules
- Misuse of company resources
- Creating backdoor accounts
- Installing unauthorized apps or malware
- Disabling system logs
- Changing security configurations of corporate machines and systems
- Downloading large amounts of corporate data
- Sending sensitive data to non-corporate email addresses
When selecting monitoring software for employees, consider giving preference to solutions that can record, automatically detect, and alert you to signs of malicious behavior.
Portrait of Malicious Insiders: Types, Characteristics, and Indicators
5. Limit new employees’ access to sensitive data
New employees shouldn’t be trusted as much as your proven workers are. Giving new hires full access to your infrastructure is not the best strategy to secure your organization’s data. To minimize the risk of insider threats from new personnel, consider limiting their access to critical assets and provide access as needed.
The principle of least privilege, zero-trust model, and just-in-time approach to access management may be handy:
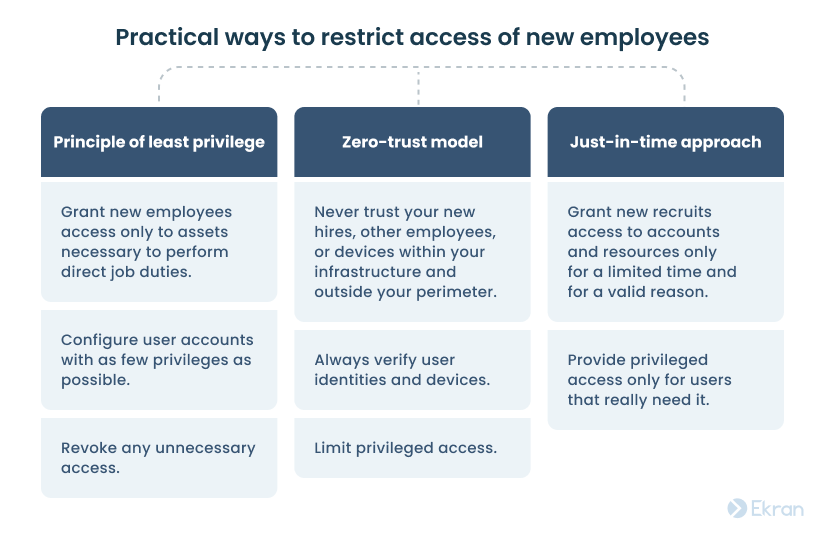

Implementing the above principles still allows you to provide employees with the access they need while limiting the potential attack surface.
6. Protect new employees’ passwords and secrets
Despite many organizations’ efforts to form healthy password behavior, a considerable number of data breaches happen because of compromised login credentials. Verizon’s 2022 Data Breach Investigations Report claims that nearly 50% of all data breaches involve compromised user credentials.
Your security officers must make it their responsibility to manage your staff’s passwords and secrets, considering various experiences and cybersecurity habits of new employees. Failure to do so is considered one of the most common mistakes in securing remote work environments.
To ease and enhance your security officers’ efforts in controlling new employees’ passwords, consider deploying a password management solution. Give preference to solutions that offer passwordless authentication capabilities, automation of password management processes, and encryption of stored passwords.
7. Be prepared to respond to insider threats from new employees
Implementing all the practices described above can’t guarantee that you’ll never face an insider threat. You still have to be prepared.
A detailed incident response plan gives your cybersecurity team coherence and confidence to act fast and efficiently by providing them with thought-through steps to take in different types of incidents.


Make sure that your organization’s freshly hired employees know what to do and whom to notify if they suspect an incident or need a consultation on security-related questions.
To enhance their incident response capabilities, some organizations deploy insider threat management software with relevant automated incident detection and response mechanisms.
5 Reasons to Start Pseudonymizing Personal Data in Your Organization
Manage insider risks from new employees with Ekran System
Ekran System is a universal insider risk management platform that allows you to handle cybersecurity risks from new employees from the day they start working at your organization.
Ekran System helps you implement a holistic approach to insider risk management by allowing you to:
| Ekran System’s holistic approach to insider risk management | |
Monitor user activity |
|
Manage access |
|
Respond to incidents |
|
Additionally, Ekran System has advanced auditing and reporting functionality along with other features that can help you cover a range of IT compliance requirements.

See how Ekran System helped one of our customers:
Conclusion
To protect your organization’s IT environment, consider each of your new employees a possible insider threat. You can reduce insider risks by conducting background checks on your new hires, involving them in extensive cybersecurity training, and securing their remote work environment.
Leverage insider threat protection software like Ekran System to monitor user activity of new employees, manage their access to sensitive data, and detect suspicious user behavior.






