While it’s difficult to imagine our business lives without USB devices, each USB connection can pose a serious risk to an organization’s security. Attackers can infect USB devices with malware that attacks your corporate system once a user connects an infected device. Such attacks can damage your infrastructure or machines and result in the theft or compromise of sensitive data.
Protecting your corporate computers from infected USB devices is crucial, but it’s challenging when you don’t know where to start. Let’s begin by discovering the most common types of USB device dangers and then review handy approaches to USB attack prevention.
What dangers do USB devices pose?
The number of USB attacks is increasing year by year. Аccording to the Honeywell Industrial Cybersecurity USB Threat Report 2022 [PDF], the number of threats capable of spreading over USB devices rose from 37% in 2020 to 57% in 2021. But before we figure out how to prevent USB attacks, it’s worth looking at why they’re so dangerous.
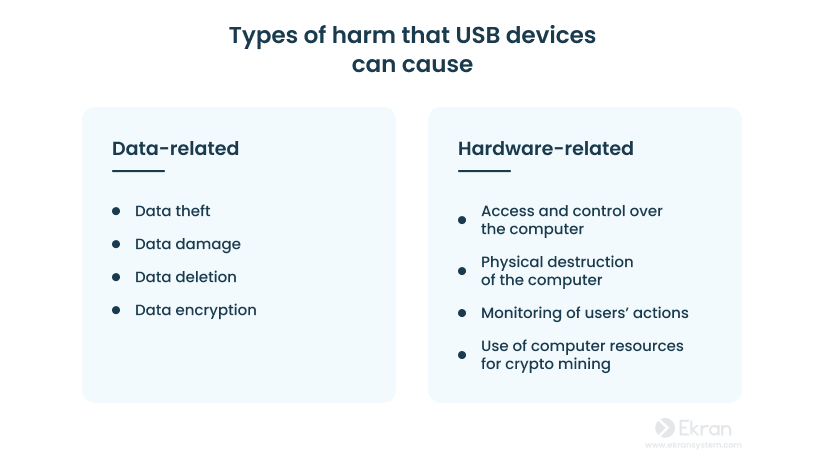
Hackers can use USB devices to gain access to a computer. In such a way, they can harm, steal, or change sensitive information, physically destroy the computer, use computer resources to spy on users, etc. In most cases, the victims remain unaware for a long time that they have been targeted.

How do USB devices get infected?
Users can infect USB devices with malware either intentionally or unintentionally.
Unintentional infection occurs when someone inserts an unprotected USB device into a compromised system.
In an intentional infection, someone knowingly infects a device in order to connect it to a system and harm sensitive data. A device infected during production may also make it onto store shelves due to a lack of quality control.
Researchers from the Ben-Gurion University of the Negev in Israel point out four ways perpetrators may attack your organization with the help of USB devices:
- Reprogramming a device’s internal microcontroller. In this case, the device doesn’t act like it’s supposed to (e.g. a charger injects keystrokes upon connection).
- Reprogramming firmware to perform actions (starting data exfiltration, launching a cryptocurrency miner, infecting a computer with a Trojan, etc.).
- Exploiting flaws in USB protocols or standards (.exe files automatically running, upgrading a driver using infected files).
- Executing an electrical power surge attack to destroy the computer.
USB Attack Types: How USB Hackers Can Attack Your System
Cybercriminals can infect not only USB flash drives but any device that connects via a USB port, such as a keyboard, microphone, or mouse. To understand how to mitigate threats from USB attacks, you first need to know what methods and devices hackers use to steal sensitive information or harm hardware.
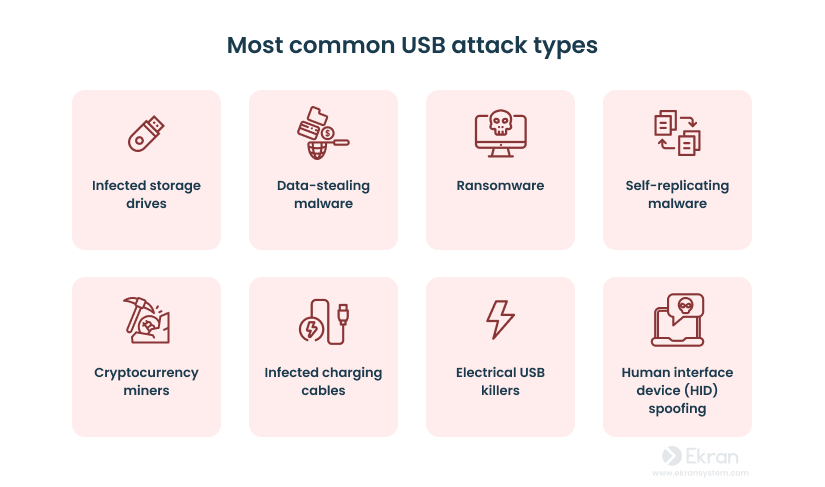

Infected storage drives
Storage devices are convenient for employees who need to work from home, share data with partners at conferences, or use several computers. But with a simple USB stick, it is very easy to infect endpoints. For example, an employee may compromise their computer by using unknown USB devices or personal USB devices that were infected elsewhere.
Between December 2021 and September 2022, the Turla espionage group (supposedly sponsored by the Russian government) carried out a cyber attack on a Ukrainian organization using an infected USB device. The incident started when someone inserted an infected USB stick into the victim’s endpoint and clicked a disguised malicious link leading to the deployment of Andromeda. This malware helped perpetrators download other malware to the victim’s computer and eventually exfiltrate sensitive data.
Employee Keystroke Monitoring with Ekran System
Data-stealing malware
Data-stealing malware is hard to detect. Once it gets inside a system, it masks itself as a harmless process. Depending on a hacker’s goal, the malware scans the network and steals browser forms, emails, or specific types of files.These types of USB malware attacks have evolved alongside USB specifications. In 2019, researchers found a vulnerability in the Thunderbolt interface of USB-C ports. The Thunderbolt connection allows low-level direct memory access, which makes it possible for installed malware to monitor keystrokes, network traffic, and even framebuffer data.
Ransomware
Ransomware is a type of malware designed to encrypt files on a computer and make them impossible to open and use. In case of a successful ransomware attack, malicious actors threaten to publish sensitive information online or permanently block access to it unless the victim pays a ransom.
In October 2022, Microsoft discovered that a relatively new worm called Raspberry Robin was being spread via USB devices and used for human-operated ransomware activity in combination with other malware. The case that Microsoft was observing started with a Raspberry Robin infection followed by Cobalt Strike activity. This activity included a TrueBot infection — a downloader malware that eventually led to the deployment of Clop ransomware.
7 Examples of Real-Life Data Breaches Caused by Insider Threats
Self-replicating malware
Self-replicating malware USB attacks allow cybercriminals not only to infect the system that a malicious USB device initially connects to but also to infect other USB devices that are subsequently connected to the same system.
In November 2022, Mandiant Managed Defense identified cyber espionage activity leveraging USB devices as a major attack stream. The initial malware side-loaded three other types of malware, disguising it as legitimate activity. And by self-replicating each time a new USB device connected to the system, this malware was able to propagate to new systems and potentially gather information from air-gapped systems.
Cryptocurrency miners
Cryptojacking is the act of hijacking someone’s computing device and utilizing the device’s processing power to mine cryptocurrencies. Cryptojacking isn’t a new type of malicious activity, but it has gained popularity over the last few years. Although miners don’t harm your system and steal your data, they exploit computer resources, slowing down performance.
Trojan.BitCoinMiner is one of the popular malicious crypto miners and can be spread via files, messages, emails, and USB devices.
Crypto mining malware called LemonDuck affects Windows and Linux systems and spreads via phishing emails, exploits, USB devices, and brute force attacks. Once LemonDuck gets into a system, it attacks all other malware already present and gains access to all vulnerabilities. After that, it steals credentials, removes security controls, and starts a crypto mining campaign.
Infected charging cables
Employees often need to charge their mobile phones and connect them to their corporate computers via a USB charging cable to do so. However, this comes with a risk that your corporate system will be damaged with a hacking device like USBsamurai — a remote-controlled USB injecting cable that costs less than $15. It uses its own wireless protocol and allows a hacker to record keystrokes through a covert wireless channel. In such a way, air-gapped networks, where systems are totally isolated from third-party devices, can be subject to attacks.
Another example of an infected device is a cable with an integrated Wi-Fi PCB created by security researcher Mike Grover in 2019. This cable is recognized by Windows and Linux systems as a human interface device. A hacker can use Wi-Fi PCB to connect to the computer remotely and manipulate the cursor, stealing information.
10 Must-Have Information Security Policies for Every Organization
USB killer
A USB device can do more than just infect your system with malware. Such devices can also exploit a well-known USB power surge vulnerability. In the USB specification, power and data lines are poorly protected from voltage peaks. This is probably the only type of USB attack you can’t protect from.
For example, the USB Kill device charges a computer’s capacitors to 110 volts and leads to system death. In 2019, a student from the College of St. Rose in New York used USB Kill to destroy 59 college computers.
Human interface device (HID) spoofing
Human interface device (HID) spoofing is a cyber attack that helps malicious users easily take control over a victim’s computer by disguising a USB device as a legitimate keyboard. Such attacks can be difficult to detect and prevent, as human interface devices are often considered trusted peripherals by most operating systems. Once your employee connects a malicious HID, it executes a set of keystrokes predefined by the attacker. In most cases, it involves downloading various malware, such as credential grabbers, backdoor malware, or ransomware.
One of the devices used in HID attacks is a Rubber Ducky. In the past, a Rubber Ducky was capable of generating fake Windows pop-ups for credential harvesting and sending a user’s saved passwords from the Chrome browser to the attacker. Recently, Rubber Duckies have become even more advanced, being able to steal data faster by encoding it in binary format.
Other USB devices
Cyber attackers can use any USB device, not only storage drives and charging cables.
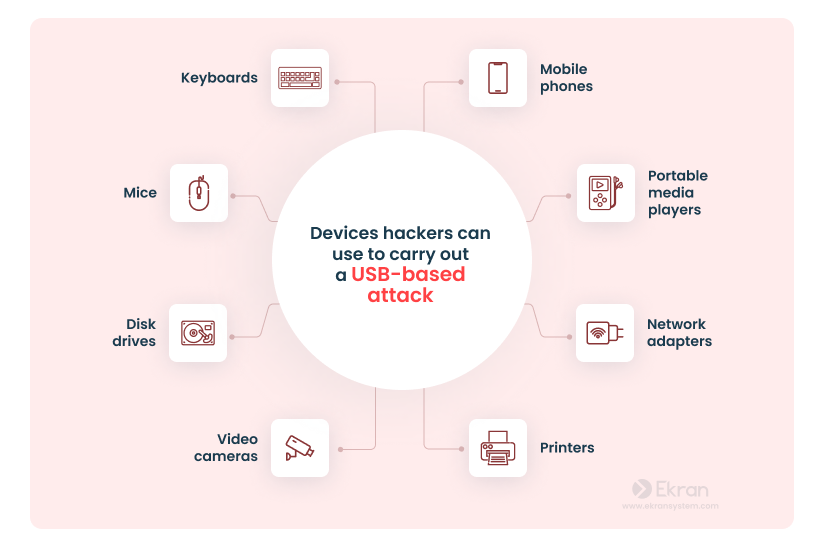

There are numerous cases when hackers have taken control of routers and cameras and used them to collect data or conduct denial of service attacks. This can happen because any such device has a microcontroller that’s responsible for communication. However, this microcontroller isn’t protected against code changes, so hackers can make it work in a completely different way than it was initially designed to.
For example, in 2021, security researchers discovered a printer-based attack vector that had lurked in HP printer drivers for 16 years and caused damage to hundreds of millions of machines. Due to this bug, hackers could gain access to a system and view, change, delete, or encrypt important data.
If an employee inserts an infected USB device into a USB port, it will take seconds to infect the computer. But detecting such an attack and estimating the damage from it is much more time-consuming. Let’s take a look at how to prevent sensitive data leaks caused by USB devices.
12 Cybersecurity Best Practices to Prevent Cyber Attacks in 2023
How to protect your organization from USB attacks
In 2022, the FBI’s cyber division updated one of their FLASH Numbers regarding a case of a cyber criminal group that targeted the US defense industry with a USB-based attack. This signals that the threat of USB attacks is still real for organizations.
Hackers continue their attempts to obtain sensitive corporate information with the help of USB devices and invent sophisticated new ways to do so. This means you should keep learning about possible threats and consider installing additional security measures to protect sensitive data from possible USB attacks.
Let’s overview some of the essential measures you can take to protect your corporate computers and networks from infected USB devices.
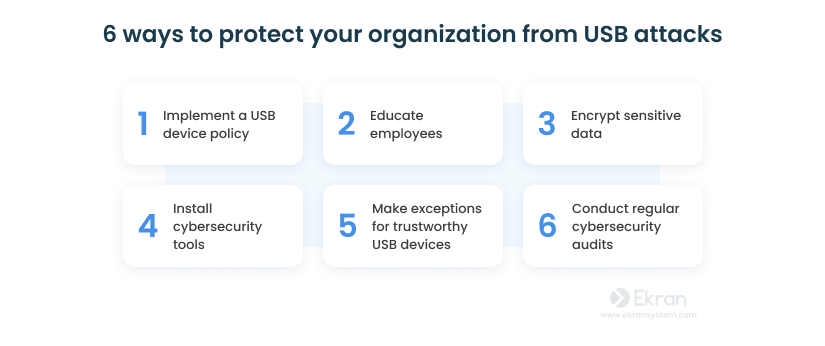

Implement a USB device policy
Creating and implementing an unambiguous policy regarding the use of USB devices in the workplace is crucial. Make sure your organization has a policy that clearly defines the correct steps for connecting USB devices to corporate computers and provides guidelines for the use of personal USB devices.
Educate employees
The human factor plays a significant role in the spread of USB cyberattacks. An employee may be irresponsible or uninformed and use an infected USB device. That’s why it’s a good idea to train your employees. Provide employees with instructions on:
- How to store sensitive information
- How to protect a USB device from viruses
- Which devices can and cannot be plugged into corporate computers
- How to recognize a USB threat
- How to protect from threats against USB-enabled devices
- What to do in case of a cyber attack
The main goal of such training is to motivate employees to be more responsible in cybersecurity matters and to do their best to prevent cyberattacks.
Insider Threat Awareness: What Is It, Why Does It Matter, and How Can You Improve It?
Encrypt sensitive data
Consider protecting your data by encrypting it. In order to access encrypted data, a user has to enter a password or key file. Thus, even if attackers manage to steal your organization’s encrypted information with a USB device, they won’t be able to read and use it.
Install cybersecurity tools
Make sure that the antivirus software you’re currently using has the scanning functionality to check every connected USB device. As well, consider using a USB management tool that can block or inform you about unapproved devices. Be sure to regularly check these systems and regularly update them.
Make exceptions for trustworthy USB devices
You may think that blocking all USB devices and ports might seem like the perfect solution to protect your organization from malware. But in fact, this will be challenging to execute and disruptive for employees. Therefore, you can create a list of exceptions with allowed removable devices based on their type or manufacturer. Thus, everything except specified devices will automatically be blocked.
Conduct regular cybersecurity audits
Over time, cybercriminals’ methods evolve and change, just as your company’s infrastructure does. New employees come in, new devices are used, new methods of protection against cyber attacks emerge. Make sure you conduct regular system audits, update the list of exceptions with allowed USB devices, and update protection tools regularly to prevent USB-based attacks and ensure your organization’s data security. Moreover, regular checks can help you identify weak points that need additional protection.
How to Pass an IT Compliance Audit
How can Ekran System help you prevent USB-based attacks?
Ekran System is insider risk management software that can be used for efficient USB management.
Using its configuration rules, you can specify the types of USB devices to monitor and block. These rules can easily be customized for every individual client and client group.
By default, Ekran System provides you with the following features:

- Monitoring of connected USB devices. Ekran System collects logs of a specified class of connected USB devices along with all other user activity metadata.
- Alerts about connected USB devices. Ekran System notifies security officers with real-time alerts when a potentially dangerous device is plugged into a USB port.
- Blocking of connected USB devices. The software automatically blocks any new device and optionally notifies the user with a pop-up message.
- Access control for USB devices. Users must ask permission to use a USB device when it is connected. The administrator can manually allow or deny access.
- Exception rules for allowed USB devices. You can add exceptions for USB devices that are allowed to connect, creating rules by vendor, hardware, and other parameters.
Finally, upon your request, Ekran System can generate a report that includes data about all events associated with USB devices.
Conclusion
As the use of USB devices in the workplace becomes more prevalent, so does the risk of security breaches. Malicious USB devices can easily steal sensitive data or infect entire networks, causing significant damage to a company’s IT security.
Ekran System provides a comprehensive USB-based attack protection tool that can be tailored to meet the unique needs of any business. With its default and customizable rules, it provides effective protection against USB threats to every computer on a corporate network.
Besides USB device management, Ekran System offers other robust functionalities to enhance the protection of your organization’s sensitive data and overall cybersecurity, such as privileged access management, user activity monitoring, real-time incident response, and auditing and reporting.
Request a free trial of Ekran System to start protecting yourself against USB attacks today!





